In the recent MITRE Engenuity ATT&CK Enterprise Evaluation, CrowdStrike demonstrated the power of its unified platform approach to stopping breaches. Facing attack emulations from the highly sophisticated WIZARD SPIDER and VOODOO BEAR (Sandworm Team) adversaries, the CrowdStrike Falcon®® platform:
- Achieved 100% automated prevention across all of the MITRE Engenuity ATT&CK Enterprise Evaluation steps.
- Demonstrated powerful native identity protection capabilities that prevented the test evaluator from gaining initial access to the environment — stopping the test before it could even start.
- Showcased the native intelligence automation capabilities of CrowdStrike CROWDSTRIKE FALCON® INTELLIGENCE™ threat intelligence to deliver enriched detections and indicators of compromise on the tactics and techniques used by the adversaries.
- Provided a clear demonstration of the dynamic nature of CrowdStrike Falcon® Fusion in delivering the automated workflows customers require to stop today’s most sophisticated threats.

The CrowdStrike Falcon® OverWatch™ managed threat hunting service operates 24/7 with the primary mission of pinpointing malicious activities at the earliest possible stage to provide customers with timely, accurate and relevant notifications and context to inform a swift and decisive response. The speed with which OverWatch can deliver rich insights into a threat actor’s movements and tactics, techniques and procedures (TTPs) buys victim organizations valuable time in responding to an intrusion. While OverWatch was not a formal part of this year’s MITRE Engenuity ATT&CK validation testing, the OverWatch team actively tracked this emulation from the sidelines to demonstrate how it would defend against similar intrusions in the real world. In this writeup, we review some of the context and insights that our expert team of human threat hunters would have delivered had the MITRE evaluation’s simulated adversary attacks occurred in a real-world environment.
OverWatch vs. WIZARD SPIDER: Patented Tooling Enables Rapid Detection and Correlation of Malicious Behaviors
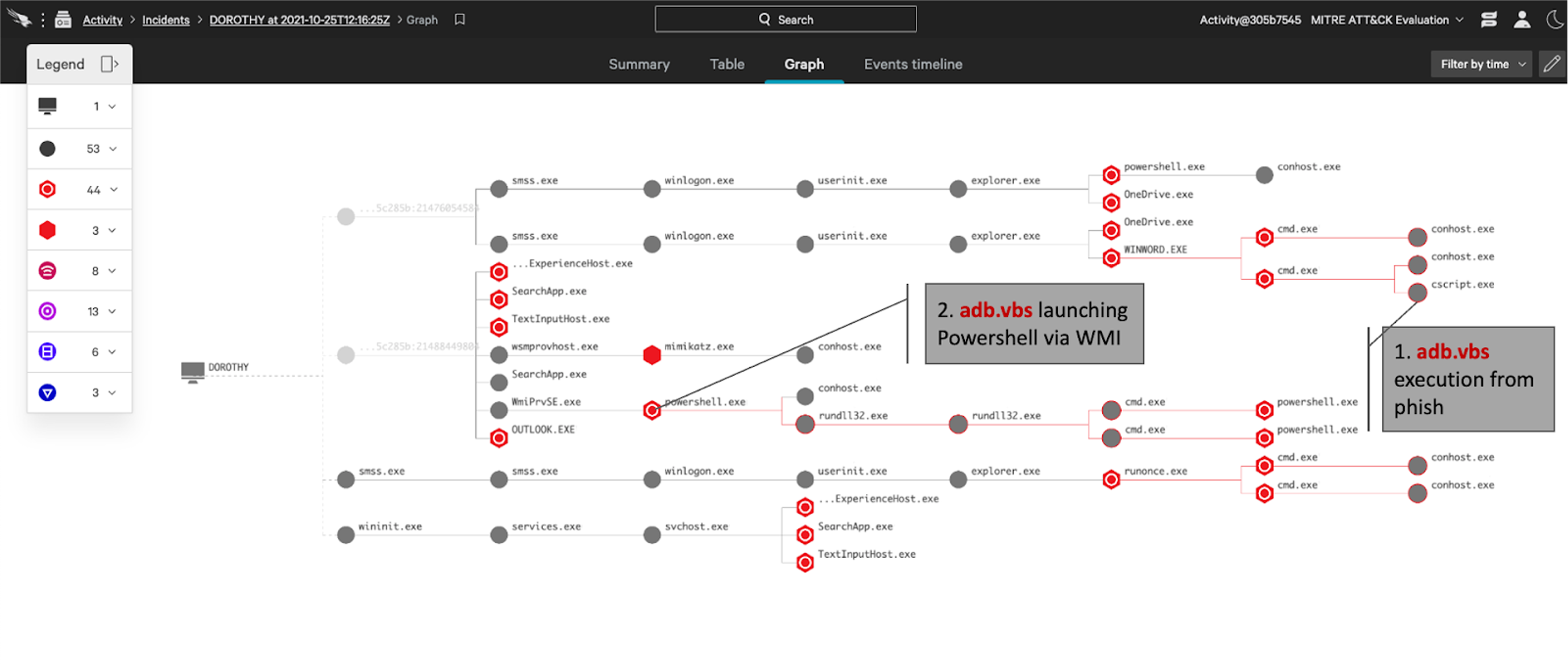
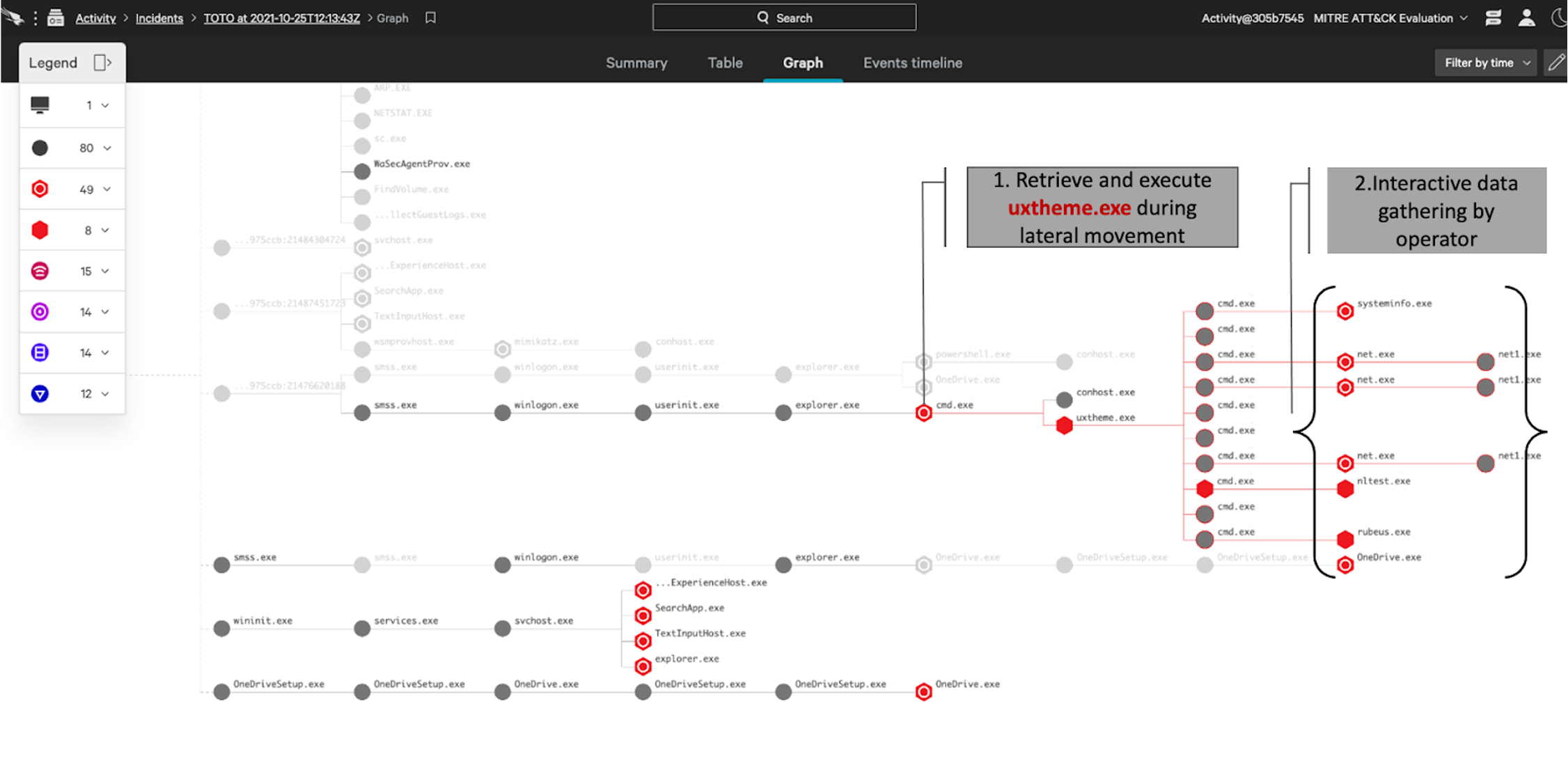
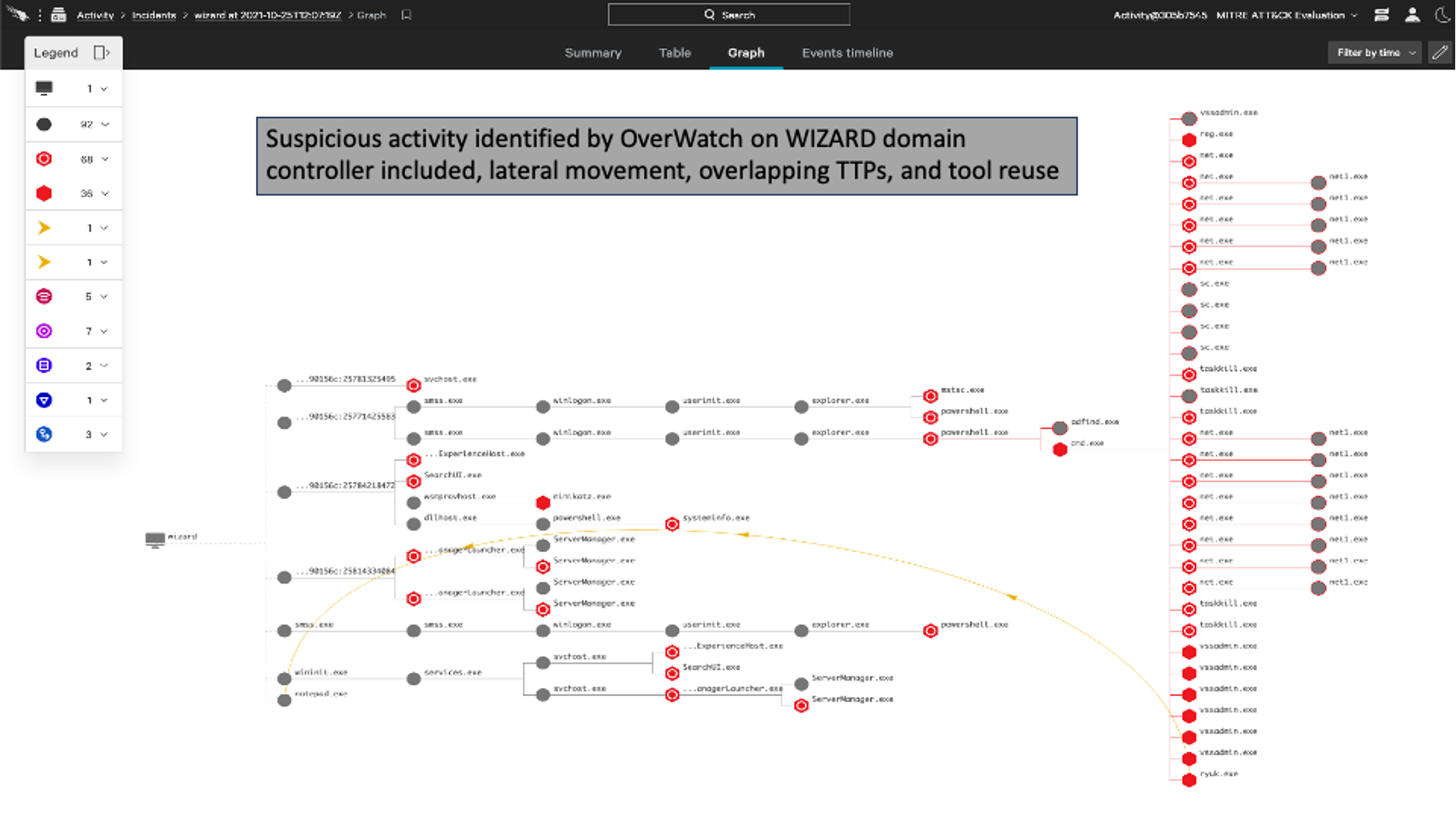
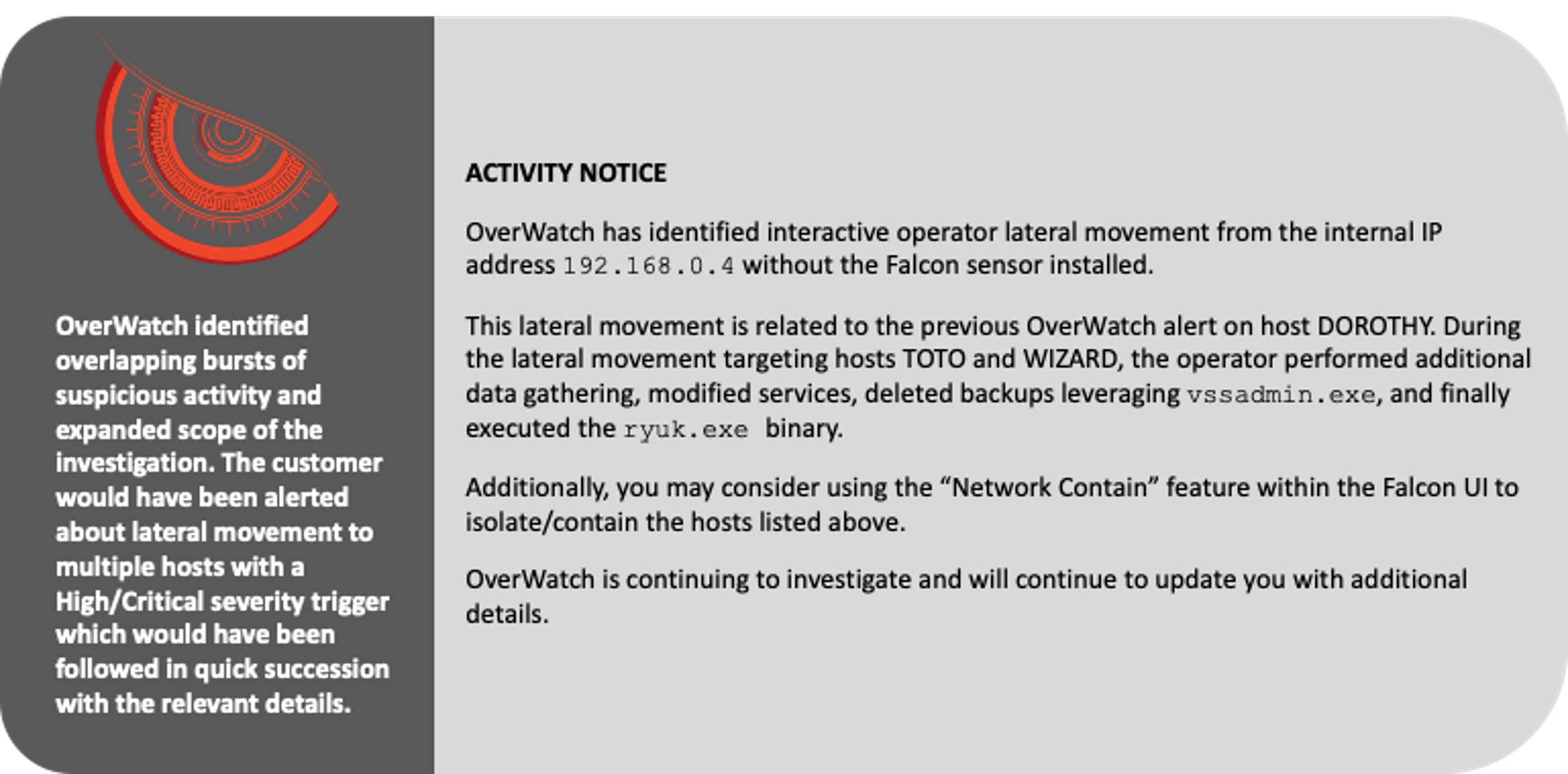
Within minutes of the malicious activity beginning, OverWatch rapidly built out the scope of the intrusion and was ready to alert on the actor’s activities. The actor began by delivering an implant via phishing, and then moved laterally to two hosts. OverWatch was able to identify the