- On May 27, 2022, a remote code execution vulnerability was reported affecting the Microsoft Windows Support Diagnostic Tool (MSDT)
- The vulnerability, which is classified as a zero-day, can be invoked via weaponized Office documents, Rich Text Format (RTF) files, XML files and HTML files
- At time of writing, there is no patch available from the vendor
- The CrowdStrike Falcon® platform protects customers from current Follina exploitation attempts using behavior-based indicators of attack (IOAs)
A new zero-day remote code execution vulnerability (CVE-2022-30190) was reported by security researchers on May 27, 2022. The flaw, dubbed Follina, affects the Microsoft Windows Support Diagnostic Tool (MSDT). Successful exploitation of the vulnerability abuses native trust granted to the Microsoft Windows Diagnostics Tool (msdt.exe) allowing it to download and execute remote code. At time of writing, research indicates that exploiting file-based versions of the vulnerability requires user interaction, by opening a tainted Microsoft Office, RTF, XML or HTML file. Proof-of-concept payloads are publicly available and exploitation of this vulnerability is of low complexity.
A Primer on How the Vulnerability Works
The initial proofs of concept (POCs) leverage a Microsoft Office remote template feature to retrieve a weaponized HTML file from a remote server. Once retrieved, the HTML file utilizes the ms-msdt MSProtocol URI to import shellcode and execute PowerShell commands.
This vulnerability bears similarities to CVE-2021-40444 as both manipulate how HTML or Javascript code is loaded through an external link. However, Follina is significantly less complex to leverage and contains fewer dependencies.
