- The Cybersecurity and Infrastructure Security Agency (CISA) warns of potential critical threats similar to recent cyberthreats targeting Ukraine
- U.S. companies are advised to implement cybersecurity measures to maximize resilience
- The CrowdStrike Falcon®® platform provides continuous protection against wiper-style threats and real-time visibility across workloads
Following mid-January 2022 incidents involving a series of Ukrainian website defacements and the deployment of data-wiping WhisperGate malware, CISA issued guidance on how companies can maximize resilience against similar incidents. To better understand how WhisperGate malware operates, CrowdStrike Intelligence recently performed a technical analysis of the malicious bootloader and how the destructive wiping operation occurs.
The Falcon platform uses machine learning and behavior-based detections to provide continuous protection from threats — including data-wiping malware — and deliver real-time visibility across workloads.
A Primer on Destructive Malware
Destructive malware includes threats that render compromised systems inoperable by deleting or wiping critical data instead of making it inaccessible through encryption.In 2017, two destructive ransomware outbreaks — NotPetya and WannaCry — leveraged the EternalBlue vulnerability in the Server Message Block (SMB) protocol to quickly spread and infect vulnerable systems worldwide.
The NotPetya ransomware outbreak started in Ukraine, and shortly after security researchers found that a faulty encryption routine made file recovery impossible regardless of whether victims paid. The WannaCry ransomware outbreak that followed also made data recovery impossible, as the ransomware could not tie payment to a particular victim machine.
The recent WhisperGate threat targeting Ukraine features no decryption or data-recovery mechanism, and only performs destructive wiping operations on the infected host’s hard drives. While the threat attempts to masquerade as genuine modern ransomware operations, it irrevocably corrupts the affected host’s data. The CISA alert urges companies to immediately implement cybersecurity measures to protect their infrastructures.
