On Friday May 30, 2014, an unprecedented botnet disruption was initiated by the United States Department of Justice (DOJ) in coordination with numerous law enforcement and industry partners. This coordinated effort was the culmination of months of activities, including technical analysis, legal documentation, and a tremendous amount of investigation. The CrowdStrike Intelligence team provided technical expertise to permit the enforcement of a Temporary Restraining Order (TRO), which successfully disrupted not only the infamous Gameover Zeus (GOZ) botnet, but also Cryptolocker, which was using GOZ as an installation vector.
Gameover Zeus
Gameover Zeus is a complicated botnet with numerous layers of infrastructure. When a machine is infected, the bot may use several mechanisms to communicate with its human handler (more on the adversary later). The bot will use a proprietary Peer-to-Peer (P2P) communication protocol. P2P is commonly associated with file sharing and data transfers.
In the case of GOZ, what is being shared by infected hosts is not music or video, but new updates, configurations/taskings, and lists of neighbor peers that are currently live. Some parts of the protocol use digital signatures to prevent unauthorized data from being distributed across the P2P layer. If the P2P cannot be contacted using known peers, a Domain Generating Algorithm (DGA) is the fallback channel.
The deterministic DGA can generate 1,000 domains per week across a limited set of Top Level Domains (TLD), specifically .com, .net, .ru, .org, info, and .biz. The adversary knows what domains will be generated by the bots, allowing them to periodically enable domains by registering them and using them for command and control.
GOZ is commonly used to inject into victim web browsers in order to compromise account credentials. The GOZ adversaries, as documented in the criminal complaint introduced in the western district of Pennsylvania, notoriously targeted Automated Clearing House (ACH) accounts in order to make large fraudulent transfers. This malware was also available to distribute other malware packages, which is addressed in terms of Cryptolocker as an example. Lesser known about this malware, in addition to the e-crime motivation, was the tasking of collection for non-financial-related data. Essentially, these actors went after anything and everything, and some indications exist that this capacity was available on a contractual basis.
Cryptolocker
The package known as Cryptolocker was also impacted by the recent disruption. Cryptolocker is a particularly infamous piece of code that is known as “ransomware”; this is because it encrypts all of the important files on an infected machine and holds them for ransom. The malware that was often observed being distributed via GOZ would search for popular file extensions on an infected host, and use RSA asymmetric encryption to encrypt the file. Once the encryption was complete, a message would be displayed to the user.
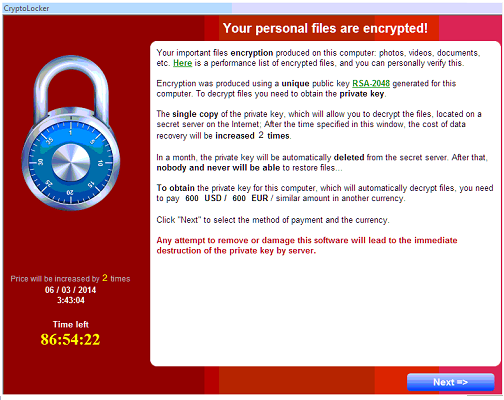 At this point the user had the option to pay the ransom (typically around 2 BTC) and have a decryption tool with the key provided. The mechanism by which Cryptolocker is able to negotiate the asymmetric key exchange was also established using a DGA.
Disruption
The technical efforts at this disruption, which were supported by CrowdStrike and other researchers, were extremely well coordinated; this was a necessity to prevent the adversary from reacquiring control over the botnet. In the case of GOZ, the technical approach required a few steps: the DGA had to be mitigated, the P2P channel needed to be disrupted, and lastly the backend needed to be taken offline.
The DGA mitigation was accomplished by reverse engineering the algorithm used for domain generation. This was used to create two large lists of domains (one for .ru and one for the other TLDs) that were sinkholed in order to prevent the adversary from using them to regain control of the botnet.
The
At this point the user had the option to pay the ransom (typically around 2 BTC) and have a decryption tool with the key provided. The mechanism by which Cryptolocker is able to negotiate the asymmetric key exchange was also established using a DGA.
