We’re thrilled to share that the CrowdStrike Falcon® sensor now fully supports Google Cloud Run, bringing advanced security capabilities to your serverless applications. While we announced this at Google Cloud Next in April 2024, this blog goes deeper into the integration and shares how customers leveraging Google Cloud Run and CrowdStrike can deploy Falcon quickly to enhance their serverless security requirements.
To recap, Google Cloud Run offers a powerful, fully managed platform for deploying containerized applications that scale automatically with demand. However, the dynamic and ephemeral nature of serverless environments poses unique security challenges. With the Falcon sensor now integrated with Google Cloud Run, organizations can leverage CrowdStrike’s industry-leading protection to secure their serverless workloads.
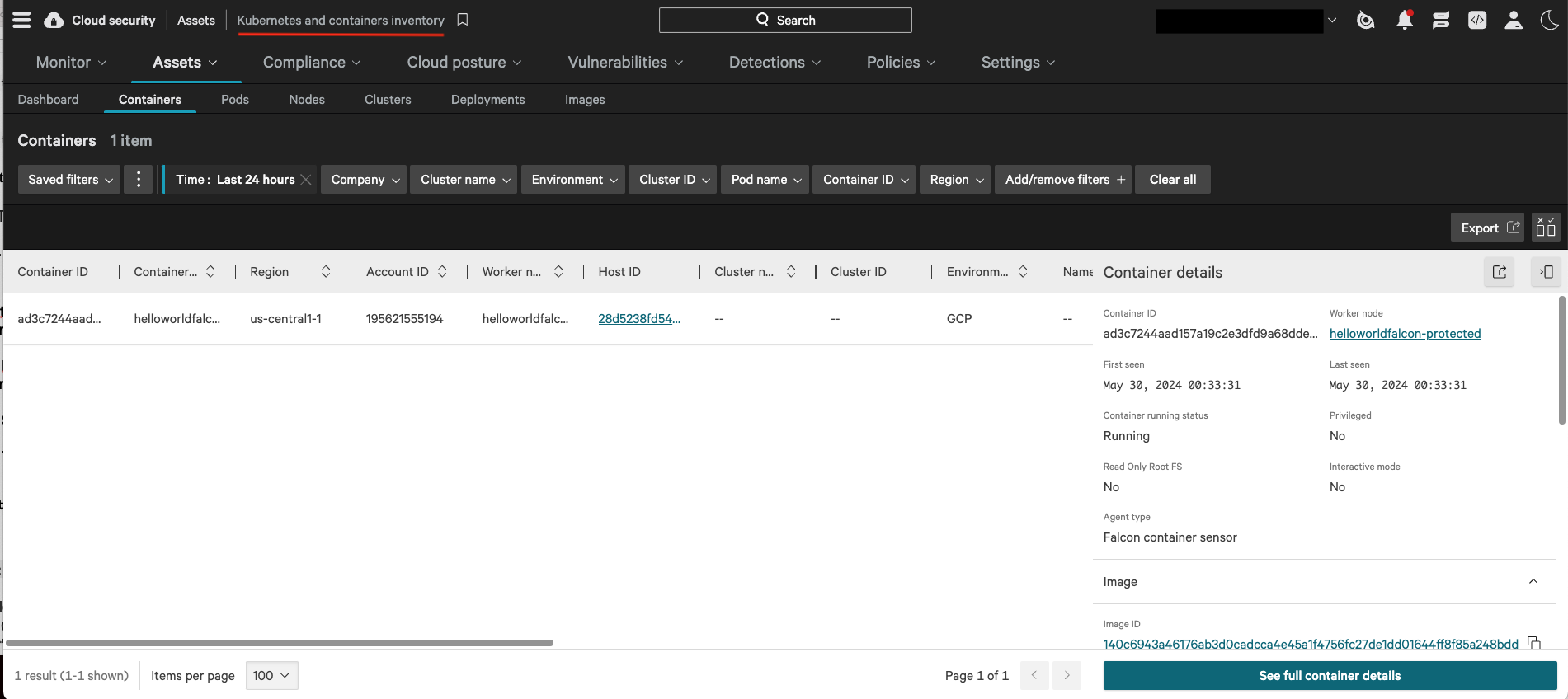
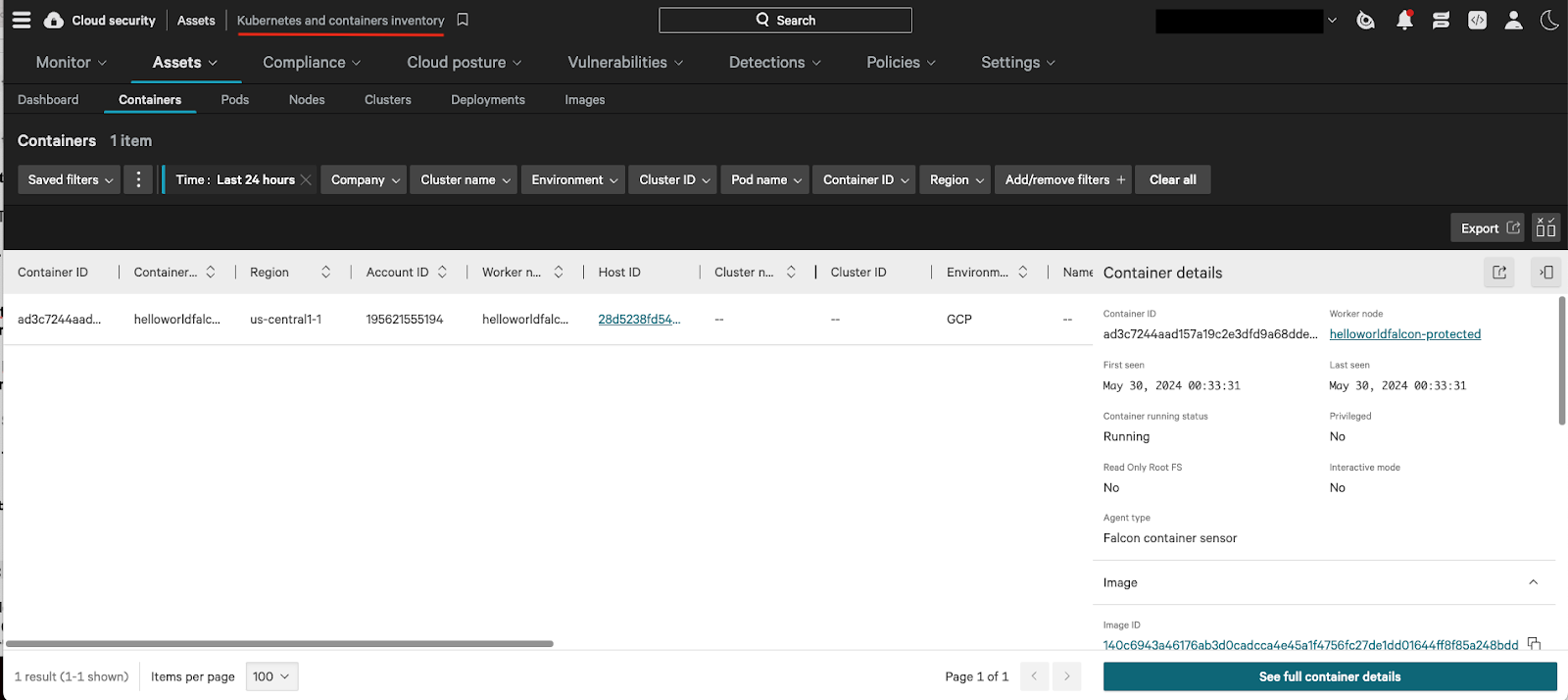
Figure 1. Google Cloud Run shown via containers in the Falcon console.
Enhanced Security for Serverless Applications
By supporting Google Cloud Run, the Falcon sensor ensures that your serverless applications benefit from the same robust security measures that protect traditional and cloud-based workloads. The AI-native CrowdStrike Falcon® cybersecurity platform provides real-time threat detection, automated incident response and comprehensive visibility into your serverless environment. This integration helps you identify and mitigate threats before they can impact your applications, ensuring continuous protection across your entire cloud infrastructure.
