“We were asked to disable identity protection capabilities to let the testing proceed — and still achieved 100% prevention.”
- The CrowdStrike Falcon®® platform delivers 100% prevention across all nine steps in the MITRE Engenuity ATT&CK® Enterprise Evaluation
- The Falcon platform delivers comprehensive visibility and actionable alerts, scoring visibility on 96% of substeps in the ATT&CK Evaluations while presenting evidence for 99% of substeps
- CrowdStrike was the only vendor to demonstrate native and unified Zero Trust and identity protection capabilities in its platform
 That’s why I’m excited to share the results of Round 4 of the MITRE Engenuity ATT&CK Enterprise Evaluation: The CrowdStrike Falcon® platform stops breaches with 100% prevention, comprehensive visibility and actionable alerts.
This clearly demonstrates the power of the Falcon platform and our unified approach to delivering the most robust protections to stop today’s most sophisticated threats. The results of the MITRE Engenuity ATT&CK Evaluation are clear: The Falcon platform continues to set the industry standard by stopping ransomware and destructive malware, stopping adversaries and stopping breaches.
That’s why I’m excited to share the results of Round 4 of the MITRE Engenuity ATT&CK Enterprise Evaluation: The CrowdStrike Falcon® platform stops breaches with 100% prevention, comprehensive visibility and actionable alerts.
This clearly demonstrates the power of the Falcon platform and our unified approach to delivering the most robust protections to stop today’s most sophisticated threats. The results of the MITRE Engenuity ATT&CK Evaluation are clear: The Falcon platform continues to set the industry standard by stopping ransomware and destructive malware, stopping adversaries and stopping breaches.
In this blog and throughout the next week, we’ll dive into the details of our participation in MITRE Engenuity ATT&CK Evaluation and the intricacies of MITRE’s approach to testing, and we’ll provide additional context that will help you understand what exactly the MITRE results mean for your business.
One interesting thing to note is that MITRE testing this year revealed the importance of understanding how adversaries are increasingly exploiting identity and credentials to try and evade detection. CrowdStrike is the only vendor to have Zero Trust and identity protection capabilities built into the Falcon platform, a capability that was part of the MITRE Engenuity ATT&CK Evaluation. CrowdStrike’s approach to Zero Trust detects and automatically prevents identity-based attacks, stopping adversaries from gaining a foothold using stolen credentials.
As testing kicked off, the Falcon platform identified that the MITRE Engenuity ATT&CK Evaluation was using a breached password and an account that was compromised. This prevented the test evaluator from gaining access to the environment to attempt compromise, stopping the breach before it started. Due to methodology, we ultimately had to disable our identity protection capabilities to let the testing proceed — and still achieved 100% prevention across all nine steps. This is a testament to the power of the Falcon platform and our unified approach to stopping adversaries from progressing attacks. We’re excited to work with MITRE Engenuity to advance the test methodology to support identity-based defenses and Zero Trust in the future. We’ll also be sharing more anecdotes from behind the scenes next week, including a deep dive on why identity security needs to be deeply embedded in security strategies to stop today’s attacks.
CrowdStrike Delivers a Unified Platform Approach to Stopping Breaches
Achieving 100% automated prevention across all of the MITRE Engenuity ATT&CK Evaluation steps speaks directly to our mission: We stop breaches. In addition to our leading prevention capabilities, analysts can leverage the Falcon platform to observe and understand all incident events from multiple vantage points to gain context on the behavior and tactics of sophisticated threats. This empowers customers to rapidly investigate threats, improve their security posture and reduce adversary breakout time. In this year's MITRE Engenuity ATT&CK Evaluation, the Falcon platform demonstrated excellence in prevention, visibility and context across all evaluation steps for both threat actors. The WIZARD SPIDER and VOODOO BEAR (Sandworm Team) adversary emulations were selected because of their sophistication and their broad range of post-exploitation tradecraft, which made them ideal for assessing visibility and coverage for security products. Figure 1. WIZARD SPIDER (left) and VOODOO BEAR (right) adversary groups
Figure 1. WIZARD SPIDER (left) and VOODOO BEAR (right) adversary groupsCrowdStrike Falcon® Platform Delivers 100% Prevention
Attackers are increasingly attempting to accomplish their objectives without writing malware to the endpoint by using legitimate and stolen credentials to try to evade detection by legacy antivirus products. According to the CrowdStrike 2022 Global Threat Report, 62% of attacks are malware-free and consist of hands-on-keyboard activity. Once inside, it only takes 98 minutes for an adversary to move laterally from an initially compromised host to another host within the victim environment. Organizations must be able to stop attackers immediately, before they can move around the network and cause damage.
