As we gather for Fal.Con 2024, we’re thrilled to unveil groundbreaking advancements in CrowdStrike Falcon® Cloud Security that are set to redefine cloud security. These innovations are more than just technical enhancements — they’re a bold step towards a future where unified security posture management (USPM) across cloud infrastructure, applications, data and AI becomes the new standard. With these updates, we’re empowering security teams to anticipate, understand and neutralize threats faster than ever before.
Cloud adoption has revolutionized how we do business, but it has also opened new frontiers for adversaries. The numbers are staggering: Cloud breaches increased 75% in 2023, the CrowdStrike 2024 Global Threat Report states. The report highlights a shift in the threat landscape, in which adversaries are expanding their targets to include new, more complex attack surfaces such as applications, data services and AI models.
This rapidly evolving environment demands a unified, intelligent approach that can keep pace with modern attacks. Traditional security tools, often fragmented and disconnected, simply can’t offer the comprehensive visibility and swift response that security teams need. We’ve made strategic moves to build a platform that doesn’t just detect threats but fully understands them in context and stops them before they cause damage.
Elevating Cloud Security: Uniting Data, Applications and AI for Complete Threat Context
As we dive deeper into this new era of cloud security, it becomes clear that staying ahead of sophisticated threats requires more than isolated defenses. A USPM approach, providing a 360-degree view of infrastructure, applications, data, identity and AI, is crucial. Falcon Cloud Security’s latest advancements, powered by our acquisitions of Flow Security for data security posture management (DSPM) and Bionic for application security posture management (ASPM), unite DSPM, ASPM and AI security posture management (AI-SPM) to deliver comprehensive protection across every layer of your environment.
DSPM, powered by Flow Security, adds a transformative layer to Falcon Cloud Security by automatically scanning AWS S3 buckets for sensitive data such as protected health information (PHI), personally identifiable information (PII) and payment card industry (PCI) data. This goes far beyond compliance — DSPM provides real-time, actionable insights into where your most valuable data resides, how it’s accessed and what vulnerabilities exist. This enriched data layer sharpens risk prioritization, enabling teams to defend critical assets with precision.
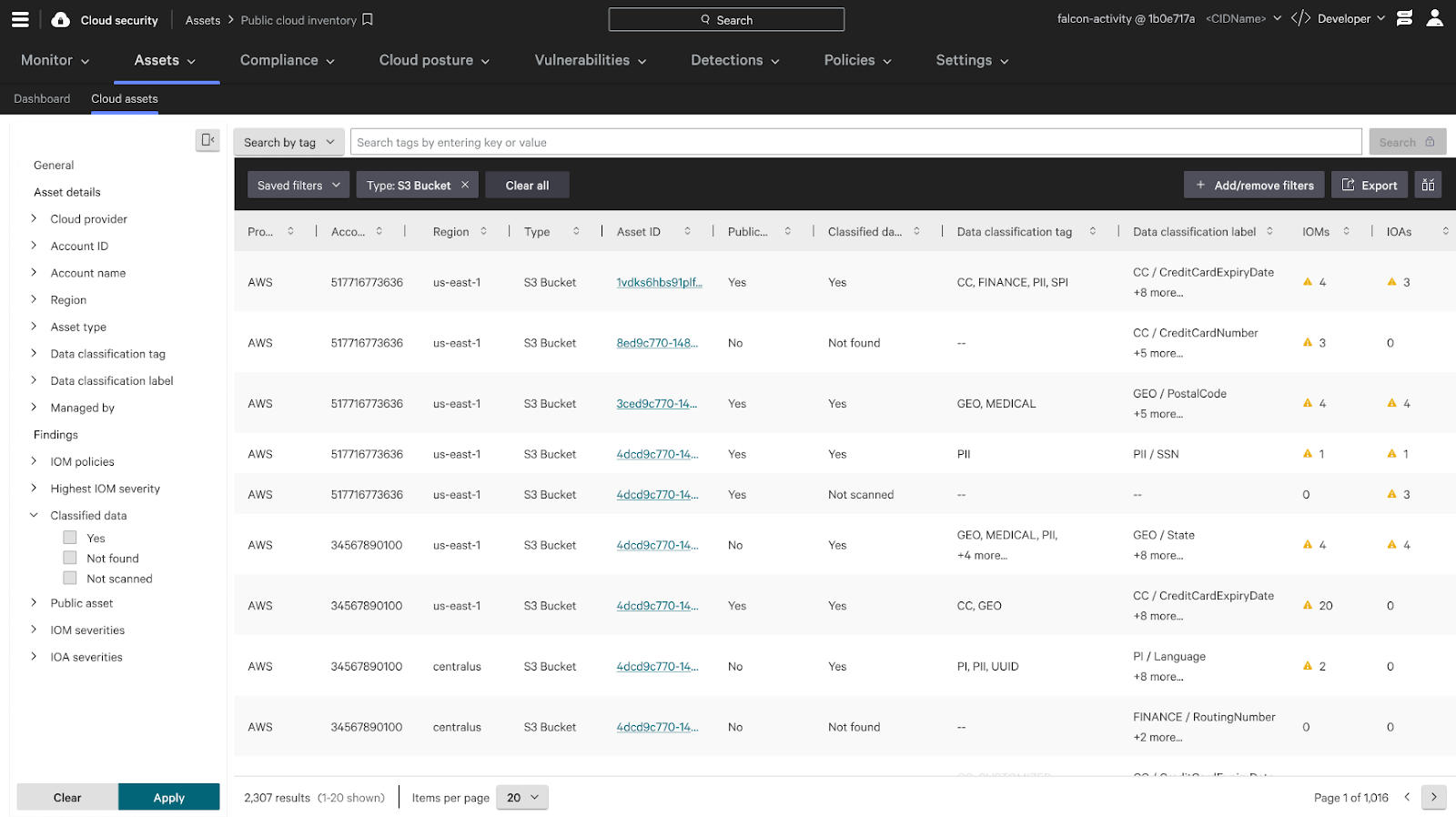
Figure 1. DSPM in Falcon Cloud Security’s Asset Inventory
DSPM helps customers discover and classify sensitive data, providing visibility and prioritization within the Falcon Cloud Security asset inventory for enhanced risk management. (Click to enlarge)
