- The MITRE Engenuity Center for Threat-Informed Defense created a public adversary emulation library in 2020 as adversary emulation plans comprising MITRE ATT&CK® tactics and techniques are essential to test defenses against specific adversaries
- The growing collection of public emulation plans has remained Windows-focused, which has left a coverage gap as adversaries target macOS and Linux systems
- The Center for Threat-Informed Defense, working with research partners including CrowdStrike, created the first public adversary emulation plan combining macOS and Linux for full-scope purple teaming
The MITRE ATT&CK framework, a key resource for helping organizations defend against cyberattacks, is critical to advancing cybersecurity research. The MITRE Engenuity Center for Threat-Informed Defense’s public library of adversary-specific emulation plans has become a valuable component of the ATT&CK framework. Each plan in the library provides comprehensive ATT&CK tactics and techniques employed by well-known adversaries.
These emulation plans allow organizations to evaluate their defenses against real-world cyberattacks. The library offers full emulation plans for a range of nation-state and criminal adversaries, including Turla, WIZARD SPIDER, Sandworm and OceanLotus, along with a dozen micro emulation plans that provide coverage for common behaviors used by multiple adversaries. However, these emulation plans have historically focused on attacks against Windows-based systems. The OceanLotus project was developed to create the first public adversary emulation plan that combines macOS and Linux tradecraft.
Both operating systems have become widely used in enterprise settings — as a result, they have become adversary targets. CrowdStrike researchers have been closely tracking and analyzing macOS threats. Linux distributions, at the heart of much of today’s cloud infrastructure, are used to power many enterprise servers — and Linux-based malware has been on the rise. Here, we discuss the OceanLotus project and some of the details of this adversary emulation plan.
Details of the Project
MITRE chose OceanLotus — the Vietnam-based adversary known by CrowdStrike as OCEAN BUFFALO — to be the subject of the first combined macOS and Linux public adversary emulation plan for multiple reasons:
- OceanLotus has a history of attacking macOS and Linux environments
- OceanLotus attacks are unique enough to be identifiable but they utilize enough clearly defined ATT&CK techniques for emulation
- The group has been active since 2012, and there is a large volume of open-source reporting on the group’s repeatable behaviors and post-exploit behavior, including a documented history of watering hole attacks targeting multiple private sector industries, foreign governments, journalists and political activists across multiple countries, including the U.S., Australia, Germany, the Philippines, Cambodia, Laos and Vietnam
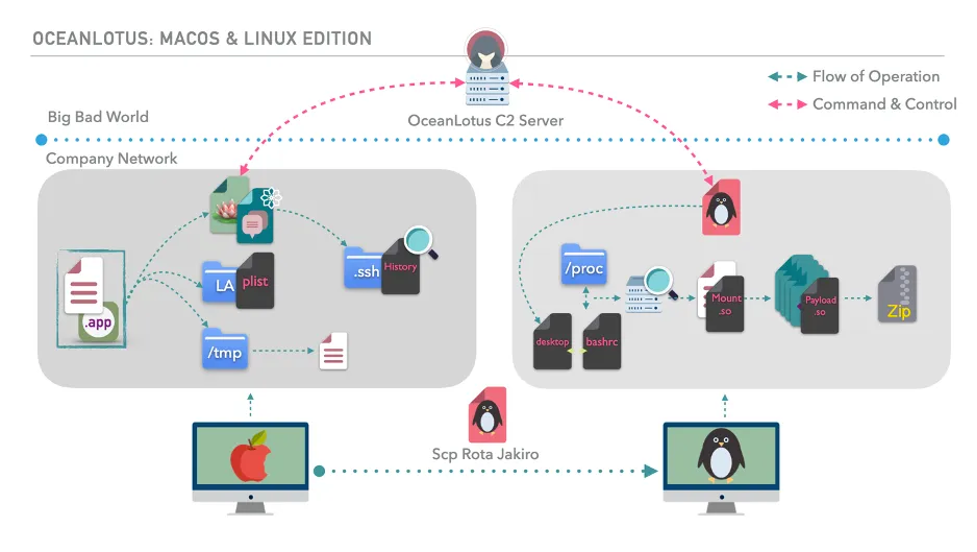 Figure 1. OceanLotus emulation plan operational flow (copyright: Center for Threat-Informed Defense)
Figure 1. OceanLotus emulation plan operational flow (copyright: Center for Threat-Informed Defense)
The emulated attack scenario began with the download of a macOS application bundle disguised as a Microsoft Word document from an OceanLotus-compromised website. Double-clicking the malicious bundle results in a bash script dropping three files to disk, and one of these establishes a connection to an OceanLotus command-and-control (C2) server. From there, OceanLotus is able to perform discovery on remote services, including SSH. When the target logs into a Linux server using SSH, OceanLotus gains access and copies a backdoor to the Linux host. Executing the backdoor establishes persistence, and OceanLotus performs discovery techniques and exfiltrates files of interest.
By undergoing this emulated scenario, organizations can evaluate how their defenses would perform against an Ocean Lotus campaign targeting environments running macOS and Linux.
What the OceanLotus Project Accomplished
This project produced an emulation plan for OceanLotus that starts on macOS and ends on a Linux host with explicit defensive telemetry for a full-scope purple-teaming perspective. This is an industry first and hopefully sets the stage for future public emulation plans that encompass the macOS and Linux operating systems.
Enhancing the coverage of public adversary emulation plans to include versions targeting macOS and Linux will allow organizations to test previously inaccessible environments using the MITRE ATT&CK framework. This will strengthen their defenses against cyberattacks. The addition of macOS and Linux public adversary emulation plans will also advance the ability of cybersecurity providers and independent testing organizations to evaluate and improve products.
If you want to learn more about the technical details of the OceanLotus project, the Center for Threat-Informed Defense has published a deep-dive post.
CrowdStrike’s Commitment to Cybersecurity Research and Innovation
Our relentless focus on innovation can be seen in results like the perfect score awarded to the AI-native CrowdStrike Falcon® platform in the recent MITRE Engenuity ATT&CK Evaluations: Enterprise. The Falcon platform achieved 100% protection, 100% visibility and 100% analytic detection across all steps in all 13 scenarios, stopping the sophisticated VENOMOUS BEAR (Turla) adversary at every stage of an attack.
In addition to ensuring the Falcon platform delivers best-in-class protection, CrowdStrike is strongly committed to furthering research and innovation that benefit the entire cybersecurity industry.
CrowdStrike researchers and threat analysts are tracking adversaries’ every movement, ensuring the Falcon platform protects against even the most sophisticated tradecraft. Many of our findings are published in public forums, advancing global defenses against the latest adversary tactics and malware. Our research also benefits independent testing organizations, helping to ensure their testing tools and product evaluations include coverage for the most recently discovered cybersecurity threats.
As a Research Partner for the Center for Threat-Informed Defense, CrowdStrike actively participates in cybersecurity research projects sponsored by this nonprofit R&D organization. The OceanLotus project is the latest in a series that included TRAM II and Summiting the Pyramid in 2023.
Additional Resources
- Learn more about how the Falcon platform extends protection for macOS here.
- Learn how you can stop cloud breaches with CrowdStrike unified cloud security for multi-cloud and hybrid environments — all in one lightweight platform.
- Read about adversaries tracked by CrowdStrike in the CrowdStrike 2023 Global Threat report.
- Test CrowdStrike next-generation antivirus (NGAV) for yourself. Start your free trial of CrowdStrike Falcon® Prevent today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