Disruption
The technical efforts at this disruption, which were supported by CrowdStrike and other researchers, were extremely well coordinated; this was a necessity to prevent the adversary from reacquiring control over the botnet. In the case of GOZ, the technical approach required a few steps: the DGA had to be mitigated, the P2P channel needed to be disrupted, and lastly the backend needed to be taken offline.
The DGA mitigation was accomplished by reverse engineering the algorithm used for domain generation. This was used to create two large lists of domains (one for .ru and one for the other TLDs) that were sinkholed in order to prevent the adversary from using them to regain control of the botnet.
The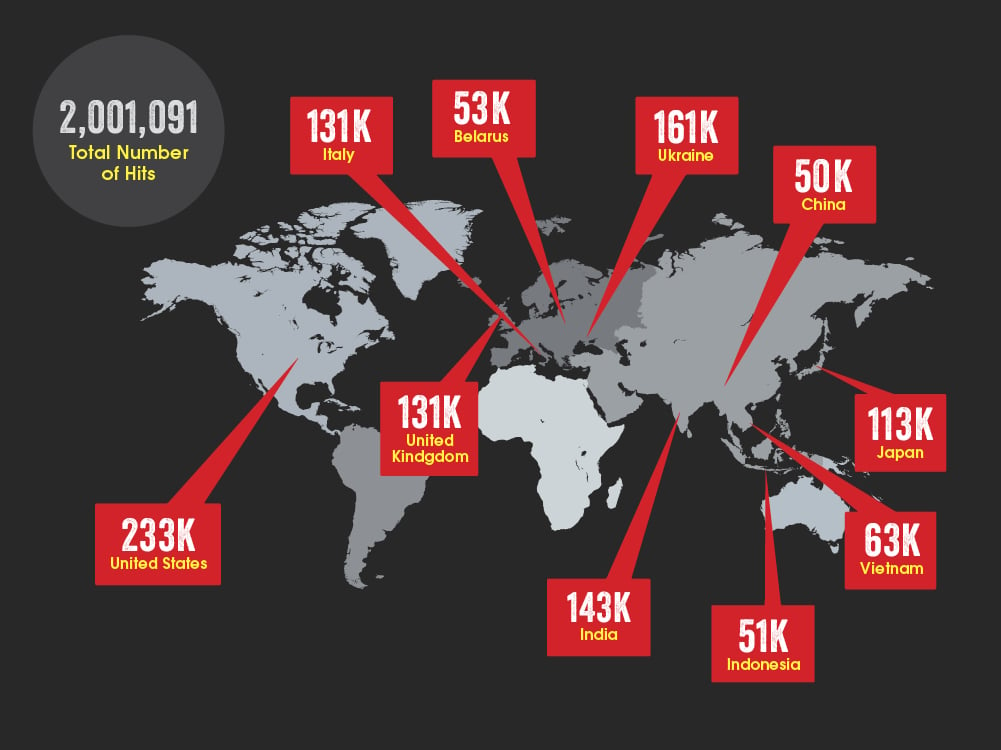 To date, the impact of this action resulted in the successful quarantining of more than 2,000,000 infected machines. GOZ implements a unique ID per infected machine that allows for accurate tracking of infection distributions. Nevertheless, the metrics of understanding the success of this action can be a little more difficult than one might imagine. There are lots of researchers who have created custom tools to monitor and measure this botnet. Furthermore, there have been numerous traffic injection and other disruptive attacks against this infrastructure. In short, there is a lot of weird stuff floating around in the GOZ space. To attempt to get the truest metrics around the data collected, we have deduplicated both the bot IDs generated by GOZ and IP addresses. This way, hosts that announce multiple IDs from one single IP address, a technique that is used by some of the monitoring systems, are only counted once.
While this method does not account for multiple real infections behind gateways that should be counted individually, it is a simple means to make sure that the total number of infections is not overestimated. The number presented above should therefore be regarded as a lower bound. A breakdown of the infections per country is quite interesting and perhaps unexplainable without much deeper analysis and investigation.
