This blog was originally published Sept. 18, 2020 on humio.com. Humio is a CrowdStrike Company.
Zerologon is arguably the most dangerous Windows vulnerability the security industry has seen. Organizations want to know with no uncertainty whether they’ve been attacked. That assurance doesn’t come from searching 30 days or even 90 days’ worth of Windows logs. It comes from a comprehensive search of all your Windows logs.Humio
customers can get the certainty they need in a matter of seconds. Last month, Microsoft issued a patch for
Zerologon. Since then, the severity of the vulnerability has come to light. The bug, identified as CVE-2020-1472, has a
Common Vulnerability Scoring System (CVSS)
score of 10.0. When left unpatched, Zerologon allows an attacker to manipulate Netlogon authentication procedures by adding zeros to Netlogon authentication parameters. To exploit the bug, an attacker must already have access to the enterprise network. From there, however, attackers can take control of any part of an enterprise Windows infrastructure or the entire network--in a matter of seconds. The example exploit code is a trivial Python script of less than 100 lines. It can be executed in seconds, giving an attacker full administrative control of the domain controller. If your organization uses Humio for log management, you have the benefit of
querying all of your Windows logs to determine whether your environment has been compromised.
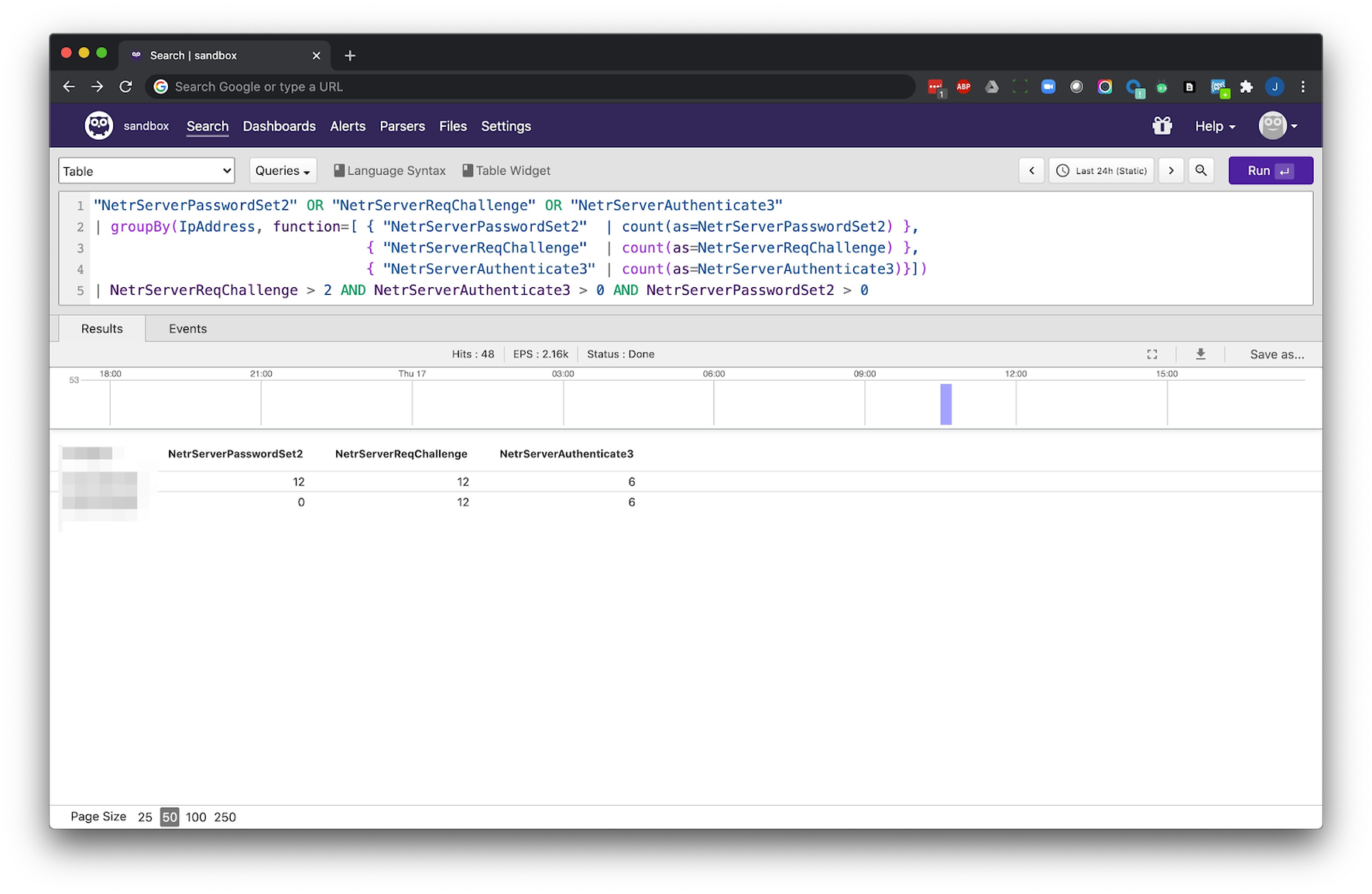 At the request of a customer who was looking to detect the Zerologon attack in their own logs, we wrote a query for this purpose. Running this one query across relevant Windows logs will let you know, in a matter of seconds, if you’ve been impacted by Zerologon.
At the request of a customer who was looking to detect the Zerologon attack in their own logs, we wrote a query for this purpose. Running this one query across relevant Windows logs will let you know, in a matter of seconds, if you’ve been impacted by Zerologon.
"NetrServerPasswordSet2" OR "NetrServerReqChallenge" OR "NetrServerAuthenticate3"
| groupBy(ipAddress, function=< { "NetrServerPasswordSet2" | count(as=NetrServerPasswordSet2) },
{ "NetrServerReqChallenge" | count(as=NetrServerReqChallenge) },
{ "NetrServerAuthenticate3" | count(as=NetrServerAuthenticate3)}>)
| NetrServerReqChallenge > 2 AND NetrServerAuthenticate3 > 0 AND NetrServerPasswordSet2 > 0on-demand webinar with our partner, Vijilan. Also learn how to simplify the
ingestion of Office 365 logs into Humio with O365beat.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)











































