As cyberattacks continue to grow relentlessly, enterprises have to continue improving their cyber defenses to stay one step ahead of the adversaries. One area that CISOs have recently started paying more attention is identity threat protection. This is not surprising considering 80% of modern attacks are identity-driven leveraging stolen credentials. In fact, identity threat detection and response is highlighted as one of the top trends in cybersecurity in 2022 by Gartner. Their key recommendation includes: “Prioritizing the security of identity infrastructure with tools to monitor identity attack techniques, protect identity and access controls, detect when inclusions are occurring, and enable fast remediation.”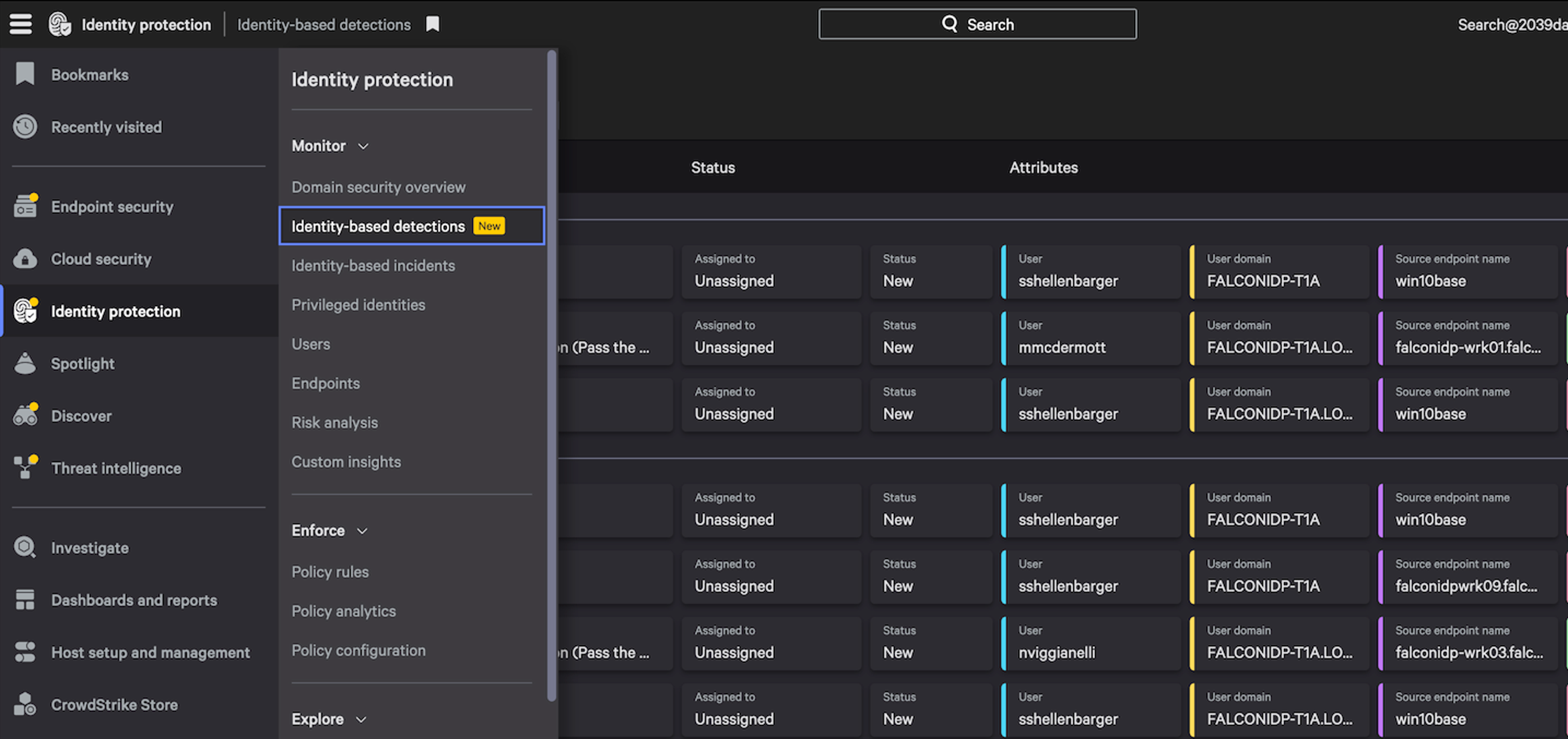 Figure 3. The Falcon platform’s standard Detections interface used for identity threat detections (Click to enlarge)
Figure 3. The Falcon platform’s standard Detections interface used for identity threat detections (Click to enlarge)
CISOs have started looking at the most effective and optimal way to address identity threats without overwhelming their security operations center (SOC) with yet another standalone tool that isn’t integrated with the rest of their security stack, causing additional alert fatigue. One option is to simply settle for identity security features or modules included in enterprise bundles from their identity and access management (IAM) legacy vendors. In a previous post, we examined the pitfalls of this approach including competing interests of the vendor, lack of security focus and risk of vendor lock-in. Essentially, settling for an identity security solution from your identity vendor will lead to poorer security outcomes and increase the risk of breaches.
