The fastest adversary can “break out” — or move laterally — in only seven minutes after compromising an endpoint. Yes, you heard that right. Seven minutes.
In the relentless race against adversaries, every second counts. To avoid breaches, you need to detect and stop adversaries before they can break out and expand their realm of control. This requires analyzing your key security data, including CrowdStrike Falcon® platform data and proxy logs, as soon as an intrusion occurs.
Unfortunately, relying on a traditional SIEM to find fast-moving threats might not work. During the time it takes adversaries to break out from a compromised endpoint, legacy SIEMs might still be ingesting, parsing, enriching and indexing logs. If your SIEM can’t quickly collect and process data, your SecOps team will struggle to stop advanced threats before damage is done.
In this post, we’ll discuss why your team needs proxy logs for incident response and how shifting proxy logs from a slow, expensive legacy SIEM to CrowdStrike Falcon® LogScale can help you find adversaries faster, while lowering your total cost of ownership.
Stop Threats with Proxy Logs
From malware-laden, drive-by download sites to phishing domains and cross-site scripting attacks, web-based threats continue to plague end users. The ubiquity of web traffic also provides the perfect cover for adversaries to conduct command-and-control communications and steal data while staying under the radar.
For your SecOps team, proxy logs offer a treasure trove of data to uncover all of this malicious activity. Logs from proxies, also known as secure web gateways (SWGs), as well as logs from firewall URL filtering subscriptions provide rich context for investigations. With information such as usernames, URLs, file names, URL categories, browser agents and more, skilled hunters can discover unusual behavior. Proxy logs also reveal whether web requests were blocked and can track threats such as known vulnerability exploits, malware, spyware and network scans.
By collecting and storing proxy logs, you can:
- Identify compromised endpoints and credentials by investigating access to unknown domains and phishing sites
- Hunt for threats by analyzing tunneled traffic
- Review access to suspicious files, such as Java, Visual Basic Script or Batch files and unusual browser agents
- Search web access logs for indicators of compromise (IOCs) such as malicious IP addresses, URLs and domains
- Hunt for data exfiltration by analyzing large file uploads to suspicious sites
- Identify rogue devices and servers initiating connections to external sites
- Monitor web application access to maximize employee productivity
- Meet compliance requirements by storing web access logs for years
Proxy logs provide tremendous value to your threat hunters and analysts, but they can slow down SIEM performance, cause ingestion bottlenecks and increase costs. Designed over a decade ago, before log volumes skyrocketed, traditional SIEM solutions can’t keep pace with today’s scalability and performance requirements.
If you manage an enterprise SOC, you might be forced to make tough tradeoffs between what security data to log, how long to retain it, and cost. And unfortunately, proxy logs might not make the cut, creating dangerous visibility blind spots for your SecOps team.
Shift from a High-Cost Legacy SIEM to High-Speed Falcon LogScale
If you want to increase your logging capacity and supercharge search performance, but you’re not ready to replace your SIEM, you can gradually move data from your existing SIEM to Falcon LogScale. Falcon LogScale is a next-gen SIEM that elevates security operations by detecting threats with sub-second latency, accelerating investigations with blazing-fast search and collecting data at petabyte scale so you can log everything to answer anything in real time.
While many CrowdStrike customers start their journey to Falcon LogScale with Falcon platform data, you can easily extend the retention of your endpoint, cloud and identity data using proxy logs. You can then assess other types of data stored in your SIEM and identify the high-volume data bogging down SIEM performance and migrate it to Falcon LogScale. As you migrate data, you’ll not only reduce the load on your SIEM, you can also cut SIEM costs and improve search speed so you can find and stop adversaries faster.
Get Started Quickly with New LogScale Marketplace Packages
Falcon LogScale streamlines the collection and processing of logs from proxies and other third-party tools with out-of-the-box packages available in the Falcon LogScale Marketplace. You can easily install packages for Zscaler, Blue Coat and dozens of other sources and get insights from your data faster.
Falcon LogScale Marketplace packages for proxy logs provide:
- Parsers that map incoming data into Falcon LogScale fields. Parsers normalize the data to a subset of this schema based on OpenTelemetry standards for analysis and correlation while still preserving the original data.
- Live and historical dashboards that visualize threats, web traffic, access controls and more
- Saved queries to show top URLs, users, threats and events
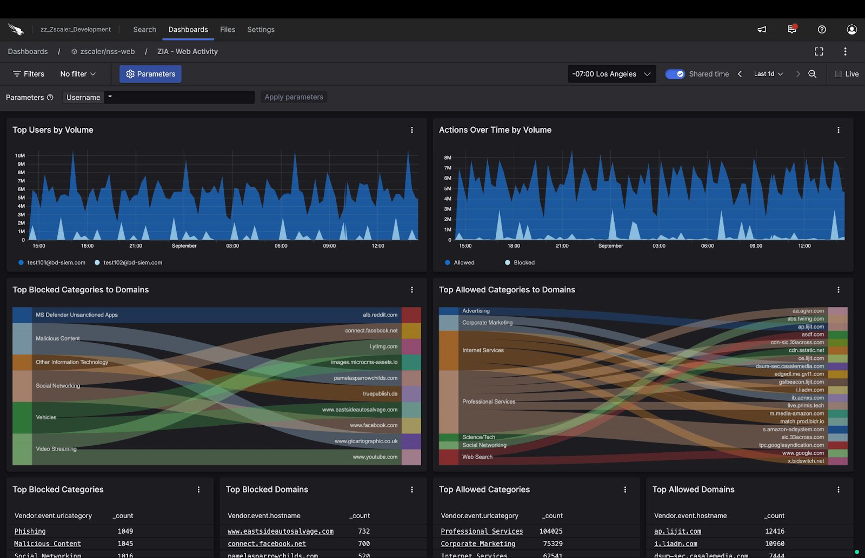 Prebuilt dashboards reveal top blocked internet/SaaS app traffic categories by domain and top users by volume, as shown in this Zscaler Internet Access (ZIA) Activity dashboard (click to enlarge)
Prebuilt dashboards reveal top blocked internet/SaaS app traffic categories by domain and top users by volume, as shown in this Zscaler Internet Access (ZIA) Activity dashboard (click to enlarge)
Join leading organizations by augmenting or replacing your SIEM with Falcon LogScale for unbeatable scalability and performance. With its unique index-free architecture and advanced compression technology, Falcon LogScale empowers you to stop breaches by delivering high-speed search and sub-second latency for live dashboards and real-time alerting.
With Falcon LogScale, you can cut costs by up to 80% compared to legacy SIEMs. Its vast scale and affordable price let you avoid making tough tradeoffs between cost, how much data you can collect and how long you can store it. With Falcon LogScale, you can retain petabytes of data for years.
To find out if Falcon LogScale can help you fulfill your SIEM and logging requirements, contact a CrowdStrike expert today.
Additional Resources
- Check out our Unstoppable Innovations CrowdCast series to learn more about how you can rise above the adversaries and shut down breaches.
- Download the CrowdStrike eBook, 8 Things Your Next SIEM Must Do, to understand the critical capabilities to look for when evaluating SIEM solutions.
- See Falcon LogScale in action by watching a fast-paced demo.
- Sharpen your threat hunting skills with Falcon LogScale by attending a hands-on lab.
- Learn more about today’s adversaries and how to combat them at Fal.Con 2023, the can’t-miss cybersecurity experience of the year. Register now and meet us in Las Vegas, Sept. 18-21!
- Find out how to log everything to answer anything in real time by visiting the Falcon LogScale product page.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































