Mobile devices have become critical endpoints for accessing enterprise applications, systems and data. Adversaries know this all too well, as evidenced by the growing numbers of attacks that target mobile devices. Verizon’s 2022 Mobile Security Index found almost half (45%) of enterprises had recently suffered a mobile-related compromise involving devices in the last 12 months — almost double the amount compared to the year prior.
High-profile attacks leveraging mobile malware continue to happen, such as the Pegasus Spyware campaign, first observed in 2021 and more recently in September 2023. While this trend impacts every organization, protecting mobile devices from attack has rapidly become a top priority for small and medium-sized businesses (SMBs). A recent survey shows SMBs spend as much as 70% of their security budget on mobile security.
Mobile threat defense (MTD) refers to the growing technology category aimed at countering security threats on iOS and Android devices. With CrowdStrike Falcon® for Mobile, CrowdStrike’s MTD offering, customers can extend our industry-leading endpoint detection and response (EDR) and extended detection and response (XDR) to Android and iOS devices, enabling them to manage diverse endpoint fleets through a single integrated console. We’re excited to share the following innovations released for Falcon for Mobile aimed at streamlining mobile device enrollment, advancing detection capabilities for mobile-specific adversary tradecraft and accelerating incident response.
Expanded Detection for Advanced Mobile Threats
