Cybercriminals continuously adapt to stay a step ahead of the organizations they target. Over more than a decade, CrowdStrike has carefully tracked the evolution of eCrime tactics and capabilities and codified them in more than 4,900 intelligence reports.
Today’s threat landscape is dominated by sophisticated ransomware operators and data extortionists that are supported by a robust and increasingly specialized market-based ecosystem of criminal service providers. Access brokers, ransomware-as-a-service (RaaS) providers, commodity malware developers, distribution services and marketplaces trafficking in malware, exploits, personally identifiable information (PII), financial information and credentials — all have rapidly proliferated.
For security professionals, the fast-changing dynamics of the eCrime underground presents substantial challenges:
- Easy monetization of stolen credentials via underground marketplaces and access brokers increases the likelihood of credential theft and leakage. Opportunity makes the thief!
- The eCrime ecosystem lowers the barrier for entry for criminal actors of varying sophistication levels, expanding the quantity and quality of exploits offered in turnkey as-a-service kits.
- As new vulnerabilities are regularly identified and organizations are often behind on their patch management, adversaries frequently update their tactics and tools to maximize attack efforts.
A combination of the right technologies and insights into the criminal ecosystem can provide security teams with the edge they need to proactively adjust security controls and monitor evolving security and brand risk. They need to set up a cascade of views, reports and continuous monitoring efforts against eCrime activities to stay ahead of imminent attacks.
To address these challenges, CrowdStrike is excited to announce several new capabilities for its CrowdStrike Falcon® Intelligence Recon solution — grouped in four high-level use cases — to further enhance security teams’ ability to identify and mitigate digital risk.
Use Case 1: Gaining Global Threat Awareness via Underground Activity Reports
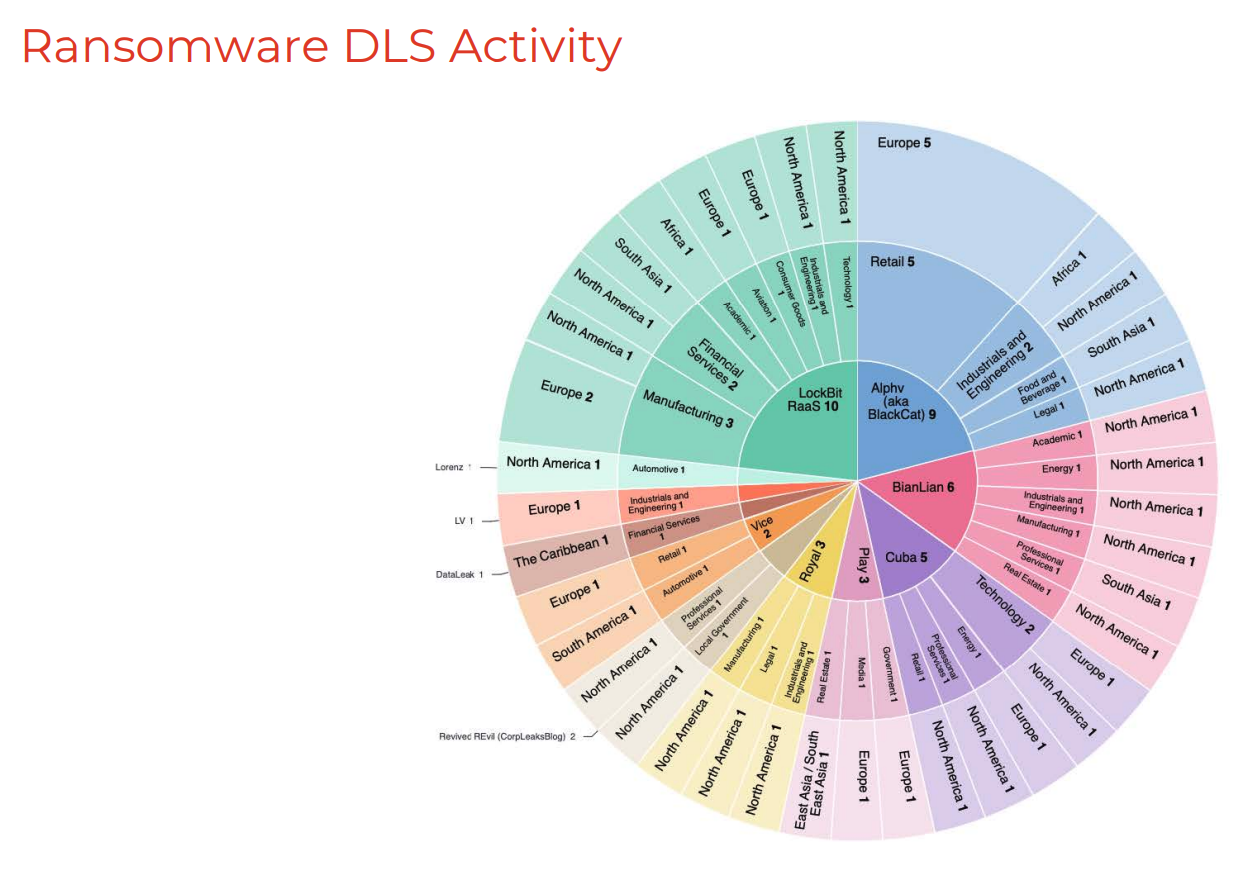
CrowdStrike threat experts periodically publish quantitative reports about evidence they’ve discovered on the criminal underground such as ransomware data leaks on adversary-controlled dedicated leak sites (DLS), access broker advertisements and frequently exploited vulnerabilities.