CrowdStrike shuts down attacks before they can start by delivering powerful capabilities like identity-based security, comprehensive indicators of attack (IOAs), machine learning (ML), automated orchestration and threat intelligence through a unified, cloud-native platform.
The performance of the Falcon platform in Round 4 of the MITRE Engenuity ATT&CK Evaluation shows that these new capabilities stop attackers quickly, with 100% prevention across all protection tests, and stop more than 93% of attacker tactics, techniques and procedures (TTPs) before they can execute.
 Figure 2. Falcon performance on each of the nine protection tests in the MITRE Engenuity ATT&CK Evaluation (Click to enlarge)
Figure 2. Falcon performance on each of the nine protection tests in the MITRE Engenuity ATT&CK Evaluation (Click to enlarge)CrowdStrike Falcon® Platform Delivers Comprehensive Visibility, Context and Actionable Alerts
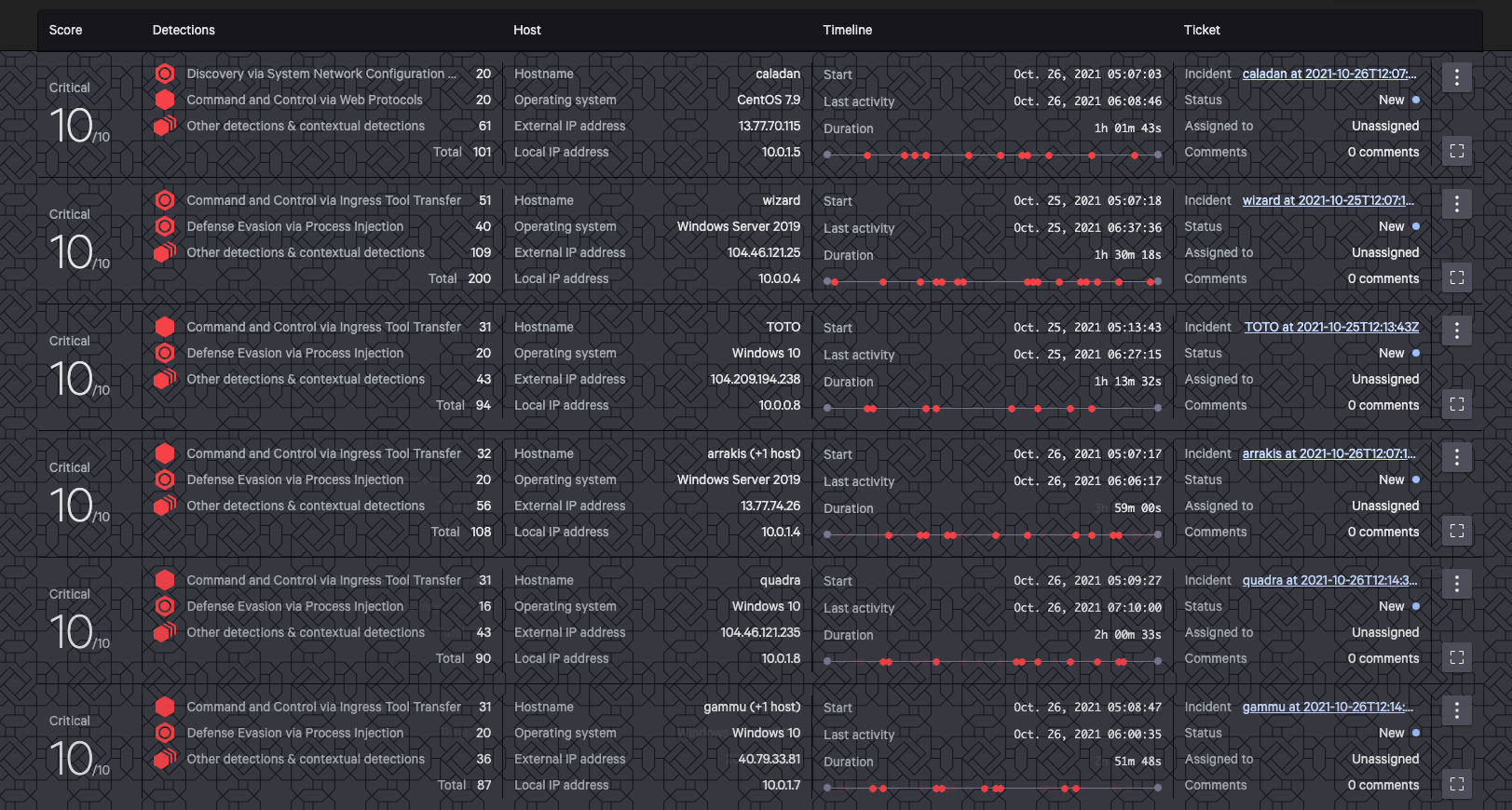
Visibility is a critical requirement of effective security, as security teams require context, historical visibility and response capabilities. The Falcon platform provides comprehensive capabilities and tools for analysts to see, stop and understand the attack, scoring visibility on 96% of substeps in the ATT&CK Evaluations while presenting evidence for 99% of substeps. Enriched results and indicators of attack give analysts the right tools to investigate and understand the technical details, process trees and TTPs. Figure 3. CrowdStrike coverage across attack steps for the MITRE Engenuity ATT&CK Evaluation WIZARD SPIDER scenario
Figure 3. CrowdStrike coverage across attack steps for the MITRE Engenuity ATT&CK Evaluation WIZARD SPIDER scenario Figure 4. CrowdStrike coverage across attack steps for the MITRE Engenuity ATT&CK Evaluation VOODOO BEAR (Sandworm Team) attack scenario