Custom Indicator of Compromise (IOC) Management
Falcon for Mobile customers can now author and manage custom indicators of compromise (IOCs). This capability enables our customers to block any domain, IP or subdomain they consider a risk. Many organizations are also using custom IOCs to block traffic to specific apps or browsers, a scenario that has gained prominence with the recent ban of TikTok across government devices. Falcon for Mobile’s custom IOCs can be created and managed via the same CrowdStrike API for traditional endpoints, enabling customers to retrieve, upload and search for IOCs using indicators provided by threat feeds they have access to.
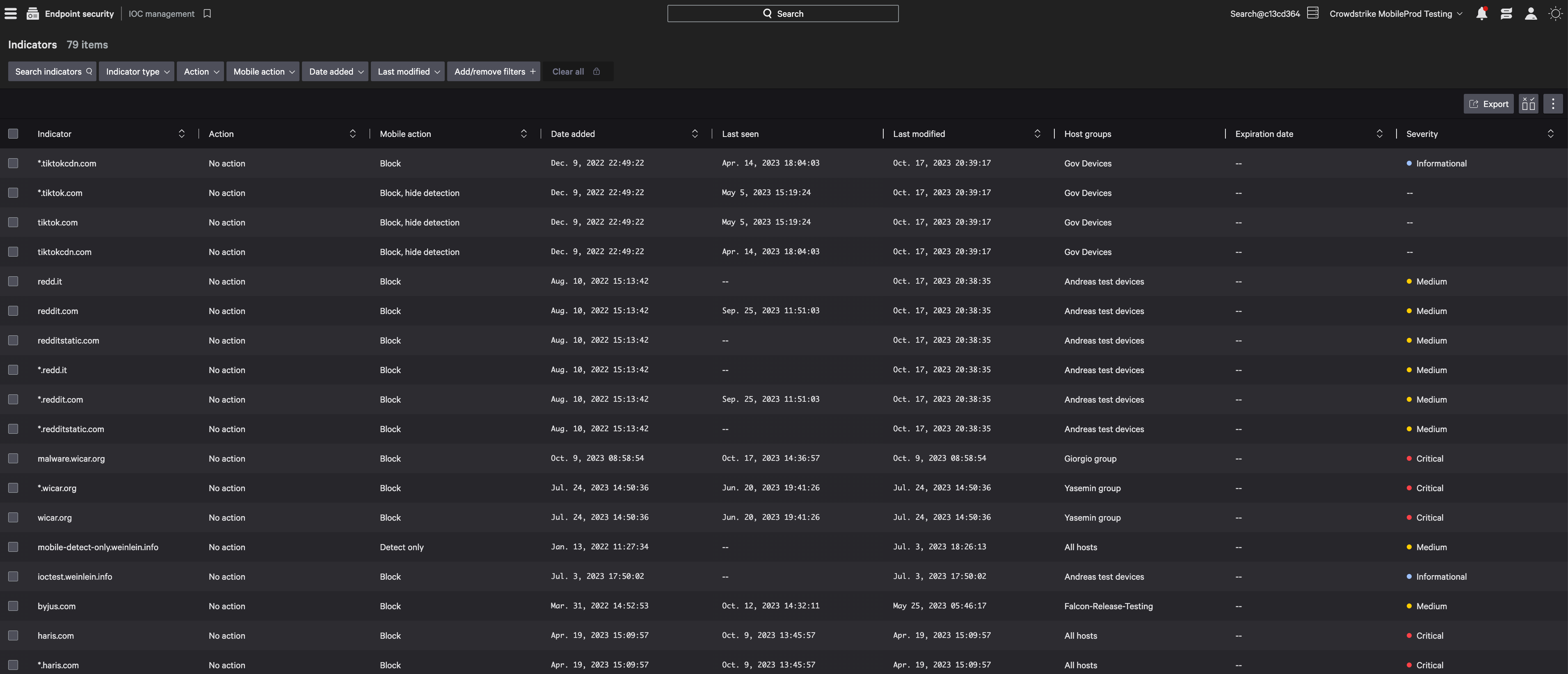 Figure 1. Falcon for Mobile allows organizations to create and manage custom IOCs (click to enlarge)
Figure 1. Falcon for Mobile allows organizations to create and manage custom IOCs (click to enlarge)Accelerating Investigations with Automated App Analysis on Android and the Falcon Platform’s Built-in Sandbox
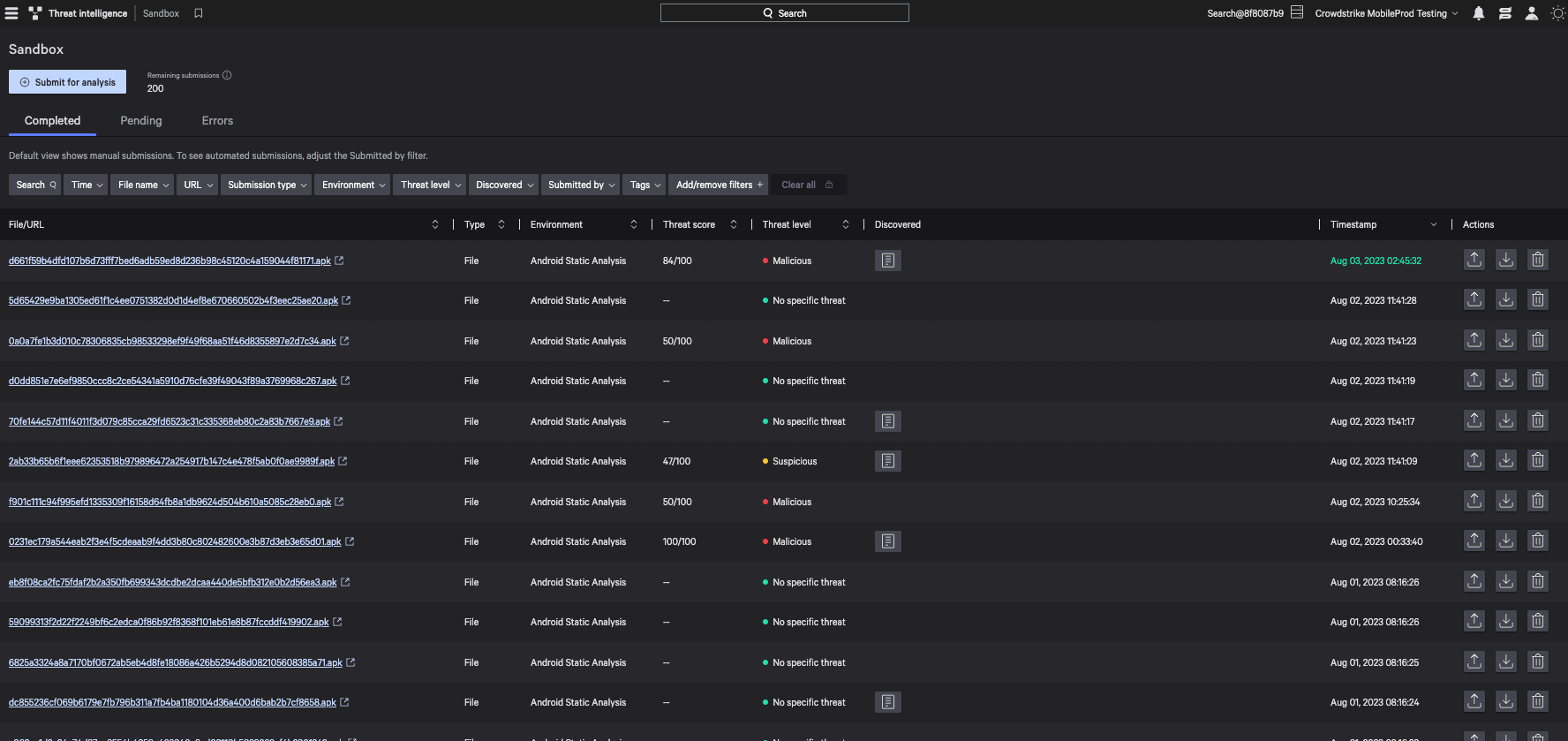
To reduce response and investigation times, Falcon for Mobile now automatically sends suspicious Android applications to the CrowdStrike Falcon® platform’s built-in sandbox for analysis, enabling organizations to rapidly identify anti-virtualization techniques or attempts by mobile-first adversaries to activate spyware. IT and device managers can then leverage mobile device management (MDM) solutions to globally remove suspicious or malicious apps from devices in their fleets.