Point Solutions Are Not the Answer
Another option we examine in this post is a standalone identity security solution that security teams can deploy separately and integrate with their SOC. A web search for “workforce identity protection” or “AD security” yields a number of solutions from various vendors that can potentially fit the bill. They all claim to protect against identity-based threats. Not so fast. Here are a few reasons why point solutions to address identity threats in isolation is a bad idea:- Deployment/integration overhead: A separate standalone solution would require you to deploy it and integrate with the rest of the tools in the SOC to get any value out of it. Even with a custom integration, your SOC personnel would still need to deal with multiple disparate consoles to correlate threats across endpoints, identity and workloads.
- Agent sprawl/maintenance: As every standalone solution has its own agent, you would end up with agent sprawl and consequent maintenance overheads. A multitude of agents from different vendors would slow down performance at best and could interfere with each other at worst. Further, the onus of keeping all the agents up to date across the organization is on you.
- Lack of correlation: The biggest challenge of this approach is the lack of correlation of threats across endpoints and identity. Your SOC personnel would have to traverse multiple consoles and manually correlate threats across endpoints and identity to detect an attack.
- Lack of automated responses: While quick and accurate detection are important, what you really need are automated policy-based responses such as blocking the adversary or throwing a multifactor authentication (MFA) challenge. Crafting automated policy-based responses across different products can be a huge challenge.
- Slower response: The frustration over manually correlating threats and lack of responses based on automated policies would slow you down when dealing with a real attack. Worse, the fatigue of dealing with multiple alerts from different systems could cause SOC personnel to miss actual threats.
A Unified Security Platform Is the Best Solution
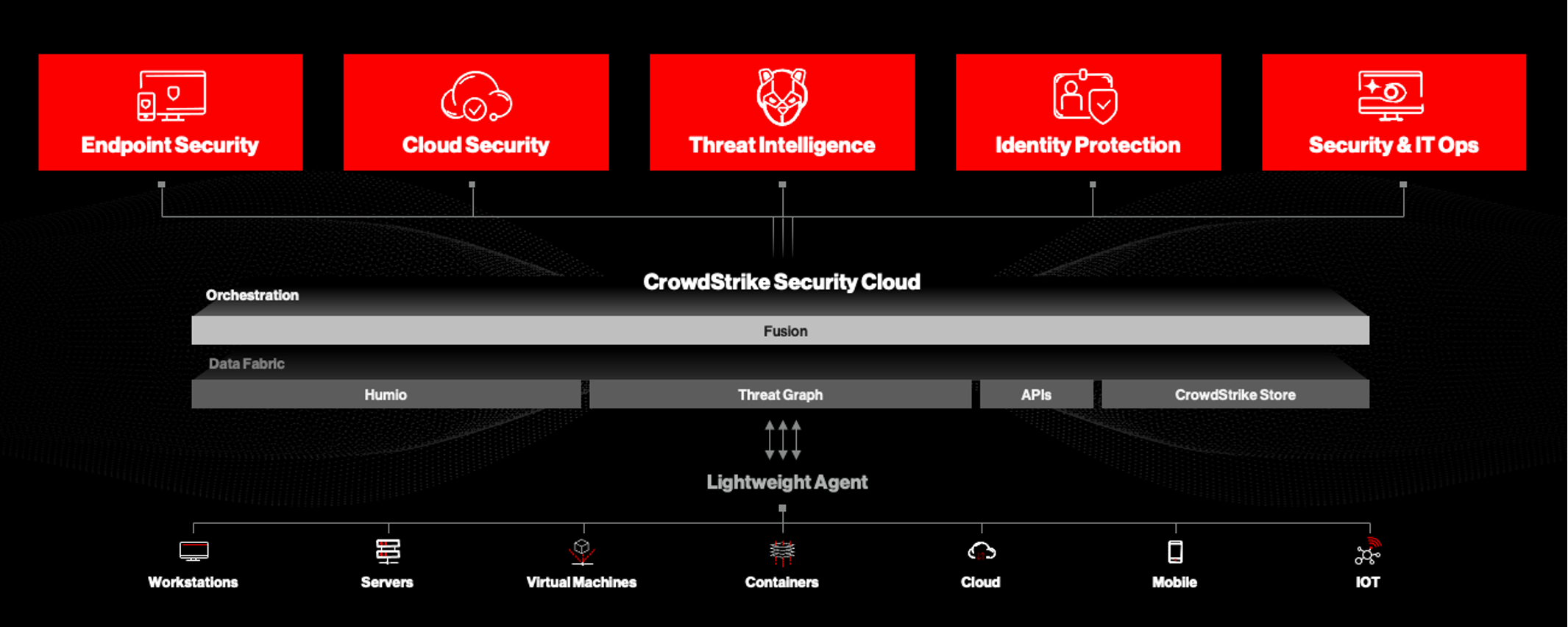