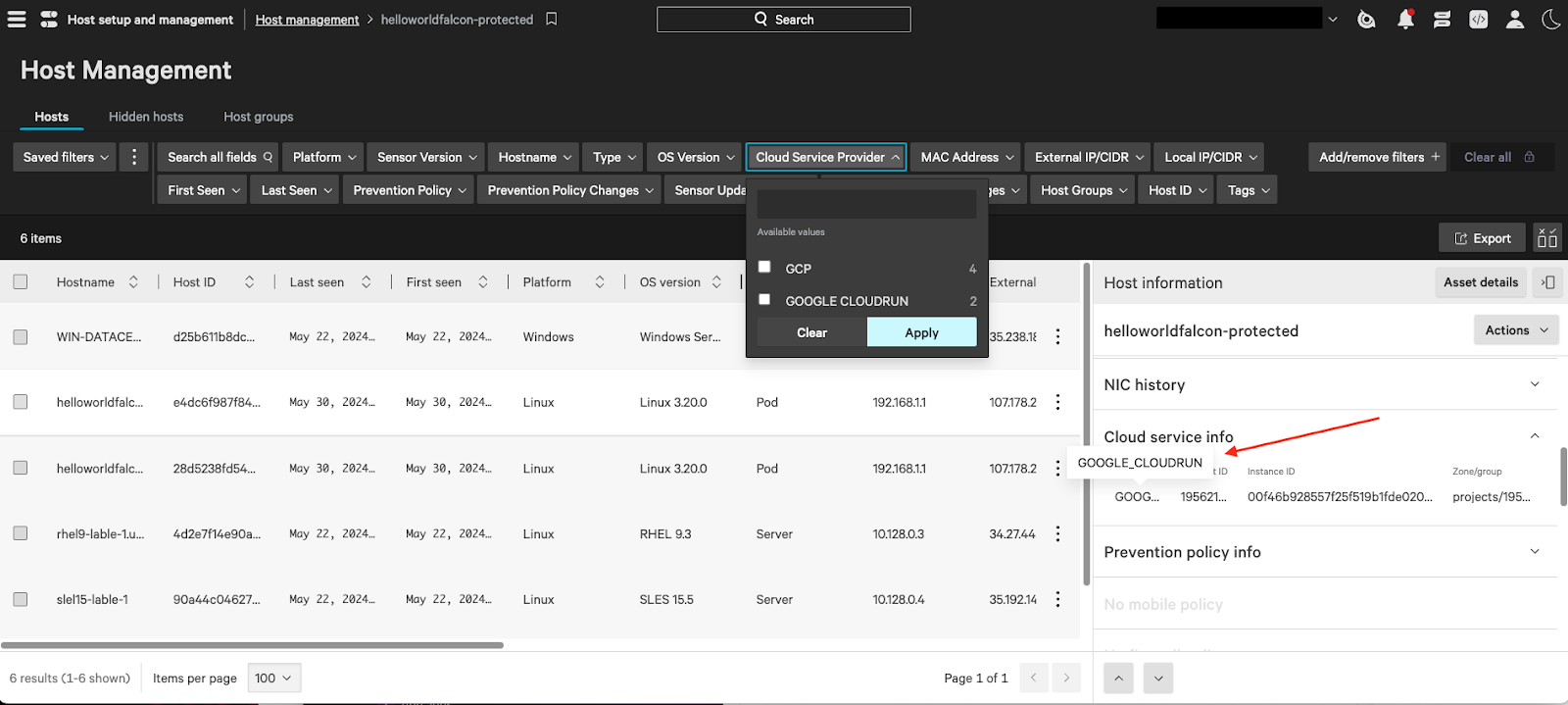
Figure 2. The host management dashboard in CrowdStrike Falcon® Cloud Security shares information for Google Cloud Run services.
