- CrowdStrike introduces accelerated memory scanning into the CrowdStrike Falcon® sensor for Windows to enhance existing visibility and detection of fileless threats
- The Falcon sensor integrates Intel® Threat Detection Technology (Intel® TDT) to perform accelerated memory scanning for malicious byte patterns
- Memory scanning is optimized for performance on Intel CPUs, including high-performance operation, by offloading the operation to an available Intel integrated graphics processing unit (GPU)
- Memory scanning will be available as beta starting with Falcon sensor version 6.37
- CrowdStrike constantly researches and develops new technologies and features to protect customers from today’s most sophisticated threats
CrowdStrike is introducing Intel TDT accelerated memory scanning into the CrowdStrike Falcon® sensor for Windows to increase visibility and detect in-memory threats, adding another layer of protection against fileless threats. In recent years, threat actors have increased their dependence on fileless or malware-free attacks. The CrowdStrike 2022 Global Threat Report noted that 62% of all attacks in the fourth quarter of 2021 were malware-free, with attackers relying instead on built-in tools and code injection techniques to accomplish their goals without dropping a malicious binary to disk.
Memory scanning augments the coverage of the CrowdStrike Falcon® sensor in detecting fileless threats, extending the protection already provided by Script Control and behavioral indicators of attack (IOAs).
The memory scanning technology allows the Falcon sensor to search through large amounts of process memory in a highly performant way, looking for malicious patterns indicative of a fileless attack. The memory scanning engine integrates Intel Threat Detection Technology accelerated memory scanning (AMS) into the Falcon sensor. Intel TDT AMS optimizes performance on Intel CPUs and offloads computation to the Intel integrated graphics processing unit (iGPU) when present. With high-performance scans, more memory can be scanned more often in order to find artifacts of malicious intrusion.
The accelerated memory scanning feature will be available as beta starting with Falcon sensor version 6.37 and is supported by sixth-generation or newer Intel CPUs with an enabled iGPU, running Windows 10 RS1 and above.
Fileless Attacks: A Threat from Initial Access to Persistence
More accurately termed “executable-less attacks,” the dominant feature of a fileless attack is that it does not drop traditional malware or a malicious executable file to disk. A fileless attack may rely on other types of files, such as weaponized document files, to achieve initial access, or on scripts (sometimes encrypted or encoded) to aid in execution. However, it is carried out without an executable file to scan — the attack itself is carried out entirely in memory.
Initial access is often achieved through the same techniques as executable-based attacks, such as browser or application exploits or phishing and social engineering attacks. Once a foothold is gained, fileless attacks need to find novel ways to execute malicious code and gain persistence. Execution of malicious logic and lateral movement is often carried out by “dual-use” applications, also called “living off the land” binaries or “LOLbins.” These dual-use attacks use legitimate applications, scripts and administrative tools to accomplish their malicious purpose. LOLbins include both native applications and scripting tools like PowerShell, MSHTA, Windows Management Instrumentation (WMI), regsvr32 and Task Scheduler. These tools and techniques were used in fileless attacks including Cobalt Strike malware, the Helminth trojan (see CrowdStrike Intelligence Tipper: CSIT-16096 PowerShell-Based Malware Used Against Middle Eastern Financial Sector Targets) and PoshSpy.
Execution may alternatively be carried out by code injection attacks, whereby shellcode injection or reflective DLL loading is used to run code in either the compromised process or a remote process. Cobalt Strike malware, Kovter (see CrowdStrike Intelligence Tipper: CSIT-17083 Kovter Bot Analysis) and NotPetya are known to use code injection, reflective loading or process hollowing to achieve malicious execution.
By not dropping and executing a malicious binary itself, fileless attacks need to find other ways to gain persistence. Persistence requires both a location to store code or data and a means to trigger malicious code or script launch. Dropping scripts, storing malicious code or scripts in the registry, or using LOLbins like WMI or Task Scheduler are all strategies to achieve persistence. These techniques are associated with in-the-wild activity for Poweliks and Kovter malware, PoshSpy attacks and the Helminth backdoor.
