- AI-powered indicators of attack (IOAs) are the latest evolution of CrowdStrike’s industry-first IOAs, expanding protection with the combined power of cloud-native machine learning and human expertise
- AI-powered IOAs use the speed, scale and accuracy of the cloud to rapidly detect emerging classes of threats and predict adversarial patterns, regardless of tools or malware used
- AI-powered IOAs are now available for CrowdStrike customers, requiring no configuration and at no additional cost
CrowdStrike today unveiled the next evolution of CrowdStrike’s industry-first IOAs: artificial intelligence (AI)-powered IOAs. Available to customers immediately, AI-powered IOAs are created by cloud-native machine learning (ML) models trained on the rich telemetry of the CrowdStrike Security Cloud — the engine powering the largest market share of deployed sensors in the enterprise security landscape — and expertise from our elite threat hunting teams to predict and proactively protect against emerging classes of threats. This milestone extends our approach of unifying AI and human expertise (as we have done with CrowdStrike Falcon® OverWatch™) to deliver unparalleled protection.
AI-generated IOAs fortify existing defenses (see Figure 1) by using cloud-based ML and real-time threat intelligence to analyze events at runtime and dynamically issue IOAs to the sensor. The sensor then correlates the AI-generated IOAs (behavioral event data) with local events and file data to assess maliciousness. AI-powered IOAs operate asynchronously alongside existing layers of sensor defense, including sensor-based ML and existing IOAs.
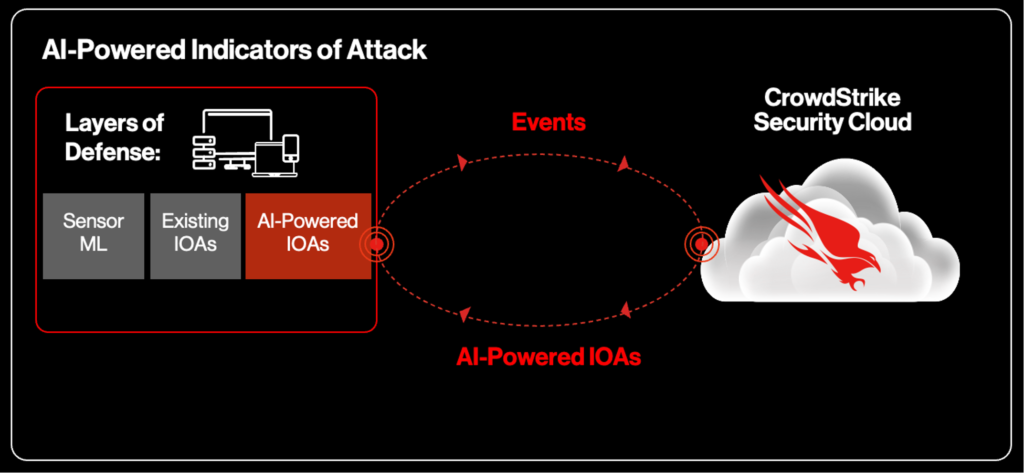 Figure 1. AI-powered IOAs issued by cloud-native ML models trained on the rich telemetry of the CrowdStrike Security Cloud
Figure 1. AI-powered IOAs issued by cloud-native ML models trained on the rich telemetry of the CrowdStrike Security CloudKey Benefits of AI-Powered IOAs
- Detect emerging classes of threats faster than ever: Stay one step ahead of adversaries by predicting shifting tradecraft and enabling proactive local defense that works alongside existing layers of defense.
- Drive automated prevention with high-fidelity detections: Cloud-native AI models share real-time IOAs with the CrowdStrike Falcon®® sensor to shut down attacks, irrespective of the specific malware or tools used.
- Reduce false positives and improve productivity: Trained on expert acumen and activated at cloud-scale, AI-powered IOAs synthesize insights from CrowdStrike’s world-renowned threat hunting team to minimize the number of false positives security teams have to deal with. This helps maximize analyst productivity and delivers automated threat hunting expertise at scale.
Foundation: What Are Indicators of Attack?
An industry-first pioneered by CrowdStrike, indicators of attack (IOAs) are sequences of observed events that indicate an active or in-progress attempt to breach a system (such as code execution, persistence and lateral movement). Tracking events as a sequence allows analysts to identify how adversaries initially gain network access and then quickly infer their motivation or objectives. By tracking key execution points across an attack surface, IOAs enable analysts to paint a full picture of an attack, regardless of malware or tools used. Beyond alerting to active attacks, IOAs apply advanced behavioral analysis to model and predict adversary patterns, delivering enhanced prevention against future attacks.
Focusing on IOAs gives customers multiple advantages over solely relying on indicators of compromise (IOCs). First, IOAs enable customers to detect attacks before or as they emerge, rather than after a system has been compromised — thus enabling a proactive and preventative defense strategy. Relying solely on IOCs puts an organization a step behind adversaries, as they alert analysts to the presence of adversaries after systems have been compromised (a reactive approach).
