During a cybersecurity investigation, digital forensics and incident response (DFIR) professionals need to obtain information from different artifacts to determine exactly what has occurred on a machine. When performing these investigations, it may help to know if an account was logged on interactively when a program was run — for example, if someone has used the Remote Desktop Protocol (RDP) to connect to the system. In addition to event logs, there’s a number of other artifacts that can provide valuable information, such as registry keys.
Many registry keys exist to help infer what programs have run on a system, such as:
 Figure 1. Windows 10 version containing FeatureUsage key
The FeatureUsage registry key exists within user registry hives (their
Figure 1. Windows 10 version containing FeatureUsage key
The FeatureUsage registry key exists within user registry hives (their 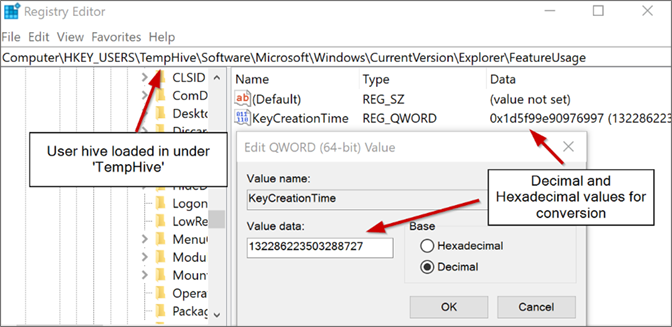 Figure 2.
In Figure 2, we see that the key has the decimal value: 132286223503288727
From here, we can use CyberChef to convert this value back to a legible date and time format.
Figure 2.
In Figure 2, we see that the key has the decimal value: 132286223503288727
From here, we can use CyberChef to convert this value back to a legible date and time format.
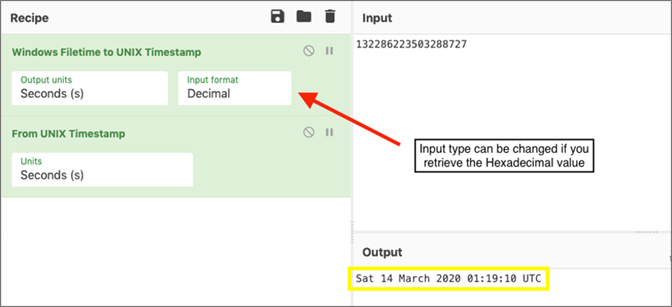 Figure 3. Windows Filetime conversion of KeyCreationTime registry key
Figure 3. Windows Filetime conversion of KeyCreationTime registry key
- UserAssist
- RecentApps
- Shimcache
- Last-Visited MRU
- Windows Background Activity Moderator (BAM)
Background and Context
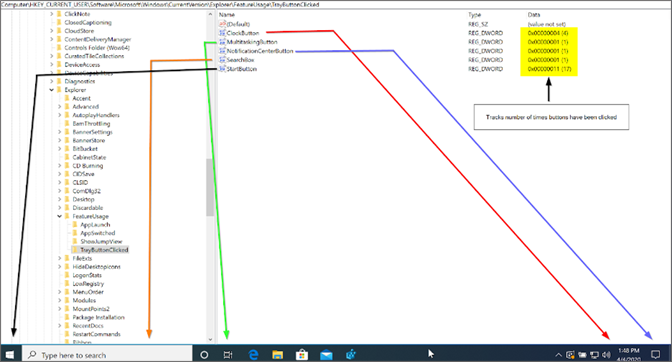
In this blog, we introduce a new registry artifact called “FeatureUsage,” which is found in builds of Windows 10 version 1903 and later. To a DFIR professional, this artifact is another way of confirming software that has been run interactively by an account, and how many times the software was run. In addition, it provides some insight into user behavior, such as how often an account switches between applications, looks at the Windows clock, clicks the Start menu and more. Figure 1. Windows 10 version containing FeatureUsage key
Figure 1. Windows 10 version containing FeatureUsage keyNTUSER.DAT file), and therefore all information stored within FeatureUsage will be unique for each account.
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsageKeyCreationTime | REG_QWORD
This key contains a 64bit QWORD value that details when the key was initially created (the first time this user interactively logged on). This provides an artifact that DFIR professionals can use to ascertain or confirm when an account first accessed a machine interactively.
KeyCreationTime Conversion
The KeyCreationTime registry key is stored in the Windows Filetime format. This format details the number of 100-nanosecond intervals that have passed since January 1, 1601 UTC. We can easily convert this to a valid timestamp using tools like CyberChef. By first converting to a Unix timestamp, it can then be converted to a valid date format that tells us the first time the account interactively logged onto a system. A potential use case for this key is to highlight or help verify the presence of a “hands-on-keyboard” adversary that has remotely logged onto a system for the first time (for example, by using RDP and a compromised service account) and has taken measures to wipe Windows event logs and other well-known forensic artifacts. Although this artifact is no replacement for a centralized logging and endpoint detection and response (EDR) solution, it may help to confirm or deny the presence of an adversary and the approximate time they first connected through RDP when these logs are unavailable.In the example below, we have retrieved a user’s registry hive (
NTUSER.DAT file) and loaded it into the Windows Registry Editor under the key name “TempHive” by clicking File > Load Hive.
 Figure 2.