overlapping bursts of suspicious activity to successfully confirm lateral movement and the expanded scope of the intrusion. OverWatch can identify overlapping malicious behaviors in near real time thanks to its high-fidelity patented tooling, which supports cardinality-based visualization of likely linked events and employs artificial intelligence to more accurately predict whether a single event is malicious or not.OverWatch’s Patented Tooling
OverWatch’s patented hunting tool for cardinality-based activity pattern detection looks for related bursts of potentially malicious activity patterns and then surfaces these for further human analysis. To support rapid analysis by threat hunters, the tool presents data visually, grouping together activity patterns with a graphical representation of the fidelity value to illustrate the degree to which each of the activity patterns indicates possible malicious activity. Some events are so common within enterprise environments that including them in the bursts would create more noise than insight. But these same events can also be key to identifying a potential intrusion. OverWatch’s patented hunting tool for security-violation detection was built to use artificial intelligence to predict whether an event is malicious on the basis of the ancestry of the command line. This tool classifies hunting leads before they go to hunters, helping to funnel only the relevant data for human analysis.OverWatch vs. WIZARD SPIDER: The Human Element Delivers Critical Context
Crucially, the outputs of OverWatch’s tooling are augmented by human analysis. This provides two clear benefits for victim organizations: identifying stealthy and novel behaviors, and deep and timely context-rich notifications.Threat hunters often go head-to-head with adversaries
that are agile and creative in navigating automated defenses. The expert OverWatch team hunts relentlessly to identify, detect and disrupt sophisticated adversary tradecraft. The second benefit comes from the timely and context-rich notifications delivered by OverWatch’s highly skilled hunters, who quickly and accurately reconstruct intrusion activity to provide victim organizations with a comprehensive picture of an adversary’s movements that can inform a decisive response.
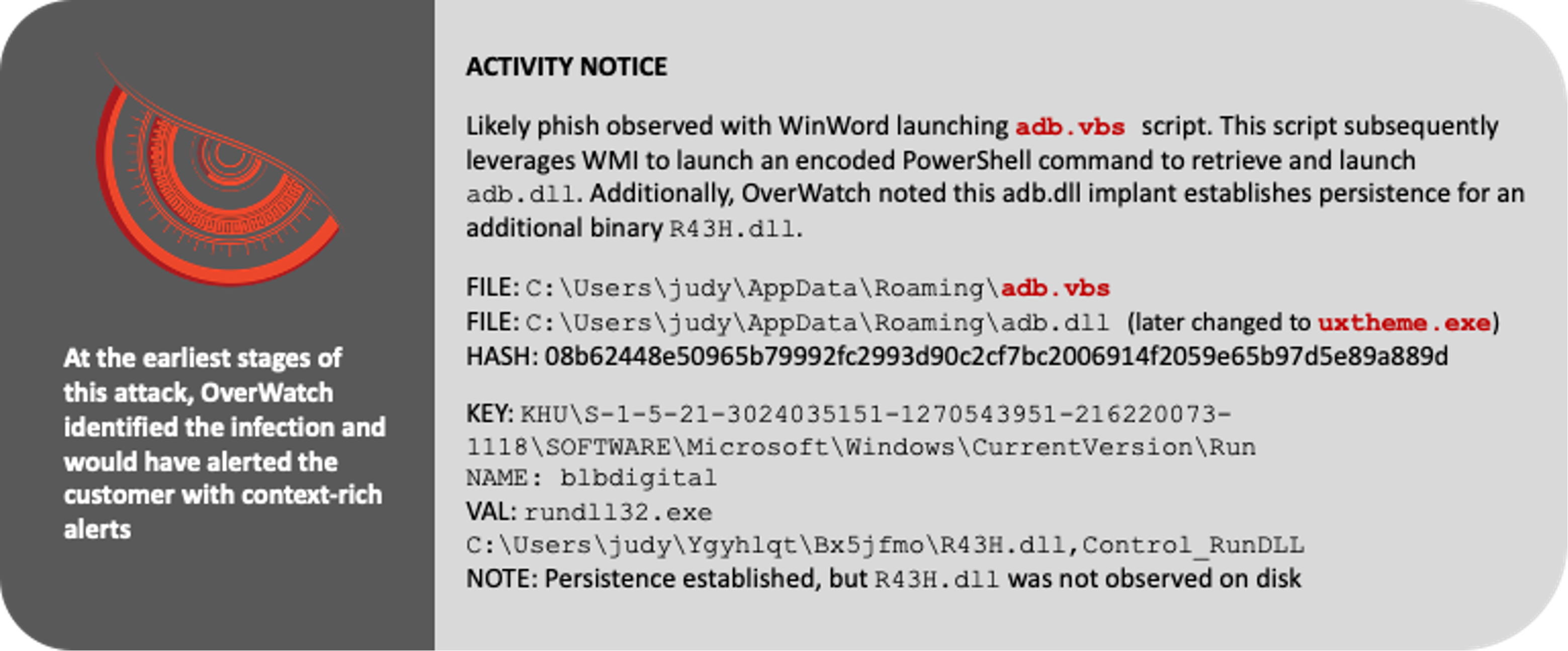
In intrusions that follow known patterns of adversary behavior, such as the MITRE WIZARD SPIDER emulation, OverWatch’s ability to quickly contextualize this information delivers real value. The following details illustrate how OverWatch