CrowdStrike is committed to protecting our customers from the latest and most sophisticated cybersecurity threats. We are actively monitoring activity surrounding CVE-2024-3094, a recently identified vulnerability in XZ Utils. In this blog, we discuss the significance of this vulnerability, how CrowdStrike protects its customers from adversaries attempting exploitation, and how this issue can be discovered with CrowdStrike Falcon® Exposure Management, CrowdStrike Falcon® Insight XDR and CrowdStrike Falcon® for IT.
Overview of CVE-2024-3094
Red Hat recently released CVE-2024-3094 (CVSS score of 10), a reported supply chain compromise found in the XZ Utils library (formerly known as LZMA Utils). The malicious code, which was introduced by a previously trusted developer, attempts to weaken the authentication of SSH sessions via SSHD. The affected versions of XZ are not widely distributed and are typically found in the most bleeding-edge Linux distribution builds such as the fedora rawhide and debian testing and unstable distributions.
According to Red Hat:
Malicious code was discovered in the upstream tarballs of xz, starting with version 5.6.0. Through a series of complex obfuscations, the liblzma build process extracts a prebuilt object file from a disguised test file existing in the source code, which is then used to modify specific functions in the liblzma code. This results in a modified liblzma library that can be used by any software linked against this library, intercepting and modifying the data interaction with this library.
This backdoor leverages the testing mechanisms in the build process. It was put in place as part of a sophisticated supply chain attack.
As the library is being built, a test process spins up, runs a few checks on the target system, and then, if the relevant checks pass, pulls a pre-built object file that is extracted and woven into the compilation and linking process. The backdoor is very selective of its target. It only weaves the backdoor into target builds running on x64 architectures, which is clearly indicated by the check that runs during the building process. This issue affects versions 5.6.0 and 5.6.1 of XZ.
Impacted Distributions
As of this writing, the compromised version of XZ is known to be present in the OS packages listed below. Because this is a developing situation, organizations should consult individual vendors, whose newest updates are linked here, to learn the latest information about affected products and updates.
- Debian - unstable / sid. versions 5.5.1alpha-0.1 up to and including 5.1.1-1
- Kali - systems that had their packages updated between March 26-29, 2024
- OpenSUSE - rolling releases: Tumbleweed and MicroOS between March 7-28, 2024
- Arch Linux - 2024.03.01, VM images 20240301.218094 and 20240315.221711, container images created between 2024-02-24 to 2024-03-28
- Fedora - Rawhide and Fedora 40 Beta
How CrowdStrike Falcon Protects Customers from CVE-2024-3094
CrowdStrike uses indicators of attack (IOAs) and machine learning to protect our customers. Our existing IOAs have extensive coverage for post-exploitation techniques and will help to prevent post-exploitation attempts leveraging the backdoor binaries.
CrowdStrike continues to research post-exploitation techniques using the backdoor binaries. We have identified indicators of compromise (IOCs) and incorporated them into our machine learning corpus. IOAs for detecting the malicious scripts that add the backdoor in the XZ Utils during build time have been deployed and are presently undergoing comprehensive testing across our entire fleet. Once they are tuned and have successfully passed our QA processes, they will be made visible in the CrowdStrike Falcon® console as either a Detection or a Prevention.
