As organizations continue to shift to multi-cloud environments and increasingly use cloud services for application development, new challenges emerge that require dramatic changes in the delivery and practice of cybersecurity.
Notably, Gartner predicts that inadequate management of identities, access and privileges will cause 75% of cloud security failures by 2023.1 Though public cloud service providers are working to minimize vulnerabilities and strengthen defenses against cloud threats, the customer is ultimately responsible for securing identities and data. Here lie the challenges for security teams: Cloud-native apps are difficult to secure without a complex set of overlapping tools spanning the development lifecycle, and fragmented cloud security approaches and tools increase complexity, costs and the likelihood of misconfigurations that can lead to breaches. DevSecOps teams often struggle to coordinate the use of these disparate security tools, resulting in blind spots and a limited view of cyber risk.

Identities Are the New Security Perimeter
As the state of cloud infrastructure and use of different architectures constantly evolve, figuring out what or who is in your environment while establishing a baseline for what normal looks like can seem an impossible task. Identity and access management (IAM) for cloud infrastructure is intended to control how cloud identities take action on specific resources, but defining roles and permissions using the principles of least privilege is challenging in hybrid environments.Key challenges include:
- The overwhelming number of machine identities, which outnumber human identities, leading to thousands of identities and resources to manage.
- Limited visibility and inconsistent entitlements across complex hybrid and multi-cloud environments make enforcing least-privileged access difficult.
- Unique IAM policy models and taxonomy across public cloud service providers (CSPs).
cloud accounts and resources. The CrowdStrike Falcon® platform sets the new standard in cloud security and identity protection. Watch this demo to see the Falcon platform in action.
CrowdStrike Introduces CIEM for AWS and Azure to Address New Requirements for Securing Identities Across Hybrid Environments
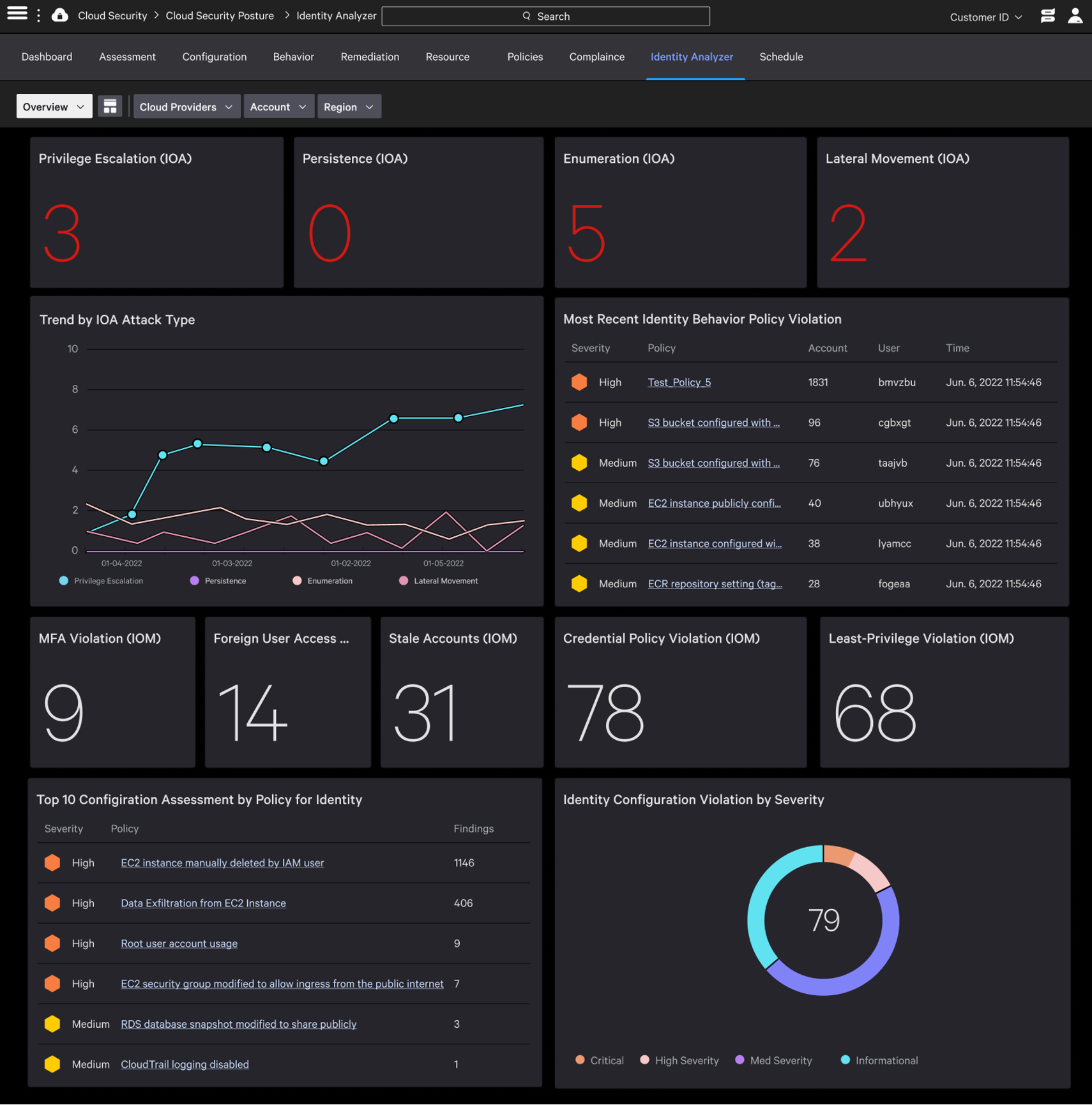
CrowdStrike Falcon® Cloud Security, CrowdStrike’s market-leading cloud security posture management (CSPM) solution, now provides integrated CIEM capabilities that deliver a single-source-of-truth for monitoring, discovering and securing identities across multi-cloud environments in a single platform. Security and identity teams can prevent identity-based threats resulting from improperly configured cloud entitlements across AWS and Azure. Uniquely, as part of CrowdStrike’s broader CNAPP offering, we deliver comprehensive cloud security, combining agent-based and agentless protection in a single, unified platform experience. With Falcon Cloud Security you gain access to the full inventory of permissions, detect overly permissive accounts, continuously monitor activity and ensure least privilege enforcement.What’s New
Falcon Cloud Security now enables you to: Unify visibility and least-privilege enforcement in public and multi-cloud environments