Gain Visibility and Stop Threats with the Falcon Platform
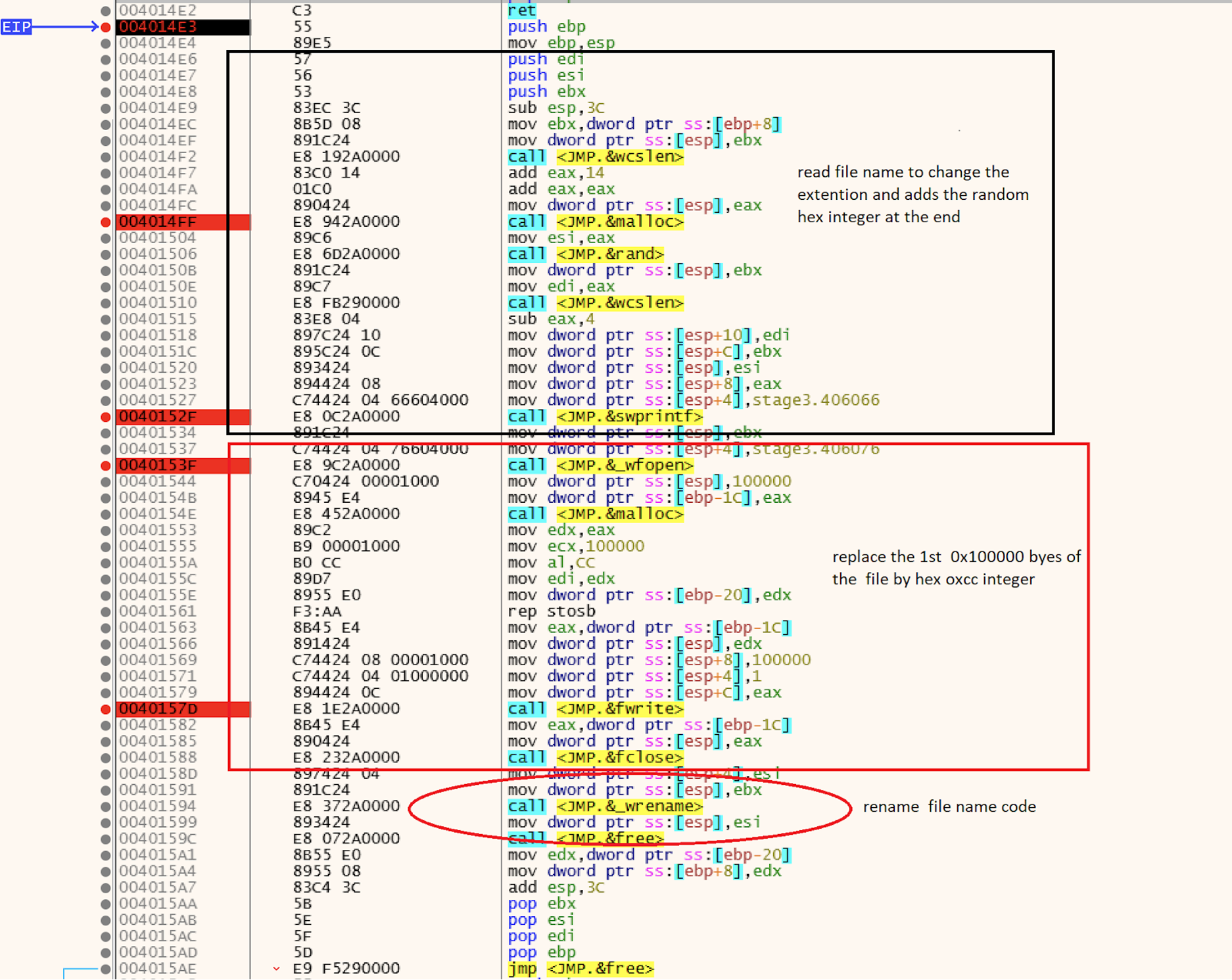
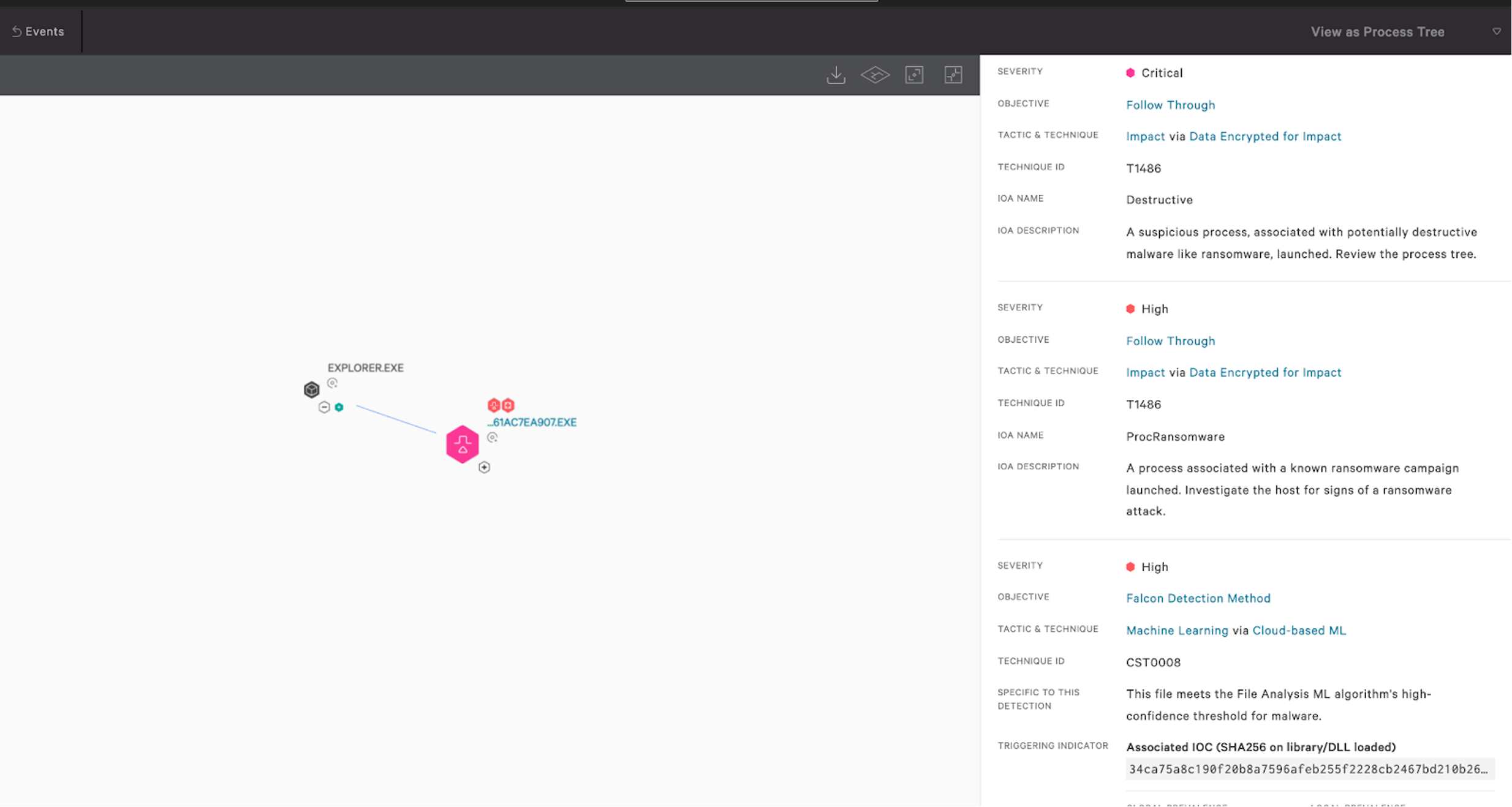
The Falcon platform offers unified visibility, threat detection and continuous monitoring and compliance for any environment, enabling security teams to reduce the time it takes to detect and mitigate security risks.The Falcon sensor employs behavior-based detections using indicators of attack (IOAs) and on-sensor and in-the-cloud machine learning to identify and block threats while incorporating intelligence derived by continuously monitoring tactics, techniques and procedures (TTPs) related to threats and threat actors. Data-wiping threats, including the recent WhisperGate, perform destructive operations on the infected host’s hard drive, making data unrecoverable. CrowdStrike Intelligence performed an analysis on the malicious bootloader, but WhisperGate also uses a downloader to retrieve the final data-wiping payload. The Falcon platform uses on-sensor machine learning to detect and prevent the downloader before fetching the data-wiping component, as seen in the screenshot below.