Please note that these require the following Linux Prevention Policies to be enabled:
- Script-Based Execution Monitoring
- Suspicious Processes
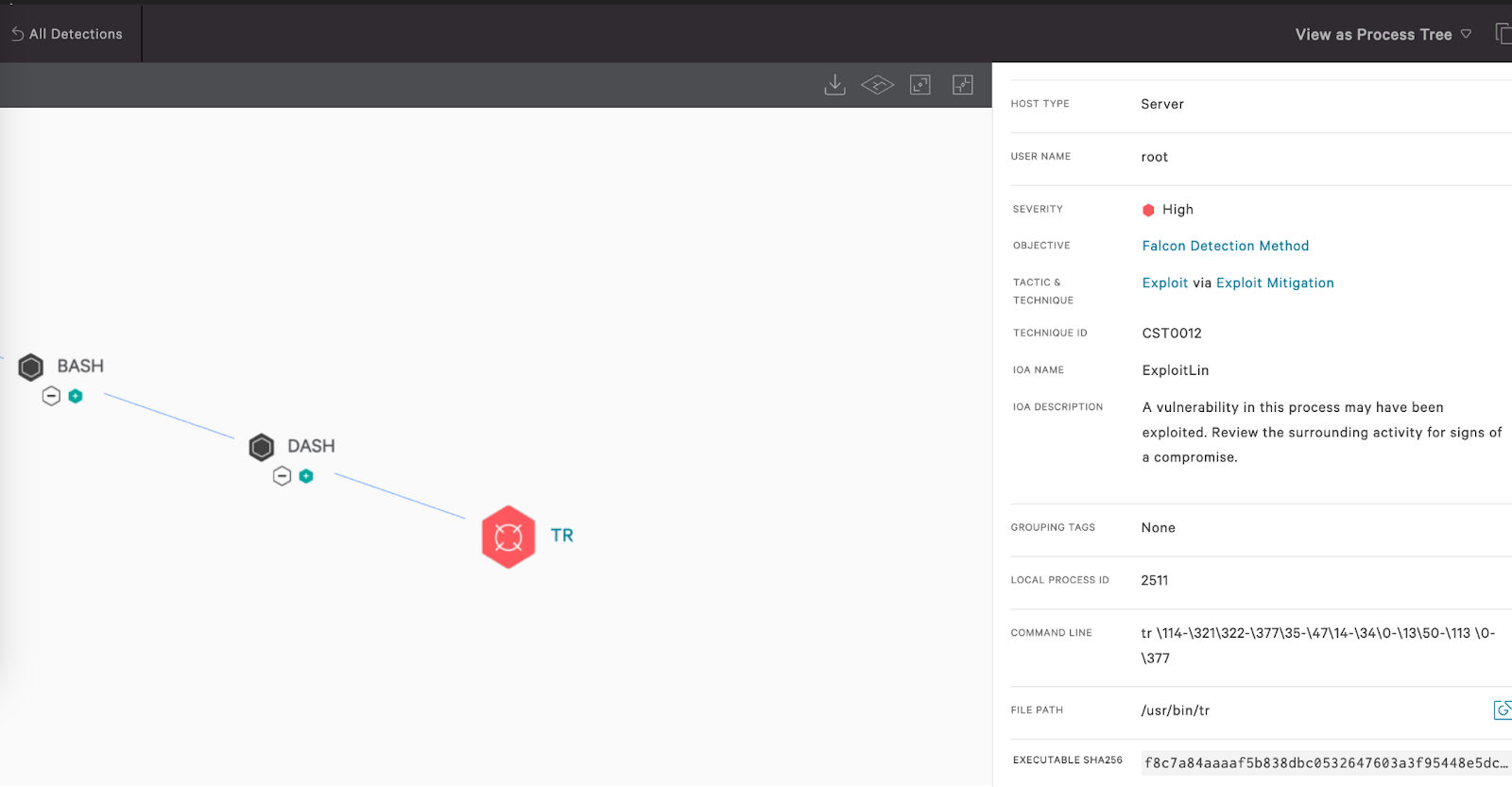
How the “tr” Command Is Used to Backdoor XZ Utils
The following obfuscated binary backdoor and scripts were added in two test files in the XZ repository:
- tests/files/bad-3-corrupt_lzma2.xz
- tests/files/good-large_compressed.lzma
During the build process, the bad-3-corrupt_lzma2.xz test file was read and de-obfuscated using “tr,” a tool meant to manipulate strings in standard input and standard output. By leveraging “tr” capabilities to manipulate strings and “translate” characters, the attackers were able to generate a bash script, which is used to chain the backdoor and weave it into the build process of XZ.
