Containers provide a wide range of benefits to both developers and system administrators — increased agility, flexibility and scalability among them. With the increase in adoption, containers have also become a target for attack by adversaries. However, securing containers is challenging due to deployment models where customers may not have full control. Traditional security measures often do not protect containers. Therefore, developers and administrators must take extra steps to ensure the security of this emerging type of virtual infrastructure. In this post, we explore the unique security issues introduced by containers and how to secure containers running on a private data center or in the public cloud using the CrowdStrike Falcon® platform.
Container Security Challenges
The container abstraction is often incorrectly perceived as a sandboxed environment that can replace virtual machines. However, containers are a set of isolated processes for running applications together with their dependencies. As containers ultimately consist of operating system processes, they must be secured as such. Furthermore, if worker nodes are compromised then all containers running on those nodes are impacted. To secure a container environment, both worker nodes and containers running on these worker nodes need to be secured.
Traditional security systems are not designed to address the new challenges posed by containers. In fact, in container environments like Fargate, traditional security solutions simply cannot be used. Therefore, organizations must update and adapt their security strategy to detect, prevent and remediate attacks aimed at containers.
Securing Containers Using Falcon
Developers are now continuously building and deploying workloads in the data center multiple times a day using DevOps. To secure a container environment, the DevOps pipeline has to be secured. The Falcon platform provides adequate support to do so. To secure a container environment, both pre- and post-runtime environments have to be secured.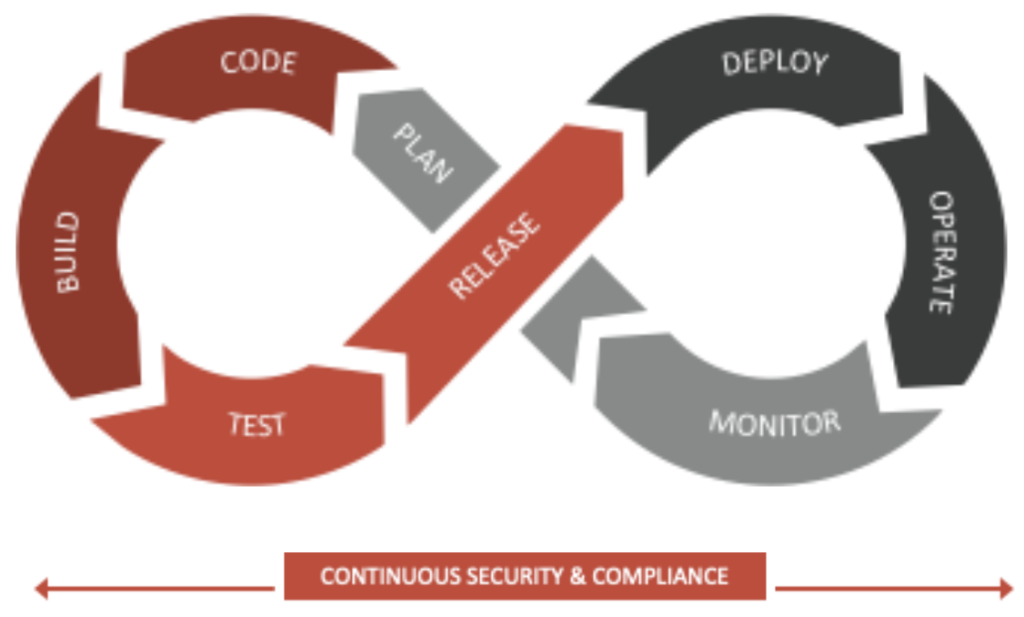
