UPDATE: It has been confirmed that disabling telemetry will not block this exploit. Applying a patch as soon as possible is the most effective remediation for this vulnerability. Patches for 8 of the 18 vulnerable versions have been released; patches for the remaining vulnerable versions are expected by April 19th.
CrowdStrike is constantly working to protect our customers from the newest and most advanced cybersecurity threats. We are actively monitoring activity related to CVE-2024-3400, a critical command injection vulnerability in the GlobalProtect feature of Palo Alto Networks’ PAN-OS software affecting “specific PAN-OS versions and distinct feature configurations,” the vendor says.
This vulnerability, which has been given a CVSSv4.0 score of 10 by the vendor, has been observed being exploited in the wild. If exploited, CVE-2024-3400 could allow an unauthenticated attacker to execute arbitrary code with root privileges on the firewall. At the time of writing, there is no patch available. Palo Alto Networks says a patch will be ready by April 14, 2024.
Here, we explain how customers of the CrowdStrike Falcon® platform can assess their risk exposure to this vulnerability. Customers should also monitor the vendor’s website for up-to-date information on vulnerable product versions, mitigations and available patches.
Assessing Risk Exposure to CVE-2024-3400
When a new and actively exploited vulnerability is reported, one of the first actions security teams must take is determining their exposure to the issue. Understanding which of their internet-exposed assets could potentially be affected by the vulnerability is the first step to understanding exposure — and clear visibility into internet-facing devices is essential.
After identifying potentially vulnerable assets, the next step is to understand if the exposed assets have the required conditions for the vulnerability to be present.
According to the vendor information, some of the most recent PAN-OS versions (listed below) are affected. An asset will be affected if the GlobalProtect gateways and device telemetry are enabled. If these features are not enabled, this vulnerability cannot be exploited.
| Version | Vulnerable Version | Fixed Version | Estimated Patch Release Date |
| PAN-OS 11.1.2 | Less than 11.1.2-h3 | 11.1.2-h3 | 04/14/2024 |
| PAN-OS 11.1.1 | Less than 11.1.1-h1 | 11.1.1-h1 | 04/16/2024 |
| PAN-OS 11.1.0 | Less than 11.1.0-h3 | 11.1.0-h3 | 04/16/2024 |
| PAN-OS 11.0.4 | Less than 11.0.04-h1 | 11.0.04-h1 | 04/14/2024 |
| PAN-OS 11.0.3 | Less than 11.0.03-h10 | 11.0.03-h1 | 04/16/2024 |
| PAN-OS 11.0.2 | Less than 11.0.02-h4 | 11.0.02-h4 | 04/16/2024 |
| PAN-OS 11.0.1 | Less than 11.0.01-h4 | 11.0.01-h4 | 04/17/2024 |
| PAN-OS 11.0.0 | Less than 11.0.00-h3 | 11.0.00-h3 | 04/18/2024 |
| PAN-OS 10.2.9 | Less than 10.2.9-h1 | 10.2.9-h1 | 04/14/2024 |
| PAN-OS 10.2.8 | Less than 10.2.8-h3 | 10.2.8-h3 | 04/15/2024 |
| PAN-OS 10.2.7 | Less than 10.2.7-h8 | 10.2.7-h8 | 04/15/2024 |
| PAN-OS 10.2.6 | Less than 10.2.6-h3 | 10.2.6-h3 | 04/16/2024 |
| PAN-OS 10.2.5 | Less than 10.2.5-h6 | 10.2.5-h6 | 04/16/2024 |
| PAN-OS 10.2.4 | Less than 10.2.4-h16 | 10.2.4-h16 | 04/19/2024 |
| PAN-OS 10.2.3 | Less than 10.2.3-h13 | 10.2.3-h13 | 04/17/2024 |
| PAN-OS 10.2.2 | Less than 10.2.2-h5 | 10.2.2-h5 | 04/18/2024 |
| PAN-OS 10.2.1 | Less than 10.2.1-h2 | 10.2.1-h2 | 04/17/2024 |
| PAN-OS 10.2.0 | Less than 10.2.0-h3 | 10.2.0-h3 | 04/18/2024 |
Table 1. PAN-OS versions vulnerable to CVE-2024-3400
CrowdStrike Falcon Exposure Management customers can quickly identify exposed PAN-OS assets in their environments by filtering directly from the external attack surface management capability. This will help customers quickly identify all of the potential exposures, thereby proactively reducing the impact of a potential exploitation.
