CrowdStrike Falcon® Discover delivers deep asset visibility with no hardware to deploy or manage, providing valuable context for all of your assets. For IT and security teams alike, Falcon Discover is a powerful tool to stop breaches.
The majority of CrowdStrike customers already use Falcon Discover to improve their IT and security posture. To continue providing them with strong protection, we’re continuously enhancing our product to help them tackle some of their most pressing challenges, including reducing the attack surface, investigating and responding to threats, and streamlining IT operations.
We’re announcing two new features that make Falcon Discover even more powerful: Application inventory with integrated vulnerability insights and expanded system insights.
Quick note before we jump into the details: This post is meant to guide users through these new features. If you’re an existing Falcon Discover customer, simply open your Falcon command console and follow along. If you’re curious about how Falcon Discover can help your organization, start your free trial. Note: To enable vulnerability analysis, customers must also license CrowdStrike Falcon® Spotlight.
Application Inventory with Integrated Vulnerability Insights
Falcon Discover currently offers an applications dashboard to help you inventory your applications. Now, we’ve integrated vulnerability insights into this dashboard to give you even more context for controlling applications, enhancing investigations and remediating potential points of compromise.
Try it for yourself: In your Falcon command console, go to Menu > Discover > Applications > Applications dashboards
Here, you’ll see a summary view of every application in your organization, including sanctioned and unsanctioned applications. You can see the total number of applications, the most used and unused applications, applications by vendor, suspicious applications, applications by category and more.
This insight can help you proactively reduce the attack surface. For example, by seeing a list of the most used suspicious applications, you can take action to block certain applications, train users or layer in additional security measures.
This updated applications dashboard can also help you control application license spend. Being able to see which applications your organization is overusing could help you restrict usage, while seeing underused applications can inform renewal decisions.
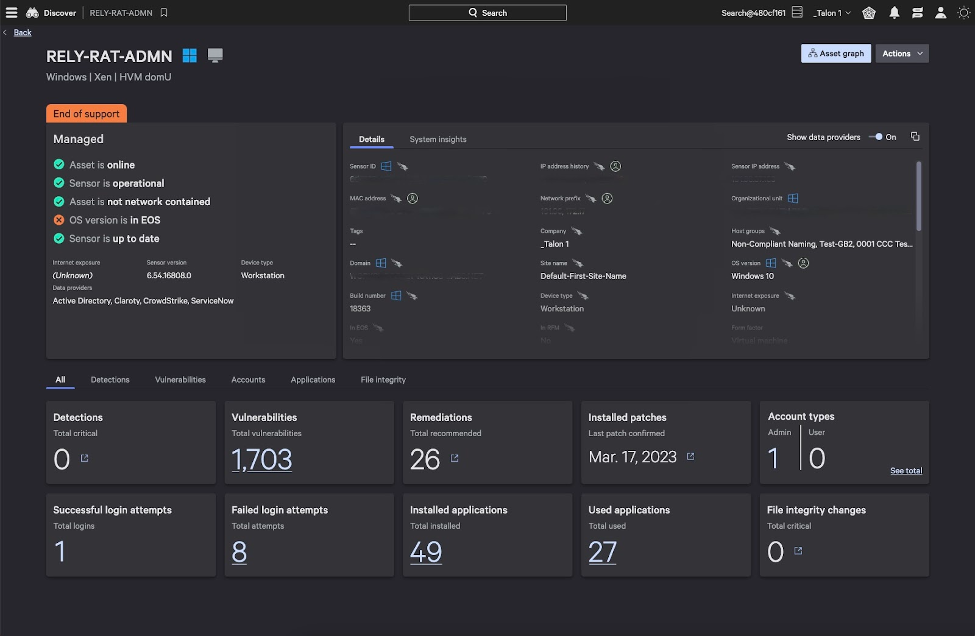
Next, go to Menu > Assets > Managed Assets > select asset > See details page
Here, we’ve integrated application and vulnerability context into a single, easy-to-use view. In this view, you can see which applications are installed on the asset and if any application vulnerabilities are present, a feature powered by Falcon Spotlight’s ExPRT.AI.
This vulnerability context can help you keep tabs on vulnerable applications. By seeing details such as the number of vulnerabilities, installed patches and failed login attempts for a certain application, you can use this insight to spark deeper investigations, if necessary
System Insights
The other exciting update to Falcon Discover is expanded system insights, which provide extensive system information in a single view. Why this level of detail? Three main reasons:
- Managing hardware vulnerabilities
Like software, hardware can have dangerous vulnerabilities. If, for example, there’s a severe vulnerability on an employee’s laptop, the new system insights in Falcon Discover can show you how many and which other assets are tied to the vulnerability to help you expedite remediation.
