- As a global cybersecurity industry leader and a Research Partner for the MITRE Engenuity Center for Threat-Informed Defense, CrowdStrike provided expertise and thought leadership to two of the Center for Threat-Informed Defense’s latest research projects.
- The Sensor Mappings to ATT&CK project aimed to map sensors and other data sources to the MITRE ATT&CK® framework techniques so SOCs know which tools and capabilities to check for the use of TTPs that would indicate their environment is under attack.
- The Insider Threat TTP Knowledge Base Version 2 project sought to enhance a repository of tactics, techniques and procedures (TTPs) used by insider attackers by including nontechnical indicators, plus their respective mitigations, helping organizations prevent and defend against insider cybersecurity threats.
Organizations worldwide rely on the MITRE ATT&CK framework as a critical resource for defending against cyberattacks. The MITRE ATT&CK framework is also a key tool for advancing threat research in the cybersecurity industry. However, one of the challenges in using the MITRE ATT&CK framework is mapping the output from logs, sensors and other tools as ATT&CK data sources in the framework. As a result, it’s not always clear to SOCs how to use the tools and services at their disposal to provide visibility into specific adversary behaviors or threats that put their environment at risk.
The MITRE Engenuity Center for Threat-Informed Defense launched the Sensor Mappings to ATT&CK project to address gaps in this area by mapping sensor events to ATT&CK data sources. When complete, this effort will help SOCs understand which of their tools and/or system capabilities they should monitor to spot specific ATT&CK techniques that adversaries use, as well as identify which tools and/or system capabilities the SOC should acquire to address any gaps in coverage. Ultimately, the Sensor Mappings to ATT&CK project will make the MITRE ATT&CK framework even more valuable.
Sometimes, the threat of a cyberattack comes from within an organization rather than from outside adversaries. Insider threats pose a unique challenge to SOCs. They are often difficult to detect — the attacker is already within the network and possesses valid, active credentials to critical resources — and they can do considerable damage. The Center for Threat-Informed Defense’s initial Insider Threat TTP Knowledge Base project identified the most commonly used TTPs for insider attacks across a wide range of industries for inclusion in a repository. The project also included mitigations for these TTPs, providing a method for organizations to take the actions needed to defend their systems against insider threats.
In the recently completed Version 2 of this project, the TTPs were expanded beyond the technical mechanisms used by insiders on IT systems that were identified in Version 1 to include nontechnical indicators. These observable human indicators (OHIs) include facts about a person or their role that might elevate their risk of being an insider threat.
CrowdStrike was a participant in both of these projects — the latest example of our commitment to cybersecurity industry research.
Sensor Mappings to ATT&CK
There are several key deliverables for the Sensor Mappings to ATT&CK project, which has the ultimate goal of extending ATT&CK data sources to link techniques to tools, capabilities and data sources such as sensors that can provide visibility. Achieving this goal will allow SOCs to better understand their current defensive capabilities so they can fill any gaps (through analytics, tools or other means) and more effectively search for threats.
- Methodology: Create a document and specification that describes how to map system logs, sensors and capabilities to ATT&CK data sources.
- Data Model: Create a new data model or extend existing models to include data source, data components, data elements, relationships and event/telemetry data.
- Mappings: Conform to the specification defined in Methodology, including a resource that will host the mappings for the purposes of review, download and analysis of coverage.
- Usability: Identify tools, documentation and other resources.
- Logs, Sensors and Capabilities: Include coverage of Sysmon (all events), Windows Event Log (any security-related events), Osquery, auditd, Zeek and AWS CloudTrail.
Mapping: Using Data Sources, Data Components, Data Elements, Relationships and Event/Telemetry Data to Detect Specific ATT&CK TTPs
The model below shows how the domains are mapped together through data sources, data components, data elements, relationships and event/telemetry data.