hunters can tie together disparate events into a clear narrative to inform action. The activity notices included below represent the types of notifications a victim organization could expect to receive during an interactive intrusion.
OverWatch Returns Time to Your Side
When OverWatch investigates an intrusion in your environment, your security team gets more than an alert. OverWatch combines the power of patented tooling with deep expertise to compile comprehensive context about a threat actor’s movements and motivations. As a result, an OverWatch notification is not just an alert — it is a detailed blueprint of the intrusion lifecycle that provides a solid foundation for building a response.
In the MITRE WIZARD SPIDER test scenario, a context-rich OverWatch analysis and notification would have been received within minutes of the initial activity. With the Falcon platform actively preventing the actor’s attempts to advance, the OverWatch notification would have provided the critical information needed to evict the actor from the environment before they could do damage.
Every minute an actor is in your environment is a minute too long. In order to prevent an actor from burrowing deep into your environment, it is paramount that a response is swift and decisive. OverWatch notifications provide the detail and context that makes this possible. As an added layer of defense, customers can use the natively integrated Falcon Fusion capability to orchestrate and automate complex workflows. This provides the ability to trigger host containment in near real time in response to OverWatch’s high-fidelity notifications. Customers can also use Falcon Fusion to set up and configure notifications via plugin applications to customize how they receive OverWatch notifications to enable timely response.
The deep expertise of threat hunters, alongside our patented workflows and tooling, enable OverWatch to deliver rich context to your security team quickly — when minutes matter.
Additional Resources
- Read the press release and blog.
- Read more about how OverWatch uses the human element to augment technology to protect customers against both known and unknown threats in this CrowdStrike blog.
- Watch this video to see how Falcon OverWatch proactively hunts for threats in your environment.
- Learn what others are saying about CrowdStrike — visit the CrowdStrike Industry Recognition and Technology Validation webpage.
- Learn about the powerful, cloud-native CrowdStrike Falcon® platform.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)