| Filter | Value | Expected Result |
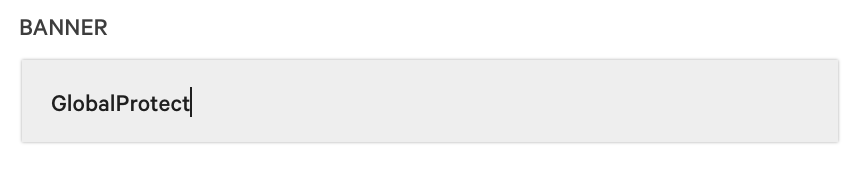
| Banner | GlobalProtect | All devices that return a GlobalProtect Banner |
| Platform | PAN-OS | All devices that are on a PAN-OS platform |
Table 2. Falcon Exposure Management query filters to detect CVE-2024-3400
NOTE: The two filters listed above should be used independently as using them in tandem will likely net 0 results.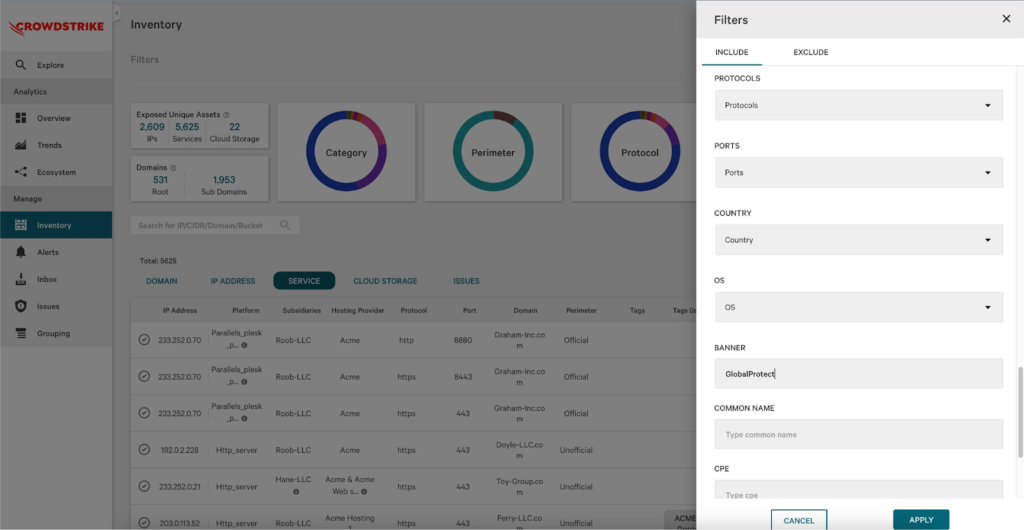
As pictured below, Falcon Exposure Management customers can broaden their search for all Palo Alto Networks devices by selecting the platform “PAN-OS,” enabling them to locate firewalls running the vulnerable version of GlobalProtect.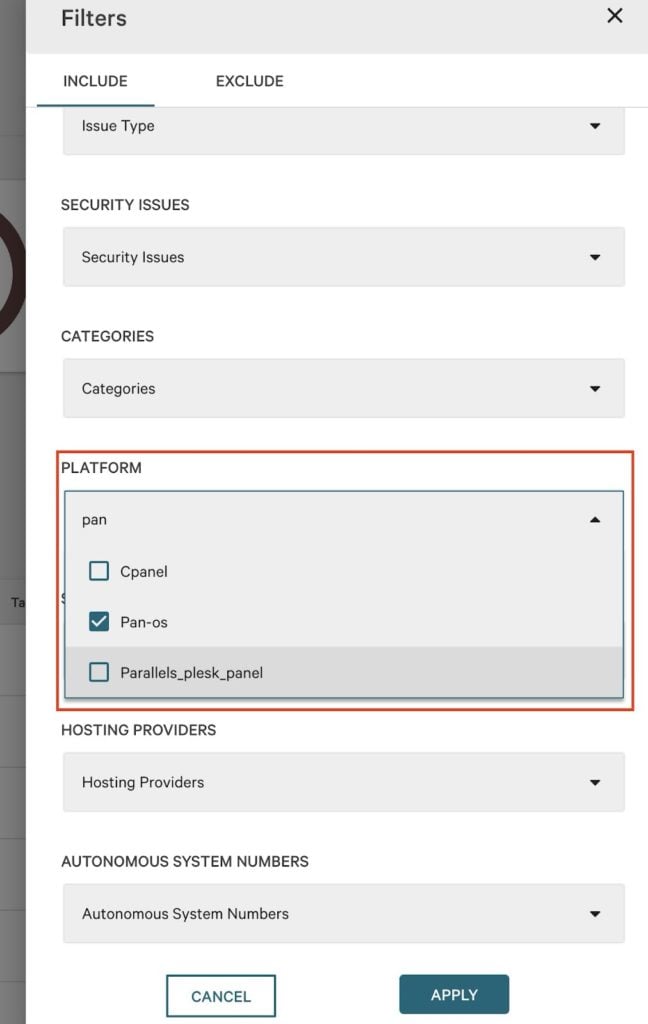
How Many Assets Could Be Affected?
