This blog was originally published on July 14, 2020.
On July 14, 2020 Patch Tuesday, Microsoft released a patch for CVE-2020-1267, an important vulnerability in the Active Directory (AD) identity store discovered by CrowdStrike (formerly Preempt) Research Labs. This discovered vulnerability in AD could lead to denial-of-service attacks against domains with unpatched domain controllers or worst case, to a full domain compromise.
The vulnerability is an integer overflow that exists in both the NTLM and Kerberos parsing codes. It occurs when the parsing of a specially-crafted Privileged Attribute Certificate (PAC) structure leads to a heap overflow. Such an overflow can be used to create a denial-of-service attack, and could be exploited to remotely execute code. (We have yet not pursued this path).
The vulnerability was classified by Microsoft as a denial of service vulnerability with a CVSS score of 4.9.
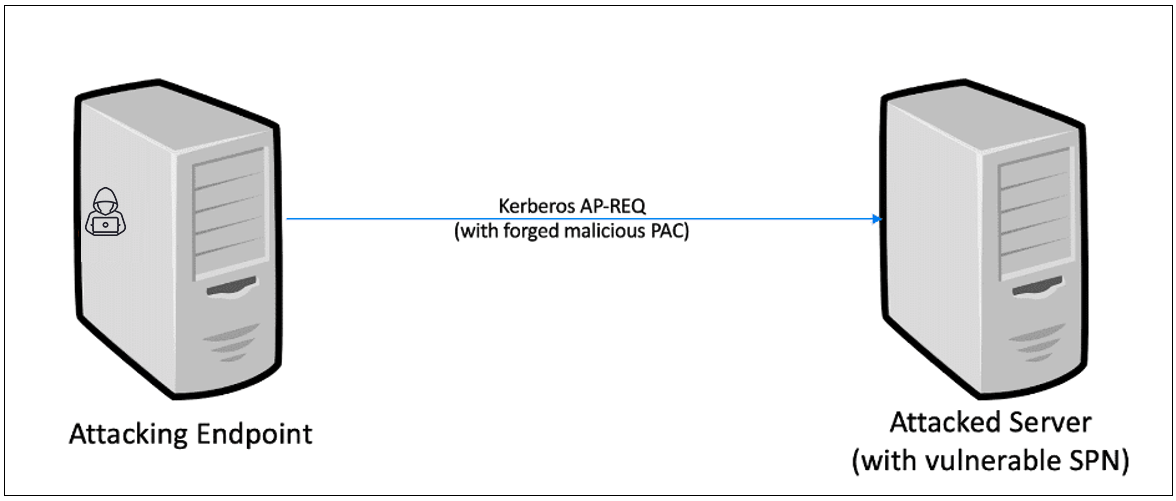 Figure 1. CVE-2020-1267 Kerberos Attack Flow
Figure 1. CVE-2020-1267 Kerberos Attack Flow
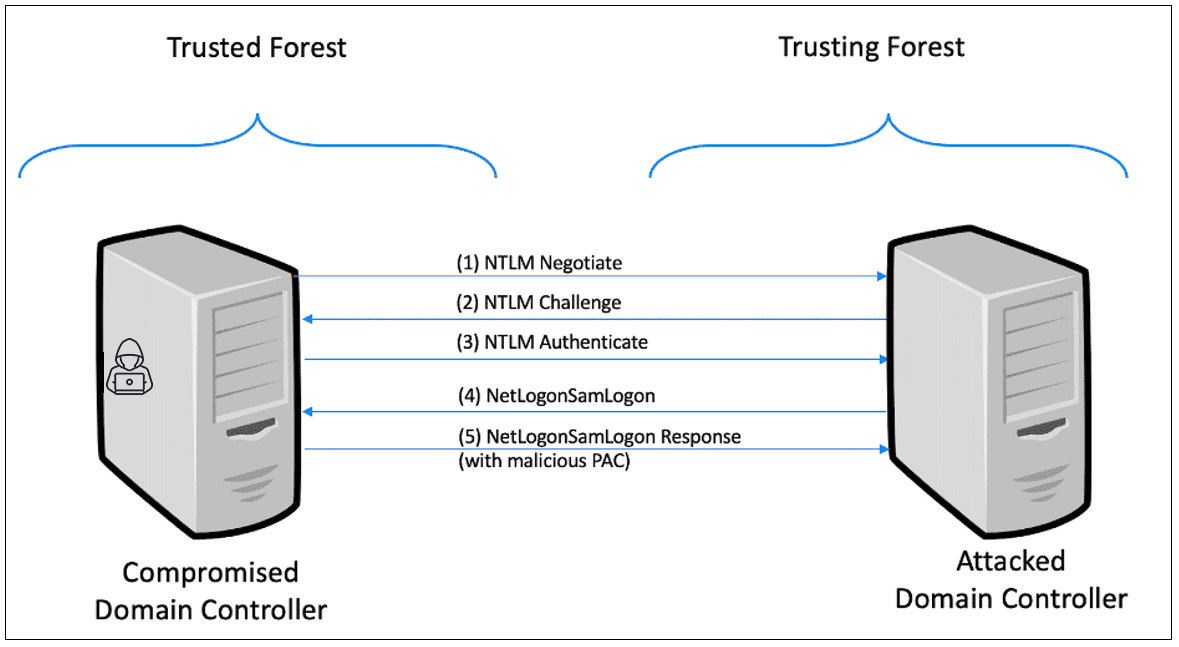 Figure 2. CVE-2020-1267 NTLM Attack Flow
Figure 2. CVE-2020-1267 NTLM Attack Flow
Impact
We have discovered two scenarios where this vulnerability could be exploited. The first is by crafting a special Kerberos AP-REQ message, and the second by exploiting NTLM over inter-forest trusts to compromise a domain after a trusted forest has been compromised. Eyal Karni (the primary researcher working on this vulnerability) will soon release a detailed blog post with all the technical details for this vulnerability. For now, these are the scenarios where we exploited the vulnerability:Kerberos Scenario
In this scenario we targeted an AD service that supports Kerberos authentication (SSPI), and we know its password. To exploit this vulnerability, we crafted a malicious PAC and sent it in an AP-REQ message to the server. This is a similar scenario to a Silver Ticket attack, with a difference that we are not application-dependent for the privilege escalation. Rather, the parsing of the PAC triggers a heap overflow vulnerability in the OS itself (lsass.exe process), for any service that uses Kerberos SSPI in the same manner. Figure 1. CVE-2020-1267 Kerberos Attack Flow