Pre-runtime Security
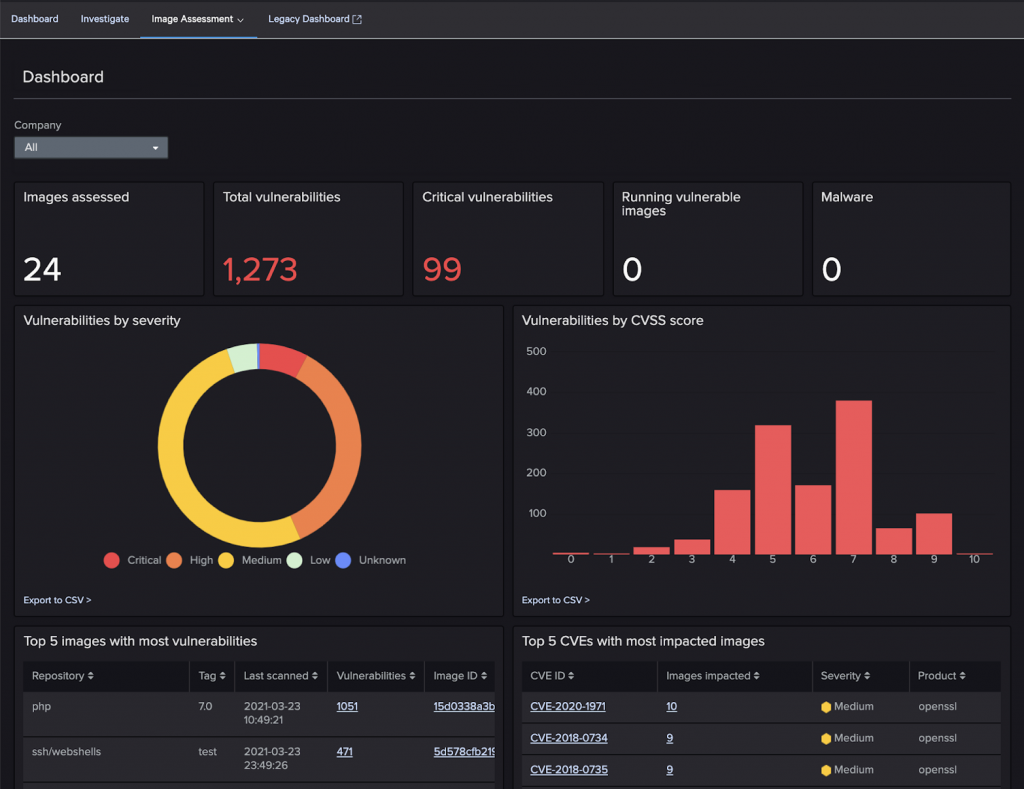
Security starts from the build time. It starts with creating a secured container. Developers sometimes use base images downloaded from an external registry to build their container images. Such images may contain malware or vulnerable libraries that can be exploited during runtime. Therefore, you must check for the existence of malware and vulnerabilities upfront. Developers may forget to remove passwords and secret keys used during development before pushing the image to the registry. When the infrastructure is compromised these passwords would be leaked along with the images. As a result, an adversary could get full access to the entire infrastructure. To reduce the attack surface, drop unnecessary binaries from containers (e.g., gcc, curl, wget, sh, bash) at build time. Falcon Image Assessment integrates into the build system to identify vulnerabilities, malware and misconfigurations as part of the build process as prescribed by the Center for Internet Security (CIS). With that in place, you can quickly perform an image assessment to determine the quality of the build. Based on the image assessment response, you can pass or fail the build. You can view image assessment via a dashboard. If any new zero-day vulnerability is found, then Falcon would detect it without rescanning the image. After the vulnerabilities are addressed Falcon would detect it and update the dashboard accordingly. Falcon console shows the latest status of your environment.
Managing Runtime Security
Application data is potentially exposed externally during run time. Therefore, it is particularly important to focus on runtime security. Most of the traditional security products can’t provide visibility within containers and many container security products can’t provide visibility and security for the worker nodes. For complete security, it’s important to secure both.
