In the cybersecurity industry, understanding the value and impact of the critical technology we use to keep organizations safe can often become lost in translation. This is undoubtedly the case with extended detection and response (XDR), where the continued misuse of the term has created more market confusion than clarity.
The definition of XDR varies depending on who you ask. Vendors, analysts and end-users can all have divergent definitions of XDR, which creates uncertainty and does nothing to help the customer.
I firmly believe that XDR can help solve some of the toughest challenges security teams face, helping them to fight adversaries by increasing visibility, simplifying operations and accelerating identification and remediation across the security stack. How? By gathering and integrating security data from a multitude of high-value, cross-domain sources to detect and respond to advanced attacks and ultimately stop breaches.
One of the questions I’m asked most often is “How can I cut through the noise and hype and identify an XDR solution that is effective and will deliver the outcomes my security team needs?”
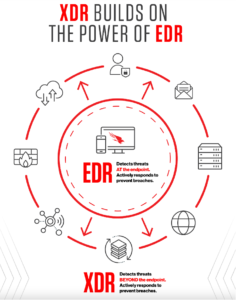
From my point of view, it starts by clearly defining what XDR is and what it's not. XDR needs to be built on the foundation of EDR. As Forrester said in an XDR report, “… good XDR lives and dies by the foundation of a good EDR.”
 “… good XDR lives and dies by the foundation of a good EDR.” — Forrester
“… good XDR lives and dies by the foundation of a good EDR.” — ForresterFurther, XDR needs to give security teams the most relevant telemetry from systems and applications across the entire IT security ecosystem to rapidly provide deep visibility. XDR must also provide detection and response actions beyond the endpoint, empowering security teams to stop breaches faster. By building on EDR, XDR can make all telemetry accessible and actionable — incorporating data from across endpoints, cloud workloads, identity, email, network traffic, virtual containers, sensors (from operational technology, or OT) and more to generate XDR detections.
Ultimately, XDR can deliver substantial improvements to security team operations by making real-time threat detection easier.For most of the customers I talk to, this is a welcomed advance. Consider what most security teams have to deal with on a daily basis to identify and hunt threats:
- Security Tool Fatigue: On average, about 45 cybersecurity-related tools are deployed on enterprise networks1 — that’s a lot of pivoting back and forth to uncover an attack story.
- Alert Overload: Security teams have to sift through many alerts — averaging about 11,000 alerts on a daily basis, 50 percent of which are false positives.2
XDR can help solve these challenges, which is part of the broader XDR conversation I had with Allie Mellen, Sr. Analyst at Forrester Research. The conversation will be featured as an on-demand CrowdCast. I encourage you to watch today and join us as we dive into:
- Industry megatrends driving the need for XDR
- Why the best XDR offerings are built on a strong foundation of EDR
- Why XDR vendors must prioritize the security analyst experience
- Key differences between open (or native) and hybrid XDR approaches
- Why security and business leaders should prioritize XDR in the next 12-18 months

Watch the "Why XDR Must Start with EDR" promo
Endnotes
- Source: The 2020 Cyber Resilient Organization Study by the Ponemon Institute
- Source: Forrester Study: The 2020 State of Security Operations
Author Michael Sentonas is the chief technology officer of CrowdStrike.
Additional Resources
- Learn more about today’s adversaries and how to combat them at Fal.Con 2022, the cybersecurity industry’s most anticipated annual event. Register now and meet us in Las Vegas, Sept. 19-21!
- View the CROWDSTRIKE FALCON® XDR demo and learn more about CROWDSTRIKE FALCON® XDR.
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)