Seamless Integration and Continuous Protection
Deploying the Falcon sensor on Google Cloud Run is straightforward and seamless, allowing you to integrate security into your DevOps processes without compromising performance or agility. The sensor automatically scales with your workloads, providing consistent protection as your application demand fluctuates. This ensures that your security posture remains strong, regardless of the size or complexity of your serverless deployments.
Empowering DevSecOps with Real-Time Insights
With this new support, DevSecOps teams can now gain real-time insights into the security status of their serverless applications running on Google Cloud Run. The Falcon platform’s advanced analytics and threat intelligence capabilities empower teams to make informed decisions, swiftly respond to incidents and continuously improve their security practices. This proactive approach helps organizations maintain a secure and resilient application environment, fostering innovation and agility.
We’re excited about this expansion and look forward to helping our customers enhance their security posture in serverless environments. For more information on how to deploy and configure the Falcon sensor on Google Cloud Run, Falcon platform customers can read this official documentation.
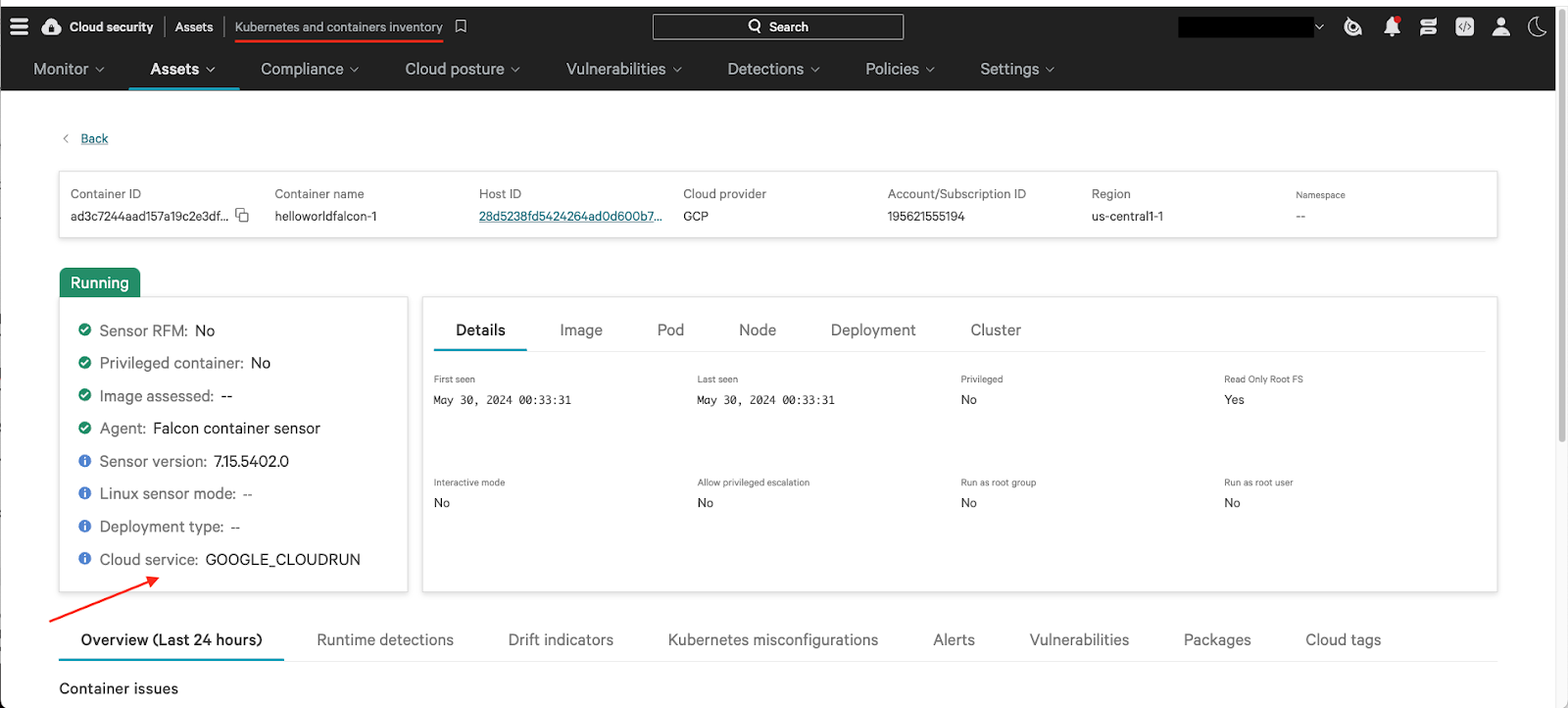
Figure 4. The Kubernetes and containers inventory dashboard in Falcon Cloud Security is where you can find Google Cloud Run service monitoring and detections.