 Figure 2. Analysis and report of an Android application in the Falcon platform’s built-in sandbox (click to enlarge)
Figure 2. Analysis and report of an Android application in the Falcon platform’s built-in sandbox (click to enlarge)New Automated Response Integrations
Automated Response Actions for Mobile Threats
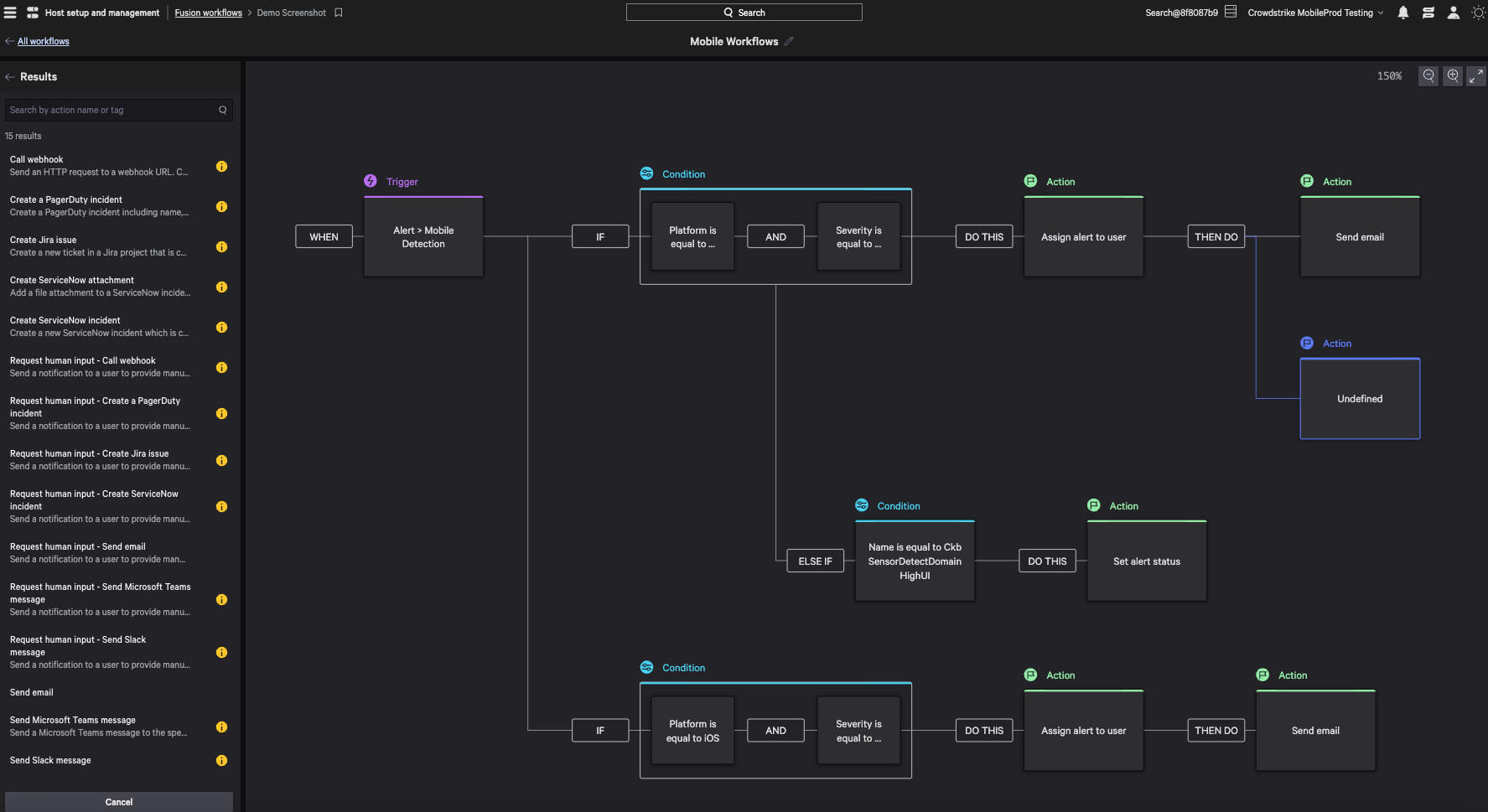
Earlier this year, we launched automated response actions for mobile detections. Enabled via integration with CrowdStrike Falcon® Fusion, CrowdStrike’s integrated security orchestration automation and response (SOAR) framework, Falcon for Mobile customers can now build and customize automated workflows, triggered by mobile detections. This enables organizations of all sizes — especially organizations with smaller security and IT teams — to scale their output by accelerating detection, investigation and response actions, notably in the case of repetitive, manual tasks.
With Falcon Fusion, incident responders can configure distinct analyst assignments based on unique threat indicators and can further customize how notifications or tickets are sent (e.g., Slack, PagerDuty, Microsoft Teams, email, ServiceNow, Jira). As shown in Figure 3, we can use the example of a new mobile detection triggering multiple workflows, with one alerting select users based on the severity of the threat, and another alerting other groups of users if the impacted endpoint is an iOS device.
Automated Mitigation via Mobile Network Containment
Customers can mitigate mobile threats by activating a new Network Containment action in the Falcon console for supervised (iOS) or fully managed (Android) devices. This feature expands Falcon for Mobile’s network preventions, enabling customers to respond to mobile threats using the same containment functionality they use for traditional endpoints within the console.
For other deployment modes, such as unsupervised or Work Profile devices, this mechanism can be used to enforce conditional access for corporate resources, such as blocking access to enterprise apps to protect a customer’s intellectual property. Network Containment can be enabled manually via the host management console as part of active investigations or can be configured to be triggered automatically as part of a Falcon Fusion workflow (Figure 4).