Figure 2. NTUSER.DAT file loaded within the Windows Registry Editor Figure 3. Windows Filetime conversion of KeyCreationTime registry key
Figure 3. Windows Filetime conversion of KeyCreationTime registry keySubkey Overview
The FeatureUsage registry key has five subkeys. The keys exist for the purpose of taskbar metrics; however, for a DFIR professional, they can provide valuable insight into the usage of a system by an account.- AppBadgeUpdated
- AppLaunch
- AppSwitched
- ShowJumpView
- TrayButtonClicked
Each of these keys contains values that correspond to an executable or GUI-based application, the number of times run, and interactions through the taskbar.
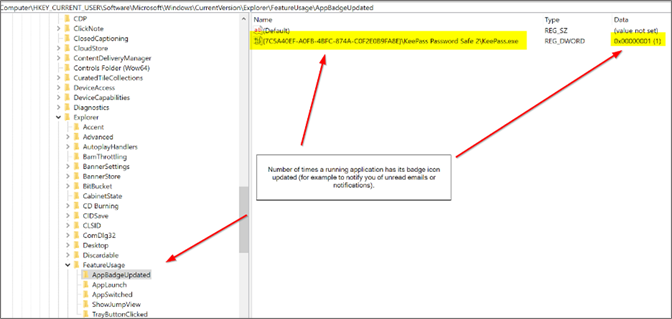
AppBadgeUpdated
This key provides the number of times a running application has its badge icon updated (for example, to notify you of unread emails or notifications). A potential use case of this key is to determine the quantity of notifications someone has received from a particular application. This may hold value — for example, in the case of a messaging application that has since been removed and wiped from the machine. The key may help to infer that the application was indeed used, and received a number of message notification updates during the time it was used.AppLaunch
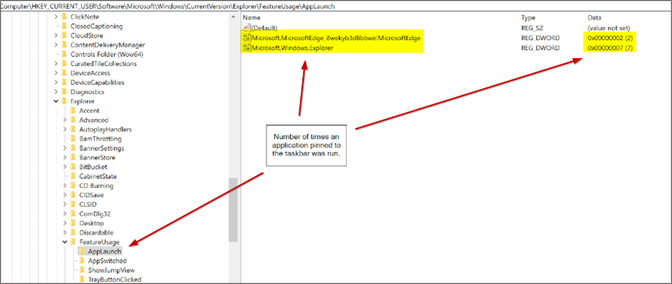
This key provides the number of times an application pinned to the taskbar was run.A potential use case of this key is to highlight an application that was pinned to the taskbar and how frequently it was run. In a criminal investigation, this may help to prove that an account holder knew about an application (as it is shown to them on the taskbar) and knowingly ran the application a certain amount of times from the pinned link.
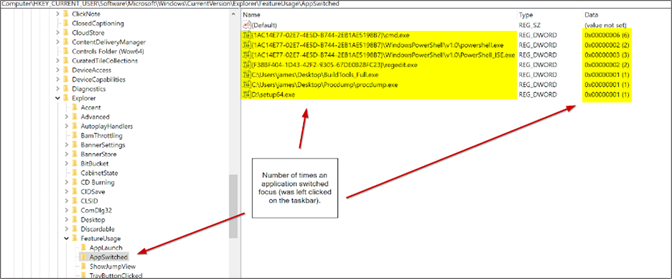
AppSwitched
This key provides the number of times an application switched focus (was left-clicked on the taskbar). This key functions much like the UserAssist and RecentApps registry keys and can be used to find evidence of GUI application execution; however, it instead shows the number of times the application was minimized or maximized, as opposed to just launched.ShowJumpView
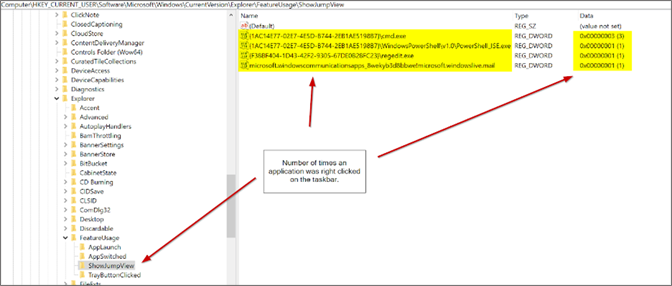
This key provides the number of times an application was right-clicked on the taskbar. Similar to the AppSwitched key, this key functions much like the UserAssist and RecentApps registry keys and can be used to find evidence of GUI application execution; however, it instead shows the number of times the application was right-clicked as opposed to just launched.TrayButtonClicked
This key provides the number of times built-in taskbar buttons were clicked (e.g., clock, Start button, etc.). Using this key, an investigator may be able to gain further insight into user behavior and how someone interacts with the operating system based on the number of times that taskbar buttons are clicked. A potential use case for this is to determine how frequently an account has been interactively used.Conclusion
By analyzing the FeatureUsage registry key, a DFIR professional may be able to further validate their findings with other known forensic artifacts to help strengthen their findings during an investigation. This may also provide insight into the potential use of RDP, when it first occurred, and if anti-forensic techniques were employed by an actor to remove more well-known forensic artifacts, or in the case of a criminal investigation, it may provide some insight into user behavior and how they interact with Windows.
Additional Resources
- Find out how CrowdStrike can help your organization answer its most important security questions: Visit the CrowdStrike Services webpage.
- Learn how any size organization can achieve optimal security with Falcon Complete by visiting the product webpage.
- Learn more about CrowdStrike Falcon® Intelligence threat intelligence by visiting the webpage.
- Learn about CrowdStrike’s comprehensive next-gen endpoint protection platform by visiting the Falcon products webpage.
- Test CrowdStrike next-gen AV for yourself: Start your free trial of Falcon Prevent™.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)