Figure 1. CVE-2020-1267 Kerberos Attack FlowNTLM Scenario
The NTLM version of this vulnerability is exploitable in environments with inter-forest trusts. If attackers compromise a domain in one forest, they could access a domain controller from another forest and inject the malicious PAC in the NETLOGON pass-through authentication flow. In this scenario we created a PoC where we have crashed the lsass.exe process on the attacked domain controller. An attacker could also possibly use this vulnerability to remotely execute code on the attacked domain controller while bypassing the forest security boundaries. Figure 2. CVE-2020-1267 NTLM Attack Flow
Figure 2. CVE-2020-1267 NTLM Attack FlowDisclosure Timeline
Our research team discovered these security flaws in February, and have been in contact with Microsoft since then:- 02/26/2020 – Heap overflow was disclosed to Microsoft Security Research Center (MSRC)
- 03/04/2020 – MSRC acknowledged the issue started working on a fix
- 06/17/2020 – MSRC updated Preempt (now CrowdStrike) research labs that vulnerability is assigned CVE-2020-1267, and will be fixed in July’s patch Tuesday
- 07/14/2020 – CVE-2020-1267 security update released
Summary
Windows authentication protocols (Kerberos, NTLM) are relatively old and have existed in the Windows code base for more than 20 years. Even though this code is an active target for attackers and defenders, it was not detected previously by fuzzing techniques. Authentication protocols are usually complex and difficult to fuzz since messages are encrypted and specific setups (passwords, trust objects, etc.) are required to effectively cover the entire code. This limitation allowed us to find a relatively simple integer overflow on a critical authentication server that was present for many years.Additional Resources
- Learn more by reading the white paper, “The Security Risk of NTLM.”
- Visit the CrowdStrike Falcon® Identity Protection solutions webpage.
- Request a demo of CrowdStrike Falcon Zero Trust or Falcon Identity Threat Detection products.
- Read expert insights and analysis on other complex threats — download the CrowdStrike 2020 Global Threat Report.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