These new reports help threat intelligence analysts orient and understand how cybercriminals move around, the sectors and geographic areas they target and the new tactics they adopt. Using this information, the extended cybersecurity team can be put on heightened alert and preemptively adjust controls.
Use Case 2: Understanding Your Organization’s Threat Profile
Tightening security controls based on threat trends is one way to reduce risk. However, restricting unnecessary processes or access can negatively affect business operations. A better way to mitigate risk while maintaining productivity is by understanding the organization’s threat profile.
Once the team has gained global threat awareness, this second use case provides security teams an outside-in view of their risk by surfacing information such as unknown digital exposures, who is targeting the organization, what the threat actors’ capabilities are and which technologies they are most likely to exploit. To help users better understand their threat landscape, CrowdStrike has introduced several powerful new capabilities in Falcon Intelligence Recon:
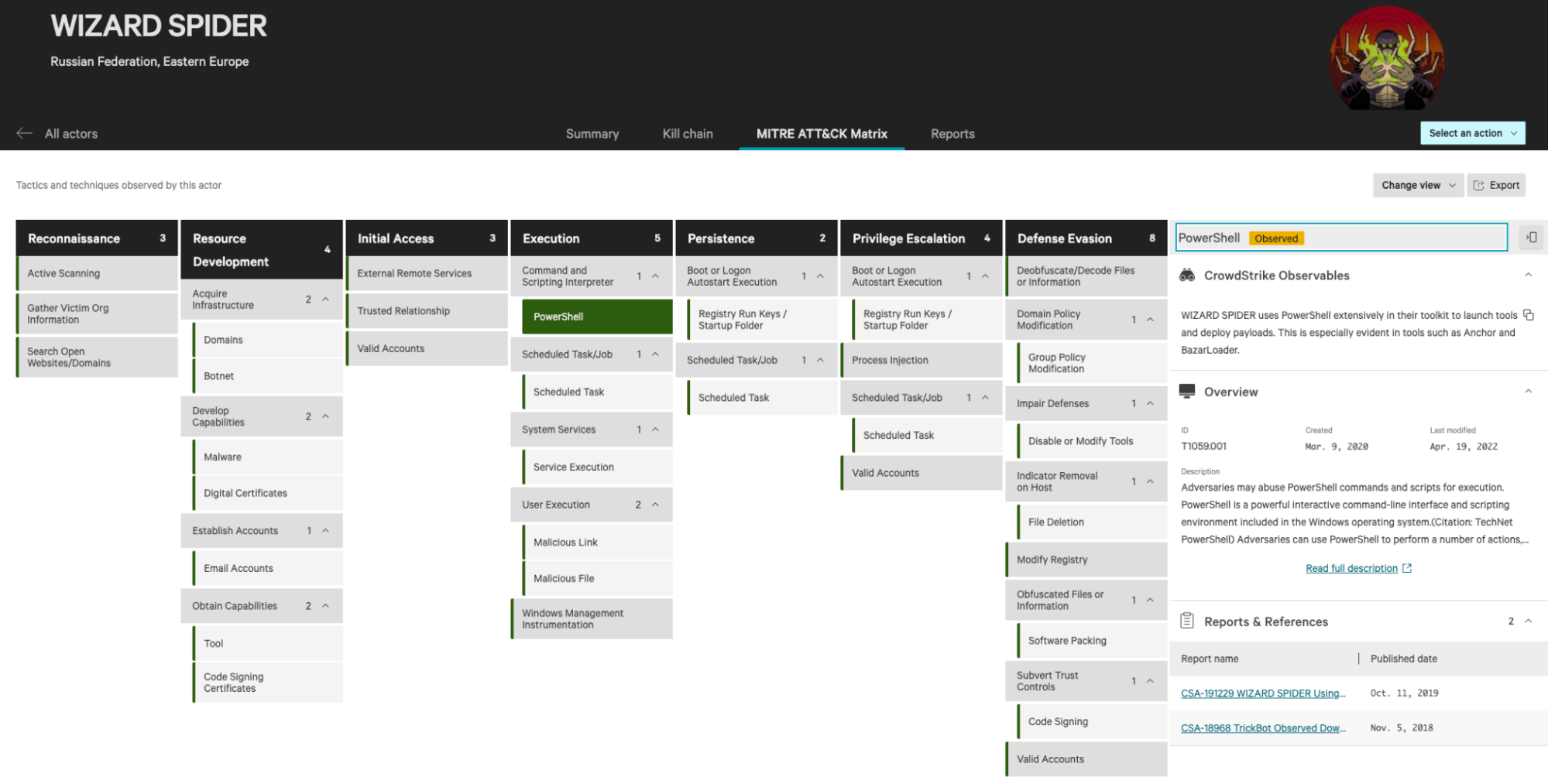
MITRE ATT&CK Adversary Mapping. Expanding threat actor profiles with MITRE ATT&CK® navigation, enables the user to filter a specific actor and understand their individual technical tactics through CrowdStrike’s published observables and analyst notes captured in human-readable intelligence reports.
Vulnerability Intelligence view: Enabling users to view the details of, and context behind, new vulnerabilities in near real time. Users can sort and filter on over 200,000 vulnerabilities by exploit status, related threat actors or threat campaigns. IT asset owners or security planners can even start by searching a vendor or product name to help determine whether including new technologies in their inventory would pose new threat risks. For subscribers of CrowdStrike Falcon® Intelligence Premium, this view enables users to immediately pivot into related vulnerability research and reporting.
 Figure 3. Vulnerability Intelligence view with Exploit Status, Actors, Timing and Report links (click to enlarge)
Figure 3. Vulnerability Intelligence view with Exploit Status, Actors, Timing and Report links (click to enlarge)Use Case 3: Refined Searching and Continuous Monitoring of Underground Forums and Criminal Markets
