Earlier this year, CrowdStrike released Falcon Orchestrator as a contribution to the open source community. By leveraging the robust Falcon Connect API ecosystem, organizations can easily extend the Falcon platform by integrating with other internal data sources for context enrichment and execution of security response workflows. The initial release of Orchestrator provided a variety of basic response features geared to assist organizations with triage for security events.
The next iteration of Orchestrator has now been released on the project’s GitHub page. 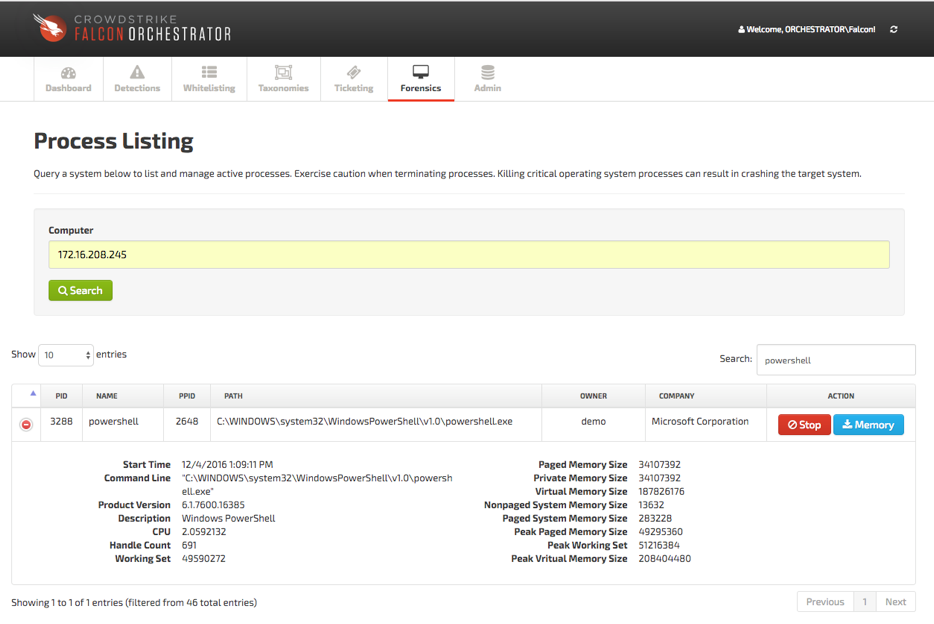
It builds on the PowerShell-based response capabilities to provide a number of new response features focused on remediation:
- Process Management: A listing of active processes provides quick insight into activity on the target endpoint. This listing serves as the basis for performing subsequent activities on active processes.
- Termination: When a malicious or hijacked process is identified, users can now leverage Orchestrator to terminate it.
- Memory Dump: When a suspicious process is flagged, a common triage workflow involves capturing memory for post analysis using a framework such as volatility. For this feature, Orchestrator leverages the Out-Minidump script from the exceptional PowerSploit project.
This allows a full process memory minidump of the selected process.