Figure 4. CrowdStrike coverage across attack steps for the MITRE Engenuity ATT&CK Evaluation VOODOO BEAR (Sandworm Team) attack scenario
 Figure 6. CrowdStrike Incident Workbench graph timeline for the MITRE Engenuity ATT&CK Evaluation VOODOO BEAR emulation (Click to enlarge)
Figure 6. CrowdStrike Incident Workbench graph timeline for the MITRE Engenuity ATT&CK Evaluation VOODOO BEAR emulation (Click to enlarge)Commitment to Transparency and Public Testing
As we continue our commitment to transparency, it is essential to focus on the importance of testing and understand how a solution should behave in an operational deployment where environmental factors — such as type of infrastructure, existing policies and cost of ownership — are at play.With adversary tactics and techniques constantly evolving, CrowdStrike continues to innovate and deliver new capabilities to automatically detect and prevent emerging tradecraft, protecting customers. Throughout the fourth round of the MITRE Engenuity ATT&CK Enterprise Evaluation, the Falcon platform proved excellent prevention against sophisticated adversaries, provided visibility across attack steps and substeps, and demonstrated once more that we stop breaches.
Additional Resources
- Read the press release.
- Learn what others are saying about CrowdStrike — visit the CrowdStrike Industry Recognition and Technology Validation webpage.
- Learn about the powerful, cloud-native CrowdStrike Falcon®® platform.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and learn how true next-gen AV performs against today’s most sophisticated threats.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)