The U.S. was predictably on top of the list; this is likely because it was also the most targeted country. High infection rates were also detected in Ukraine, India, and Japan. India is heavily populated, which may explain that, but the Ukraine infection rate is certainly unusual. Perhaps there was nationalistic targeting of Ukraine; given the recent hostilities between the Russian Federation and Ukraine, it is possible there was patriotic motivation in targeting Ukraine. The researchers involved will be combing through this data for some time trying to better understand the impact of this disruption and to reconstruct the stories of what happened in three years of GOZ targeting.
Adversary
Behind every piece of malicious software, exploit, or attack, there is an adversary. These adversaries are responsible for building malware, creating the exploits and tools, and building the infrastructure required to launch an operation. Whether these operations are targeted or not, there is a human or humans pulling together the components necessary to accomplish their objective.
We believe that understanding who these adversaries are and what their motivation is can help build appropriate defenses and ultimately change the calculus of deterrence in these attacks by raising the cost of a successful attack. In the case of this investigation due to the involvement of the DOJ and Law Enforcement, criminal charges were able to be filed. Several people were implicated, however one individual has been the primary focus of this investigation: Evgeniy Mikhailovich Bogachev:
To date, the impact of this action resulted in the successful quarantining of more than 2,000,000 infected machines. GOZ implements a unique ID per infected machine that allows for accurate tracking of infection distributions. Nevertheless, the metrics of understanding the success of this action can be a little more difficult than one might imagine. There are lots of researchers who have created custom tools to monitor and measure this botnet. Furthermore, there have been numerous traffic injection and other disruptive attacks against this infrastructure. In short, there is a lot of weird stuff floating around in the GOZ space. To attempt to get the truest metrics around the data collected, we have deduplicated both the bot IDs generated by GOZ and IP addresses. This way, hosts that announce multiple IDs from one single IP address, a technique that is used by some of the monitoring systems, are only counted once.
While this method does not account for multiple real infections behind gateways that should be counted individually, it is a simple means to make sure that the total number of infections is not overestimated. The number presented above should therefore be regarded as a lower bound. A breakdown of the infections per country is quite interesting and perhaps unexplainable without much deeper analysis and investigation.
The U.S. was predictably on top of the list; this is likely because it was also the most targeted country. High infection rates were also detected in Ukraine, India, and Japan. India is heavily populated, which may explain that, but the Ukraine infection rate is certainly unusual. Perhaps there was nationalistic targeting of Ukraine; given the recent hostilities between the Russian Federation and Ukraine, it is possible there was patriotic motivation in targeting Ukraine. The researchers involved will be combing through this data for some time trying to better understand the impact of this disruption and to reconstruct the stories of what happened in three years of GOZ targeting.
Adversary
Behind every piece of malicious software, exploit, or attack, there is an adversary. These adversaries are responsible for building malware, creating the exploits and tools, and building the infrastructure required to launch an operation. Whether these operations are targeted or not, there is a human or humans pulling together the components necessary to accomplish their objective.
We believe that understanding who these adversaries are and what their motivation is can help build appropriate defenses and ultimately change the calculus of deterrence in these attacks by raising the cost of a successful attack. In the case of this investigation due to the involvement of the DOJ and Law Enforcement, criminal charges were able to be filed. Several people were implicated, however one individual has been the primary focus of this investigation: Evgeniy Mikhailovich Bogachev:
 Actionable Intelligence
We always want to provide some way to take the intelligence that our team produces and help make it useful in an operational environment. The following YARA rules will enable you to identify live GOZ infections on a system by scanning running processes:
Actionable Intelligence
We always want to provide some way to take the intelligence that our team produces and help make it useful in an operational environment. The following YARA rules will enable you to identify live GOZ infections on a system by scanning running processes:
 At this point the user had the option to pay the ransom (typically around 2 BTC) and have a decryption tool with the key provided. The mechanism by which Cryptolocker is able to negotiate the asymmetric key exchange was also established using a DGA.
Disruption
The technical efforts at this disruption, which were supported by CrowdStrike and other researchers, were extremely well coordinated; this was a necessity to prevent the adversary from reacquiring control over the botnet. In the case of GOZ, the technical approach required a few steps: the DGA had to be mitigated, the P2P channel needed to be disrupted, and lastly the backend needed to be taken offline.