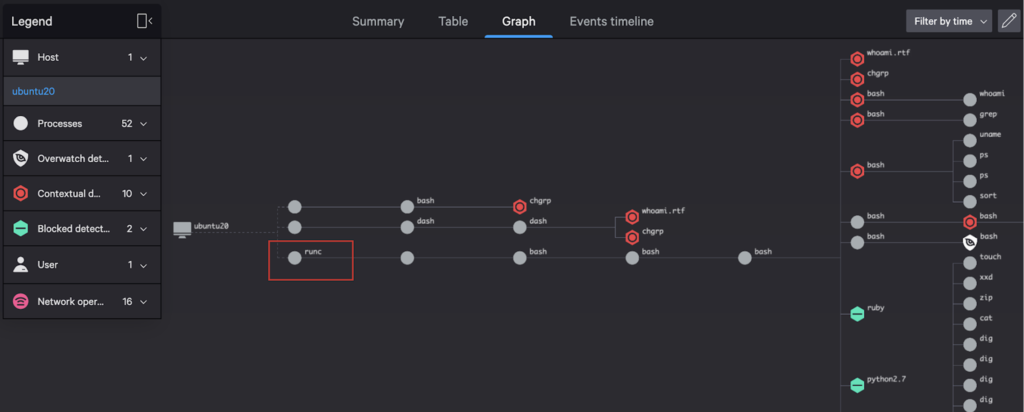
CrowdStrike Falcon® can secure both worker nodes and all containers running on these worker nodes. Falcon captures the activity generated within containers in real-time as events along with container metadata such as image and container runtime information. It also identifies misconfigurations such as containers running with root privileges. The runtime security is extended to both containers and worker nodes. Falcon uses machine learning to correlate events from the worker nodes with the events generated from containers to identify an incident. Thereby providing a holistic view for investigation. Adversaries can’t bypass security by executing malware in the container. Your Linux policies can be enforced within containers to prevent the execution of malware in containers. In the below picture you can observe that both worker nodes and containers are compromised as part of an incident. You can easily investigate the attack based on various parameters such as network, user or process.
Securing Serverless Containers
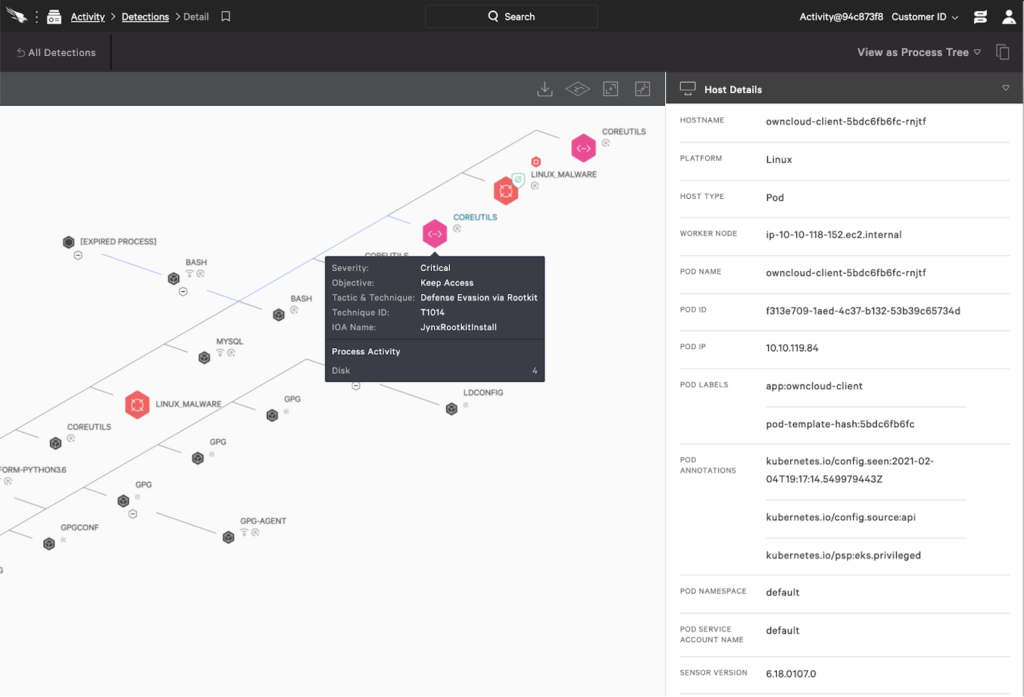
Securing serverless container environments such as Amazon AWS Fargate can be challenging. In such an environment, you can’t install any traditional security software that relies on access to the worker node. Privileged containers are also not allowed. Therefore, any security solution based on the use of privileged containers fails to secure such environments. To address these challenges we specifically designed Falcon Container Sensor for serverless container environments. See this white paper for details about the broader context for this offering. Falcon Container uses a unique design that runs the sensor as part of the Kubernetes pod. Falcon Container is integrated with your Kubernetes cluster such that it can easily scale with your applications to keep your containers secured during runtime. It provides the same level of security as a self-managed container environment. For example, you can group pods in a host group to enforce Linux prevention policies on containers running on serverless environments such as Fargate. In fact, you can use Falcon containers to secure your entire managed Kubernetes environment (e.g., Falcon containers can secure managed Kubernetes environments such as Amazon Elastic Kubernetes Service, or EKS). When an application is blocked you can view the Kubernetes context such as Kubernetes namespace or pod name as part of the detection as shown below.