- Monitoring resource usage
Before installing an application or performing a vulnerability scan, you may want to ensure your assets have the capacity to handle it. The new system insights in Falcon Discover provide a near real-time view of system performance to enable this action. Additionally, ITOps and DevOps teams can use CPU and memory data to reallocate underused compute resources.
- Meeting compliance requirements
Many organizations strive to encrypt their data to help meet compliance requirements and/or adhere to internal best practices. With visibility into drive encryption data in Falcon Discover, you can quickly see how much of your endpoint data is encrypted or not. You can also identify enabled and disabled Windows OS security settings for all assets, helping improve your security posture.
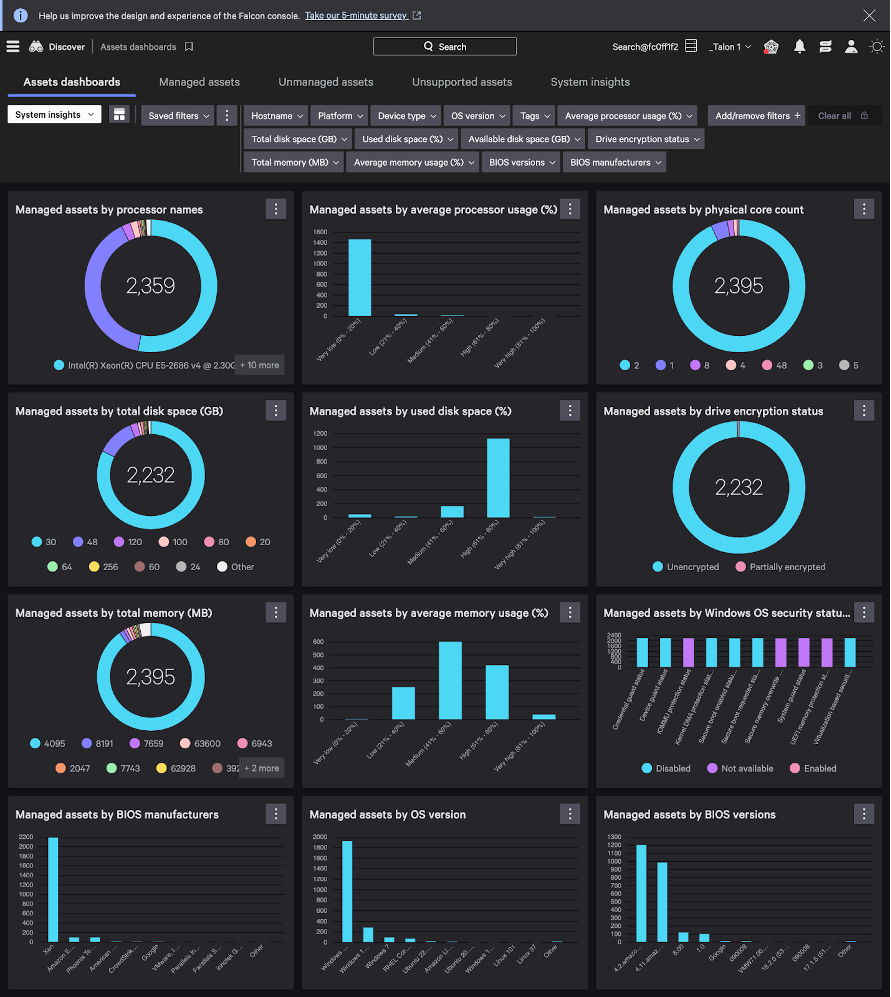
Try it for yourself: In your Falcon command console, go to Assets > System Insights > Managed assets
Here, you can see a dashboard of all system information for managed assets, including hardware. If an employee laptop is affected by a hardware vulnerability, for example, this view would allow you to filter on all assets with the same hardware to quickly see the scope of the vulnerability’s impact. From there, you can take the necessary steps to remediate any risks associated with the vulnerability, such as pushing an update.
The system insights dashboard also allows you to filter on average processor usage. This allows you to verify that adequate performance resources are in place before executing a given task and spin up additional resources for assets near peak usage. Conversely, you can see which assets are being underutilized and could be spun down or retired.
There’s a good reason why more than 70% of CrowdStrike customers use Falcon Discover. With these new features, one of the best IT asset visibility tools in cybersecurity just got better. Explore these new features — and the countless other insights available — to uplevel your IT and security posture today.
Additional Resources
- Visit the Falcon Discover webpage for more information.
- Watch this video to learn more about the new system insights in Falcon Discover.
- Start a free trial of Falcon Discover to uplevel your IT and security posture.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)