The right way to address these challenges is a unified platform approach that seamlessly integrates telemetry from across customer endpoints, workloads, identities and data to offer accurate detections and real-time protection without overwhelming your SOC personnel. Here are the key platform differentiators you can expect from the CrowdStrike Falcon® Identity Threat Protection™ solution:
- Single unified sensor: The same stable and reliable CrowdStrike Falcon®® sensor that protects millions of endpoint devices can protect your AD domain controllers as well. It has the intelligence to pull the relevant identity data into the unified Falcon platform, simplifying the deployment architecture. This single-sensor approach not only eliminates deployment overheads and agent sprawl but also ensures easier maintenance.
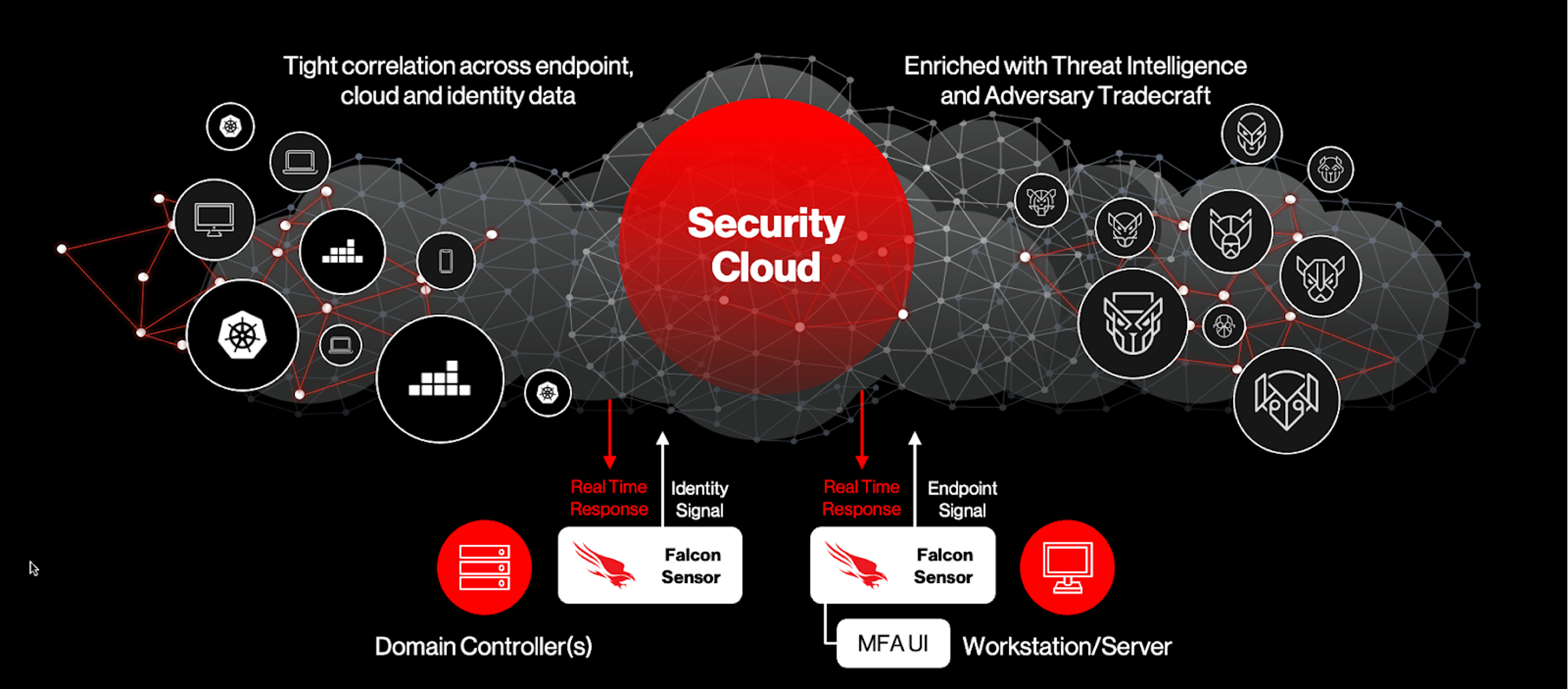
- Single unified platform: The Falcon platform is powered by the CrowdStrike Security Cloud — one of the world’s largest unified, threat-centric data fabrics — that correlates trillions of security events per day with indicators of attack (IOAs), the industry’s leading threat intelligence and enterprise telemetry from across customer endpoints, workloads, identities and data. This holistic platform approach ensures a rapid, cohesive response to threats that is very hard to achieve by cobbling together disparate point solutions.
- Standard detections interface: The single platform approach ensures your SOC personnel have a unified view of identity threat detections in the Falcon console instead of having to traverse multiple consoles. This familiar interface not only reduces training overheads but would be invaluable in the event of an actual attack, where every second is precious.
 Figure 3. The Falcon platform’s standard Detections interface used for identity threat detections (Click to enlarge)
Figure 3. The Falcon platform’s standard Detections interface used for identity threat detections (Click to enlarge)- Tight correlation across endpoints and identity: Another key benefit of the unified platform approach is that it can apply intelligence to automatically correlate threat data as well as response across endpoints and identity. For example, the Falcon sensor can block the authentication operation from an endpoint that may have been compromised or block an endpoint used by a user that is determined to be risky.