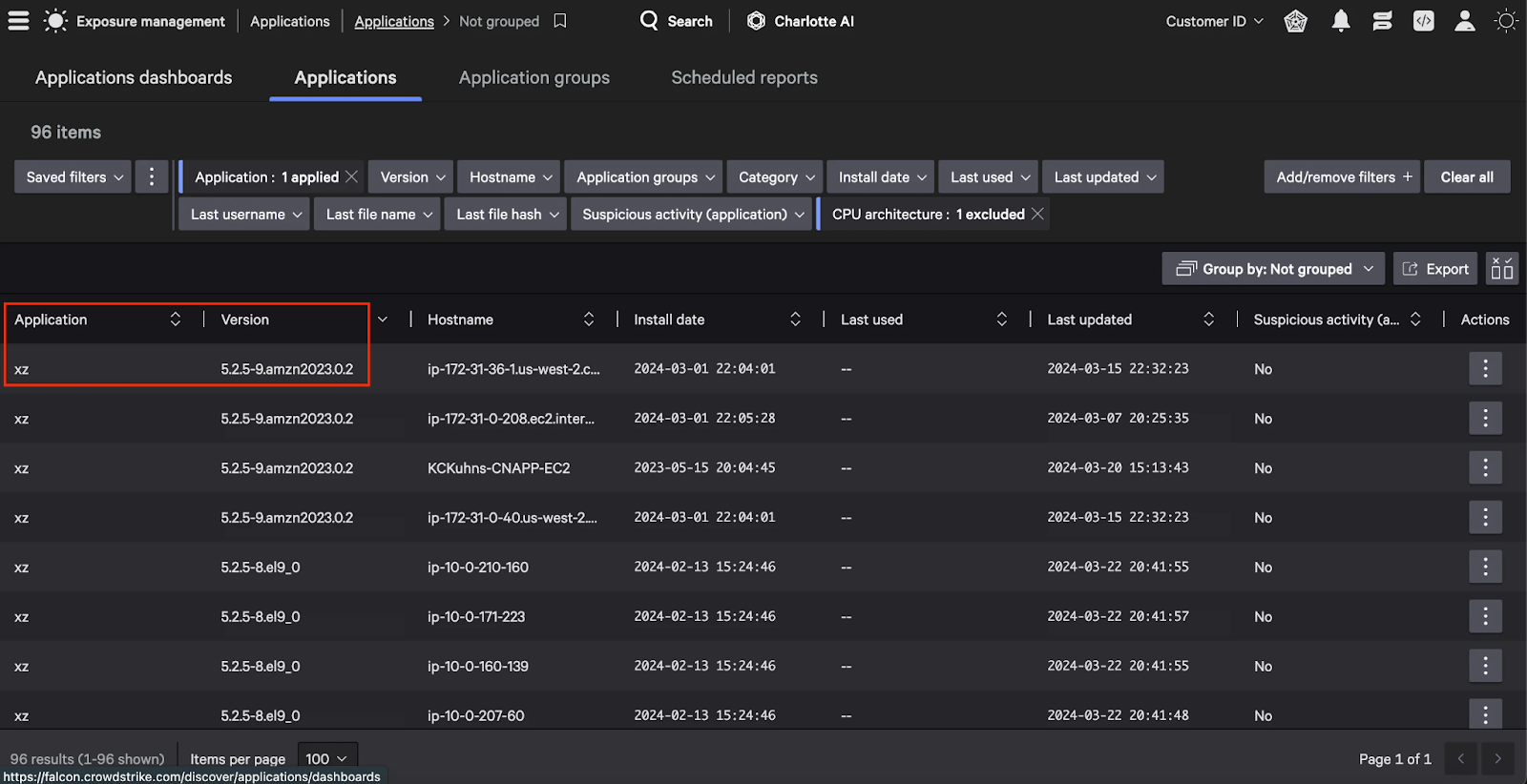
Finding CVE-2024-3094 with Falcon Exposure Management
Falcon Exposure Management will have detections for all supported platforms and applications. Exposure for most customers is expected to be limited, as the CVE does not affect any Linux distribution currently supported by the Falcon sensor.
Applications inventory can be used to hunt for affected applications that have been installed or used.
