- New features in CrowdStrike Falcon® Device Control deliver enhanced data identification and enable investigation into data loss and exfiltration activities through USB devices.
- New file metadata capabilities let analysts see unique details about documents, files and data copied to external media devices.
- CrowdStrike’s industry-leading machine learning platform now detects source code movement and identifies over 40 programming languages.
CrowdStrike is delivering powerful new file movement visibility features in CrowdStrike Falcon. Device Control to help customers identify and mitigate the risk of data loss through USB devices.
Data exposure can cause tremendous damage to an organization, whether it stems from malicious intent or simple negligence. Legacy endpoint protection solutions often fail to provide the visibility and control required to identify and mitigate data loss incidents. These solutions lack visibility into files written to authorized removable media, source code movement, and the event data sets required to identify or investigate accidental data loss or deliberate data exfiltration. This problem is exacerbated by the extensive use of cheap and widely available USB devices. This lack of visibility and control can leave security teams in the dark when critical data leaves an organization.
The new capabilities in Falcon Device Control give customers a more powerful tool against data loss by combining enhanced file visibility and granular device control so analysts can ensure only approved devices are used in their environment and understand exactly what data is being written to those devices.
The industry-leading CrowdStrike Falcon® platform sets the new standard in cybersecurity. Watch this demo to see the Falcon platform in action.
Tracking Files and Source Code Written to USB
Organizations often lack visibility and context into external media activities and don’t have a systematic way to analyze files written to USBs at scale, making them vulnerable to data loss. Falcon Device Control now solves these challenges with enhanced file visibility and user activity context to help identify data loss and exfiltration activities. Organizations will be able to minimize the risk of data loss through:
Augmented USB file write visibility. In order to understand data exposure risk and accelerate data loss investigations, CrowdStrike has introduced enhanced visibility for USB file write activity. This new functionality provides detailed information about the user performing the activity, the USB device being used, and the type and volume of data being transferred.
Critically, by reporting on the application writing the file, as well as the source/destination file paths, Falcon enables analysts to focus on key data locations and better understand data provenance.
Automated identification of source code. Complementing the Falcon sensor's ability to identify common file types using binary file analysis, the Falcon Device Control module now includes an embedded deep learning-based classification algorithm that automatically identifies source code, with initial support for over 40 source code language families. Archive introspection and sensitivity label identification. The ability for users to quickly add files to zip archives is built into the OS and creates a visibility blind spot. Falcon Device Control now supports ZIP archive introspection for file writes to removable media. For most ZIP archives, including password-protected files, the new Falcon Device Control feature can sample and enumerate file names for investigations. Further, the new introspection mechanism reports Microsoft Purview Information Protection sensitivity labels for added context during investigations. This new file activity data is used to further enrich the vast telemetry powering the Falcon platform.
Catching Data Obfuscation in the Wild
Let's take a moment to see how this new functionality would work in practice with the fictitious character, Tom.
Tom has worked as an engineer for the better part of 10 years and has extensive access to intellectual property as part of his day-to-day activities. Tom is planning to move over to a competitor, unbeknownst to his company, and is using a USB device to facilitate the transfer of some proprietary information, including highly sensitive source code that he feels will help establish himself in his next role.