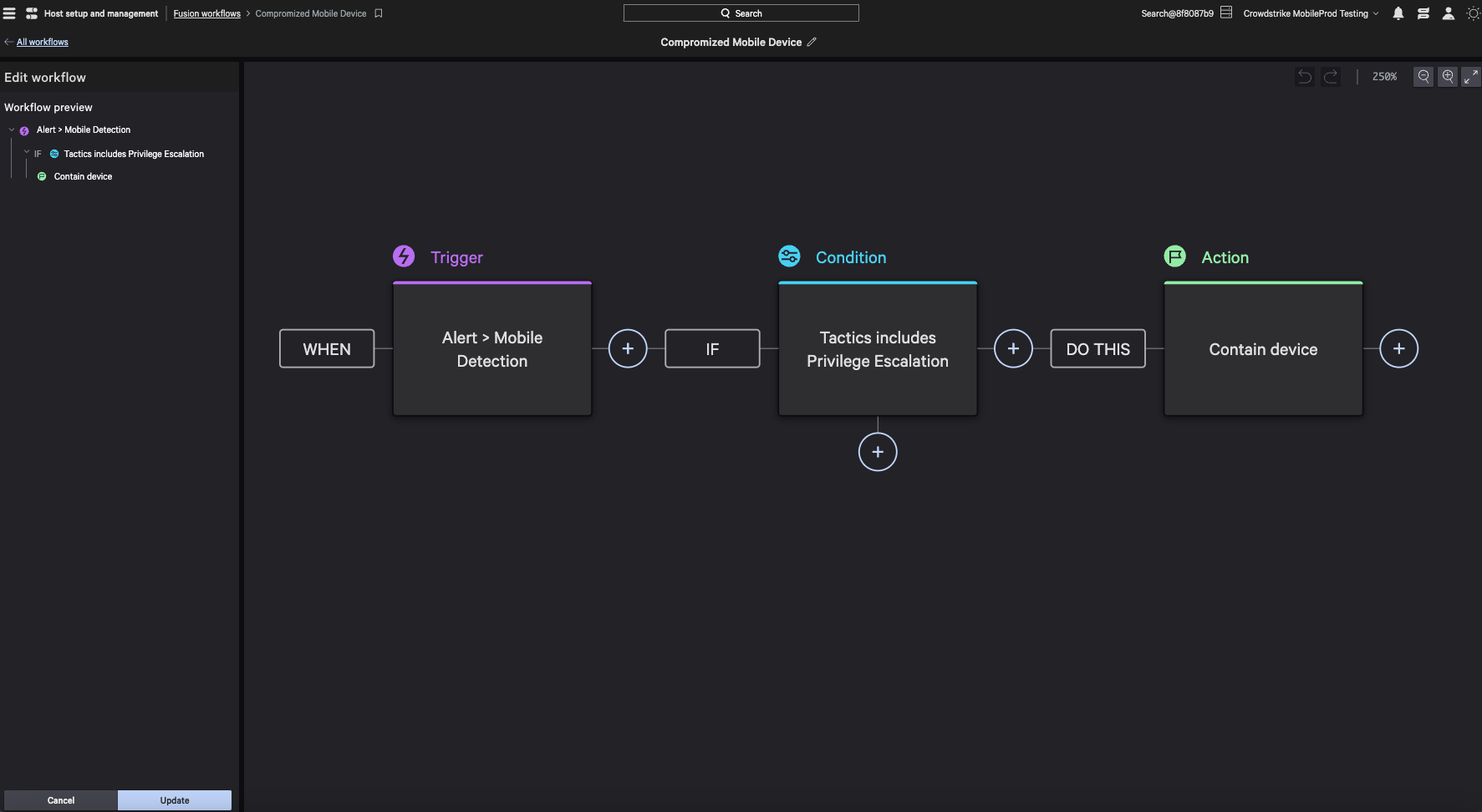 Figure 4. Falcon for Mobile customers can configure Falcon Fusion workflows for mobile detections to automate network containment of impacted hosts (click to enlarge)
Figure 4. Falcon for Mobile customers can configure Falcon Fusion workflows for mobile detections to automate network containment of impacted hosts (click to enlarge)Falcon for Mobile has also released a new mobile policy to protect devices against man-in-the-middle attacks (MiTM), automating network containment in instances where a user has connected to a rogue WiFi network, as shown in Figure 5.
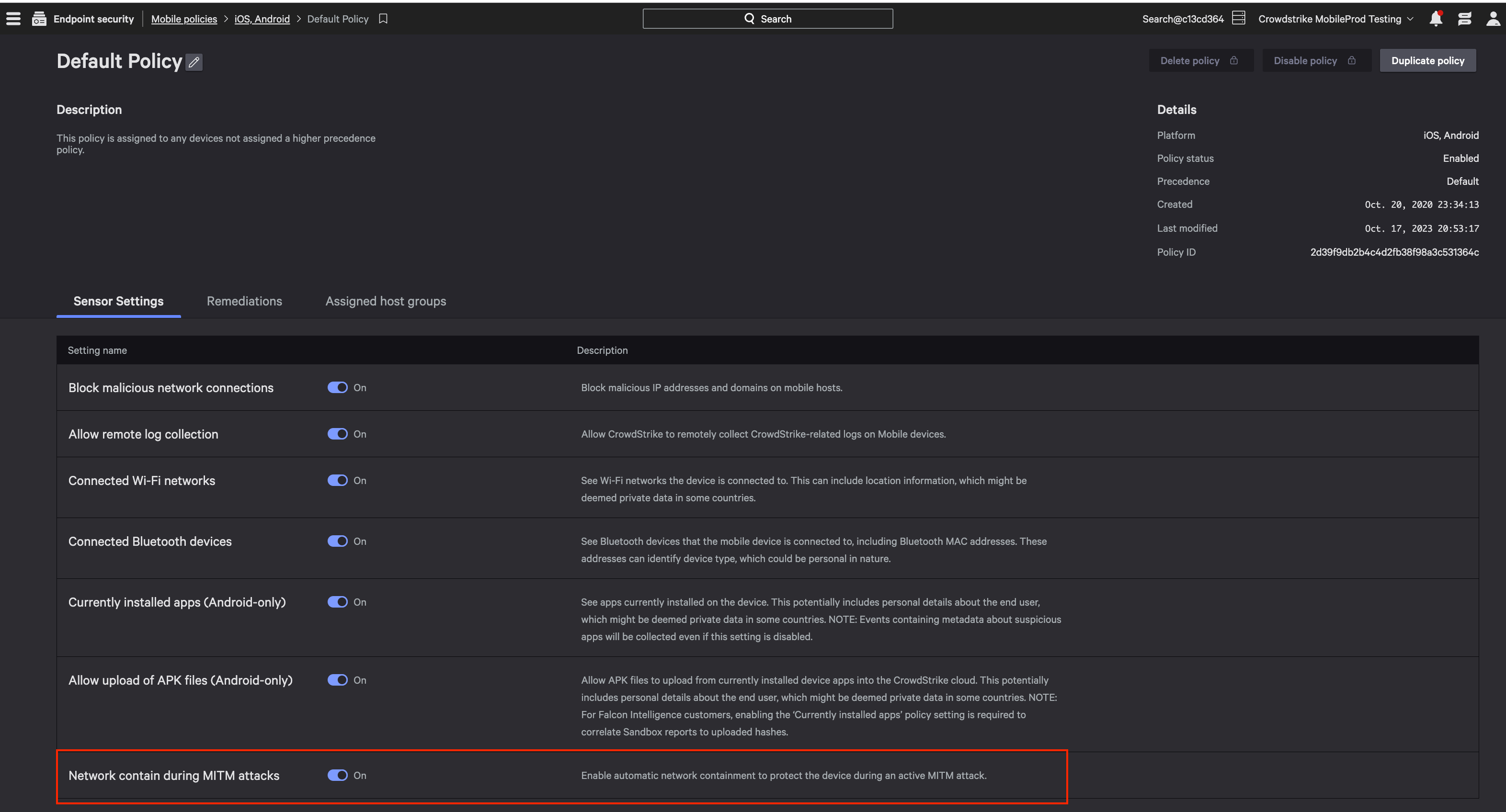 Figure 5. Falcon for Mobile customers can now enable automated network containment during MiTM attacks (click to enlarge)
Figure 5. Falcon for Mobile customers can now enable automated network containment during MiTM attacks (click to enlarge)Conditional Access for Corporate Assets
