In Part 1 of this two-part “Tales from the Trenches” blog, we examined a stealthy Remote Desktop Protocol (RDP) intrusion uncovered by CrowdStrike® Falcon CompleteTM experts. In this installment, we’ll walk you through remediation efforts, highlighting Falcon Complete’s ability to directly eject a threat actor and bring the customer’s environment back to a clean, operational state.
The Remediation
In most traditional managed detection and response (MDR) services, once an investigation is completed, the customer is provided a list of compromised hosts and remediation recommendations that they are expected to perform themselves. This is more typical of a homework assignment than a full response. The CrowdStrike Falcon® Complete team directly performs many of the critical remediation actions for customers, including the surgical removal of all identified malicious binaries and persistence mechanisms. This may include stopping active processes or removing malicious artifacts and complex persistence mechanisms.
The Falcon Complete team accomplishes this all within minutes, without disruption to our customers or the need to “wipe and reload.” In this sense, we are truly an extension of our customers' existing cybersecurity operations teams. We work hand-in-hand with them to ensure that all appropriate actions are taken and that affected hosts are properly remediated.
One of the first things we did in response to this Remote Desktop Protocol (RDP) intrusion was inform our customer of the external RDP connections, and recommend that they place this host behind a firewall and block all external RDP connections to the host unless they were coming from specific, authorized IP addresses. After that, we began our remediation efforts.
When dealing with targeted intrusion activity, in order to fully remediate and kick the threat actor out, we need to ensure that all backdoors and persistence mechanisms have been removed.
We methodically started with the “patient zero” host, and once this host was remediated, we continued to move to the other compromised hosts to remove any malicious binaries and persistence. Based on our previous CrowdStrike Endpoint Activity Monitoring (EAM) queries, we had discovered over 40 hosts that had indicators of attack (IOAs) related to this threat actor. These 40+ hosts had a mix of malware that was written to disk, as well as lateral movement via RDP using the compromised account.
This means all of these hosts needed to be treated as potentially compromised, and proper analysis and validation needed to occur. Manual remediation of one host typically isn't too lengthy, but manually remediating 40 or more hosts can result in hours of work. This is where the Falcon Complete team’s innovation and automation come into play. By leveraging a customizable CrowdStrike Falcon®® Real Time Response (RTR) API script developed by Falcon Complete analysts, we are able to perform bulk automated remediation across a large number of hosts.
One of our main goals is to ensure we can remediate compromised hosts quickly and efficiently, without interrupting our customer’s business operations. While going through the initial triage of these hosts, we built a list of IOAs that contained the files and folders that were dropped by the actor, as well as the persistence mechanisms that were put in place. Using this list, we created a custom PowerShell script that interrogated all of the compromised hosts and provided an output of artifacts for each endpoint. We then used this to complete the remediation/removal actions in an automated fashion. Once the remediation actions were completed, we provided a report of all actions to the customer and included additional recommendations to reset compromised credentials and limit any external exposure of protocols such as RDP. Once the customer confirmed these actions, Falcon Complete removed the network containment.
The Conclusion of a Successful Mission
Let’s recap what took place during this incident:
Detect
- 0:00 It all started with a single alert for the attempted execution of a malicious XMRig coinminer binary that Falcon detected and prevented. While investigating the surrounding activity, we quickly realized that we were dealing with an interactive attacker.
Investigate
- 0:10 We were able to leverage EAM to discover and identify additional compromised hosts via file write events for known IOAs, and within 10 minutes of the initial detection/prevention we informed the customer.
- 0:20 Approximately 10 minutes later, further EAM queries were performed for all hosts to identify successful lateral movement via RDP from the compromised account. We discovered an unknown/unmanaged asset based on this query and worked with the customer to install the Falcon sensor on the endpoint to improve our visibility and ability to respond.
- 1:10 Once the sensor was installed at approximately an hour and ten minutes after the initial detection, we connected, analyzed and discovered RDP authentication logs for the compromised account coming from yet another unmanaged/unknown host.
- 2:00 We once again worked with the customer to have the agent installed on this unmanaged host, which led to our identification of the patient zero system at approximately two hours after the initial detection.
Respond
- 3:00 We quickly contained patient zero and began analysis and remediation efforts. The patient zero host was remediated within three hours of the initial detection. We then began automating our IOA identification efforts for all of the other 40 affected hosts, leveraging our customizable RTR API script.
- 6:00 Approximately three hours later, all affected hosts had been queried for IOAs and remediation efforts began.
It’s worth noting that the response time in this case was extended due to the involvement of several exploited, unmanaged hosts. In order to ensure the fastest possible incident response and best levels of protection, the Falcon Complete team recommends a full deployment of Falcon agents throughout the environment.