The criminal underground can be a treasure trove of information, yet setting up in-depth monitoring beyond the perimeter is both an art and a science. It requires a continuous back and forth between discovering evidence and tuning detection rules. CrowdStrike has expanded Falcon Intelligence Recon to include advanced historical searching, allowing the user to build out a timeline search based on word, phrase, domain, email or IP address against underground activities; review the results; and tune the search criteria and save them for later reuse.
Use Case 4: Finding Exposed Sensitive Data
Not all exposed data is immediately used by cybercriminals, as it may have been leaked but not yet shared within the underground community. Threat analysts of course want to know about these leaks and see if any organizational credentials have been leaked (e.g., through a third-party breach). To address this early-warning use case, Falcon Intelligence Recon can now monitor for exposed data, allowing users to enter emails or domains and be notified when breach information containing their domain name gets published.
Falcon Intelligence Recon’s New Capabilities Help Find Needles in the eCrime Haystack
The eCrime underground keeps expanding and changing quickly. Always knowing if your organization is at risk requires a lot of extra eyes and a step-by-step approach. Falcon Intelligence Recon’s multiple new capabilities help customers gain a global perspective on the underground trends, understand their own threat profile and take deep monitoring actions to get early, actionable warnings on active threats related to their organization.
Additional Resources
- Attend a Falcon Encounter Hands-On Lab to experience Falcon Intelligence Recon and monitor activity across criminal forums, domain registrations and underground communities to gain early warnings on emerging threats to your business
- To find out more about how to incorporate threat intelligence into your security strategy, visit the CrowdStrike Falcon® Intelligence page.
- Read about the cybercriminals tracked by CrowdStrike Intelligence in the CrowdStrike 2022 Global Threat Report.
- Learn more about the powerful, cloud-native CrowdStrike Falcon® platform by visiting the product webpage.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)