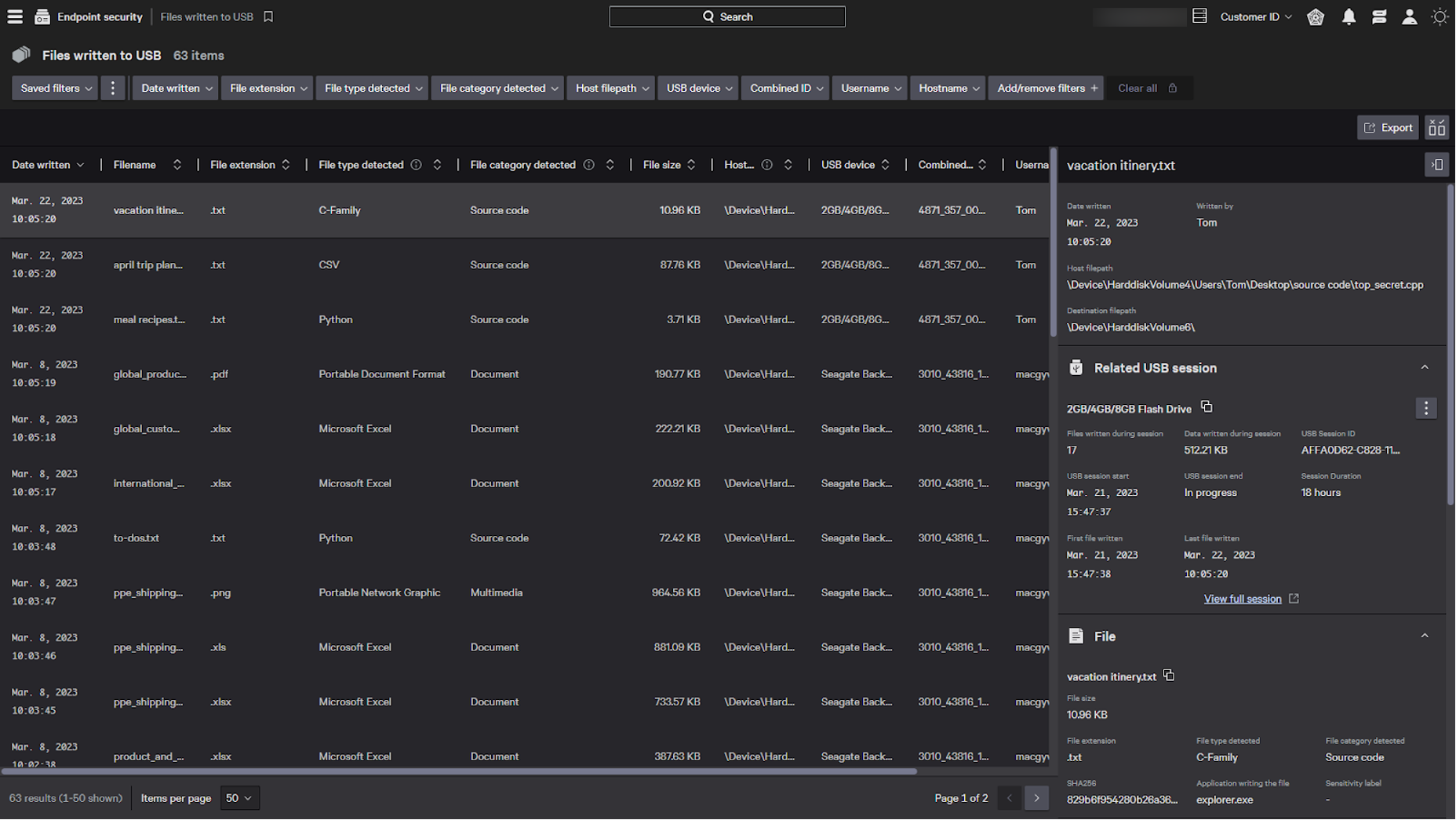
In an effort to avoid detection, Tom has obfuscated key files by renaming them to appear as personal files using names such as “April trip plans,” “vacation itinerary” and “meal recipes.” Tom is attempting to hide sensitive data — right before the final step of copying them to an external USB media device.
As Tom attempts to move these files to the USB drive, Falcon Device Control uses on-sensor machine learning to identify source code in the renamed files in real time. The Falcon agent is also able to extract key provenance metadata and unique details about documents, including sensitivity labels. As the data is copied to external media, the Falcon console immediately allows reviewing the activity in context and provides a unique view of what the files truly contain.
From the console, a security analyst will see information about the data exfiltration Tom has initiated. In the “Files Written to USB” dashboard, the analyst can see in one of the files Tom has moved, the file extension of .txt differs from the Python source code identified within the file. Looking at the host file path, the analyst can see Tom moved the file from a folder called “source_code” to his USB, further increasing suspicion that Tom is attempting to exfiltrate company data.
Conclusion
Data loss risk has proven to be a continued liability for organizations, driving the need for analysts to be able to control their organization’s USB device risk exposure. Falcon Device Control enables safer utilization of USB devices across your estate. Built on CrowdStrike’s cloud-native Falcon platform, Falcon Device Control uniquely combines visibility and granular control so analysts can ensure only approved devices are used in your environment and they have deep visibility into data going onto those devices. When used with CrowdStrike Falcon® Insight XDR, visibility is extended, adding searchable history and logs of USB device usage, including file metadata and source code written to devices.
Additional Resources
- Learn more about how Falcon Device Control provides the needed visibility and granular control to limit risks associated with USB devices.
- Learn how the powerful CrowdStrike Falcon platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon Prevent and see for yourself how true next-gen AV performs against today’s most sophisticated threats.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)