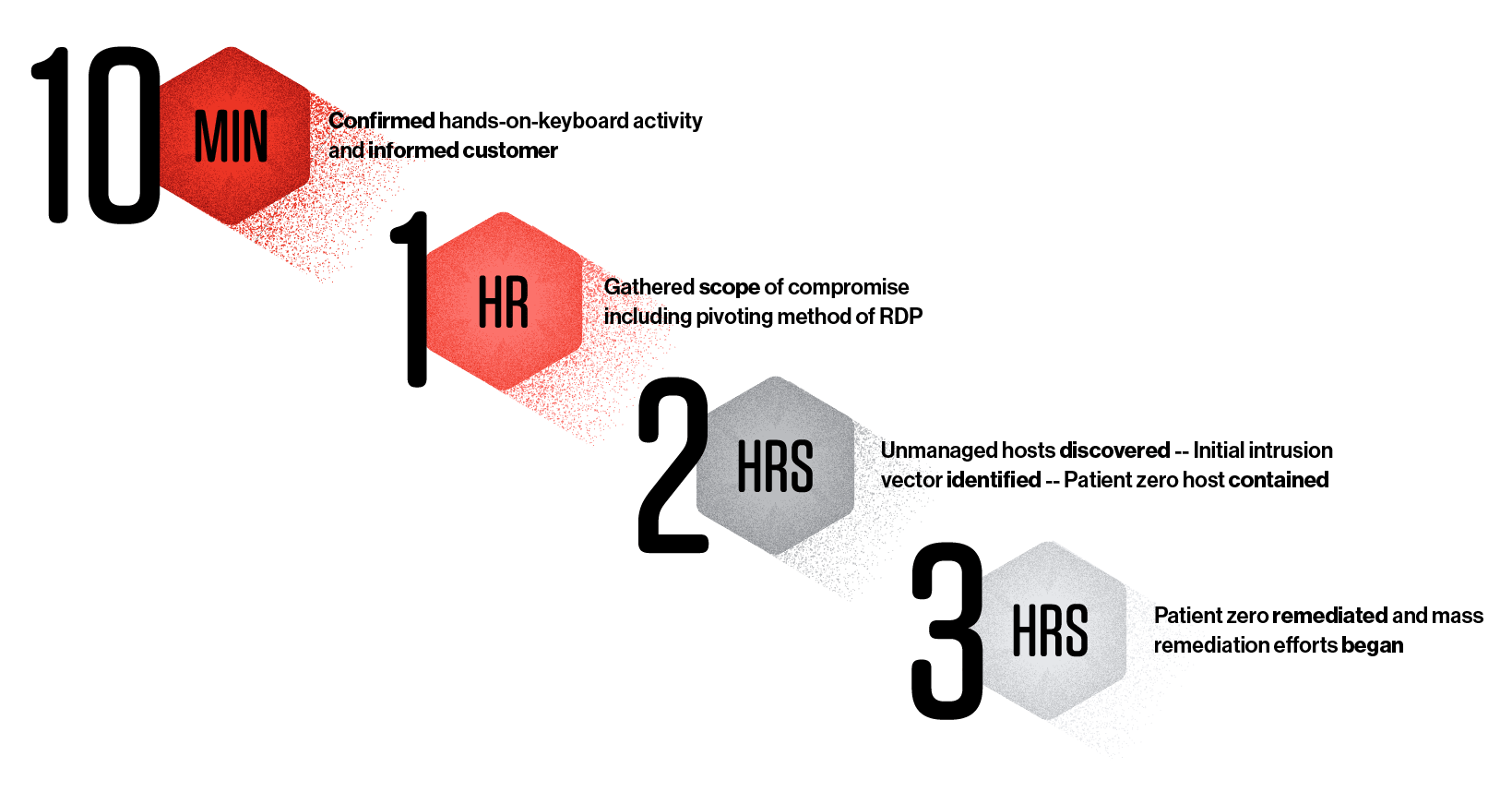 Figure 2. A timeline showing the speed at which the Falcon Complete team went from detection of this stealthy attack to remediation efforts that returned the customer to a clean, operational state
Figure 2. A timeline showing the speed at which the Falcon Complete team went from detection of this stealthy attack to remediation efforts that returned the customer to a clean, operational stateResponse Methodology That Works
In this interesting case study, a detection for a single quarantined binary, which normally may not have necessitated further investigation, turned out to be interactive threat actor activity that impacted multiple hosts.
In a matter of hours, the Falcon Complete team was quickly able to investigate the activity, scope out the extent of intrusion, and contain and remediate the compromised endpoints. All of this occurred without reboots or reimaging, and with zero impact on end users. Finally, the Falcon Complete team worked in collaboration with the affected organization to better understand the methods of intrusion and strengthen their defenses moving forward. The Falcon Complete team’s response methodology provides these kinds of results for our customers every day, delivering on the CrowdStrike promise: We stop breaches.
Additional Resources
- Read Part 1 of this blog.
- Learn more by visiting the Falcon Complete product webpage.
- Read a white paper: CrowdStrike Falcon® Complete: Instant Cybersecurity Maturity for Organizations of All Sizes.
- Test CrowdStrike next-gen AV for yourself: Start your free trial of Falcon Prevent™.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)