The job for CIOs, CISOs and their security and IT teams may be more complex than ever in 2022. Ongoing support for hybrid workforces, coupled with the continued shift to the cloud, has expanded the threat surface. At the same time, the infrastructure and environments supporting organizations are growing ever more vulnerable. According to the National Institute of Standards and Technology (NIST), more than 18,000 vulnerabilities were reported in 2021.
In addition, cyberattacks continue to grow more sophisticated, more common and more devastating, and security and IT teams often face these challenges shorthanded because of an acute shortage of cybersecurity talent (there are a reported 465,000 unfilled cyber jobs across the U.S. alone).
Security for the modern enterprise requires a new approach that not only stops the breach, but addresses the critical issues that security and IT teams are facing. CrowdStrike is leading the industry forward with the world’s most advanced cloud-native platform that provides teams with superior protection and performance, while reducing the complexity and friction that legacy approaches can introduce.
Here are three ways that CrowdStrike is addressing the critical challenges facing today’s security teams.
Challenge #1: Digital Transformation and Attack Surface Sprawl
Most information workers have been fully remote for almost two years now and the pre-pandemic requirement of working five full days in the office isn't expected to return any time soon. Security teams therefore have had to adapt to their new hybrid operating environments practically overnight. According to the ESG 2022 Technology Spending Intentions Survey, the top driver increasing IT complexity has been the rise in remote workers due to COVID-19 (cited by 49% of respondents), followed by the growing number and types of endpoint devices they have to secure (39%). “Digital transformation and the move to the cloud are further impacting endpoint security strategies, as organizations work to implement more holistic, integrated endpoint and cloud security solutions,” said Dave Gruber, Principal ESG Analyst. “As more advanced threats traverse systems and cloud workloads, security solutions must be able to correlate signals to detect and stop attacks in progress.” Traditional perimeter security technologies, including firewalls, VPNs and legacy on-premises security solutions, can’t scale to properly secure today’s hybrid, multi-cloud environments, remote workforces and business-critical cloud applications. Security teams now need cloud-native solutions to protect the cloud and hybrid environments outside the perimeter.
Challenge #2: Evolving Threats and Smarter Adversaries
At the heart of every attack is a human adversary, and they’ve come a long way from the early days when they primarily acted alone. Today’s security teams face eCrime syndicates and nation-state actors that are well-organized, well-funded, tactically precise, and that invest heavily in the design and refinement of their own proprietary tradecraft.
A decade ago (in pre-CrowdStrike days), signature-based antivirus (AV) software — relying heavily on reactive, CPU-intensive signature match scanning — was considered an adequate defense against cyber threats. But even then, legacy AV was routinely failing organizations. Threat actors had already begun to evolve their tradecraft to easily circumvent known controls and checks that AV systems were likely to flag, and they no longer depended on malware that needed to be downloaded to the device to carry out the attack.
According to the CrowdStrike 2022 Global Threat Report, 62% of intrusions detected were malware-free. Attackers are more likely to manipulate legitimate software programs, tools and files (e.g., using “living off the land” tactics and hands-on-keyboard attacks) to easily evade autonomous detections. As adversaries continuously advance their tradecraft to bypass legacy security solutions, the combination of world-class technology combined with expert threat hunting and human expertise has become absolutely mandatory to see and stop the most sophisticated threats. Autonomous machine learning alone is simply not good enough to stop dedicated attackers.
Challenge #3: The Rise of Ransomware
Ransomware and ransomware-as-a-service (RaaS) have upended the game. Threat actors are bolder, stakes are higher and ransomware costs and extortions are surging. Ransomware is no longer a hacker’s side hustle. Today, ransomware campaigns are executed by well-funded criminal enterprises targeting organizations of every size, region and industry.