- Real-time automated response: The platform approach and tight correlation also enables the orchestration of rapid, automatic response to block threats in real time via a flexible policy engine (e.g., a policy that automatically enforces an MFA challenge to the user when the request comes from an unmanaged endpoint like a temporary contractor’s laptop). This type of automation is hard to implement when your endpoint and identity protection solutions are not fully integrated.
- Fully managed option: While this unified approach significantly simplifies the deployment and operation of your SOC, you may prefer a fully managed offering if you do not have the in-house resources to take on adversaries. CrowdStrike is the only security-focused vendor to offer a fully managed identity threat protection solution that provides expert management, monitoring and remediation to deliver frictionless, real-time identity threat prevention — all backed by an industry-leading Breach Prevention Warranty.
Conclusion
The importance of this platform approach to take on adversaries is also recognized by analysts. In his recent paper “Identity & Security: Addressing the Modern Threat Landscape,” John Tolbert from KuppingerCole makes the case as to why a unified security and identity approach is necessary to deter malicious actors. Download his white paper to get an analyst’s perspective on why consolidating identity protection into a unified security platform is key.Endnotes
- Gartner, Top Trends in Cybersecurity 2022, Peter Firstbrook, Sam Olyaei, Pete Shoard and others, 18 February 2022.
Additional Resources
- Learn more about attack techniques leveraging identities at Fal.Con 2022, the cybersecurity industry’s most anticipated annual event. Register now and meet us in Las Vegas, Sept. 19-21!
- Learn how CrowdStrike Falcon® Identity Protection products reduce costs and risks across the enterprise by protecting workforce identities.
- Watch this video to see how Falcon Identity Threat Protection detects and stops ransomware attacks.
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)