This blog was originally published on March 13, 2018. On March Patch Tuesday, Microsoft released a patch for CVE-2018-0886, a vulnerability discovered by Preempt (now CrowdStrike) researchers. The vulnerability consists of a logical flaw in Credential Security Support Provider protocol (CredSSP), which is used by RDP (Remote Desktop Protocol) and Windows Remote Management (WinRM) and that takes care of securely forwarding credentials to target servers. The vulnerability can be exploited by attackers by employing a man-in-the-middle attack to achieve the ability to run code remotely on previously not infected machines in the attacked network. The vulnerability, in many real-world scenarios where the victim network has vulnerable network equipment, could result in an attacker gaining the ability to move laterally in the victim’s network and even infect domain controllers with malicious software. No attacks have been detected in the wild by Preempt at the time of this original publication. The vulnerability is a logical one and affects all Windows versions to date. In terms of the
vastness of this issue, we can note that RDP is the most popular application to perform remote logins as of the time of original publication. To further highlight this, in internal research we found that almost all enterprise customers are using RDP, making them vulnerable to this issue.
How Does the Attack Work?
An attacker can exploit this vulnerability in conjunction with a man-in-the-middle attack. The attacker will set up the man-in-the-middle, wait for a CredSSP session to occur and, once it does, will steal session authentication and perform a remote procedure call (DCE/RPC) attack on the server that the user originally connected to (e.g., the server user connected with RDP). An attacker which has stolen a session from a user with sufficient privileges could run different commands with local admin privileges. This is especially critical in case of domain controllers, where most remote procedure calls (DCE/RPC) are enabled by default. 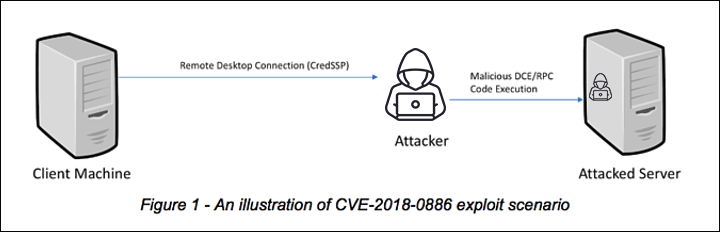 This attack could be mounted in many real world scenarios. To list a few:
This attack could be mounted in many real world scenarios. To list a few:
- An attacker with WiFi/Physical access: If an attacker has some physical access to your network, then he could easily launch a man-in-the-middle attack. If you also have WiFi deployed in areas of your network, you might be vulnerable to key reinstallation attacks (KRACK), thus making all machines that do RDP via WiFI exposed to this new attack.
- Address resolution protocol (ARP) poisoning: Despite being an old attack technique, many networks are still not 100% protected from ARP poisoning. If this is the case in your network, this new vulnerability means an attacker with control of one machine could easily move laterally and infect all machines in the same network segment.
- Attacking sensitive servers (including domain controllers): Sometimes, an attacker has control of several workstations in an organization and needs to find a way to infect sensitive business-critical servers (which might require higher privileges). If the network has some vulnerable routers/switches (e.g., CVE-2018-0101 that allows remote code execution on some Cisco routers), it might be relatively easy to infect your critical servers. An attacker will simply infect the router/switch near the server and wait for an IT admin to log-on to the server using RDP.
Microsoft response Center (MSRC) response and timeline
Microsoft acknowledged the issue, a CVE has been issued (CVE-2018-0886) and a fix has been released. Timeline:
- 20/08/2017: Initial disclosure to MSRC
- 30/08/2017: MS repro attack and acknowledge issue
- 18/09/2017: Microsoft requested an extension on 90 days SLA
- 12/03/2018: Microsoft fixes CVE-2018-0886 as part of March patch Tuesday.
How can I protect myself from these vulnerabilities?
Here are the main steps you need to take to make sure you are protected from this recent threat:
- CrowdStrike Zero Trust (formerly Preempt Platform) customers have been protected from this flaw by providing in-depth defense with both alerting and real-time prevention when vulnerabilities, such as the CredSSP flaw, are exploited in the network.
- Make sure that your workstations and servers are properly patched. This is a basic requirement. However, it is important to note that patching alone is not enough as you will also need to make a configuration change to apply the patch and be protected. For further details on how to apply the patch refer to this Microsoft advisory.
- As with many previous exploits, blocking the relevant application ports/services (RDP, DCE/RPC) would also thwart the attack. It is recommended to apply the proper network segmentation policy and block unnecessary ports/services.
- As many other credential-based attack techniques (NTLM relay, pass-the-hash), the ability to carry out the attack relies on privileged users using their credentials to perform IT operations. In order to better protect your network, you should reduce privileged account usage as much as possible and use non-privileged accounts whenever applicable. If you’re an experienced IT admin, you probably already know that this could potentially be a difficult task to accomplish. To make the task of removing privileged account usage feasible, you should first make sure you first have the tools to know when and where your privileged accounts are being used.
- For CrowdStrike Zero Trust customers, it is recommended they follow the above steps. We added a hot-fix to detect attacks being exploited against domain controllers (which could alert cases of prevent domain compromise).
Additional Resources
- Learn more by reading a white paper, “Disrupting the Cyber Kill Chain: How to Contain Use of Tools and Protocols.”
- Request a demo of CrowdStrike Falcon® Zero Trust or Falcon Identity Threat Detection products.
- Visit the
CrowdStrike Falcon® Identity Protection solutions webpage. - Read expert insights and analysis on other complex threats — download the CrowdStrike 2020 Global Threat Report.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)




















