According to the CrowdStrike 2022 Global Threat Report, ransomware-related data leaks increased 82% from 2020 to 2021. Ransomware attacks using “big game hunting” tactics will continue to dominate the eCrime landscape in 2022, likely significantly increasing their use of RaaS to take advantage of a wider array of adversarial skill sets. Security professionals must take proactive measures to prevent these threats and prepare contingencies should security defenses ultimately fall short.
CrowdStrike Solves Modern Security Challenges with a Modern Platform
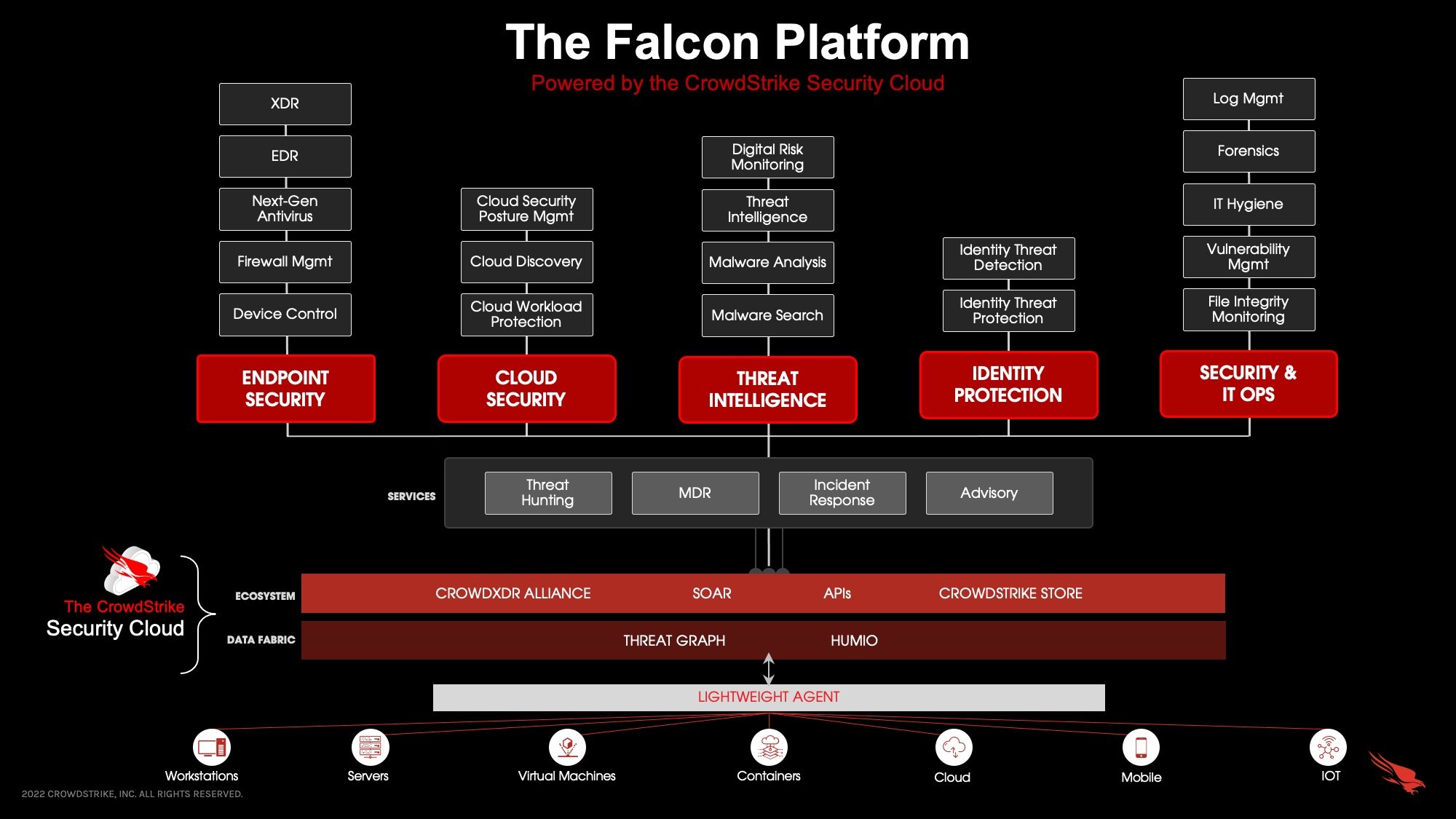
Evolution of the CrowdStrike Falcon® Platform
Since our inception, CrowdStrike’s mission has never wavered: to stop breaches. To achieve this, CrowdStrike has fostered a prosperous security community that’s strong, smart and proactive in detecting and responding to threats anywhere they reside. CrowdStrike delivers one of the world’s largest cybersecurity sensor environments that extends visibility and control universally to endpoints, cloud workloads, identities and data.