ASPM, recently integrated into Falcon Cloud Security, extends this capability by providing full visibility into your application security posture. It identifies misconfigurations and vulnerabilities across your application stack before they can be exploited, closing critical security gaps.
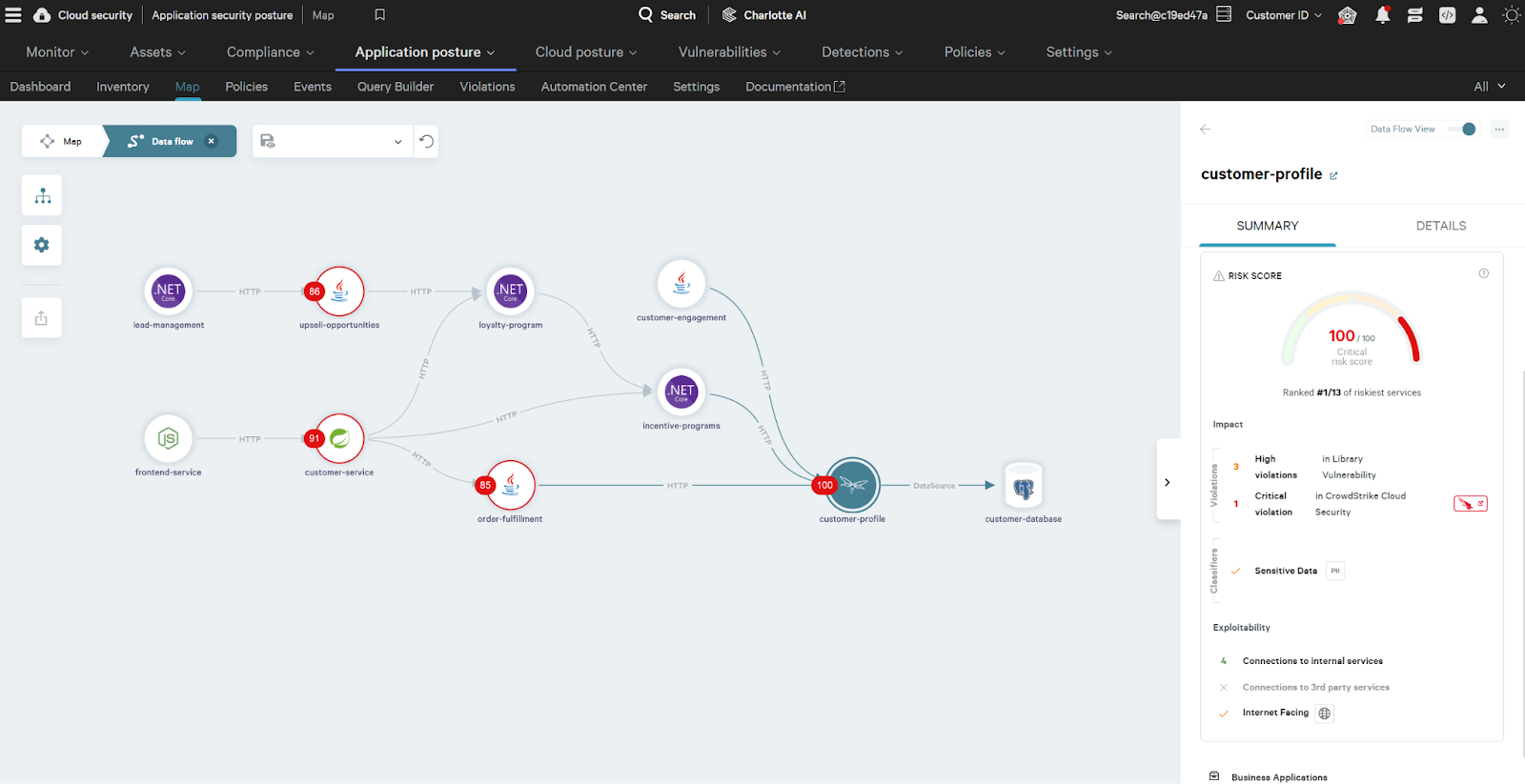
Figure 2. Falcon Cloud Security’s ASPM Application Map
Falcon ASPM finds misconfigurations and vulnerabilities and provides each microservice with a risk score based on impact, criticality and exploitability. (Click to enlarge)
AI-SPM introduces a critical layer of protection for AI models, including shadow AI, by delivering full visibility into their security posture. It detects misconfigurations and risks across platforms like OpenAI, Amazon Bedrock and Vertex AI, helping prevent AI-specific threats such as model tampering or poisoning. As AI becomes an increasingly integral part of enterprise operations, AI-SPM ensures AI models remain compliant, secure and resilient against emerging attacks.
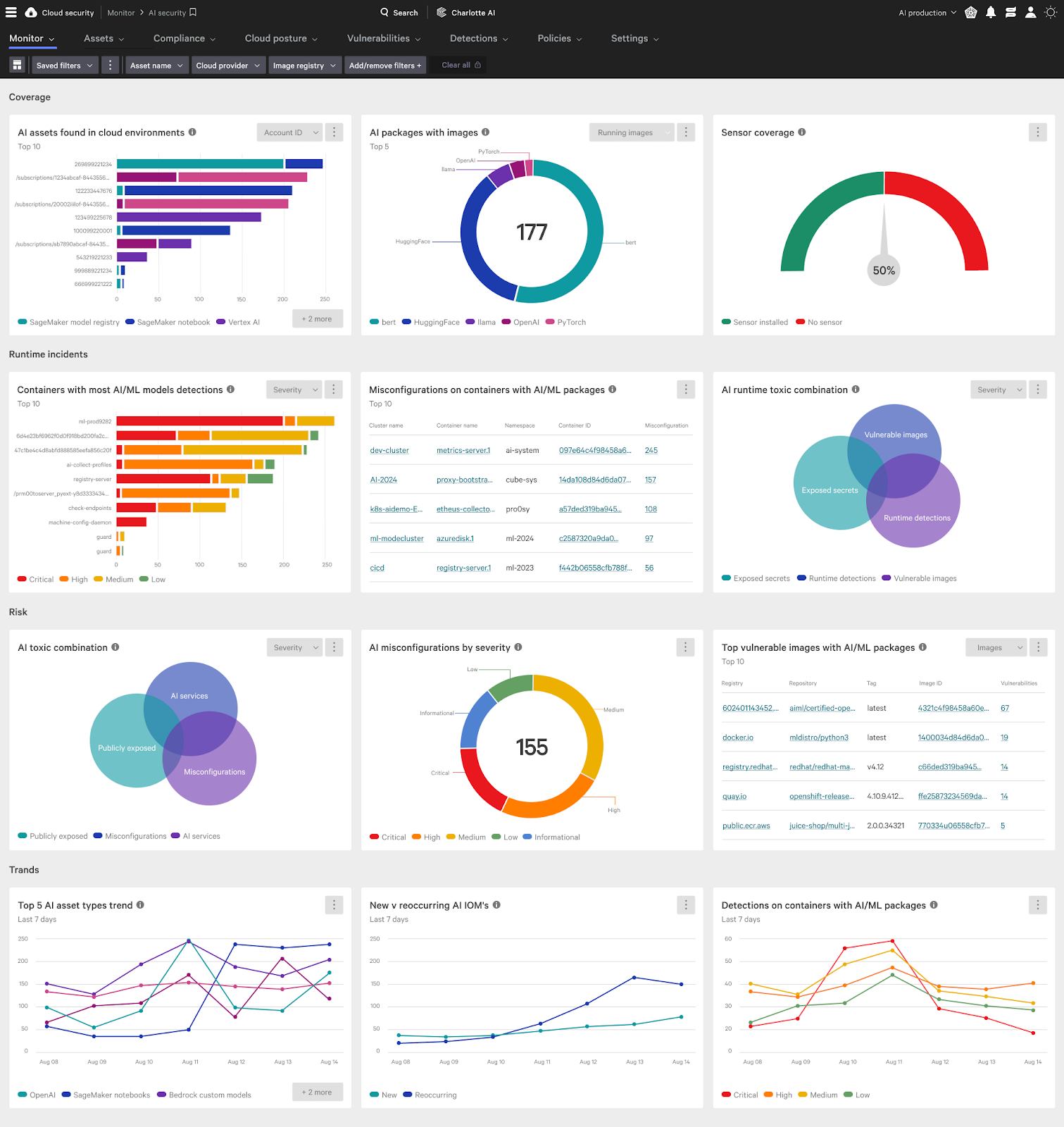
Figure 3. Overview Dashboard that Surfaces Risks and Detections for AI Services
The dashboard view provides customers visibility and insights into security risks associated with their AI workloads from build to runtime. (Click to enlarge)
Additionally, Falcon Cloud Security can monitor the runtime behavior of AI models, detecting and responding to potential threats in real time. This proactive approach enables customers to quickly identify and mitigate anomalies or threats, ensuring the continuous and secure operation of their AI systems. Together, these innovations deliver a unified, proactive approach to protecting your cloud environment, with the full context needed to stay ahead of emerging threats.
Expanding Your Control: Real-Time Asset Inventory and Drift Detection
As we expand the range of controls with DSPM, ASPM and AI-SPM, we’re also deepening it across existing assets. Falcon Cloud Security’s real-time asset inventory acts as your GPS, continuously tracking assets across AWS, Azure, Google Cloud and VMware. This live monitoring, now generally available, provides an up-to-date view of misconfigurations and potential attack paths, empowering security teams to prioritize risks and swiftly respond.
Complementing this control is our asset history feature, offering a detailed record of changes. This allows teams to pinpoint unauthorized modifications and take immediate corrective action. With VMware integration, we’ve further expanded our coverage to hybrid environments, ensuring comprehensive visibility and control across the entire cloud infrastructure.
Simplifying Detection and Response: Smarter Attack Path Analysis
As we expand control, we are also focused on simplifying it. Falcon Cloud Security streamlines attack path analysis by automatically generating a complete view of risky paths — complete with detections, problem descriptions and remediation steps — all on one intuitive screen. This provides SOC teams with the ability to quickly see the full picture, enabling swift and decisive action to neutralize threats.
