With the ongoing need to effectively and quickly detect and respond to attacks, CrowdStrike is excited to release a new version of CrowdResponse. This new update introduces the addition of @Tasks to parse Windows Task Scheduler entries, as well as a number of fixes and updates to your favorite modules. The new CrowdResponse, including patch notes, is now available at
On Windows XP and Windows Server 2003 and below systems, the Microsoft Task Scheduler leverages binary .job files commonly found in C:\Windows\Tasks\. These binary files have the same name as the task and include fixed and variable data sections for the application to execute, the account that registered the task, status, exit codes, and flags for the year/month/day/hour/minute/second/milliseconds to execute. The full file format can be viewed in MSDN at <https://msdn.microsoft.com/en-us/library/cc248285.aspx
 The xml file captures much of the same information including triggers, settings, and execution.
The xml file captures much of the same information including triggers, settings, and execution.
Table 1: CrowdResponse output for Task Scheduler 1.0 file
Table 2: CrowdResponse output for Task Scheduler 1.2 file
www.crowdstrike.com/resources/crowdresponse/
Detecting the Adversary
One key method for identifying an attacker in an environment is to find out how they move laterally between systems once an initial foothold is achieved. Many adversaries choose to avoid malware altogether and use native utilities to perform actions on both local and remote hosts. These actions can include executing dropped malware or scripts, modifying registry keys, and terminating programs like antivirus. Once an adversary has proper credentials, such as service accounts or Domain Administrator, the opportunity is unlimited for the attacker to propagate to other computers.Windows Task Scheduler
A common choice for adversaries on Microsoft Windows computers is the Windows Task Scheduler, which can run commands with administrator privileges or even System-level privileges on older operating systems like Windows Server 2003. The Task Scheduler also provides several methods for quickly scheduling tasks across multiple machines or the entire domain. Options available to attackers include the Windows Task Scheduler GUI, the application “at.exe” (deprecated in Windows 8), and using “schtasks.exe.” Each of these leave different artifacts, however we first need to talk about the different formats of scheduled tasks.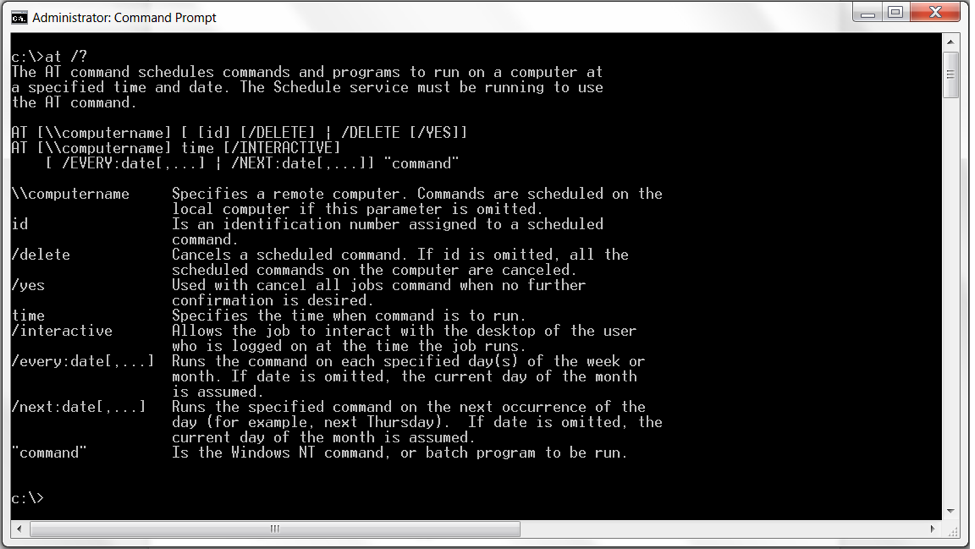 Task Scheduler 1.0
Task Scheduler 1.0
On Windows XP and Windows Server 2003 and below systems, the Microsoft Task Scheduler leverages binary .job files commonly found in C:\Windows\Tasks\. These binary files have the same name as the task and include fixed and variable data sections for the application to execute, the account that registered the task, status, exit codes, and flags for the year/month/day/hour/minute/second/milliseconds to execute. The full file format can be viewed in MSDN at <https://msdn.microsoft.com/en-us/library/cc248285.aspx
Task Scheduler 1.2
On Windows Vista and above systems, the Microsoft Task Scheduler now leverages an xml format stored in C:\Windows\System32\Tasks\. The xml file captures much of the same information including triggers, settings, and execution.
The xml file captures much of the same information including triggers, settings, and execution. Additionally, Task Scheduler 1.2 includes an API to allow programs and scripts to create tasks.