Falcon for Mobile now enables administrators to enforce conditional access to corporate assets. Users can trigger Falcon Fusion workflows using Falcon for Mobile’s custom IOCs to automatically move compromised devices to different host groups. This allows an administrator to configure the specific network resources a device can access, denying access to sensitive resources or systems whenever a device is under an elevated threat level.
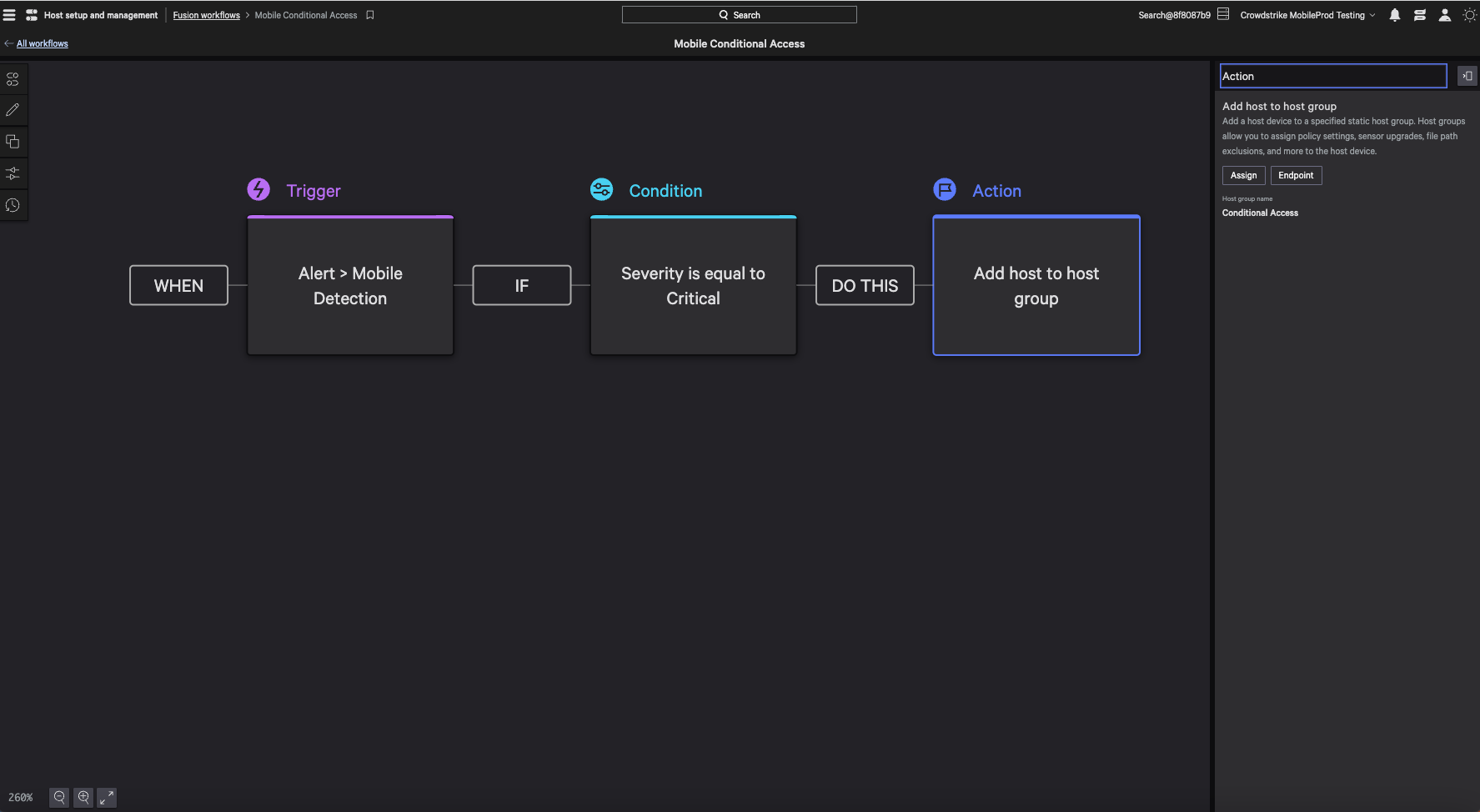 Figure 6. Falcon Fusion workflow that automatically adds hosts to a new host group if a critical-severity mobile threat is detected (click to enlarge)
Figure 6. Falcon Fusion workflow that automatically adds hosts to a new host group if a critical-severity mobile threat is detected (click to enlarge)Enabling Greater Ease-of-Use
Zero-Touch Deployment
Our customers have ever-expanding endpoint fleets, elevating the importance of a fast, simplified deployment and enrollment process. To enable accelerated onboarding, Falcon for Mobile customers can automatically deploy and activate the Falcon agent through many commonly used MDMs, eliminating the need for end users to open the CrowdStrike mobile app. This specific functionality is available for supervised iOS devices and for most supervised/unsupervised Android devices.