- Access a single source of truth: Get up and running in minutes and access a single dashboard for all cloud assets, identities and security configurations.
- Simplify privileged access management and policy enforcement: Manage and enforce identities and permissions across AWS and Azure.
- Identify and investigate cloud entitlements: Detect risky permissions, and remove unwanted access to cloud resources including identity misconfigurations and cloud entitlements to achieve least-privilege.
- Prevent identity-based threats at scale: Secure cloud identities and permissions, detect account compromises, prevent identity misconfigurations, stolen access keys, insider threats and malicious activity.
- Secure Azure Active Directory: Ensure Azure AD groups, users and apps have the correct permissions using new Identity Analyzer reports.
- One-click remediation testing: Simulate remediation tactics to understand outcomes and ensure confidence by performing a dry run prior to deployment.
- Predict and prevent modern threats: Ensure real-time cloud workload protection via CrowdStrike Threat Graph®, which provides full visibility of attacks and automatically prevents threats in real time for any hybrid environment across CrowdStrike’s global customer base.
- Access enriched threat intelligence to supercharge investigations: Get deeper context for faster investigation and more effective response for cloud-based attacks with a visual representation of relationships across account roles, workloads and APIs.
- Accelerate response: Arm your responders in real time via the Falcon platform, empowering incident responders to focus on what matters most, understand threats and act decisively to stop cloud breaches.
- See and secure cloud identities and entitlements: Gain complete visibility into cloud resources, and understand the relationships between access and permissions automatically.
- Optimize cloud implementations: Perform real-time point queries for rapid response, as well as broader analytical queries for asset management and security posture optimization.
- Mitigate risks across the attack surface: Get 360-degree visibility into your organization’s assets and their interdependencies across hosts, configurations, identities and applications.
Additional Resources
- For an in-depth examination of how attackers target the cloud, download “Protectors of the Cloud: Combating the Rise in Threats to Cloud Environments.”
- Learn how you can stop cloud breaches with CrowdStrike unified cloud security posture management and breach prevention for multi-cloud and hybrid environments — all in one lightweight platform.
- Learn more about how Falcon Cloud Security
enables organizations to build, run and secure cloud-native applications with speed and confidence. - See if a managed solution is right for you. Find out about Falcon Cloud Workload Protection Complete: Managed Detection and Response for Cloud Workloads.
Endnotes
- Gartner, Managing Privileged Access in Cloud Infrastructure, Paul Mezzera, Refreshed December 7, 2021, Published June 9, 2020. (GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.)





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)