How CrowdStrike Falcon Protects Customers from Follina

Demo: How CrowdStrike Detects and Prevents the Follina Vulnerability
The CrowdStrike Falcon® platform takes a defense in-depth approach to protecting customers by employing machine learning (ML) and behavior-based IOAs. The Falcon platform uses incoming telemetry to power its detections and provide real-time threat mitigation for customers.
CrowdStrike’s Rapid Response team was able to enhance existing coverage immediately via proactive threat-hunting combined with malware and exploit research. As soon as critical content is available, the Falcon platform pushes updates in real time to all customers without having to upgrade or update the sensor.
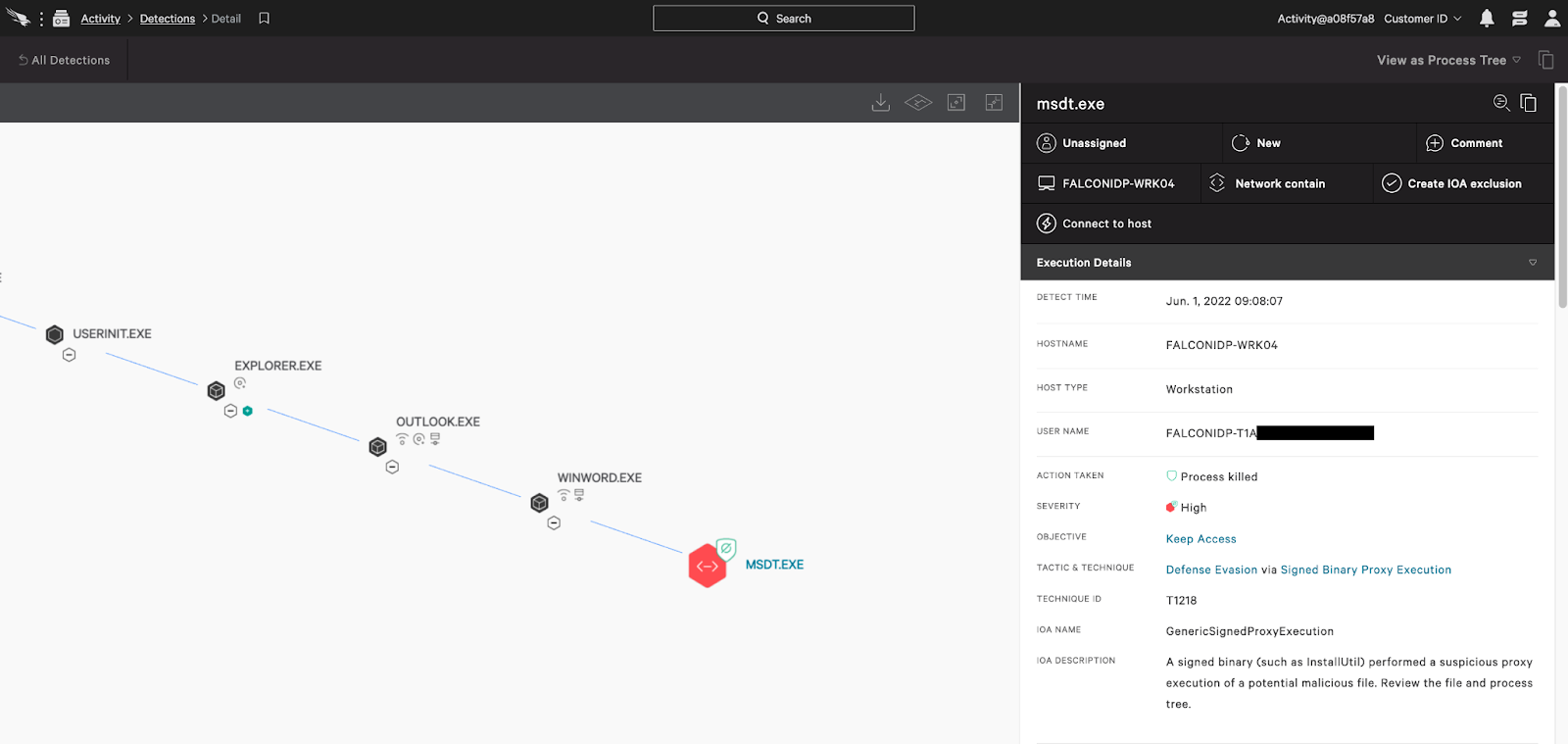
The Falcon sensor has detection and prevention logic that addresses exploitation of this vulnerability. With "Suspicious Process Blocking" enabled, Falcon will block code execution attempts from msdt.exe. Even without "Suspicious Process Blocking" enabled, Falcon will generate a detection in the Falcon console.
Follina Phishing Attack Prevention Scenario
An attacker can send a maliciously crafted Microsoft Office or RTF document via email to invoke remote code execution when run. CrowdStrike Falcon has prevention and detection capabilities that can immediately shut down attack attempts such as these.
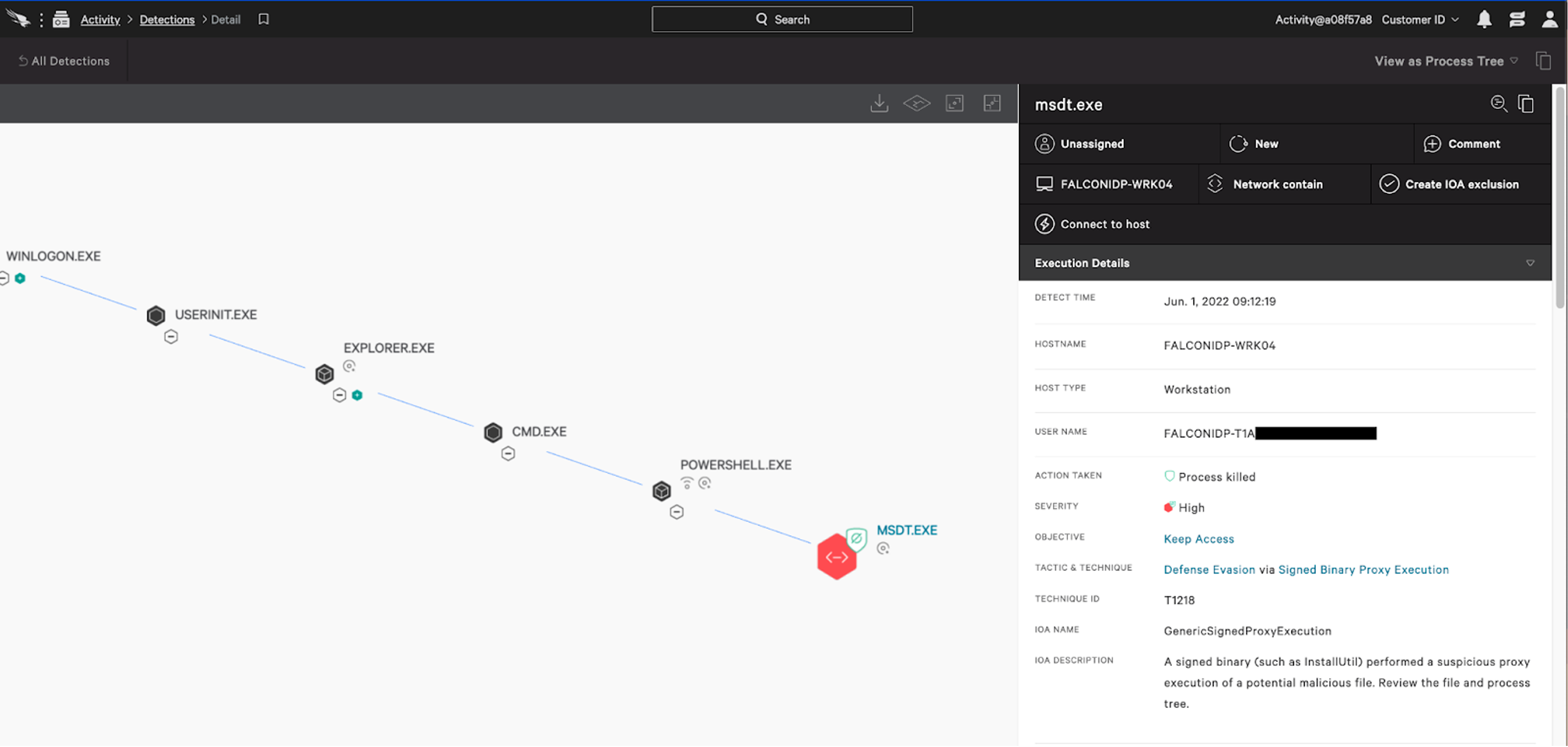
Follina PowerShell (wget) Attack Prevention Scenario