The DGA mitigation was accomplished by reverse engineering the algorithm used for domain generation. This was used to create two large lists of domains (one for .ru and one for the other TLDs) that were sinkholed in order to prevent the adversary from using them to regain control of the botnet.
The
At this point the user had the option to pay the ransom (typically around 2 BTC) and have a decryption tool with the key provided. The mechanism by which Cryptolocker is able to negotiate the asymmetric key exchange was also established using a DGA.
Disruption
The technical efforts at this disruption, which were supported by CrowdStrike and other researchers, were extremely well coordinated; this was a necessity to prevent the adversary from reacquiring control over the botnet. In the case of GOZ, the technical approach required a few steps: the DGA had to be mitigated, the P2P channel needed to be disrupted, and lastly the backend needed to be taken offline.
The DGA mitigation was accomplished by reverse engineering the algorithm used for domain generation. This was used to create two large lists of domains (one for .ru and one for the other TLDs) that were sinkholed in order to prevent the adversary from using them to regain control of the botnet.
TheP2P layer was disrupted by propagating a peer list that would prevent the adversary from introducing new peers, and would propagate throughout the P2P network. As this controlled list of peers propagated, the infected hosts were further isolated from their master and locked into the controlled sinkhole. All of this needed to be coordinated with the disruption of the botmaster’s backend systems, which would prevent them from being able to take action in the first few hours of the disruption to regain control of the botnet. Cryptolocker had fewer avenues for command and control; it used a DGA that was also reverse engineered, and the algorithm used to create a large list of domains that was similarly sinkholed to prevent the ability for Cryptolocker to encrypt files on victim machines. Impact
 To date, the impact of this action resulted in the successful quarantining of more than 2,000,000 infected machines. GOZ implements a unique ID per infected machine that allows for accurate tracking of infection distributions. Nevertheless, the metrics of understanding the success of this action can be a little more difficult than one might imagine. There are lots of researchers who have created custom tools to monitor and measure this botnet. Furthermore, there have been numerous traffic injection and other disruptive attacks against this infrastructure. In short, there is a lot of weird stuff floating around in the GOZ space. To attempt to get the truest metrics around the data collected, we have deduplicated both the bot IDs generated by GOZ and IP addresses. This way, hosts that announce multiple IDs from one single IP address, a technique that is used by some of the monitoring systems, are only counted once.
While this method does not account for multiple real infections behind gateways that should be counted individually, it is a simple means to make sure that the total number of infections is not overestimated. The number presented above should therefore be regarded as a lower bound. A breakdown of the infections per country is quite interesting and perhaps unexplainable without much deeper analysis and investigation.
The U.S. was predictably on top of the list; this is likely because it was also the most targeted country. High infection rates were also detected in Ukraine, India, and Japan. India is heavily populated, which may explain that, but the Ukraine infection rate is certainly unusual. Perhaps there was nationalistic targeting of Ukraine; given the recent hostilities between the Russian Federation and Ukraine, it is possible there was patriotic motivation in targeting Ukraine. The researchers involved will be combing through this data for some time trying to better understand the impact of this disruption and to reconstruct the stories of what happened in three years of GOZ targeting.
Adversary
Behind every piece of malicious software, exploit, or attack, there is an adversary. These adversaries are responsible for building malware, creating the exploits and tools, and building the infrastructure required to launch an operation. Whether these operations are targeted or not, there is a human or humans pulling together the components necessary to accomplish their objective.
We believe that understanding who these adversaries are and what their motivation is can help build appropriate defenses and ultimately change the calculus of deterrence in these attacks by raising the cost of a successful attack. In the case of this investigation due to the involvement of the DOJ and Law Enforcement, criminal charges were able to be filed. Several people were implicated, however one individual has been the primary focus of this investigation: Evgeniy Mikhailovich Bogachev:
To date, the impact of this action resulted in the successful quarantining of more than 2,000,000 infected machines. GOZ implements a unique ID per infected machine that allows for accurate tracking of infection distributions. Nevertheless, the metrics of understanding the success of this action can be a little more difficult than one might imagine. There are lots of researchers who have created custom tools to monitor and measure this botnet. Furthermore, there have been numerous traffic injection and other disruptive attacks against this infrastructure. In short, there is a lot of weird stuff floating around in the GOZ space. To attempt to get the truest metrics around the data collected, we have deduplicated both the bot IDs generated by GOZ and IP addresses. This way, hosts that announce multiple IDs from one single IP address, a technique that is used by some of the monitoring systems, are only counted once.