Central Management
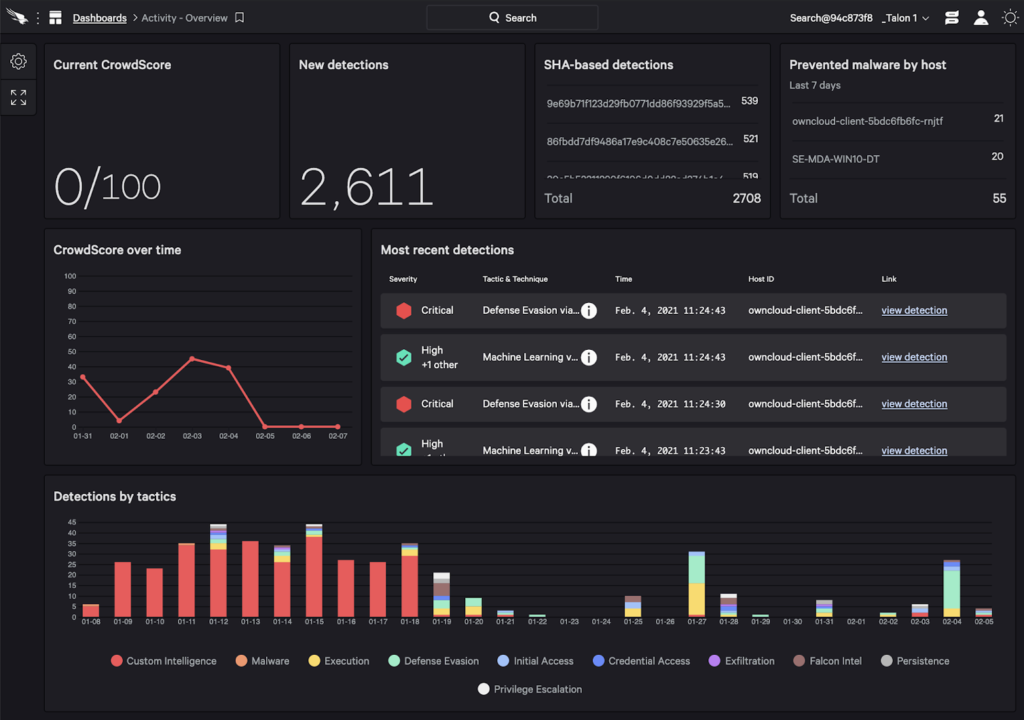
Falcon extends the single lightweight design to secure your entire Kubernetes environment no matter where the workloads are running — on-premises or in the cloud. You can centrally track your entire Kubernetes environment through an intuitive management console. Container dashboard shows both pre- and post-runtime threats within the same dashboard.
In fact, the Falcon console provides a single pane of glass to secure your entire hybrid cloud environment. Data collected by all Falcon sensors are stored centrally in CrowdStrike Threat Graph® database. Hence, Falcon provides seamless integration to hunt for adversarial activities across your data center no matter where your workloads are running — virtual machines, containers, in a private DC, public cloud or in a serverless environment. All features are homegrown and well integrated into the Falcon console, from where you can centrally manage your entire environment.
A Centrally Managed, Cloud-native Solution
In this post, we discussed how traditional security measures often fall short in securing Kubernetes environments. Even many modern security solutions fail to secure workloads running in a serverless container environment. However, as discussed above, securing containers need not be an overly complex task. Using Falcon you can seamlessly bake security as part of your DevOps process to secure self-managed, hosted and serverless containers. You can manage security centrally through Falcon console and enforce consistent policies across your Kubernetes environment. The centralized visibility helps organizations capture an enterprise-wide view of all their assets.
CrowdStrike strives to support organizations that allow their users to stay ahead of the curve and remain fully protected from adversaries and breaches. Read more in this CrowdStrike white paper, “Upleveling of the Cloud Infrastructure and Its Implications on Cloud and Container Security.”
Additional Resources
- Find out about the comprehensive breach defense and container security offered by Falcon Cloud Workload Protection.
- Discover the advantages of CrowdStrike’s powerful cloud security solutions.
- See how CrowdStrike makes cloud security posture management simple — visit the Falcon Horizon™ product webpage.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)