Countless headlines report what we already know all too well: No matter how advanced cybersecurity prevention tools are, with enough motivation, time and resources, adversaries will eventually devise a way to get through defenses. In order to stay ahead of these threats, organizations need to adopt a strong endpoint protection strategy. The core elements of an endpoint protection strategy must integrate both next-generation antivirus (NGAV) for prevention and endpoint detection and response (EDR) for detection of threats. This along with IT service management (ITSM) to improve IT productivity and security orchestration, automation and response (SOAR) for vulnerability management is required to boost the security posture of any organization.
NGAV uses a combination of artificial intelligence (AI), behavioral detection, machine learning algorithms and exploit mitigation to anticipate and immediately prevent both known and unknown threats. NGAV solutions can be cloud-based and deployed in hours, reducing the burden of maintaining software, managing infrastructure and updating signature databases.
EDR records the activities and events taking place on endpoints and all workloads, providing security teams with the visibility they need to uncover incidents that would otherwise remain invisible. An EDR solution needs to provide continuous and comprehensive visibility into what is happening on endpoints in real time. EDR solutions should offer advanced threat detection, investigation and response capabilities — including incident data search and investigation alert triage, suspicious activity validation, threat hunting, and malicious activity detection and containment.What Is the Difference Between NGAV and EDR, and Why Do I Need Both?
Antivirus is the prevention component of endpoint security, which aims to stop cyber threats from entering a network. When threats slip past an antivirus, EDR detects that activity and allows teams to contain the adversary before they can move laterally in the network.
While traditional antivirus solutions may prevent known ransomware, they fail at detecting unknown malware threats. The CrowdStrike Falcon® platform provides NGAV against known and unknown malware using AI-powered machine learning. Rather than using signatures in an effort to detect known malware iterations, Falcon looks for indicators of attack (IOAs) to stop ransomware before it can execute and inflict damage.
CrowdStrike Falcon® Insight™ EDR acts like a surveillance camera across all endpoints, capturing enriched events for automatic detection of malicious activity not identified by prevention methods and providing visibility for proactive threat hunting. Falcon Insight harnesses the power of machine learning and behavioral analytics to analyze and search the crowdsourced attack data to help uncover new tactics, techniques and procedures (TTPs) associated with attackers and discover new IOCs and IOAs — ultimately helping to stop evolving, previously unknown threats before they can become a breach and wreak havoc on the organization’s environment.
How CrowdStrike and ServiceNow Can Help
CrowdStrike and ServiceNow have partnered to provide a seamless and efficient experience for security analysts using automation, orchestration and intelligence to holistically manage threat lifecycle management, starting with visibility and analysis across IT environments, and ending with the ability to identify, prioritize and streamline investigations and quickly mitigate and recover from security incidents.
Our integrations with ServiceNow provide joint customers with a choice of eight different integration applications to help effectively orchestrate and automate incident response with timely contextual insights and streamlined workflows.
This helps you:
Additional Resources
What Is the Difference Between NGAV and EDR, and Why Do I Need Both?
Antivirus is the prevention component of endpoint security, which aims to stop cyber threats from entering a network. When threats slip past an antivirus, EDR detects that activity and allows teams to contain the adversary before they can move laterally in the network.
While traditional antivirus solutions may prevent known ransomware, they fail at detecting unknown malware threats. The CrowdStrike Falcon® platform provides NGAV against known and unknown malware using AI-powered machine learning. Rather than using signatures in an effort to detect known malware iterations, Falcon looks for indicators of attack (IOAs) to stop ransomware before it can execute and inflict damage.
CrowdStrike Falcon® Insight™ EDR acts like a surveillance camera across all endpoints, capturing enriched events for automatic detection of malicious activity not identified by prevention methods and providing visibility for proactive threat hunting. Falcon Insight harnesses the power of machine learning and behavioral analytics to analyze and search the crowdsourced attack data to help uncover new tactics, techniques and procedures (TTPs) associated with attackers and discover new IOCs and IOAs — ultimately helping to stop evolving, previously unknown threats before they can become a breach and wreak havoc on the organization’s environment.