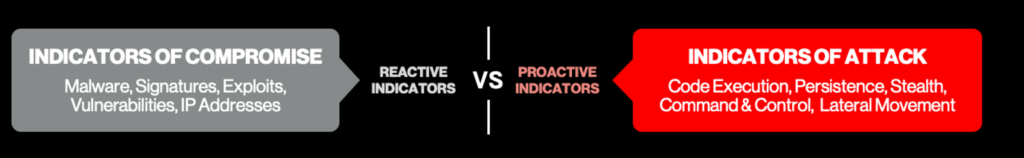 Figure 2. Indicators of compromise vs. CrowdStrike indicators of attack
Figure 2. Indicators of compromise vs. CrowdStrike indicators of attackSecond, by focusing on adversarial motivations rather than specific malware or tools used, IOAs enable customers to adapt to new classes of attacks and shifting adversarial tradecraft, such as malware-free or fileless attacks, which accounted for 62% of attacks in the last year, according to the CrowdStrike 2022 Global Threat Report.
Finally, because IOAs are generic in nature, they can be evaluated in parallel (enabling both computational efficiency and scalability) and don’t need to be updated as frequently as signature-based approaches (as is the case with IOCs).
Expanding Capabilities of IOAs with AI
Until now, the process of generating IOAs has primarily relied on the applied expertise of world-renowned threat hunters, resulting in a highly sophisticated and highly accurate indicator. To enable customers to stay ahead of tomorrow’s threats, the process of detecting and classifying active attacks needs to exceed the speed of our adversaries, without compromising on the incredible fidelity of expert-generated IOAs. To accomplish this, we’ve married human expertise with ML to expand our capacity to issue IOAs and enhance the quality of expert-generated IOAs, making detections even more comprehensive and proactive, while retaining high levels of fidelity.
We’ve rigorously trained models to detect suspicious activity on enormous, expertly curated data sets of malicious threats and benign activities. Leveraging the power of the CrowdStrike Security Cloud to train these models on our cloud-native CrowdStrike Falcon® platform, our machine learning models can synthesize enormous volumes of threat intelligence with unparalleled speed, scale and accuracy. By bringing the power of cloud-based ML to the process of developing IOAs, customers continue to benefit from the proactive, high-fidelity signals that IOAs provide, now with the speed and scale of the cloud.
Examples of AI-Powered IOAs
Since going into production, our cloud ML models have conclusively identified over 20 new indicator patterns, which have been validated by experts and enforced on the Falcon platform for automated detection and prevention. Below we’ll examine two examples of adversary tactics we’ve detected, which resulted in new IOAs for post-exploitation payloads and PowerShell attacks. Over the next few months, we’ll continue to share examples of new classes of IOAs and how they help customers stay one step ahead of adversaries.
Post-Exploitation Payload Detections
Let’s start with the example of post-exploitation payloads. A post-exploitation payload is the code that an adversary transfers to a host once they have achieved initial access. These payloads vary and could be anything from a command-and-control beacon to a sophisticated ransomware threat. The AI-powered IOAs identify these by combining the output of our static Windows sensor AI model with how a file is run and with knowledge only available through the CrowdStrike Security Cloud. For example, we can include information on the process ancestry and the modalities of how the process was launched. With this additional data, we can achieve incredibly accurate detections and rich indicators, boosting accuracy beyond what is possible with either a static or behavioral approach alone. Known adversary groups we’ve tracked associated with these attack techniques include CARBON SPIDER, WIZARD SPIDER, PRIMITIVE BEAR and VENOMOUS BEAR.
PowerShell IOAs Through the Eyes of AI
PowerShell is frequently leveraged by adversaries to deliver shellcode or tools like Mimikatz or execute malicious behaviors where an IOC will never be present on disk. These types of attacks are harder to identify, and traditional signature-based methods are easily bypassed with changes to the script or command line.
Using the power of deep learning models to automatically extract the most relevant code sections from PowerShell scripts, we can identify and protect against PowerShell-driven fileless threats. This AI has been taught to “read'' PowerShell scripts and understand the difference between legitimate and malicious code flows. It can understand encoded and obfuscated scripts faster and in ways human researchers cannot, enabling it to deliver proactive high-fidelity detection that is more difficult for adversaries to bypass. Known adversary groups that have used PowerShell to orchestrate attacks include CYBER SPIDER, OCEAN BUFFALO, HELIX KITTEN and STONE PANDA.
Conclusion
Machine learning remains a critical tool for detecting emerging patterns in data and conducting in-depth behavioral analysis to understand adversary intents and objectives. As a leader in cloud-delivered protection of endpoints, cloud workloads, identity and data, CrowdStrike is excited to keep harnessing the combined power of AI and the cloud to enhance defense, upend adversary tradecraft and help our customers stay one step ahead of adversaries to stop breaches.
Additional Resources
- Find out more about today’s adversaries and how to combat them at Fal.Con 2022, the cybersecurity industry’s most anticipated annual event. Register now and meet us in Las Vegas, Sept. 19-21!
- Read more about indicators of attack.
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)






















