Customers can now leverage our new MDM enrollments wizard to retrieve and configure the exact settings they need for the MDM used by their organization. The enrollment wizard provides users with a list of values that then need to be used within the MDM and that are presented along with the option to download a configuration file for supervised iOS devices.
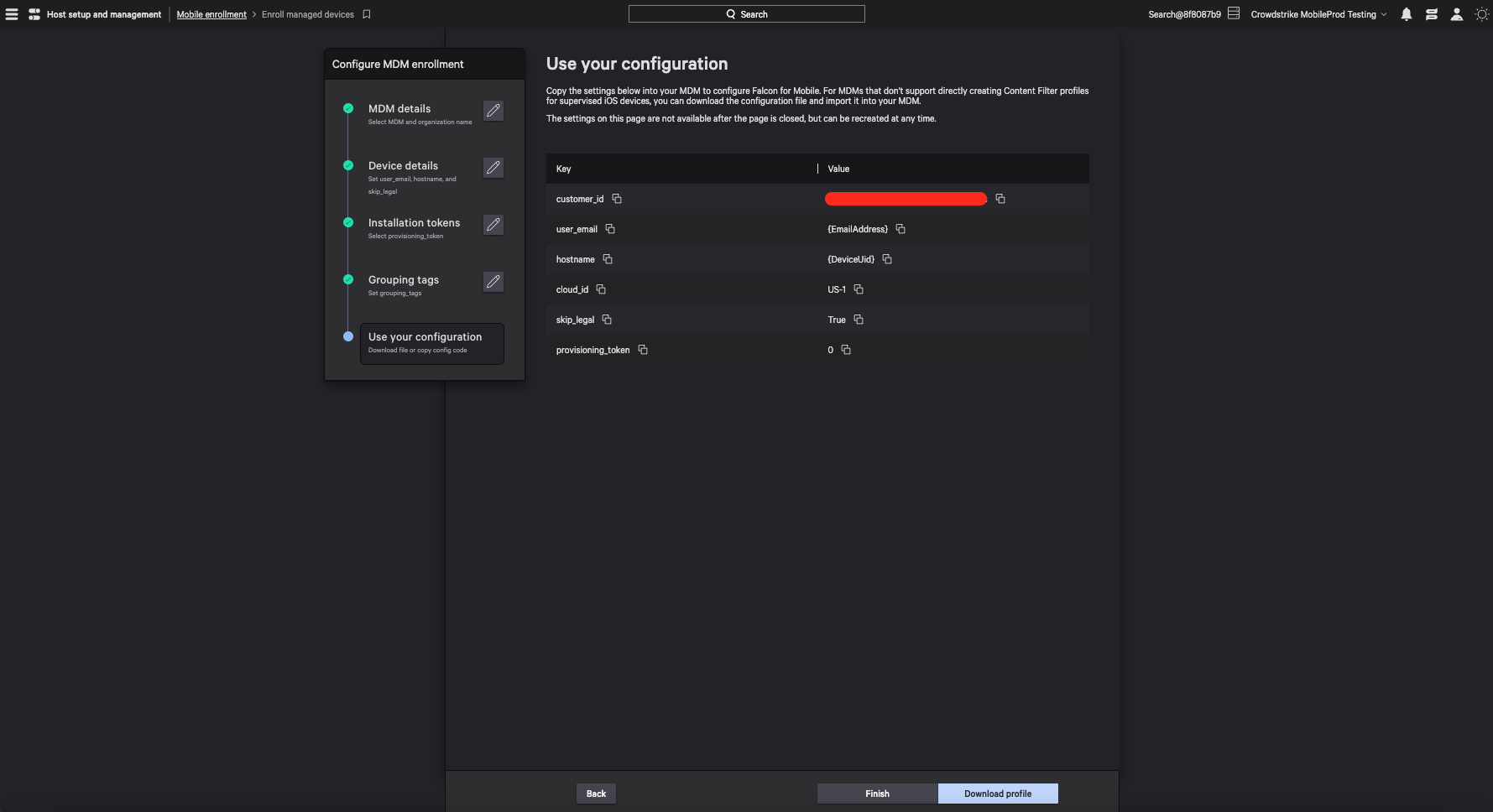 Figure 7. The Falcon for Mobile MDM enrollments wizard allows users to easily configure profiles for their mobile devices (click to enlarge)
Figure 7. The Falcon for Mobile MDM enrollments wizard allows users to easily configure profiles for their mobile devices (click to enlarge)Integrated and Unified Dashboards
To further support accelerated threat hunting and streamlined security operations, CrowdStrike customers can now access Falcon for Mobile dashboards in the UI of the Falcon console. By leveraging a single unified platform to monitor all endpoint classes, customers obtain a holistic understanding of