Scoping Linux Distributions Using Falcon Insight XDR
CrowdStrike Query Language (Raptor)
#event_simpleName=OsVersionInfo event_platform=Lin | OSVersionFileData=* | replace("(<0-9A-Fa-f>{2})", with="%$1", field=OSVersionFileData, as=OSVersionFileData) | OSVersionFileData:=urlDecode("OSVersionFileData") | OSVersionFileData=/NAME\=\"(?<DistroName>.+)\"\sVERSION\=\"(?<DistroVersion>.+)\"\sID/ | Distro:=format(format="%s %s", field=) | groupBy(, function=()) | sort(TotalSystems, order=desc)
Legacy Event Search
event_platform=Lin event_simpleName=OsVersionInfo
| rex mode=sed field=OSVersionFileData "s/(<0-9A-Fa-f>{2})/%\1/g" | eval OSVersionFileData=urldecode(OSVersionFileData) | rex field=OSVersionFileData "NAME\=\"(?<DistroName>.+)\"\sVERSION\=\"(?<DistroVersion>.+)\"\sID" | eval Distro=DistroName." ".DistroVersion | stats dc(aid) as TotalEndpoints by Distro | sort - TotalEndpoints
Finding Executions of the Binary xz
CrowdStrike Query Language
#event_simpleName=ProcessRollup2 FileName=/^xz(\-\w+)?$/
| in(field="event_platform", values=)
| groupBy(, function=()>))
| LastExecution:=ProcessStartTime*1000 | LastExecution:=formatTime(format="%F %T.%L", field="LastExecution")
| drop()
Legacy Event Search
event_platform IN (Mac, Lin) event_simpleName=ProcessRollup2
| regex FileName="^xz(\-\w+)?$"