This mission evolved from an ambitious vision to build a high-scale unified security platform powered by a single lightweight agent and universal, cloud-native architecture. CrowdStrike thus began building today’s modern, signature-less approach to security that’s dynamic, adaptive and efficient to deploy and run across every endpoint, workload and operating environment — and able to predict threats as well as it prevents them.
The CrowdStrike Falcon®® platform is extensible and modular, allowing customers to add functionality to their security stack as their real-world use cases evolve. The Falcon modules, and a variety of integrated third-party apps and plugins, can be discovered, tried and purchased through the CrowdStrike Store.
Leveraging the Power of the CrowdStrike Security Cloud
Today, solutions provided throughout the Falcon platform take full advantage of the CrowdStrike Security Cloud and the advanced artificial intelligence, machine learning and behavioral analytics that power it.
The CrowdStrike Security Cloud correlates trillions of security events per day sourced from a diverse range of endpoint, cloud and identity telemetry; indicators of attack (IOA); and a library of proprietary threat intelligence widely considered to be the industry standard.
Using world-class AI, the CrowdStrike Security Cloud creates actionable data, identifies shifts in adversarial tactics, and maps tradecraft in the patented CrowdStrike Threat Graph® to automatically prevent threats in real time, help correlate siloed threat signals into prioritized alerts and provide extended detection and response (XDR) capabilities. Ultimately, security and IT teams see tangible benefits in meaningful technical and operational security outcomes, hyper-accurate detections, automated and proactive protection, and high-speed remediation. With world-class technology, advanced analytics and frictionless automation, and in tandem with leading intelligence and expert threat hunters, the CrowdStrike Security Cloud powers a true adversary-driven approach for stopping breaches.
One End-to-end Platform to Address Every Threat
As human adversaries continuously advance their tradecraft to bypass legacy security solutions, only a combination of world-class technology combined with expert threat hunters will ensure security teams have the tools and expertise they need to see and stop advanced attacks.
Security teams equipped with the Falcon platform — with its complete portfolio of modern security solutions that unify intelligence, technology and expertise — have the solutions they need to successfully and holistically stop today’s breaches. Purpose-built in the cloud with a single lightweight-agent architecture, the Falcon platform delivers rapid and scalable deployment with reduced complexity and immediate time-to-value, while ensuring superior protection. Customers can deploy the lightweight intelligent Falcon agent on tens of thousands of machines in minutes — no reboots or additional configuration changes needed — and defend threats using machine learning with unmatched speed and simplicity from Day One.
Get a Free Trial of Our Industry-leading Technology
CrowdStrike Falcon® has been named a leader in the Gartner 2021 Magic Quadrant for Endpoint Protection Platforms (EPP) and The Forrester Wave™ Endpoint Security Software As A Service, as well as demonstrated its detection and protection capabilities in tests performed by MITRE, SE Labs and AV-Comparatives, all leading independent testing organizations. Start your free trial now and see for yourself.
Additional Resources
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Visit our Industry Recognition and Technology Validation webpage to see what industry analysts are saying about CrowdStrike and the Falcon platform.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)