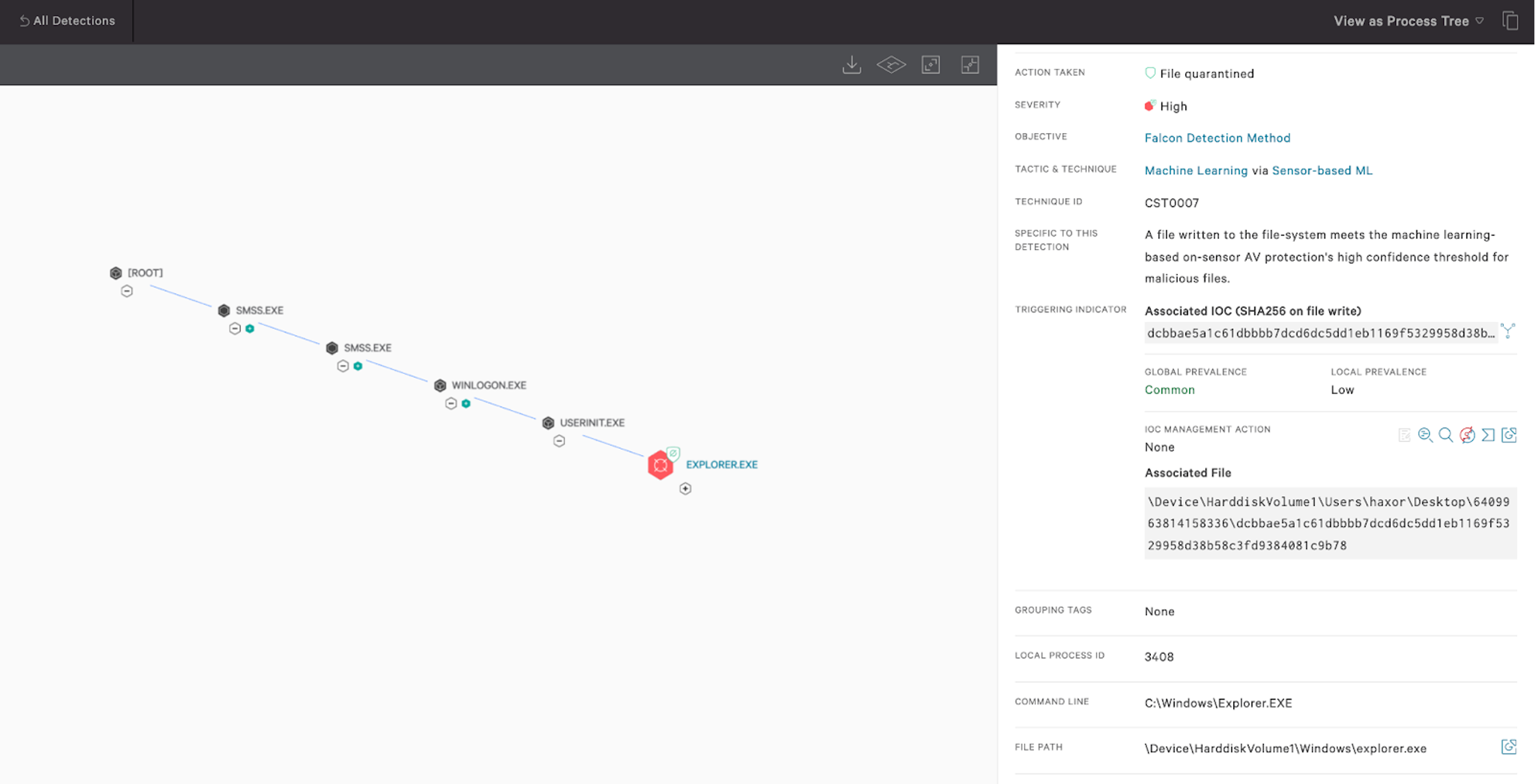 Figure 1. Falcon on-sensor machine learning coverage for the WhisperGate downloader component (Click to enlarge)
Figure 1. Falcon on-sensor machine learning coverage for the WhisperGate downloader component (Click to enlarge)security blind spots.
Maximize Resilience
Organizations that face risk from cyber incidents, including data-wiping threats, are strongly encouraged to take appropriate measures to protect their business from any significant impact on their operations.CISA recommends that organizations take cyber risk and operational resilience seriously and take steps to reduce potential damages, detect intrusions and respond to potential threats.
The Falcon platform protects customers against sophisticated adversaries and sophisticated threats, accelerating response and offering visibility into the overall security posture of the organization. Organizations leveraging the power of the Falcon platform can detect and protect themselves from ransomware, data-wiping malware and other sophisticated threats and adversaries.
Additional Resources
- Read more about WhisperGate in this CrowdStrike Intelligence blog: Technical Analysis of the WhisperGate Malicious Bootloader.
- Learn about the powerful, cloud-native CrowdStrike Falcon® platform by visiting the product webpage.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ to see for yourself how true next-gen AV performs against today’s most sophisticated threats.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)