Each of these stages (initial access, execution and persistence) leaves behind unique and revealing artifacts of intrusion in memory. While memory scanning is already a valuable forensics tool, it does not need to be limited to post-breach incident responses — but it can be used to detect attacks in progress.
Memory Scanning Enables a New Level of Visibility and Protection
Historically, there’s been a substantial impact on CPU performance when scanning memory, limiting its ability to be used broadly for attack detection. To meet the threat of fileless attacks in a performant way, CrowdStrike partnered with Intel Corporation to integrate its Intel TDT AMS into our Falcon sensor. With Intel TDT AMS, the Falcon sensor can scan large swaths of a program’s virtual memory looking for artifacts of a malicious intrusion.
From exploitation to execution and impact, the Falcon platform identifies and protects against fileless attacks through behavioral IOAs composed of data from features like Script Control, Call Stack Analysis and Additional User Mode Data. Memory scanning plugs seamlessly into the complex system of events and behaviors on the Falcon platform, providing a new level of visibility and protection.
Byte Pattern Memory Scanning
Memory scanning identifies a process of interest (the “target process”) and iterates through its memory space to identify malicious artifacts. These artifacts could include shellcode patterns, unique strings or malicious patches.
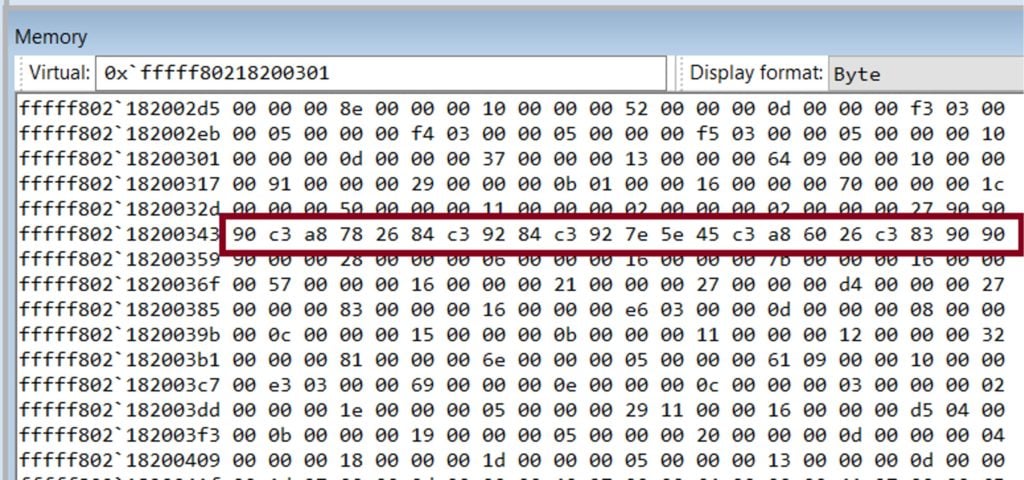 Figure 1. Kernel debugger view of a sample malicious byte pattern found in the memory of a suspect process
Figure 1. Kernel debugger view of a sample malicious byte pattern found in the memory of a suspect processA memory scan is defined by high-fidelity pattern specifications and rules around when and where the scan for those patterns should be performed. A triggering mechanism describes either a routine or potentially suspicious circumstance when the memory scan should be initiated. The memory pattern specification describes the pattern itself and provides optional hints as to the type of memory in which the pattern should be found. For example, shellcode might only be expected to fall in executable memory, but unique strings in read-only memory. These memory description down-selects provide both a performance and a precision benefit. Only the necessary memory is scanned and evaluated, which saves cycles and improves efficacy by allowing for more precise specifications.
When a memory pattern scan is initiated, the memory scan component will acquire the specified chunks of memory from the target process into the scanning process. Like the other workloads in the CrowdStrike Falcon® user-mode arsenal, the scanning process is run as a secure container on the endpoint. Once the memory has been acquired, the scanning process iterates through the scanned memory using the Intel TDT AMS high-performance pattern-matching algorithm, which has been optimized to run as a massively parallelized workload.
