Update: CrowdStrike Completes Acquisition of SecureCircle — read more here.
In today’s enterprise, everything flows through the endpoint. Users and identities are authenticated through the endpoint, while code repositories, cloud workloads, SaaS applications and files are accessed through the endpoint. As a result, enterprise data flows through and resides on countless devices. This is why the modern endpoint is now the epicenter of enterprise risk — it’s the gateway to a company's most critical assets and most sensitive data.
At the same time, the move to a distributed workforce has created a massive new attack surface that adversaries exploit. As employees operate across different networks from different locations, maintaining visibility and securing endpoints from attacks is increasingly complex.
As a result, data is increasingly at risk — an infiltration on one endpoint can put an entire company in jeopardy of a massive data breach.
Despite the growing risk to data via the endpoint, there has been very little innovation in the data protection market over the years. Practically every customer conversation I have on data protection revolves around the failures of data loss prevention (DLP) technology and how it’s become a black hole with little return when it comes to security budgets.
For too long, data protection has suffered from a lack of innovation and a failure to evolve with the modern enterprise.
Let’s be clear: like endpoint security, data protection should be frictionless and easy to deploy.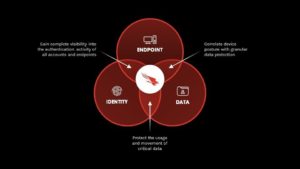 Here at CrowdStrike, we continue to redefine security for the cloud era by focusing on the greatest source of enterprise risk — the endpoint. And with the acquisition of SecureCircle, we stay true to this mantra as CrowdStrike natively enforces Zero Trust protection at the device layer, the identity layer, and with SecureCircle technology will do so at the data layer. All delivered through CrowdStrike’s lightweight Falcon agent on the endpoint.
This innovative approach will put the power of data protection back into the hands of CrowdStrike customers, giving them visibility and control for how data is downloaded, used and shared across the organization, while simultaneously enforcing encryption in all three states: in transit, at rest and in use.
Moreover, after we combine SecureCircle’s technology with CrowdStrike Zero Trust Assessments and Falcon Zero Trust, customers will gain even more fine-grained visibility and control through flexible, user-based data access management and policy enforcement driven by CrowdStrike’s advanced Zero Trust scoring system. Ultimately, customers gain continuous risk monitoring to detect and respond to threats, whether they manifest at the device, identity or data layer.
At CrowdStrike, we did the hard work early on to develop a cloud-native platform that addresses today’s toughest security challenge. With SecureCircle, we saw an aligned vision for how data security should be delivered similar to everything we bring to market: security solutions that are easy to deploy, easy to manage and highly effective without interference on good user behavior.
To learn more about today’s news and CrowdStrike’s Zero Trust capabilities, visit our website and the CrowdStrike Zero Trust solution page.
*Source: This is a CrowdStrike estimate based on IDC data. IDC, Worldwide Data Loss Technologies Forecast, 2021–2025: Digital Transformation Tools Applied to the Data Protection Task, October 2021 Doc # #US48288521 and IDC, Worldwide Endpoint Encryption and Key Management Infrastructure Software Forecast, 2019–2023, May 2019 Doc # US44773019. CrowdStrike has not independently verified, and makes no representations as to the adequacy, fairness, accuracy or completeness of, any information obtained from these studies.
Here at CrowdStrike, we continue to redefine security for the cloud era by focusing on the greatest source of enterprise risk — the endpoint. And with the acquisition of SecureCircle, we stay true to this mantra as CrowdStrike natively enforces Zero Trust protection at the device layer, the identity layer, and with SecureCircle technology will do so at the data layer. All delivered through CrowdStrike’s lightweight Falcon agent on the endpoint.
This innovative approach will put the power of data protection back into the hands of CrowdStrike customers, giving them visibility and control for how data is downloaded, used and shared across the organization, while simultaneously enforcing encryption in all three states: in transit, at rest and in use.
Moreover, after we combine SecureCircle’s technology with CrowdStrike Zero Trust Assessments and Falcon Zero Trust, customers will gain even more fine-grained visibility and control through flexible, user-based data access management and policy enforcement driven by CrowdStrike’s advanced Zero Trust scoring system. Ultimately, customers gain continuous risk monitoring to detect and respond to threats, whether they manifest at the device, identity or data layer.
At CrowdStrike, we did the hard work early on to develop a cloud-native platform that addresses today’s toughest security challenge. With SecureCircle, we saw an aligned vision for how data security should be delivered similar to everything we bring to market: security solutions that are easy to deploy, easy to manage and highly effective without interference on good user behavior.
To learn more about today’s news and CrowdStrike’s Zero Trust capabilities, visit our website and the CrowdStrike Zero Trust solution page.
*Source: This is a CrowdStrike estimate based on IDC data. IDC, Worldwide Data Loss Technologies Forecast, 2021–2025: Digital Transformation Tools Applied to the Data Protection Task, October 2021 Doc # #US48288521 and IDC, Worldwide Endpoint Encryption and Key Management Infrastructure Software Forecast, 2019–2023, May 2019 Doc # US44773019. CrowdStrike has not independently verified, and makes no representations as to the adequacy, fairness, accuracy or completeness of, any information obtained from these studies.
It should be fast. Most important of all, it should be completely invisible to the end-user. This is why I’m pleased to announce that CrowdStrike has agreed to acquire SecureCircle to modernize data protection and secure data on, from and to the endpoint. We are acquiring SecureCircle in order to allow customers to enforce security at the device level, the identity level and the data level.
