Threat actors continue to exploit users, devices and applications, especially as more of them exist outside of the traditional corporate perimeter. With employees consistently working remotely, adversaries are taking advantage of distributed workforces and the poor visibility and control that legacy security tools provide. Traditional tools that connect employees to corporate applications like VPNs and IP-based controls grant excessive trust, potentially exposing users to threats like data loss, phishing and malware. As adversaries continue to advance their tradecraft to bypass legacy security solutions, organizations should enhance detection and response capabilities with secure Zero Trust application access beyond the bounds of traditional perimeters to dynamically protect employees and data, wherever they are located.
CrowdStrike is excited to partner with Cloudflare, a security, performance and reliability company that is helping to build a better internet. The Cloudflare and CrowdStrike integrations deliver defense-in-depth and ensure employees have secure access to applications from anywhere. Cloudflare’s work with the CrowdXDR Alliance and its expanded Zero Trust integration with the CrowdStrike Falcon® platform will accelerate the Zero Trust journey for customers and protect them from an increasingly complex threat environment.
The Cloudflare Zero Trust platform integrates with the Falcon platform to combine insights from Cloudflare’s secure global network with the enriched telemetry of the CrowdStrike Security Cloud for deep visibility and defense-in-depth across environments. This newest Zero Trust integration with Falcon allows organizations to build conditional access policies based on CrowdStrike’s Falcon Zero Trust Assessment (ZTA) device health and compliance checks and helps unify security from the network to the endpoint. The expanded partnership between Cloudflare and CrowdStrike empowers customers to rapidly identify and respond to threats, strengthening Zero Trust security posture and enhancing detection and response capabilities to thwart adversaries.
Secure Employee Access with Zero Trust Policies
To secure increasingly distributed workforces, Cloudflare’s Zero Trust Network Access (ZTNA) and Secure Web Gateway (SWG) integrate with Falcon ZTA to offer a safe, fast and easy way to enable conditional application and network access for employees. Cloudflare protects critical resources, ensuring users are granted access after verifying the identity, context and policy adherence of each request.
CrowdStrike’s Falcon ZTA scores deliver continuous real-time security posture assessment across all endpoints in the organization, providing needed context for security teams to enable effective conditional access. Users can build and enforce custom Zero Trust policies based on Falcon ZTA device health and compliance checks to mitigate risks posed by compromised or malicious devices. Customers can also invoke powerful rules like Browser Isolation, Tenant control, Anti-virus or any part of the Cloudflare deployment, leveraging enriched context from CrowdStrike to secure employees’ access to applications, no matter where they are working. 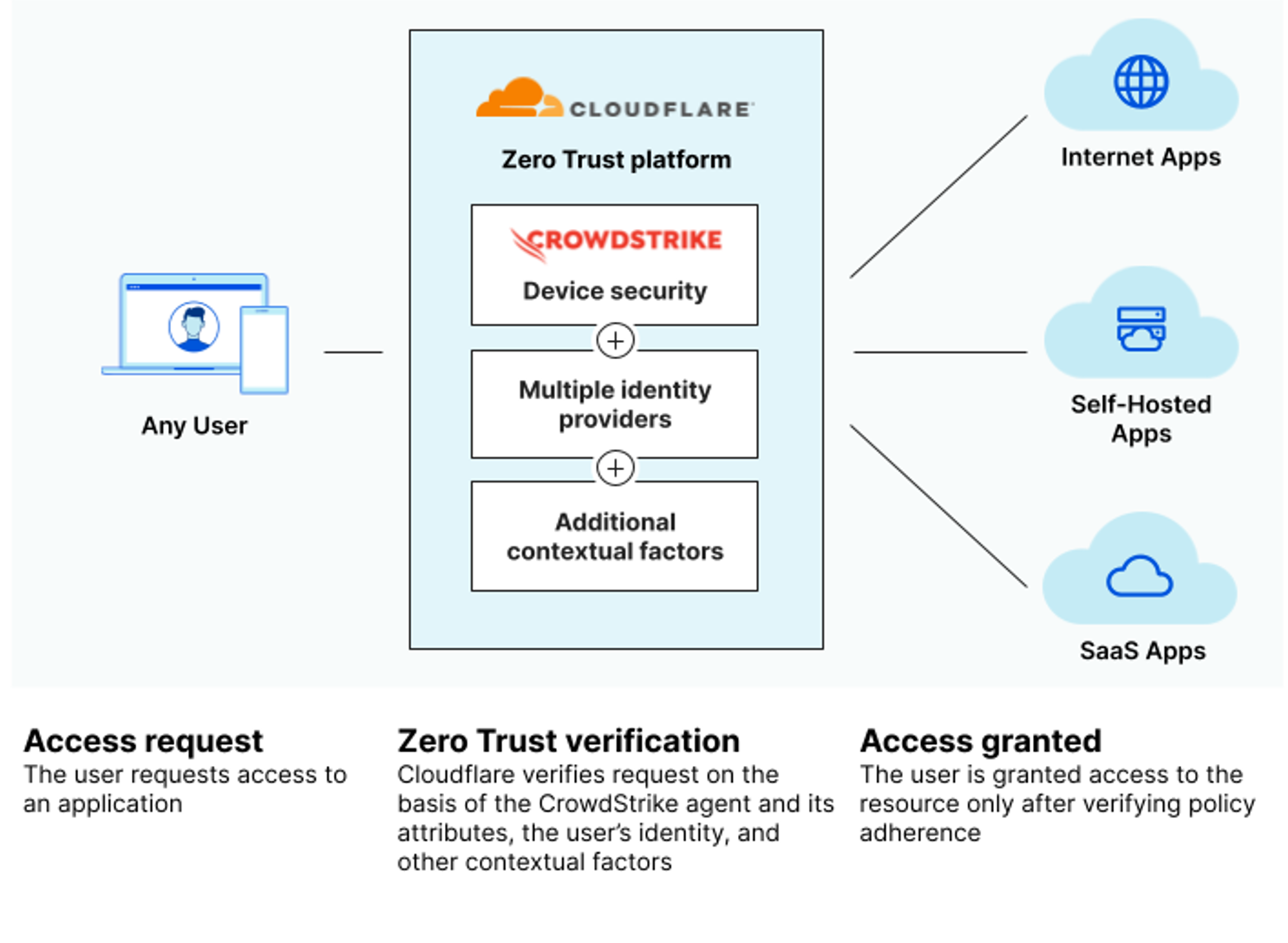 This technology enables customers to identify, investigate and remediate threats quickly, and works to ensure that organizations’ external, public-facing web properties and internal resources are secure. By enforcing device-aware access policies with ease in the Cloudflare dashboard, customers can prevent lateral movement from infected devices, restricting them from accessing sensitive data like account credentials. Security teams can enable conditional access policies that require a minimum Falcon ZTA score to be met before a user is granted access, and if a user does not meet the threshold ZTA score, administrators can choose to block, isolate and run other checks.