| stats latest(ProcessStartTime_decimal) as LastExecution by aid, ComputerName, FileName, FilePath
| convert ctime(LastExecution) as LastExecution
Using Falcon for IT to Query in Real Time
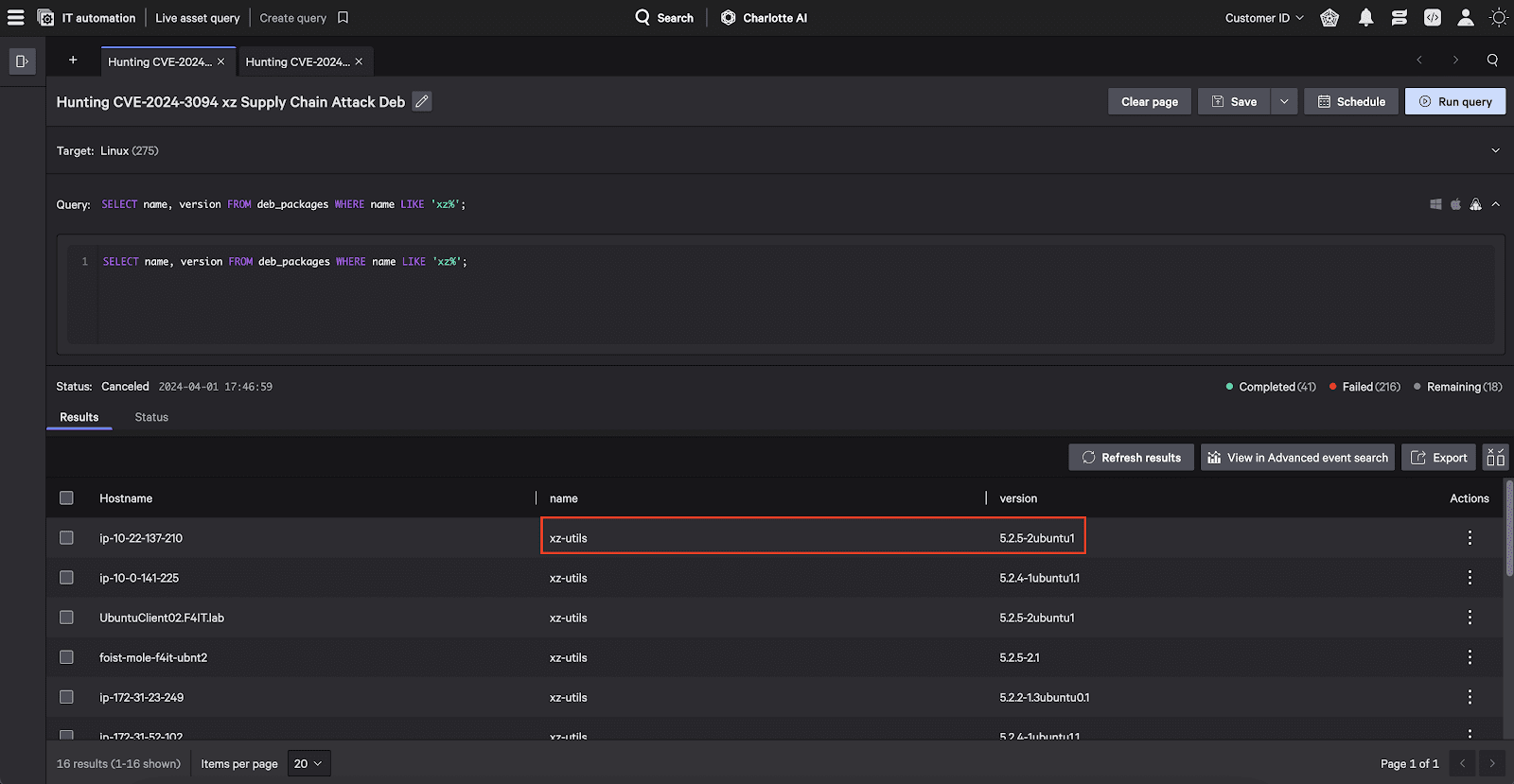
Additionally, Falcon for IT customers can use one of the following two queries to pull exact versions of XZ from systems at will. While the results are similar to those found in Falcon Exposure Management, Falcon for IT gives customers the ability to query their fleet in real time and add additional data points to their hunting and investigation process. Below is one query for DEB-based distributions and another for RPM-based distributions: 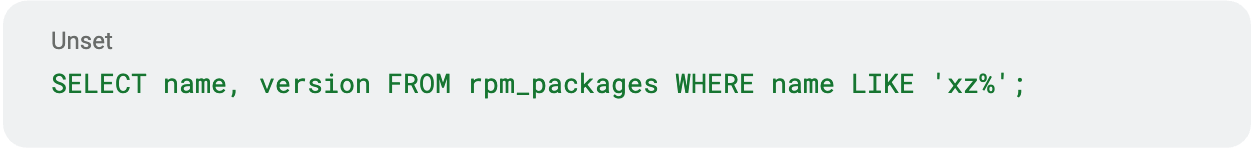 or
or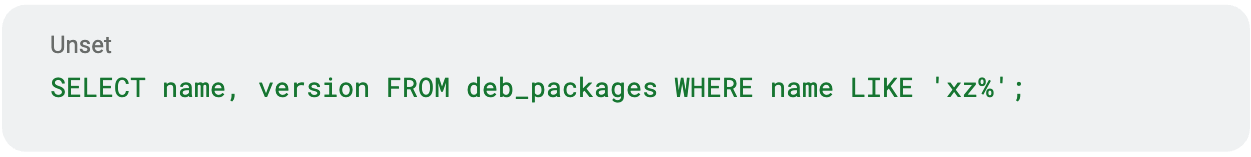
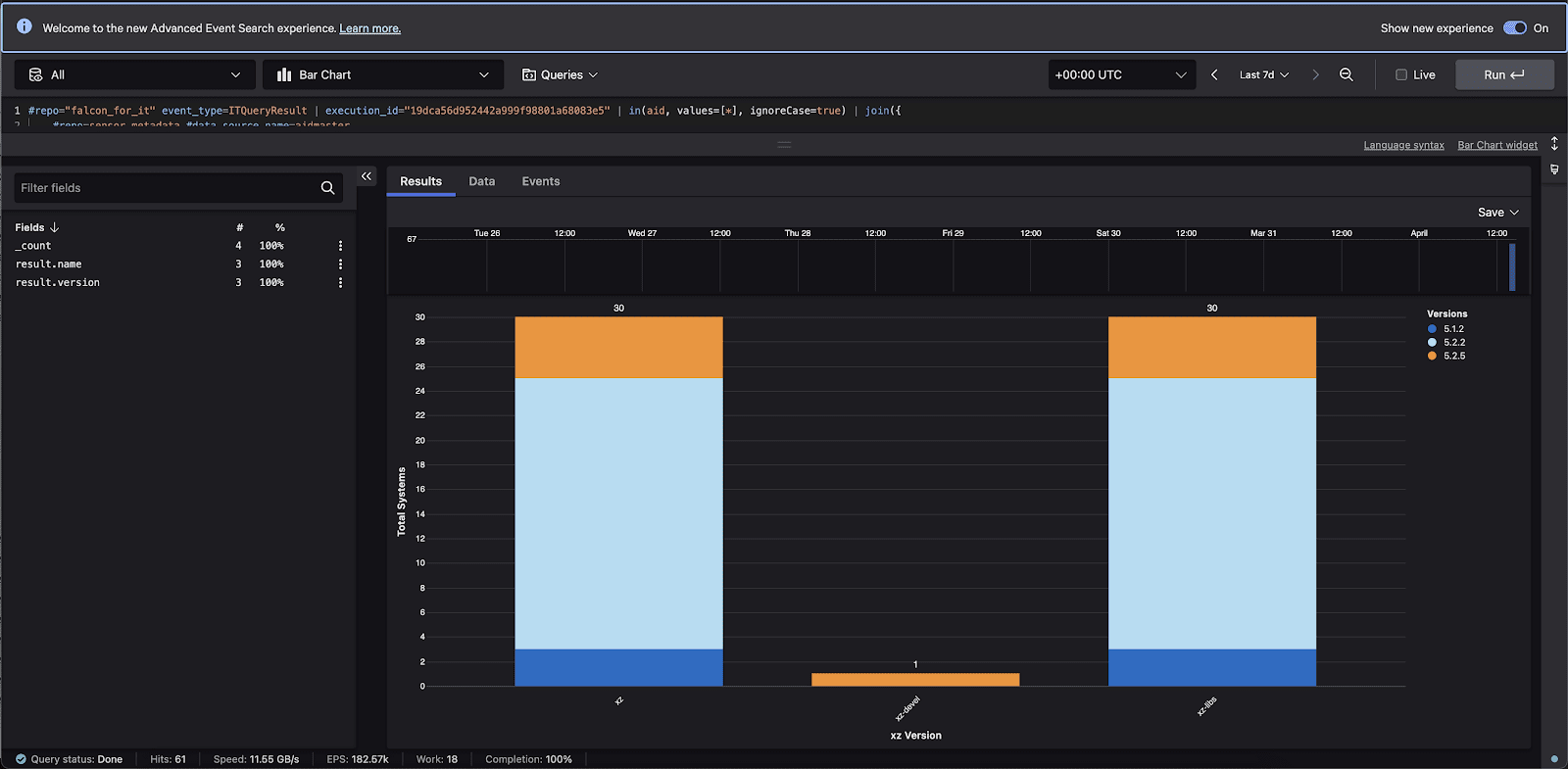
Conclusion and Recommendations
CrowdStrike’s product and internal security teams continue to actively monitor this dynamic and ongoing situation. CrowdStrike will continue to take additional steps, including mitigation and patching. As new information becomes available, we will publish updates as necessary. In tandem, we continue to develop and release new behavioral logic for the Falcon platform to detect and prevent malicious behavior related to CVE-2024-3094. Below is guidance for organizations seeking to defend their environments against exploitation of CVE-2024-3094.