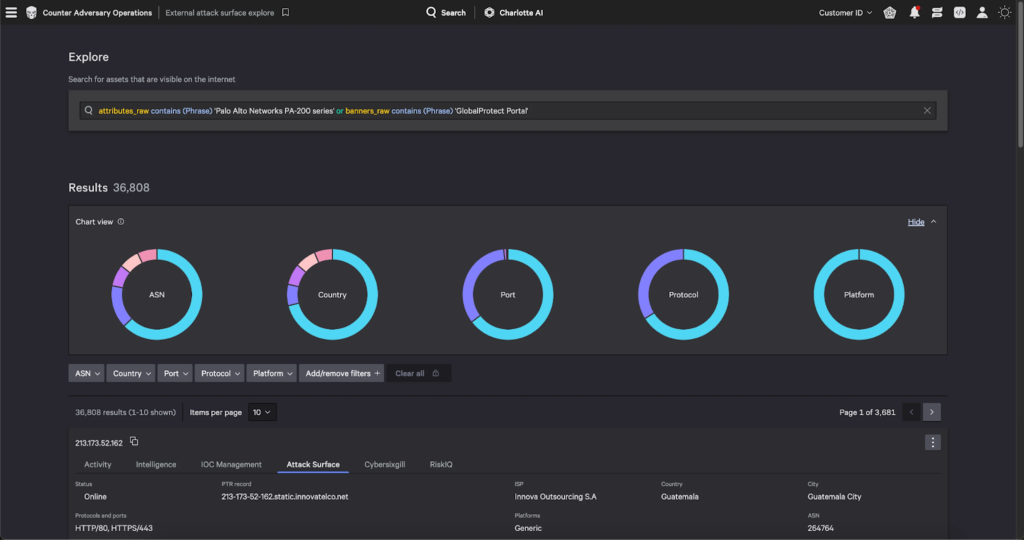
Customers of CrowdStrike Falcon® Counter Adversary Operations who would like to identify the total number of potentially vulnerable internet-exposed assets can navigate to “External attack surface explore” located in the “External monitoring” section of the Counter Adversary Operations menu. There, they can use some of the following filters to view other PAN-OS assets visible on the broader internet:
| Query | Expected Result |
| attributes_raw contains (Phrase) 'Palo Alto Networks PA-200 series' or banners_raw contains (Phrase) 'GlobalProtect Portal' | Returns any device whose attributes contain the phrase “Palo Alto Networks PA-200 series” or returns the phrase “GlobalProtect Portal” in the HTML banner |
| platform.name contains (Phrase) 'Pan-os' | Returns any device with “PAN-OS”‘ in its platform name |
| 'cpe:/a:paloaltonetworks:pan-os' | Returns any device that is noted as having PAN-OS installed |
Table 3. Queries for detecting possible vulnerable assets in “External attack surface explore,” an external monitoring feature in Counter Adversary Operations
Conclusion and Recommendations
Critical vulnerabilities, especially those actively exploited, pose a high risk to organizations. In order to mitigate the risk of exploitation, those affected by CVE-2024-3400 are advised to update vulnerable appliances with the vendor-supplied patch. Patches for 8 of the 18 vulnerable versions have been released, and patches for the remaining vulnerable versions are expected by April 19th. In addition, it is advised to increase monitoring of vulnerable appliances as well as non-vulnerable assets potentially accessible by the appliance.
Our product and internal security teams continue to actively monitor this dynamic and ongoing situation. CrowdStrike will continue to take additional steps, including mitigation and patching. As new information becomes available, we will publish updates as necessary. In tandem, we continue to develop and release new behavioral logic for the Falcon platform to detect and prevent malicious behavior related to CVE-2024-3400.
Additional Resources
- See Falcon’s unrivaled protection in action in a short demo.
- Learn about our threat intelligence and hunting subscriptions.
- Experience how the industry-leading CrowdStrike Falcon® platform protects against modern threats. Start your 15-day free trial today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)