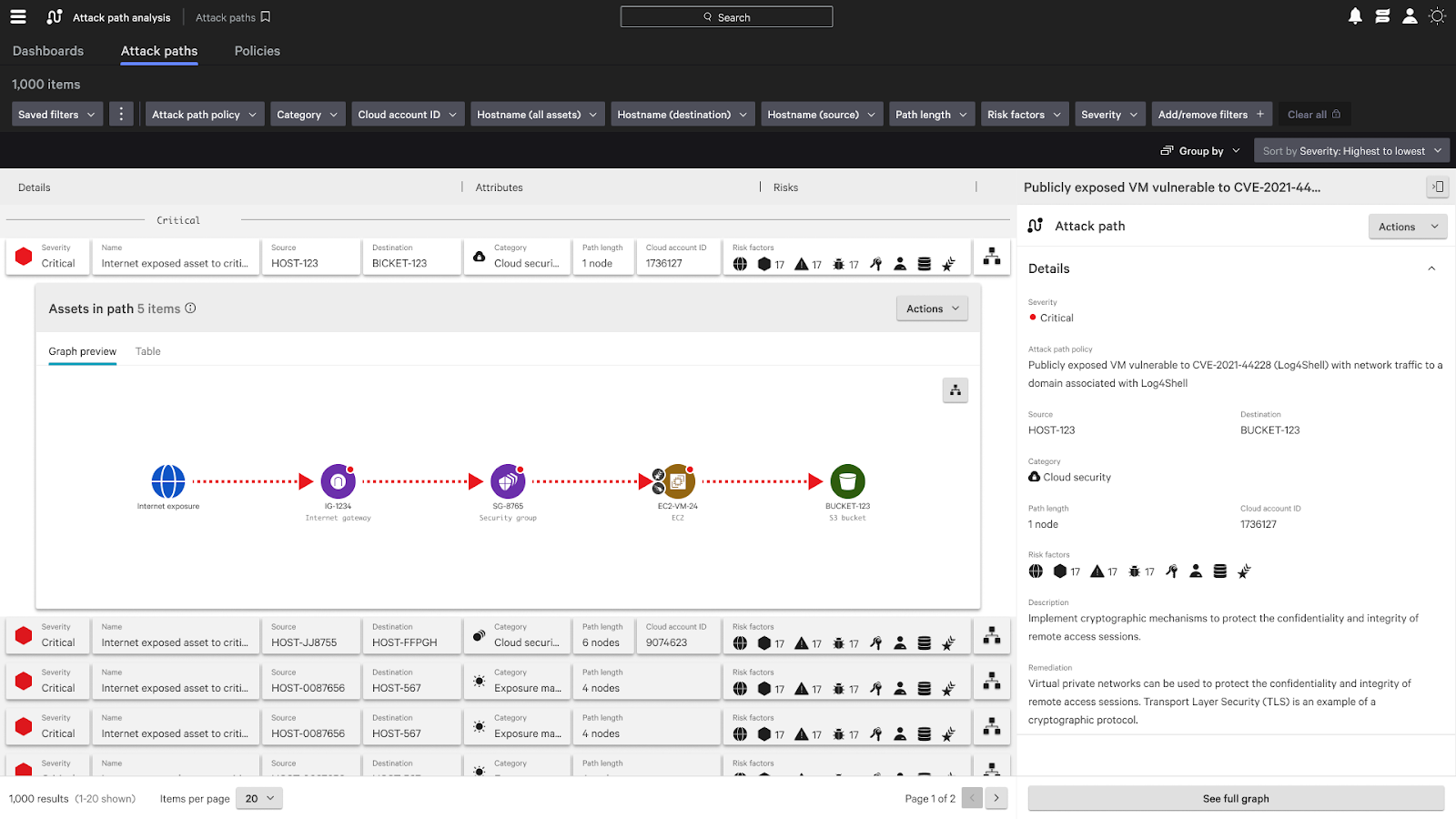
Figure 4. Attack Path Analysis in Falcon Cloud Security
From a single screen, customers can view detections, attack paths, problem descriptions and automatically generated remediation steps, reducing response time. (Click to enlarge)
Empowering Threat Hunting: Direct Cloud Log Access
The story of cloud security wouldn’t be complete without addressing the critical need for effective threat hunting. Falcon Cloud Security’s new direct cloud log access, now generally available, allows analysts to query AWS CloudTrail and Azure Activity Logs directly within the console. This enables deep investigations into specific events without leaving the platform, ensuring faster detection and response to potential threats.
Redefining Cloud Security: The Falcon Advantage
In uniting these innovations, Falcon Cloud Security is not just evolving — it’s revolutionizing cloud security. Unified security posture management is our foundation, but the ultimate goal is clear: stopping breaches before they happen. With real-time visibility, smarter risk prioritization and proactive AI-driven protection, your teams gain the edge to stay ahead of threats.
More than a safeguard, Falcon Cloud Security fortifies your entire cloud environment for whatever comes next. As we push boundaries, we’re committed to strengthening your cloud strategy and keeping you ahead of emerging risks. Stay tuned as Falcon Cloud Security drives the future of breach prevention.
Additional Resources
- Explore the latest innovations: Read our Fal.Con Cloud Security press release
- Strengthen your defenses: Request a free CrowdStrike Cloud Security Health Check
- Stay ahead of threats: Download the Insider’s Playbook: Defending Against Cloud Threats
- Understand the risks: Access the CrowdStrike 2023 Cloud Risk Report
- Try it yourself: Explore our Falcon Cloud Security interactive demo





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)











































