Japan, known for its innovation and efficiency, is a globally recognized industry leader. This puts Japan-based organizations at risk of being recognized as potentially valuable targets by both criminally motivated and targeted cyber adversaries. This blog, directly from the front lines of CrowdStrike® Falcon OverWatch™ threat hunting, shares intrusion insights drawn from activity observed in Japan throughout 2022 and provides actionable recommendations for securing your environment in 2023 and beyond.
Cybersecurity: A National Security Issue
In late 2022, Japan’s government updated its National Security Strategy (NSS) to reflect the state of the current threat landscape. This comprehensive document outlines the government's approach to national security, including its cybersecurity policy. In particular, the NSS highlights just how widespread the cybersecurity threat is and outlines a national response to address supply chain risks, protect critical infrastructure and prevent intellectual property theft
The revised NSS notes several key improvements, such as increased investment in cybersecurity by Japan’s Self-Defence Force, a large increase in the number of cyber personnel trained to actively defend Japan from cyberattacks, and enhanced cooperation with regional allies and international alliances.
Equally, the NSS acknowledges that the ever-increasing cyber threat to Japanese government institutions and private organizations requires a joint response effort among government, business and security experts. To participate in this partnership, security practitioners across business must understand, in detail, the threats impacting Japan.
Insights from the Security Industry
CrowdStrike has been actively protecting Japanese organizations for several years. During this time, the Falcon OverWatch threat hunters have seen firsthand the evolution of the threat to Japanese organizations and have been tracking these trends to inform the continued strengthening of their proactive hunting efforts against interactive cyberattacks.
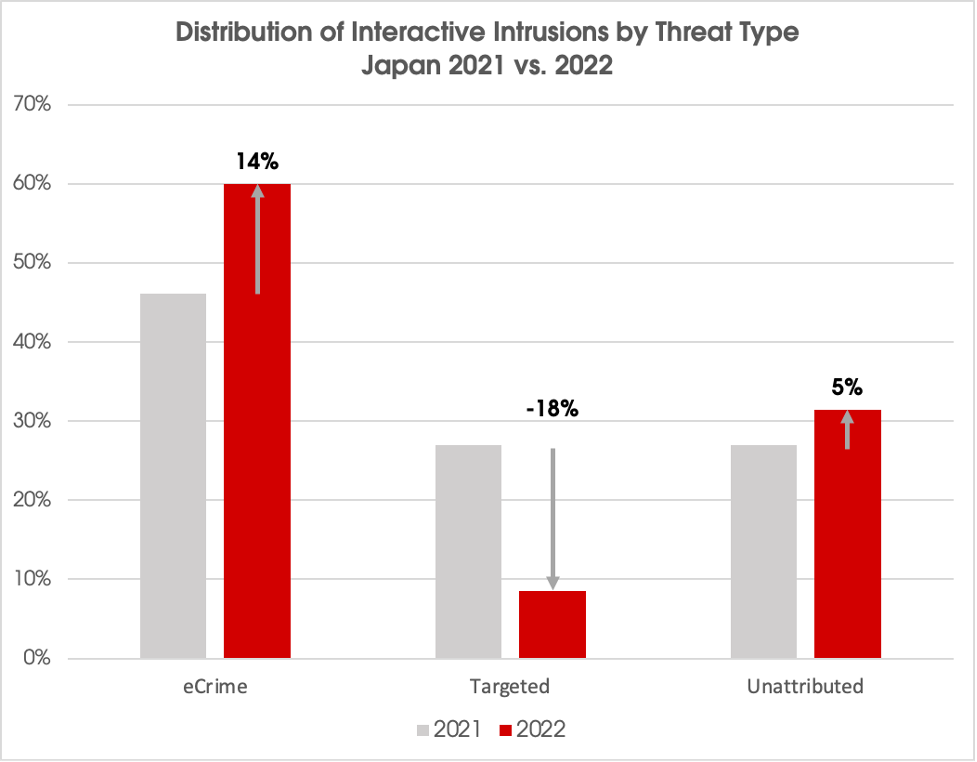
Over the past three years, interactive intrusion activity against Japan-based organizations has seen sustained year-over-year increases. In particular, an increasing proportion of intrusions has been attributed to eCrime activity. During 2022, eCrime accounted for 60% of all interactive intrusion activity observed by Falcon OverWatch.
Targeted intrusion (aka state-nexus) activity made up 9% of all intrusions uncovered, while the remaining 31% of observed intrusions were unattributed. This is compared with 2021, when eCrime accounted for 46% of activity, and targeted intrusion operations accounted for 27% of activity.
Which Adversaries Are Operating in Japan and Why?
Understanding the motivations and tradecraft of key adversaries operating in Japan is an invaluable insight for defenders looking to improve their capacity to both detect and respond to the latest cyber threats.