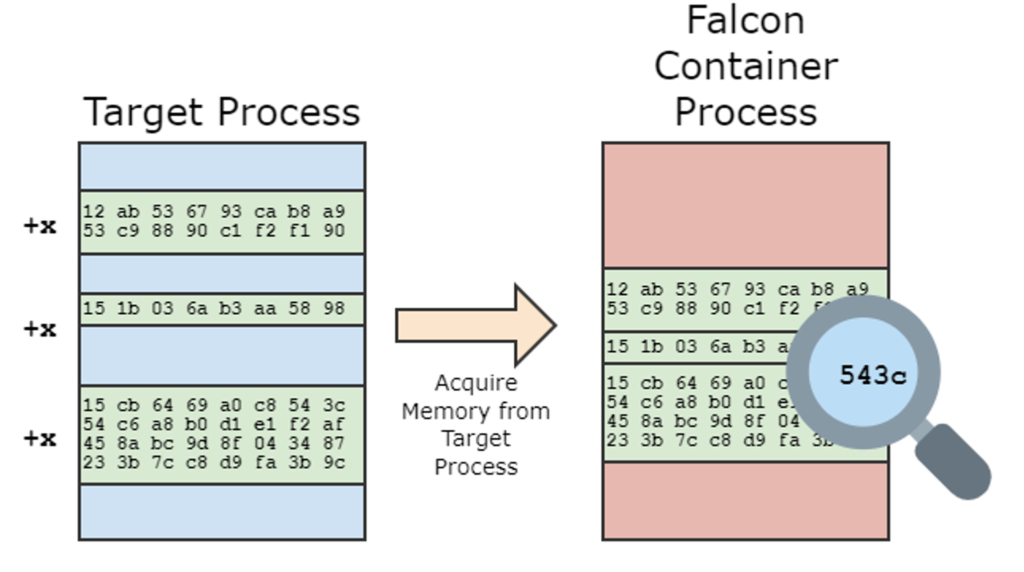 Figure 2. The Falcon container process acquires pages of executable memory from the target process and runs an accelerated memory scan on the contents, searching for the malicious byte pattern
Figure 2. The Falcon container process acquires pages of executable memory from the target process and runs an accelerated memory scan on the contents, searching for the malicious byte patternBuilding a High-Performance Solution
Traditionally both a CPU- and time-intensive operation, memory scanning is made feasible through optimizations at all levels of the design.
The partnership with Intel TDT AMS and integration design decisions prioritize performance, resulting in a pattern-matching algorithm that is optimized for execution on Intel hardware and that takes advantage of multi- and many-core architectures. The whole system benefits from careful algorithm choices and deep knowledge of Windows internals, leading to a design that maximizes performance of time-consuming operations. Design flexibility allows memory to be logically down-selected to only the parts that matter for the scan, while guardrails on memory scan size and limits on CPU utilization limit the disruption to the system and the end user’s experience.
Finally, Intel TDT AMS intelligently offloads the pattern-matching computations to the Intel integrated GPU when available, taking advantage of both the many-core GPU and the system-on-a-chip architecture with a shared memory controller. Early testing showed that Intel TDT AMS executed the compute-heavy workload at 4 to 7 times the performance of naive CPU implementations.
CrowdStrike Responds to Dynamic Threats in Real Time
Continuously escalated threats and the exploitation of zero-day vulnerabilities can only be stopped with a dynamic solution that can respond to new threats in real time.
Detection of fileless attacks starts from the same point as detection of traditional malware-based attacks. CrowdStrike’s dedicated reverse engineers, research and response teams, and Falcon OverWatch™ threat hunting team analyze real-world data and in-the-wild malicious scripts and tools 24 hours a day. Using their research and leveraging the dynamic content updates of the Falcon platform, CrowdStrike’s rapid response teams can deploy new behavioral IOAs at any time. With the addition of memory scanning to the CrowdStrike Falcon® sensor, these rapid response teams can release new memory pattern specifications and rules from the cloud to CrowdStrike customer endpoints within minutes.