This technology enables customers to identify, investigate and remediate threats quickly, and works to ensure that organizations’ external, public-facing web properties and internal resources are secure. By enforcing device-aware access policies with ease in the Cloudflare dashboard, customers can prevent lateral movement from infected devices, restricting them from accessing sensitive data like account credentials. Security teams can enable conditional access policies that require a minimum Falcon ZTA score to be met before a user is granted access, and if a user does not meet the threshold ZTA score, administrators can choose to block, isolate and run other checks.
In addition to these capabilities, organizations can leverage device context from Falcon ZTA to influence various mitigation and protection measures, allowing for dynamic policies that empower Zero Trust. Cloudflare and CrowdStrike’s combined technologies help enhance and expand existing Cloudflare ZTNA and SWG policies, enabling Zero Trust for devices, applications and networks.
Accelerate Detection, Triage and Response with Unparalleled Protection
Zero Trust alongside extended detection and response (XDR) will provide needed tools for organizations to address the gaps in legacy point solutions in order to achieve true end-to-end coverage of their expanding environment. CrowdStrike and Cloudflare’s multiple integrations provide comprehensive security coverage to accelerate detection and response with a Zero Trust framework, allowing organizations to safeguard the distributed workforce and business.
In addition to Cloudflare’s ZTA integration, customers will be able to combine insights from Cloudflare’s global network with enriched telemetry from the Falcon platform through Cloudflare’s partnership in the CrowdXDR Alliance. Security and IT teams can also gain rapid support given CrowdStrike is an incident response partner of Cloudflare, providing support to help bring web properties and networks back online in the event of an incident. The partnership between CrowdStrike and Cloudflare makes it easier for organizations of any size to strengthen their Zero Trust security posture across all endpoints and their entire corporate network to get ahead of adversaries and stop breaches.
CrowdStrike is also proud to join forces with Cloudflare and Ping Identity on the Critical Infrastructure Defense Project to strengthen U.S. cybersecurity for critical infrastructure in light of increased cyber threats. By providing comprehensive, no-cost cyber protections for U.S. hospitals and water and power utilities, this initiative aims to enhance defenses against key areas of enterprise risk and offer step-by-step security measures to defend against cyberattacks.
To learn more about CrowdStrike and Cloudflare, visit the CrowdStrike Store or watch the demo video for more information.
Additional Resources
- View the Cloudflare press release and Cloudflare blog.
- Download the CrowdStrike 2022 Global Threat Report for crucial insights into what security teams need to know — and do — in an increasingly ominous threat landscape.
- Visit the CrowdStrike Zero Trust solution page.
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