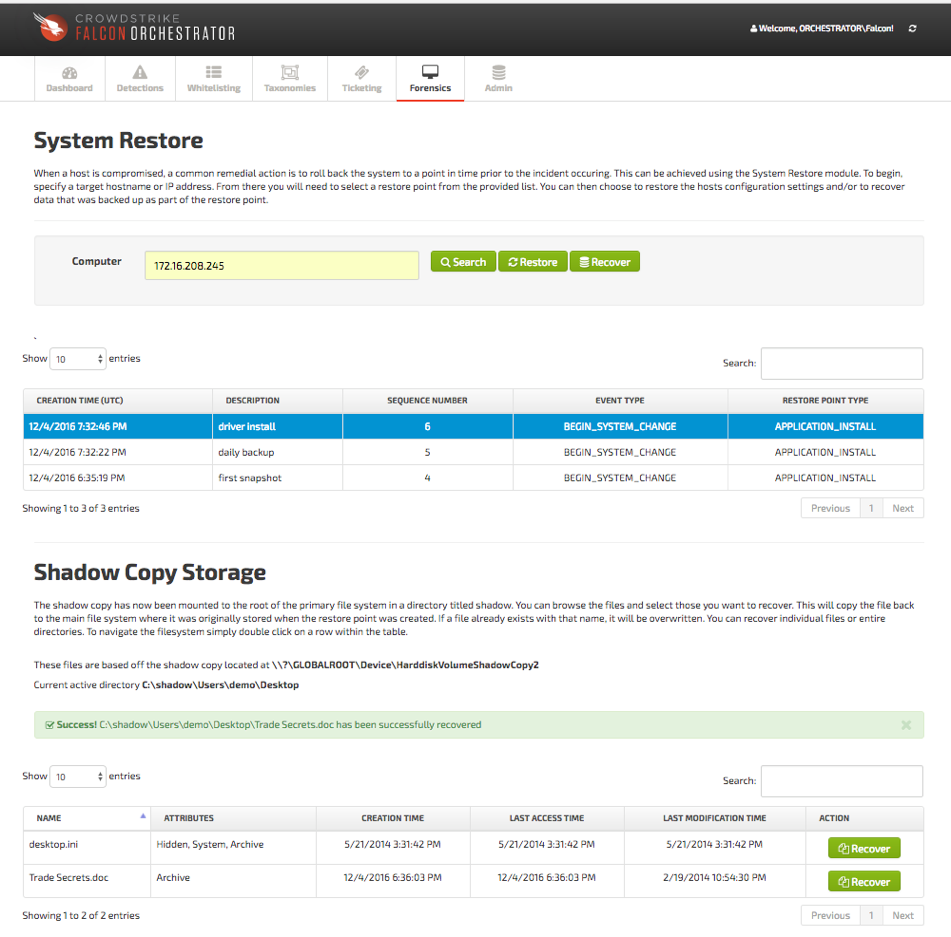
- System Restore: Targeted removal of specific artifacts (processes, registry keys, files, etc.) is a minimally disruptive approach to remediation. Under some circumstances however, it can also be an arduous and complex task, especially when dealing with attacks that inject into various processes. System restore is a simplistic approach to reverting the endpoint’s configuration settings to a pre-compromise state. By leveraging Windows restore point, Orchestrator now provides a utility for users to restore from backups.
- Data Recovery: Falcon Host provides a high-fidelity prevention Indicator of Attack (IOA) that will protect the volume shadow copies on the endpoint from being deleted by an attacker. This ensures that users can still recover data files in the event they become encrypted by ransomware or are corrupted in any way. With the data recovery feature, users can select the target restore point, mount the associated volume shadow copy and select directories or files to recover.

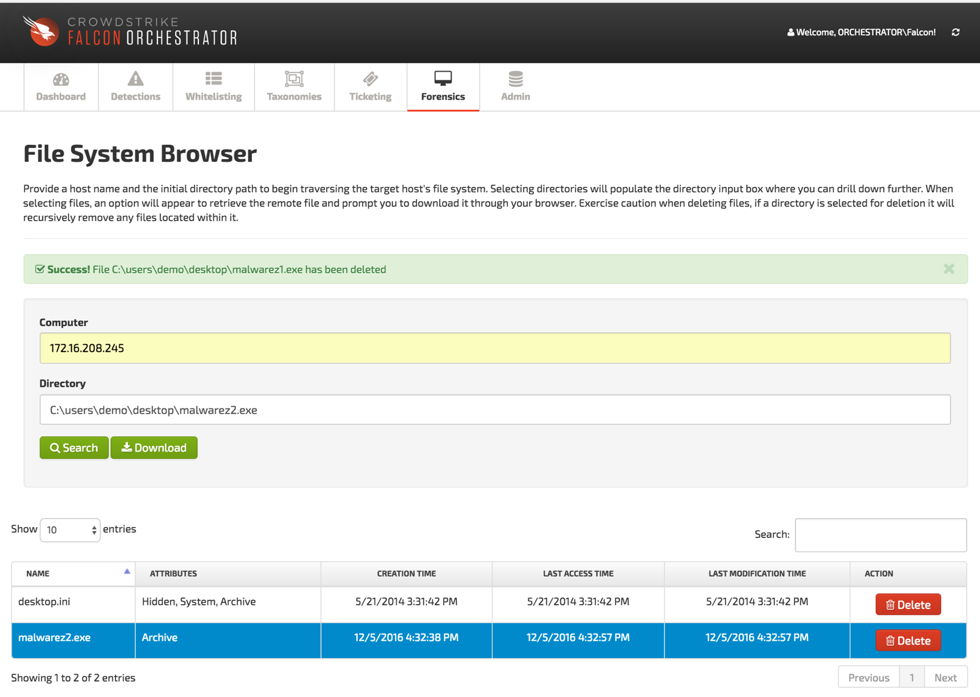
- File Deletion: With the visibility provided by Falcon Host, users can easily identify malicious file artifacts that should be removed from an endpoint as part of a targeted remediation. The extension of the file system browser now allows users to selectively remove entire directories or specific files.

Customers can take advantage of powerful workflow automation and case management capabilities, as well as an extendable wide range of security forensics and remediation actions that work in conjunction with and complement the capabilities of CrowdStrike Falcon® Host. So take Falcon Orchestrator for a spin if you haven’t already done so and let us know your feedback!






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