At Jobs
One of the most common means of execution used by adversaries is leveraging the At.exe application and creating scheduled tasks. By default, only a Local Administrator can issue an AT command however, with valid credentials, AT scheduled tasks run under local SYSTEM privileges on Windows XP or Windows Server 2003 devices. This can be used in assisting the attacker to obtain the elevated and coveted SYSTEM privileges. This utility was originally created to help system administrators; however, Microsoft didn’t anticipate attackers also leveraging the tool to elevate their access. The At.exe application has been deprecated in Windows 8 and Server 2012. Privilege escalation aside, the At.exe application ultimately creates the same binary .job and xml task files, depending on your flavor of Windows. These At.exe created tasks should stand out in most organizations as each task is named sequentially starting with At1, At2, At3, etc. For backwards compatibility, these files can be created in both C:\Windows\Tasks and C:\Windows\System32\Tasks.CrowdResponse @Tasks
The new @Tasks module within CrowdResponse parses both Task Scheduler 1.0 and 1.2 files, including those created with the At.exe application, with a source type of tasksv1 and tasksv2, respectively. The purpose of this module is to provide a quick look at scheduled tasks on a particular system or across an enterprise to identify suspicious or malicious attacks. Once a suspicious task of particular interest has been identified, CrowdResponse parses critical information like the event triggers for execution and principal user that created the task. To run the new tasks module, simply include @Tasks in your configuration file or directly at the command line: “CrowdResponse.exe @Tasks” An example of the results from CrowdResponse parsing an “at.exe” scheduled task to execute evil.exe on a virtual machine can be seen below.Results for both v1.0 and v1.2 tasks are returned since this action created artifact files in both formats.
| Field | Value |
| _time | 2016-05-10T18:37:31.000+0000 |
| arguments | /c "c:\Windows\Temp\evil.exe" |
| engagement | CS_TEST |
| execpath | cmd |
| executiontimelimit | 259200000 |
| ffcruntime | 2016-05-09T16_00_00Z |
| ipaddress | 10.1.1.12 |
| linecount | 1 |
| name | At1.job |
| priority | 32 |
| source | /usr/rpochron/Documents/mod_tasksv1_00000.csv |
| sourcetype | csv |
| system | CS_TEST,RP-VM,10.1.1.12,2016-05-09T16_00_00Z |
| systemname | RP-VM |
| timestamp | none |
| field | value |
| _time | 2016-05-08T18:37:31.000+0000 |
| allowdemandstart | TRUE |
| allowhardterminate | TRUE |
| arguments | /c "C:\Windows\Temp\evil.exe" |
| context | Author |
| disallowstartifonbatteries | TRUE |
| enabled | TRUE |
| engagement | CS_TEST |
| execpath | cmd |
| exectype | TASK_ACTION_EXEC |
| executiontimelimit | PT72H |
| ffcruntime | 2016-05-09T16_00_00Z |
| hidden | FALSE |
| id | Author |
| ipaddress | 10.1.1.12 |
| lastruntime | 2016-05-08T18:37:31.000+0000 |
| lasttaskresult | 0x1 |
| linecount | 1 |
| logontype | TASK_LOGON_INTERACTIVE_TOKEN_OR_PASSWORD |
| name | At1 |
| numberofmissedruns | 0 |
| path | \At1 |
| restartcount | 0 |
| runlevel | TASK_RUNLEVEL_HIGHEST |
| runonlyifidle | FALSE |
| runonlyifnetworkavailable | FALSE |
| source | /usr/rpochron/Documents/mod_tasksv2_00000.csv |
| startwhenavailable | FALSE |
| state | READY |
| stopifgoingonbatteries | TRUE |
| system | CS_TEST,RP-VM,10.1.1.12,2016-05-09T16:00:00Z |
| systemname | RP-VM |
| timestamp | none |
| userid | AtServiceAccount |
| waketorun | FALSE |
Conclusion
In closing, Windows Task Scheduler can be used for a variety of purposes including establishing persistence and lateral movement via remotely executing dropped files. The new CrowdResponse can parse the binary and xml files created with Microsoft Task Scheduler 1.0 and 1.2and is now available at
www.crowdstrike.com/resources/crowdresponse. CrowdResponse is a free version of the tool developed by the CrowdStrike Services team to collect forensic artifacts from a host exhibiting suspicious behavior or an entire enterprise during an intrusion. More information about the CrowdStrike Services team and our Incident Response offering can be found at /content/crowdstrike-www/locale-sites/us/en-us/services. While CrowdResponse handles historic artifacts and is a snapshot in time, CrowdStrike also has a commercial product, Falcon Host, which is an endpoint protection solution that combines Next-Gen AV, enterprise detection and response, real-time monitoring and hunting capabilities. Detailed information on Falcon Host and CrowdStrike’s full product lineup is also available on our website at /content/crowdstrike-www/locale-sites/us/en-us/products/. Stay tuned for more updates to CrowdResponse and happy hunting!





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)











