Why IT/SecOps Collaboration Is Critical for Remediating Threats
Adversaries move at machine speed, and to stay ahead, security and IT teams need to leverage tools that can automate the process using the power of the cloud so that they can collaborate quickly and effectively on vulnerability and incident response.Challenges security teams face include:
- Not enough resources, and teams are already stretched when sifting through large amounts of data with no context
- Manual and time-consuming processes that can be prone to errors when managing and tracking threats
- Siloed data and disconnected security products and teams that can result in cumbersome processes and manual handoffs during investigation, response and remediation
How CrowdStrike and ServiceNow Can Help
CrowdStrike and ServiceNow have partnered to provide a seamless and efficient experience for security analysts using automation, orchestration and intelligence to holistically manage threat lifecycle management, starting with visibility and analysis across IT environments, and ending with the ability to identify, prioritize and streamline investigations and quickly mitigate and recover from security incidents.
Our integrations with ServiceNow provide joint customers with a choice of eight different integration applications to help effectively orchestrate and automate incident response with timely contextual insights and streamlined workflows.
This helps you:
- Prioritize security incidents. Share relevant endpoint security events detected by the CrowdStrike Falcon® platform with
ServiceNow and automatically create Security Incident Response tickets for centralized analysis, automated workflow and streamlined response. - Utilize threat intelligence. Enrich ServiceNow security incidents with CrowdStrike’s leading threat intelligence to gain additional insight into attacker attribution and the scope of the incident.