Throughout 2022, suspected eCrime adversaries, named SPIDERs in CrowdStrike’s threat actor terminology, were the most prolific adversary group operating in Japan. Japan’s economic strengths make it an obvious target for financially motivated eCrime adversaries. Japan is an internationally recognized innovation hub and home to global brands across key sectors including technology, manufacturing and automotive. With an estimated gross domestic product (GDP) of $4.4 trillion USD in 2023, Japan is the third largest globally, with a GDP value representing more than 2.2% of the world's economy.1
Falcon OverWatch continues to observe eCrime adversaries targeting high economic growth industries in Japan as a means of generating revenue. In 2022, the technology, software and retail industries were the most commonly targeted. Technology and software companies in particular accounted for 36% of all intrusions observed by Falcon OverWatch, and of those intrusions, 62% were eCrime related.
Among the eCrime activity that Falcon OverWatch uncovered, hunters found activity carried out by two known eCrime groups: CARBON SPIDER and MUMMY SPIDER.
CARBON SPIDER, active in the eCrime space since approximately 2013, is a criminally motivated group that targets primarily the hospitality and retail sectors in pursuit of payment card data. Stolen payment data is sold on the dark web for use in further criminal enterprise, such as fraud or money laundering.
MUMMY SPIDER is an eCrime group known for their development of Emotet malware. Emotet is often deployed through initial access vectors such as phishing. Once executed, Emotet will often deploy further malware such as banking trojans or information stealers, which then work to collect and exfiltrate information from victims. Emotet can also deploy implants, which may be used by targeted intrusion operators to gain persistent command-and-control over a victim. The growing threat of data loss and data extortion is something organizations need to be acutely aware of. Adversaries have learned that stealing data, rather than simply encrypting data, places them in a much stronger negotiating position when it comes to making ransom demands.
Ransomware campaigns also remained persistently popular in Japan in 2022. Falcon OverWatch observed multiple ransomware families being deployed by eCrime adversaries, the most prevalent being Phobos ransomware. Adversaries deploying this type of ransomware tend to target externally accessible Remote Desktop Protocol (RDP) services as a means of access. By comparison, in 2021, Makop was the most prevalent ransomware family in Japan, also commonly deployed after initial access via unsecured RDP services.
Japan’s targeted intrusion activity was predominantly attributed to suspected China-nexus adversaries — named PANDAs in CrowdStrike adversary terminology— as well as SILENT CHOLLIMA (North Korea-nexus) and NEMESIS KITTEN (Iran-nexus). Organizations need to be particularly alert to the threat of nation-state economic espionage. This moves beyond traditional information-collection campaigns motivated by national security interests into espionage that is commercially motivated.
Again, Japan’s global reputation as an economic powerhouse makes Japan-based organizations an attractive target for adversaries with economic espionage objectives. Japan is considered a leader in technological innovation, and its products and services are highly sought-after globally. With a high concentration of valuable intellectual property and sensitive information, Japan is a valuable target for economically motivated espionage by state-nexus adversaries, including China-affiliated adversaries.Moreover, Japan and China’s complicated geo-political history may serve as a motivator for more traditional forms of nation-state espionage.
SILENT CHOLLIMA, a North Korea-nexus threat actor, appears to have begun shifting their objectives in 2015. This threat group has expanded beyond intelligence collection on government and military entities into economic espionage operations against privately owned companies with technology that could help DPRK develop its economy. Given Japan's proximity to North Korea and the geopolitical tensions in the region, Japanese organizations make for opportune targets for SILENT CHOLLIMA to carry out their objectives.
NEMESIS KITTEN, closely aligned with the Iranian government, is known to target misconfigurations and unpatched vulnerabilities in external-facing services, such as those in Microsoft Exchange and more recently Log4j. During follow-on activity, NEMESIS KITTEN often ransoms organizations using in-built encryption software, such as BitLocker full-disk encryption. Organizations must pay the ransom amount in exchange for decryption keys. Given Japan's strong economy and dependence on technology, Japanese organizations are a target for this kind of activity.
What Does This Threat Activity Look Like?
Both eCrime and targeted intrusion adversaries are increasingly using malware-free techniques to achieve their objectives against entities in Japan. Globally, 71% of all intrusion activity observed by Falcon OverWatch was malware-free. (For more information on global interactive intrusion trends, download a copy of the Falcon OverWatch 2022 Threat Hunting Report.)
eCrime adversaries, in particular, frequently use valid credentials to gain access to victim environments in an attempt to blend in with expected activity. The credentials are often obtained through access brokers — eCrime adversaries that specialize in gaining and then selling access to victim environments — or by brute-force attacks used to guess credentials on externally exposed services. Once access is achieved, eCrime adversaries are abusing legitimate remote access software to retain that access and conduct further command-and-control. Specific tooling observed in Japan includes TightVNC, AnyDesk and Atera Agent. Often these tools and the associated domains they contact are allowlisted by organizations to enable legitimate administrative use. However, Falcon OverWatch continues to observe adversaries bringing “packs” of these tools to compromised endpoints and attempting execution until one succeeds.