Deployment Overview
Google Cloud Run is a fully managed serverless compute platform built from Knative that enables customers to run containers without the need to manage the underlying infrastructure. You can run your containers either fully managed with Google Cloud Run or in your Kubernetes Engine cluster with Google Cloud Run on Anthos. In Google Cloud Run, customers can deploy applications as jobs or services. The Falcon container sensor for Linux supports both job and service deployments.
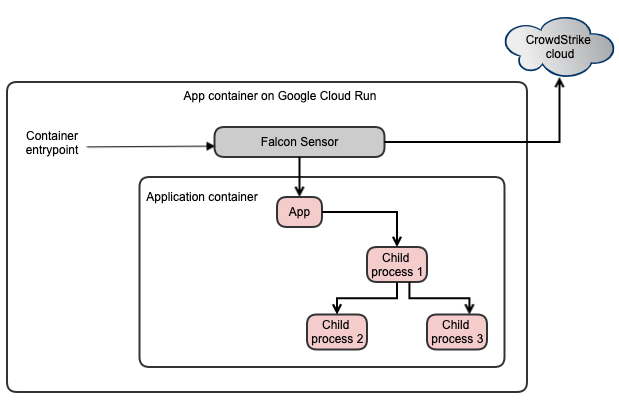
The Falcon container sensor for Linux can extend runtime security to container workloads in Google Cloud Run because it runs in the user space with no code running in the kernel or the worker node OS.
Deploying the Falcon container sensor for Linux to Google Cloud Run requires modification of the application container image. The Falcon container sensor image contains a Falcon utility that supports patching the application container image with Falcon container sensor for Linux and its related dependencies.
The Falcon container consists of two components:
- The Falcon container sensor for Linux: At runtime, the Falcon container sensor for Linux is launched inside the application container of the service or job. It uses unique technology to run in the application context.
- Falcon utility: The Falcon utility runs offline and takes the application container image as an input to generate a new container image patched with the Falcon container sensor for Linux and its related dependencies. The Falcon utility also sets the Falcon entry point as the container entry point.
Here is an overview of the installation workflow:
- Create an API client Key
- Get your CrowdStrike CID with checksum
- Retrieve the sensor image and push to Google Registry
- Run the Falcon utility to build a new image
- Push the new image to the registry
- Deploy the Falcon container sensor for Linux to Google Cloud Run
- Verify the sensor deployment
Once verification is over, you’re ready to go. For customers leveraging Google Cloud Run and CrowdStrike, this process is designed to make it easy to follow and deploy.
Here’s a more detailed step-by-step guide for customers using Falcon Cloud Security.
Shaping the Future of Cloud Security
The powerful combination of AI-powered cloud services from Google Cloud and the unified protection and threat hunting capabilities of the Falcon platform provides the security that organizations need to stop breaches in multi-cloud and multi-vendor environments.
As cloud threats and technology continue to evolve, staying ahead of threats is paramount. Modern businesses need allies to protect their cloud-based resources, applications and data as their reliance on cloud technology continues to grow. This synergy between CrowdStrike and Google Cloud will shape the future of cloud technology and security, setting a new standard for protecting today’s cloud environments.
Additional Resources
- Learn how Falcon Cloud Security can protect your Google Cloud resources.
- See why Forrester named CrowdStrike a Leader in The Forrester Wave™: Cloud Workload Security, Q1 2024.
- Get a free Cloud Security Health Check and experience Falcon Cloud Security in action for yourself.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)