- Expedite investigations. Accelerate investigations within ServiceNow by bringing back all relevant endpoint event activity captured by CrowdStrike.
- Remediate threats. Enable security teams to quickly perform remediation tasks by leveraging Falcon Real Time Response (RTR) before an incident results in a breach.
Choose From Two Available Options
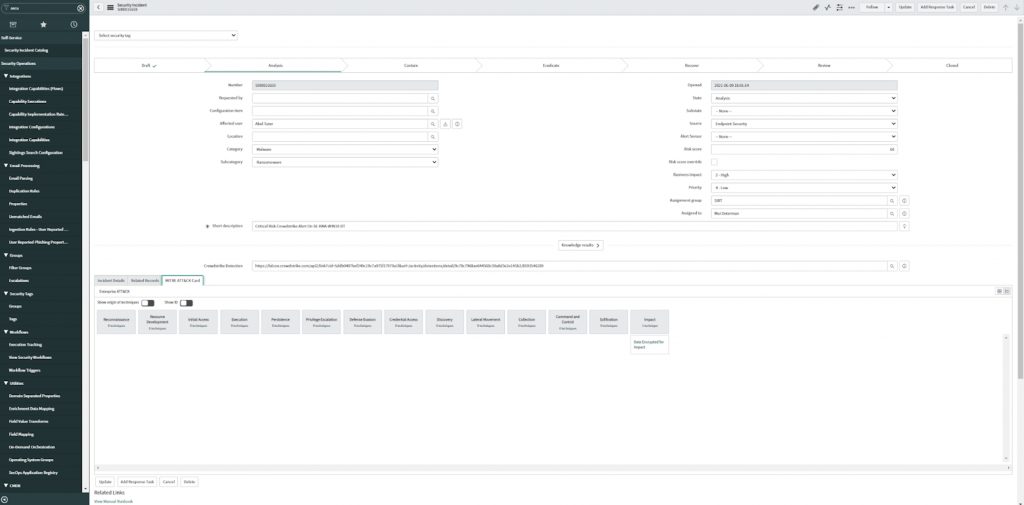
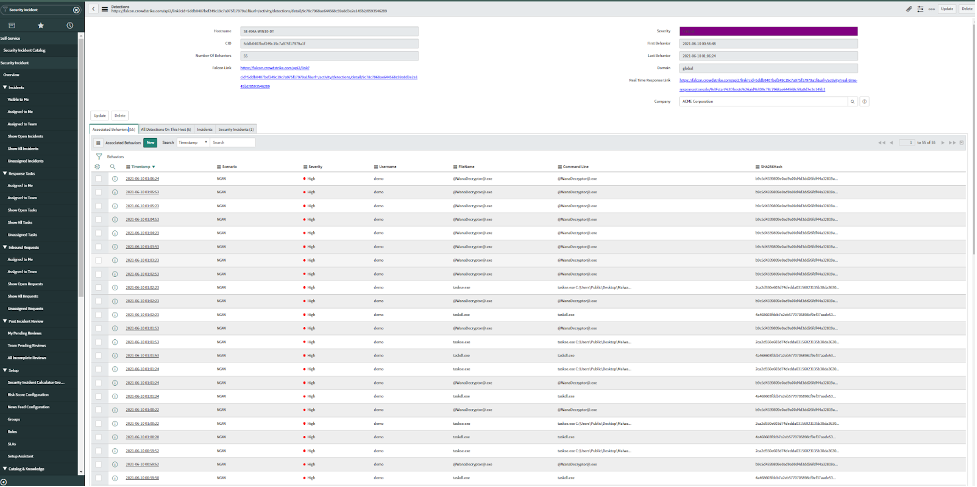
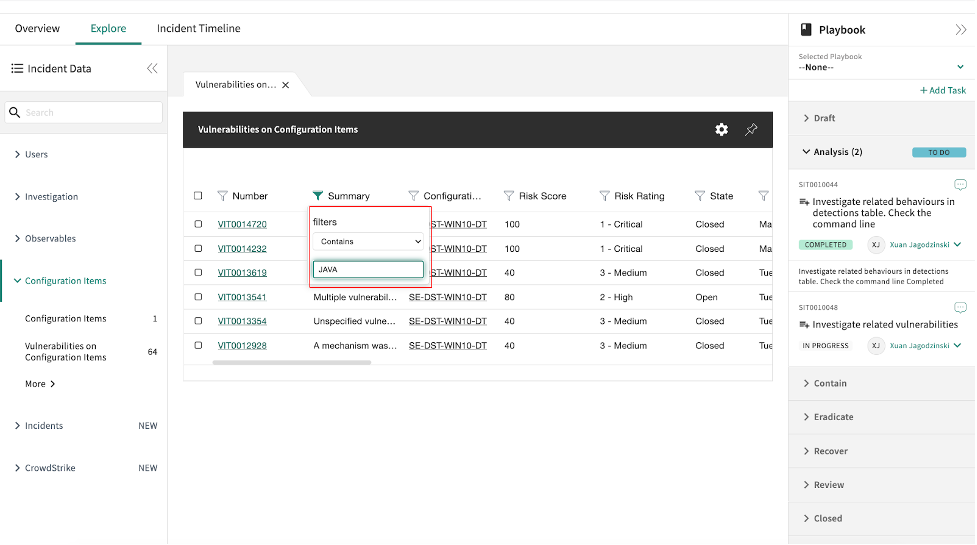
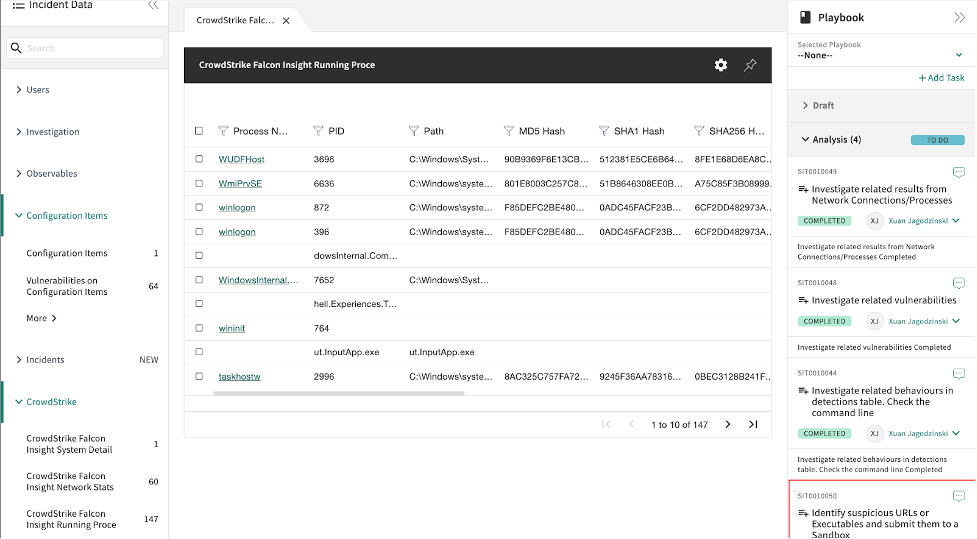
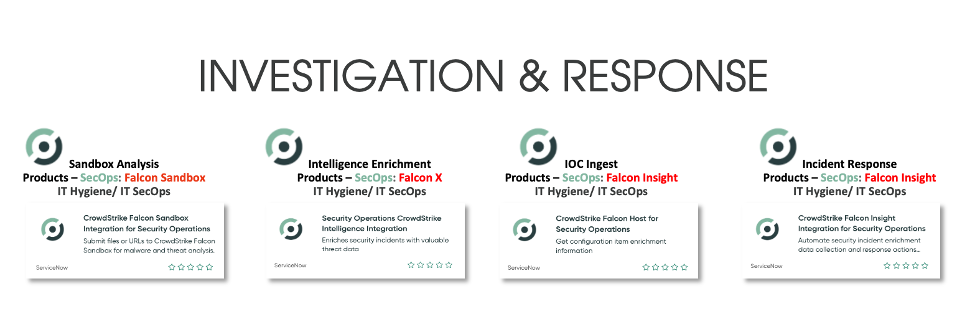
Two types of alerting options are now available in the ServiceNow store: CrowdStrike Falcon® Endpoint and CrowdStrike Falcon® Endpoint for Security Operations. Depending on which ServiceNow product is in use, the integrations can create alerts in ITSM or IT Incident Response. Vulnerability and Asset Import are also available with CrowdStrike Falcon® Spotlight™ for vulnerability response and Service Graph Connector for CrowdStrike. All endpoint detection telemetry from CrowdStrike is sent with enriched metadata about compromised host and process information and threat feeds to ServiceNow, using APIs and orchestration. Incidents created on ServiceNow are enriched with metadata from CrowdStrike to help: In addition to ingestion, our applications provide investigation and response capabilities to aid in remediation. Security teams can now use the tickets to help accelerate their investigations on the endpoints and perform remediation before threats become breaches. The lifecycle of a successful malware strategy in the ServiceNow platform comes down to three pillars: validation, containment and eradication. Starting with the investigation and validation phase, CrowdStrike Falcon® Endpoint app collects detailed event data from the malicious incident, from which we can prioritize incidents by correlating this