These trends are just two of the many examples of why human-driven threat hunting is such a critical part of the security equation. Seemingly valid users using legitimate and allow-listed tooling may not, on their own, trigger an alert from technology-based solutions. However, threat hunters can augment this information with behavioral indicators to rapidly piece together clues that the activity may be malicious. When coupled with technology-based identity threat detection and protection solutions, the door very quickly starts to close on adversaries.
Leverage People, Process and Technology to Stop Active Intrusions
In a recent intrusion against a Japanese entity, a suspected criminal adversary was observed conducting malicious interactive activity across multiple Windows hosts. The activity was preceded by a large volume of failed login attempts. This was indicative of likely password spraying, a type of brute-force attack where common passwords are tested against many different accounts in an attempt to discover valid account credentials.
Falcon OverWatch discovered the adversary operating with multiple sets of credentials in their possession. These credentials were used as the adversary deployed and attempted execution of a broad selection of adversary tooling, including GMER, PC Hunter, Defender Control and Process Hacker. These tools are commonly used by adversaries to attempt to disable security tooling.
The adversary proceeded to perform network reconnaissance operations, including scanning for devices with open RDP ports, likely as a precursor to planned lateral movement attempts. Falcon OverWatch often observes adversaries using multiple sets of valid credentials, which may be used for persistence, privilege escalation and lateral movement.
In this instance the victim organization was able to quickly act on Falcon OverWatch’s timely notifications to stop the adversary in their tracks before damage could be done. When it comes to responding to interactive intrusions, a timely response to Falcon OverWatch notifications is as important as the speed of the notification itself. In the CrowdStrike Falcon OverWatch 2022 Threat Hunting Report, Falcon OverWatch detailed a reduction in average breakout time for eCrime adversaries — the time taken for an adversary to move laterally from their initial beachhead — to 1 hour and 24 minutes.
CrowdStrike Falcon® Complete managed detection and response (MDR), which is seamlessly integrated with continuous Falcon OverWatch managed threat hunting, helps to identify, prevent and remediate active threats. Further, Falcon Complete’s Japanese-speaking analysts provide the opportunity for active partnership with organizations, ensuring that the details of any threats are clearly communicated and recommendations are offered to ensure risks are addressed comprehensiely
Five Top Tips to Secure Your Environment in 2023
Know Who’s Who
Identity threats are one of the most pervasive risks to organizations today. In 2022, 60% of intrusions Falcon OverWatch observed in Japan involved the abuse of valid accounts, and adversaries are commonly operating with multiple sets of valid credentials. Falcon OverWatch only expects this activity to grow, especially with the proliferation of access brokers such as PROPHET SPIDER, an eCrime actor known to obtain and then sell access to compromised organizations on the dark web and other forums. CrowdStrike Falcon® Identity Threat Detection and CrowdStrike Falcon® Identity Threat Protection provide additional visibility into unauthorized access and support additional layers of authentication, such as multifactor authentication (MFA), to ensure your organization’s identities remain secure.
Secure the Endpoint
As adversaries become more sophisticated, your defenses need to adapt. Traditional on-premises and hosted IT assets remain necessary gateways for the ongoing management of and access to critical cloud workloads, storage repositories and further infrastructure. As a result, these traditional assets also represent increasingly critical points of exposure for organizations as they increasingly rely on the active exchange of sensitive data, process flows and communications to operate and conduct business. With this large onset of data flow, organizations need to look to cloud-native platforms such as CrowdStrike Falcon to collect, organize and process the large volumes of events, while allowing for swift prevention and response through the Falcon sensor.
Secure the Cloud
Adversaries are continuing to adapt to the evolving world of cloud technology and are actively seeking to capitalize on the opportunity it presents to exploit gaps in an organization’s defenses. Falcon OverWatch has observed trends in adversaries gaining access to traditional endpoints and using tools to discover cloud infrastructure, such as enumerating cloud metadata.
Know the Adversary
Every adversary — such as CARBON SPIDER, NEMESIS KITTEN and PROPHET SPIDER discussed above — is unique. Each has their own set of tactics, techniques and procedures they employ to achieve their individual objectives. Knowing who these adversaries target and how they operate can assist organizations in preparing defenses.
Leverage People, Process and Technology
As we have seen in recent cases within Japan and beyond, adversaries are using advanced techniques to subvert technology systems and evade defenses, often blending in with legitimate administrative activities. To effectively detect and respond to this activity, a combination of people, refined processes and cloud-native technology is required. With Falcon OverWatch, organizations can feel more secure with our human experts hunting relentlessly, 24/7/365, for the last 1% of activity that would otherwise go undetected.
Additional Resources
- Learn more about Falcon OverWatch managed threat hunting
- See which threat actors may be targeting your industry or region by exploring the CrowdStrike Adversary Universe.
- Find out how the 24/7 expertise of Falcon Complete MDR can help your organization close the cybersecurity skills gap.
1 International Monetary Fund, World Economic Outlook Database, April 2023





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)