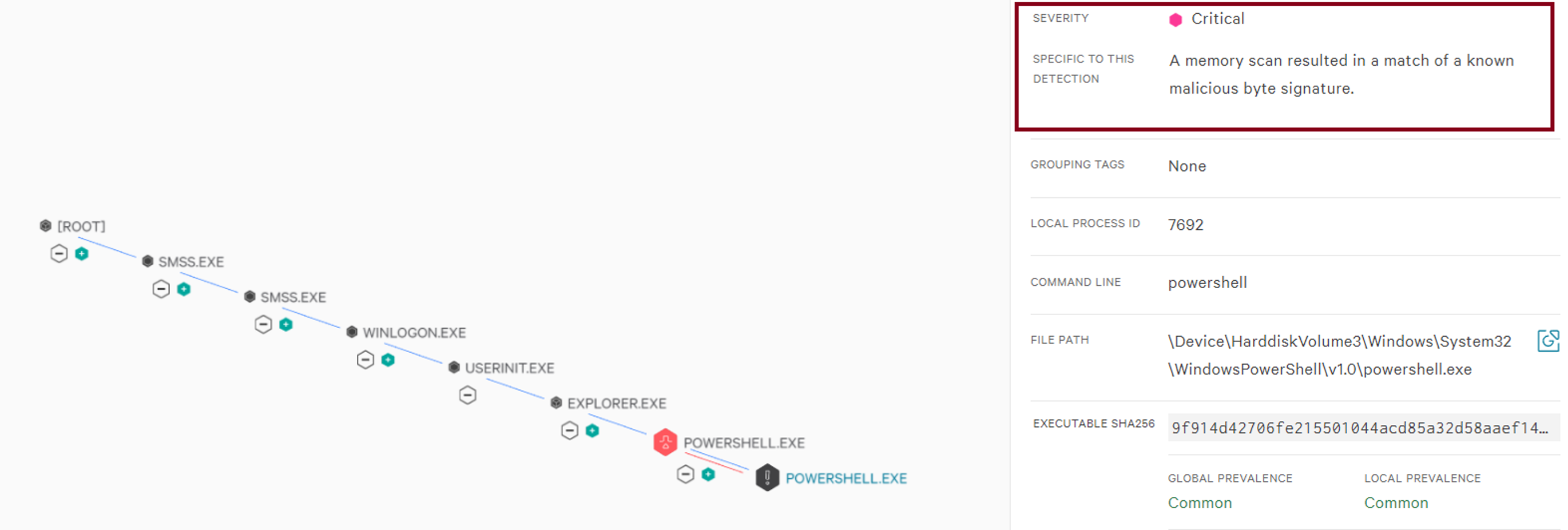
 Figure 3. The resulting event from a memory scan, showing that the result was a match for the byte pattern
Figure 3. The resulting event from a memory scan, showing that the result was a match for the byte patternCrowdStrike Memory Scanning Release Details
Memory scanning will be available in beta starting with Falcon sensor version 6.37. CrowdStrike customers can reach out to their technical account manager to join the beta release. The memory scanning beta is currently available for systems powered by sixth generation or newer Intel CPUs with an enabled Intel integrated GPU and associated drivers, running Windows 10 RS1 and above. A future release of the Falcon sensor will expand the supported platforms and CPUs.
Additional Resources
- Read about a CrowdStrike Falcon® feature, Hardware Enhanced Exploit Detection, that leverages a CPU feature — Intel Processor Trace (Intel PT) — to detect and prevent code reuse exploits: CrowdStrike Strengthens Exploit Protection Using Intel CPU Telemetry.
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers, data and identities.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and learn how true next-gen AV performs against today’s most sophisticated threats.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)