- Assess the use of the XZ Utils library within your environment:
- Identify critical applications/services and remain up-to-date with vendor-specific recommendations as the situation develops
- Document mitigation and patch procedures in the event the guidance changes and additional action is necessary
- No updates or mitigations are required for CrowdStrike Falcon deployments.
List of relevant hashes:
319feb5a9cddd81955d915b5632b4a5f8f9080281fb46e2f6d69d53f693c23ae 605861f833fc181c7cdcabd5577ddb8989bea332648a8f498b4eef89b8f85ad4 8fa641c454c3e0f76de73b7cc3446096b9c8b9d33d406d38b8ac76090b0344fd b418bfd34aa246b2e7b5cb5d263a640e5d080810f767370c4d2c24662a274963 cbeef92e67bf41ca9c015557d81f39adaba67ca9fb3574139754999030b83537 5448850cdc3a7ae41ff53b433c2adbd0ff492515012412ee63a40d2685db3049
Additional Resources
- See Falcon Exposure Management in action in an interactive demo.
- Read more about Falcon Exposure Management, Falcon Insight XDR and Falcon for IT.
- Learn more about how the unified, AI-native Falcon platform stops breaches, reduces security complexity and lowers overall costs.
- Get a free full-featured trial of CrowdStrike Falcon® Prevent and see how true next-gen AV performs against today’s most sophisticated threats.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)