As reported, an attacker can leverage non-document techniques — such as a wget request from PowerShell to an attacker controlled domain — to retrieve an HTML payload to further actions on objectives via remote code execution. Again, the Falcon platform automatically prevents and detects this attack scenario using behavior-based IOAs.
Falcon Spotlight Shines a Light on Vulnerable Endpoints
Organizations looking to gain additional visibility into endpoints vulnerable to Follina (CVE-2022-30190) can turn to the CrowdStrike Falcon® Spotlight module of the Falcon platform for always-on automated vulnerability management. Falcon Spotlight, together with research and analysis from CrowdStrike’s Threat Intelligence Team, offers valuable insights that allow customers to create a defensible security posture.
Falcon Spotlight customers have access to a trending threat dashboard that provides insights into the vulnerability to aid them in tracking their exposure and remediation progress.
Note: More detailed intelligence and technical information about Follina (CVE-2022-30190) is available to CrowdStrike customers through the Falcon console and Support Portal.
Additional Resources
- CrowdStrike customers can access more detailed intelligence and technical information about Follina through the Support Portal.
- Learn about the powerful, cloud-native CrowdStrike Falcon® platform by visiting the product webpage.
- Learn more about how CrowdStrike Falcon® Spotlight can help you prioritize and remediate critical vulnerabilities.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent to see for yourself how true next-gen AV performs against today’s most sophisticated threats.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)