CrowdStrike® Falcon® detections now align with the MITRE ATT&CK™ framework, a valuable tool that provides consistent, industry-standard terminology for describing and analyzing detections. Sometimes, security professionals also need a way to clearly explain adversary behavior to non-security leadership. To help with this, CrowdStrike evolved the ATT&CK model by adding more conversational language. I spoke at MITRE’s inaugural ATT&CKcon and presented this approach. If you’re looking to explain ATT&CK to a non-security stakeholder or understand it better on your own, this talk is for you.
Our goal is for people to read a detection and be able to quickly explain “An adversary is trying to accomplish X.” Mapping to ATT&CK tactics and techniques helps with that, but we realize not everyone knows what “credential access via Kerberoasting” means at first glance. A security expert needs to know the technique, but the information can be too detailed for other stakeholders. The tactic labels are helpful, but don’t exactly roll off the tongue.
To remedy this, we translated them into conversational language, such as explaining credential access as “stealing logins and passwords” and execution as “running malicious code.” We realized we could make it even more approachable by introducing a higher-level context – in other words, the objective behind the tactic. For a non-security stakeholder, it may be enough to know that “an adversary is trying to gain access.”
All those layers together provide a handy “Mad Libs” style word game:
"An adversary is trying to ______ by using _______. "
Explaining a detection with this approach provides useful information for all experience levels in one sentence. For example: An adversary is trying to gain access by stealing logins and passwords using Kerberoasting.
While we use ATT&CK’s tactic labels in the Falcon console, we offer our “conversational translation” in this cheat sheet. If these phrases don’t resonate with you, we encourage you to use the worksheet from the deck to come up with ones that fit better.
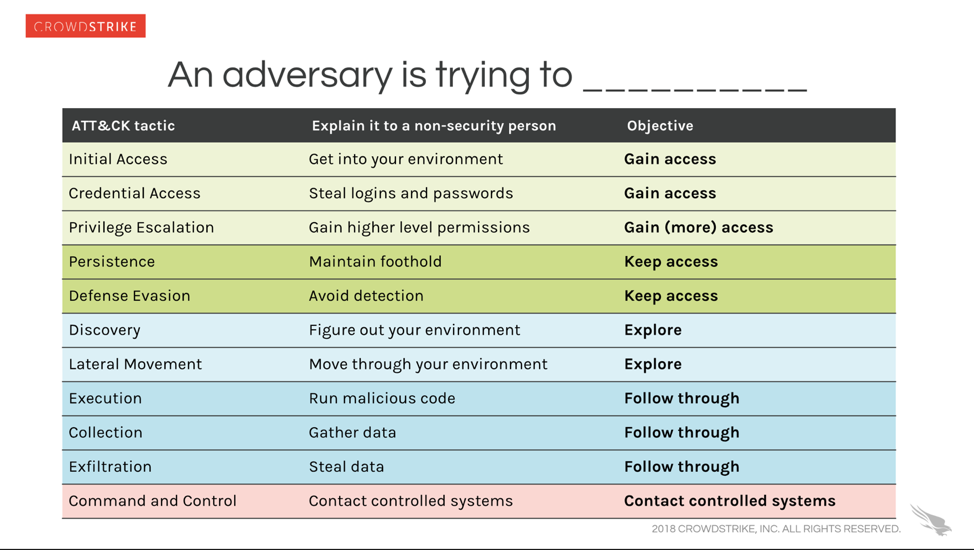 Sample worksheet with conversational translations of ATT&CK terms
Sample worksheet with conversational translations of ATT&CK termsAdditional Resources
- Read test results for the Falcon platform on the MITRE ATT&CK Emulation website.
- Read the press release on the MITRE ATT&CK Evaluation.
- Download the white paper: “Faster Response with CrowdStrike and MITRE ATT&CK.”
- See what third-party security testers and reviewers are saying about Falcon.
- Test CrowdStrike next-gen AV for yourself: Start your free trial of Falcon Prevent™ today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