While this method does not account for multiple real infections behind gateways that should be counted individually, it is a simple means to make sure that the total number of infections is not overestimated. The number presented above should therefore be regarded as a lower bound. A breakdown of the infections per country is quite interesting and perhaps unexplainable without much deeper analysis and investigation.
The U.S. was predictably on top of the list; this is likely because it was also the most targeted country. High infection rates were also detected in Ukraine, India, and Japan. India is heavily populated, which may explain that, but the Ukraine infection rate is certainly unusual. Perhaps there was nationalistic targeting of Ukraine; given the recent hostilities between the Russian Federation and Ukraine, it is possible there was patriotic motivation in targeting Ukraine. The researchers involved will be combing through this data for some time trying to better understand the impact of this disruption and to reconstruct the stories of what happened in three years of GOZ targeting.
Adversary
Behind every piece of malicious software, exploit, or attack, there is an adversary. These adversaries are responsible for building malware, creating the exploits and tools, and building the infrastructure required to launch an operation. Whether these operations are targeted or not, there is a human or humans pulling together the components necessary to accomplish their objective.
We believe that understanding who these adversaries are and what their motivation is can help build appropriate defenses and ultimately change the calculus of deterrence in these attacks by raising the cost of a successful attack. In the case of this investigation due to the involvement of the DOJ and Law Enforcement, criminal charges were able to be filed. Several people were implicated, however one individual has been the primary focus of this investigation: Evgeniy Mikhailovich Bogachev:
 Actionable Intelligence
We always want to provide some way to take the intelligence that our team produces and help make it useful in an operational environment. The following YARA rules will enable you to identify live GOZ infections on a system by scanning running processes:
Actionable Intelligence
We always want to provide some way to take the intelligence that our team produces and help make it useful in an operational environment. The following YARA rules will enable you to identify live GOZ infections on a system by scanning running processes:
rule CrowdStrike_P2P_Zeus
{
meta:
copyright = "CrowdStrike, Inc"
description = "P2P Zeus (Gameover)"
version = "1.0"
last_modified = "2013-11-21"
actor = "Gameover Spider"
malware_family = "P2P Zeus"
in_the_wild = true
condition:
any of them or
for any i in (0..filesize) :
(
uint32(i) ^ uint32(i+4) == 0x00002606
and uint32(i) ^ uint32(i+8) == 0x31415154
and uint32(i) ^ uint32(i+12) == 0x00000a06
and uint32(i) ^ uint32(i+16) == 0x00010207
and uint32(i) ^ uint32(i+20) == 0x7cf1aa2d
and uint32(i) ^ uint32(i+24) == 0x4390ca7b
and uint32(i) ^ uint32(i+28) == 0xa96afd9d
and uint32(i) ^ uint32(i+32) == 0x0b039138
and uint32(i) ^ uint32(i+36) == 0xb3e50578
and uint32(i) ^ uint32(i+40) == 0x896eaf36
and uint32(i) ^ uint32(i+44) == 0x37a3f8c9
and uint32(i) ^ uint32(i+48) == 0xb1c31bcb
and uint32(i) ^ uint32(i+52) == 0xcb58f22c
and uint32(i) ^ uint32(i+56) == 0x00491be8
and uint32(i) ^ uint32(i+60) == 0x0a2a748f
)}
You can use this rule with CrowdStrike's free CrowdResponse tool to easily scan your systems for presence of Gameover Zeus.
If you have any questions about these signatures or want to hear more about CrowdStrike's adversary intelligence, please contact: intelligence@crowdstrike.com and inquire about Falcon Intelligence, our Cyber Threat Intelligence subscription.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