Modernizing Data Protection to Move Beyond DLP’s Failures
Despite the critical need for data protection to be part of any security strategy today, legacy data loss prevention (DLP) tools have failed to rise to the challenge. As a result, security and risk teams struggle with rampant insider threats (both inadvertent and malicious), resource-intensive policy and control management, and a lagging workforce experience hampered by these burdensome and opaque rule sets. To make matters worse, the global pandemic that forced organizations worldwide to adapt to remote working has further amplified the shortcomings of traditional DLP and escalated related threats. Security leaders are spending billions on DLP technologies and gaining little security value in return. The total addressable market for DLP and related technologies is estimated to be approximately $3 billion USD in 2021*. In large part, DLP solutions come up short today because they only block or encrypt data when it’s leaving the endpoint and only when triggered by a complex set of pre-configured rules and behavioral parameters. Attackers are well-aware of DLP weaknesses, and our advanced threat intelligence shows adversaries continually refine their tradecraft to build specific malware and ransomware to take advantage of them. DLP is clearly broken. We need a new model for comprehensive, frictionless data protection that secures data as soon as it lands on the endpoint.Zero Trust Control: Device, Identity and Now Data
Through this acquisition, CrowdStrike will enforce SaaS-based Zero Trust security to protect data on, from and to the endpoint. Data protection is only truly possible when it’s secured persistently from the beginning, and wherever else it goes. Here at CrowdStrike, we continue to redefine security for the cloud era by focusing on the greatest source of enterprise risk — the endpoint. And with the acquisition of SecureCircle, we stay true to this mantra as CrowdStrike natively enforces Zero Trust protection at the device layer, the identity layer, and with SecureCircle technology will do so at the data layer. All delivered through CrowdStrike’s lightweight Falcon agent on the endpoint.
This innovative approach will put the power of data protection back into the hands of CrowdStrike customers, giving them visibility and control for how data is downloaded, used and shared across the organization, while simultaneously enforcing encryption in all three states: in transit, at rest and in use.
Moreover, after we combine SecureCircle’s technology with CrowdStrike Zero Trust Assessments and Falcon Zero Trust, customers will gain even more fine-grained visibility and control through flexible, user-based data access management and policy enforcement driven by CrowdStrike’s advanced Zero Trust scoring system. Ultimately, customers gain continuous risk monitoring to detect and respond to threats, whether they manifest at the device, identity or data layer.
At CrowdStrike, we did the hard work early on to develop a cloud-native platform that addresses today’s toughest security challenge. With SecureCircle, we saw an aligned vision for how data security should be delivered similar to everything we bring to market: security solutions that are easy to deploy, easy to manage and highly effective without interference on good user behavior.
To learn more about today’s news and CrowdStrike’s Zero Trust capabilities, visit our website and the CrowdStrike Zero Trust solution page.
*Source: This is a CrowdStrike estimate based on IDC data. IDC, Worldwide Data Loss Technologies Forecast, 2021–2025: Digital Transformation Tools Applied to the Data Protection Task, October 2021 Doc # #US48288521 and IDC, Worldwide Endpoint Encryption and Key Management Infrastructure Software Forecast, 2019–2023, May 2019 Doc # US44773019. CrowdStrike has not independently verified, and makes no representations as to the adequacy, fairness, accuracy or completeness of, any information obtained from these studies.
Here at CrowdStrike, we continue to redefine security for the cloud era by focusing on the greatest source of enterprise risk — the endpoint. And with the acquisition of SecureCircle, we stay true to this mantra as CrowdStrike natively enforces Zero Trust protection at the device layer, the identity layer, and with SecureCircle technology will do so at the data layer. All delivered through CrowdStrike’s lightweight Falcon agent on the endpoint.
This innovative approach will put the power of data protection back into the hands of CrowdStrike customers, giving them visibility and control for how data is downloaded, used and shared across the organization, while simultaneously enforcing encryption in all three states: in transit, at rest and in use.
Moreover, after we combine SecureCircle’s technology with CrowdStrike Zero Trust Assessments and Falcon Zero Trust, customers will gain even more fine-grained visibility and control through flexible, user-based data access management and policy enforcement driven by CrowdStrike’s advanced Zero Trust scoring system. Ultimately, customers gain continuous risk monitoring to detect and respond to threats, whether they manifest at the device, identity or data layer.
At CrowdStrike, we did the hard work early on to develop a cloud-native platform that addresses today’s toughest security challenge. With SecureCircle, we saw an aligned vision for how data security should be delivered similar to everything we bring to market: security solutions that are easy to deploy, easy to manage and highly effective without interference on good user behavior.
To learn more about today’s news and CrowdStrike’s Zero Trust capabilities, visit our website and the CrowdStrike Zero Trust solution page.
*Source: This is a CrowdStrike estimate based on IDC data. IDC, Worldwide Data Loss Technologies Forecast, 2021–2025: Digital Transformation Tools Applied to the Data Protection Task, October 2021 Doc # #US48288521 and IDC, Worldwide Endpoint Encryption and Key Management Infrastructure Software Forecast, 2019–2023, May 2019 Doc # US44773019. CrowdStrike has not independently verified, and makes no representations as to the adequacy, fairness, accuracy or completeness of, any information obtained from these studies.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)











