security data with asset data in the CMDB. Our ServiceGraph integration brings in system details such as MAC address, operating system details and cloud metadata. We can then leverage the CrowdStrike Falcon Insight Integration for Security Operations app to gather more information on the status of a host. For example, we can retrieve a list of running processes, active network connections and logged-on users. All of this helps with the containment part of the strategy — our integrations deliver required contextual information for identified malicious behavior and give analysts the confidence and ability to isolate the host of a malware attack. From there, we can determine appropriate response actions, using Falcon RTR to eradicate the infection. Intelligence capabilities are also exposed through our integrations. Collected indicators of compromise (IOCs) can be searched in the CROWDSTRIKE FALCON® INTELLIGENCE™ intelligence database for threat intel enrichment. Additionally, indicators can be shared from the ServiceNow platform back to CrowdStrike, enhancing hunting capabilities. These indicators can also be sent to Falcon Sandbox™ for detailed sandbox analysis. CrowdStrike and ServiceNow are helping businesses to level up their security operations by helping to automate processes and use orchestration to dramatically improve response times for security incidents before they become a breach. We encourage you to attend the “Ask the Expert” session hosted by ServiceNow on June 30, 2021, to learn more about our integrations.Additional Resources
- Visit CrowdStrike in the ServiceNow Store.
- Learn more about the CrowdStrike and ServiceNow integration in this solution brief.
- Get more information about CrowdStrike Falcon® Insight endpoint detection and response.
- Learn more about the CrowdStrike Falcon® platform.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)