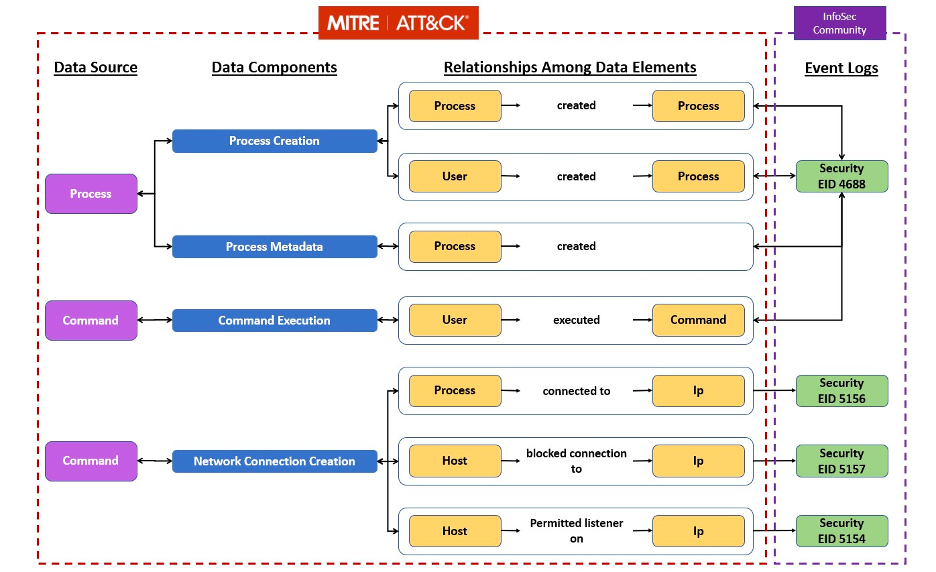
The Sensor Mappings to ATT&CK project includes the creation of a STIX 2 representation of the mappings (providing ease of use for teams that currently use STIX) as well as a command line interface tool.
Insider Threat TTP Knowledge Base Version 2
Insider threats can be employees, former employees, contractors, partners, service providers or anyone who has knowledge about and/or access to an organization’s computer systems and network. Insider threats are particularly challenging for SOCs to detect and defend against. Security solutions are primarily focused on detecting and defending against cyberattacks launched by external adversaries, so what might otherwise be suspicious behavior from within is often assumed to be legitimate use — if it’s detected at all. In addition, insiders often have the advantage of knowing details about the system and network settings and security measures. They may even have knowledge about exploitable security shortcomings or vulnerabilities.
CrowdStrike was a big part of the initial Insider Threat TTP Knowledge Base project, contributing data and expertise (you can read about that effort here). In Version 2 of the project, the primary deliverable is to expand the scope of the original project to include nontechnical OHIs, including:
- Subject with elevated privileges
- Monitoring status of subject
- Telework status of subject
- Performance improvement plan required
- Turnover rate of subject’s role
- Time at company
- Management level
- Seniority of subject
- Government security clearance
CrowdStrike researchers provided insider threat expertise and anonymized instances of insider threats for aggregation by the Center for Threat-Informed Defense team. This data allowed the team to determine the most common tactics and techniques that are employed by inside actors. In addition, our researchers helped define the mitigations for the identified insider threats and provided thought leadership on topics covered by this research, including the concept of OHIs.
Contributing to Center for Threat-Informed Defense Projects: CrowdStrike’s Ongoing Commitment to Cybersecurity Research and Innovation
CrowdStrike’s commitment to cybersecurity research and innovation is reflected in the best-in-class protection of the CrowdStrike Falcon® XDR platform.
Adversaries never stop their relentless march toward more sophisticated tradecraft, but CrowdStrike researchers and threat analysts are always watching and hunting for novel attack techniques — including insider threats. CrowdStrike researchers publish many of their findings, sharing information in the name of improving defenses globally against dangerous new adversary tactics and previously unknown malware. The findings of CrowdStrike researchers also benefit independent cybersecurity testing organizations, which are able to update their tools and evaluation processes to reflect the latest threats and tactics.
Our commitment to research extends to being a Research Partner at the MITRE Engenuity Center for Threat-Informed Defense. The Center for Threat-Informed Defense’s mission — “to advance the state of the art and the state of the practice in threat-informed defense globally” — is an important one that CrowdStike is proud to support. CrowdStrike’s participation in the Center for Threat-Informed Defense’s Sensor Mappings to ATT&CK and Insider Threat TTP Knowledge Base projects capped a 12-month period in which CrowdStrike participated in four major research initiatives with the Center for Threat-Informed Defense. CrowdStrike looks forward to continuing to provide expertise and thought leadership to the Center for Threat-Informed Defense.
You can learn more about the Center for Threat-Informed Defense’s Sensor Mappings to ATT&CK project here and the Insider Threat TTP Knowledge Base Version 2 project here.
Additional Resources
- Learn how you can stop cloud breaches with CrowdStrike unified cloud security for multi-cloud and hybrid environments — all in one lightweight platform.
- Read about adversaries tracked by CrowdStrike in the CrowdStrike 2024 Global Threat Report.
- Read about the types of insider threats and how to detect them here.
- Test CrowdStrike next-generation antivirus for yourself. Start your free trial of CrowdStrike® Falcon Prevent™ today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