activity that spans devices and identities across their estate. This will enable customers to more easily monitor activity across mobile hosts, including real-time information around OS distribution, platform versions and detections by severity, enabling them to seamlessly drill into activity across their mobile devices as they already do with traditional endpoints. Our intuitively designed dashboards focus analyst attention on critical alerts and surface real-time intelligence to enable accelerated mobile threat hunting.
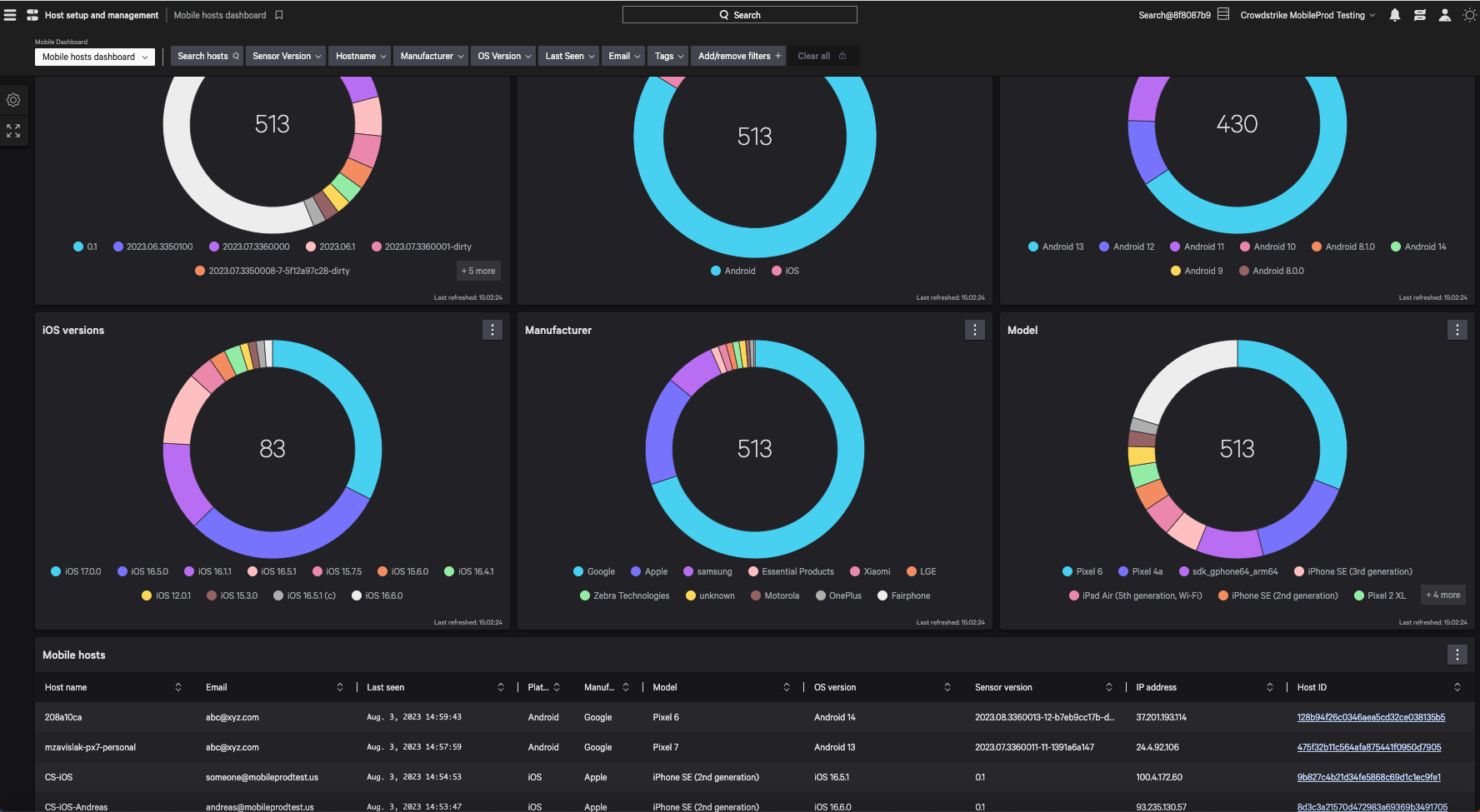 Figure 8. Users can monitor and manage diverse mobile devices in their fleet in the Falcon console (click to enlarge)
Figure 8. Users can monitor and manage diverse mobile devices in their fleet in the Falcon console (click to enlarge)Moreover, each user will be able to customize their dashboards to surface the information that is most pertinent to their organization, with easy-to-use drag-and-drop tiles that list real-time detections, analyze trends over time and provide visual breakdowns of endpoint classes.
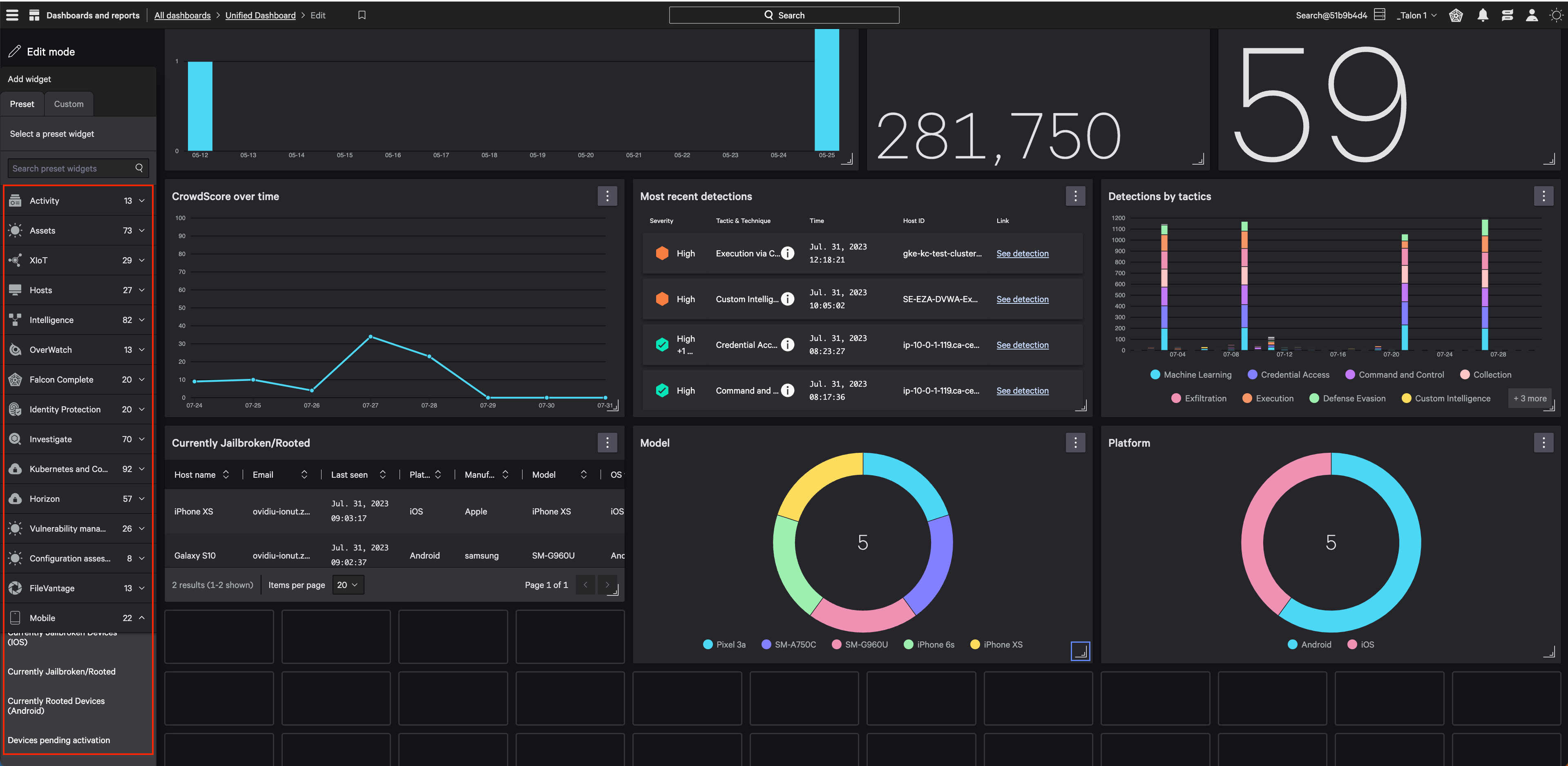 Figure 9. Users can customize their mobile dashboards to surface critical indicators for the health of their mobile fleets — this can include recent detections, their CrowdScore over time and tables of jailbroken hosts (click to enlarge)
Figure 9. Users can customize their mobile dashboards to surface critical indicators for the health of their mobile fleets — this can include recent detections, their CrowdScore over time and tables of jailbroken hosts (click to enlarge)Additional Resources
- To find out more about CrowdStrike’s industry-leading approach to endpoint detection and response, visit the CrowdStike Falcon® Endpoint Security portfolio page.
- Request a free trial of the industry-leading CrowdStrike Falcon® platform.
- Learn more about Falcon for Mobile, CrowdStrike’s offering for mobile threat defense (MTD).






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)