Every day, in a high-stakes race against the clock, protectors must hunt down and stop threats before damage is done. As adversaries work faster and smarter, protectors must operate with greater agility.
But legacy SIEMs are holding them back. Designed decades ago when log volumes and adversary speed were a fraction of what they are today, legacy SIEMs hinder investigations with agonizingly slow search speeds. Their poor scalability and high costs keep teams from collecting and retaining all of the data needed to detect attacks, increasing the risk of a breach.
Here, we take a closer look at the issues impeding legacy SIEMs and how the next generation of SIEM technology addresses them.
Legacy SIEM: Outdated Architectures
Many legacy SIEMs rely on conventional database features such as indexes. While indexes work well when query frequency is high and database updates are relatively low, logging systems constantly need to write new log messages to disk — to the tune of terabytes or even petabytes of data a day. Those log messages include many fields or keys that analysts might want to query, increasing the amount of data to be indexed.
With many of these legacy deployments still on-premises, there is a constant need to add servers to keep up with storage, rapidly driving costs due to the hardware and people required to maintain it.
The costs are not only monetary. Updating indexes requires CPU cycles, disk space and — most importantly — time. In threat hunting and detection, every second counts. With the fastest observed eCrime breakout time clocking in at a mere 2 minutes and 7 seconds in 2023, the added latency imposed by indexing could mean the difference between stopping an attack early and recovering from a devastating breach.
“With our previous SIEM, SOC analysts would initiate queries on Friday and come back on Monday for results. Sometimes, their queries timed out altogether. Not to mention logs getting stuck in the ingestion pipeline, failing to make their way into the SIEM. It was a nightmare for our SOC analysts.”
— Kevin Nejad, CEO, Vijilan
Next-Gen SIEM: Engineered for Performance
Next-gen SIEM technology relies on a cloud-native, index-free architecture. The power of the cloud makes storage fast, flexible, cost-efficient and convenient. Data is stored in buckets labeled with information to let the search engine know if sought-after data could be in them. Bloom filters and tags help the search engine avoid scanning irrelevant data for matches, reducing the amount of data to be searched by up to 100x or more.
Because they don’t need to continually re-index data, the best next-gen SIEM solutions can generate alerts and update dashboards in less than a second after ingesting data. While legacy SIEMs often have strict limits on the number of live queries, a next-gen SIEM can run thousands of queries in real time. Data is immediately available for searching, helping threat hunters and analysts swiftly find threats. Their index-free design lets them allocate compute resources to searching that would otherwise have been spent updating indexes — helping next-gen SIEMs deliver much faster search performance compared with legacy SIEMs.
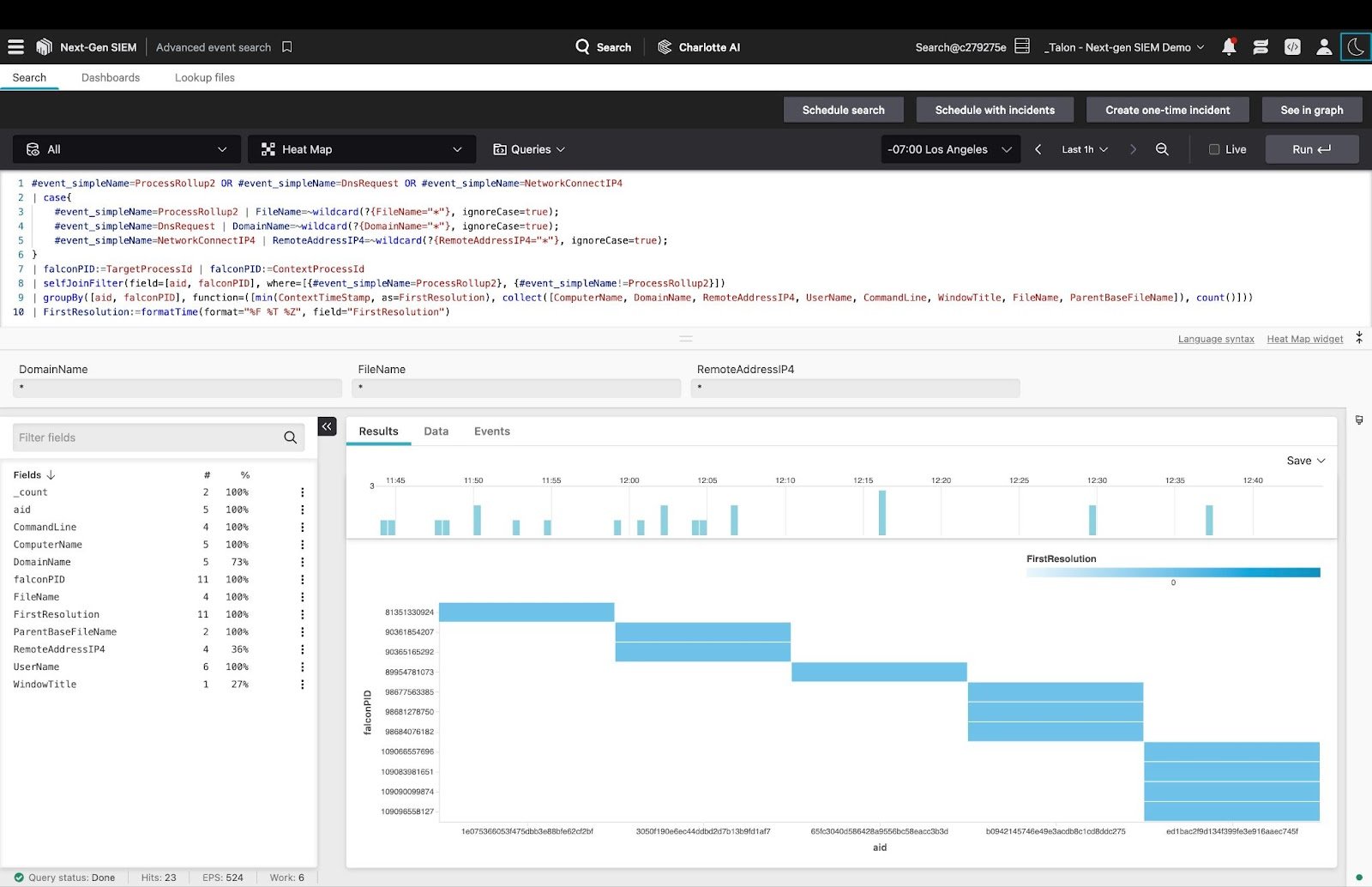
Figure 1. Next-Gen SIEMs can query billions of records per second
Detect Threats Faster with Consolidation
Legacy SIEMs rely on third-party data for detection, investigation and response. However, routing logs from myriad devices and applications to a SIEM inherently delays detection. Additionally, endpoint data can be voluminous, making it cost-prohibitive to send to your SIEM to correlate against other third-party data.
“My previous experience with SIEM was painful to say the least. Logs are generated and piped across the network. If that piping isn’t available, logs queue, they backlog, and now you’re waiting on alerts to trigger from two days ago, which is expensive from an incident response perspective.”
— Larry Wiggins, CISO, Cloudflare
A next-gen SIEM unifies data, security and IT, with AI and workflow automation on a single platform. It brings together native endpoint, identity and cloud security with third-party data for full visibility and protection. This consolidation helps accelerate investigations and drives faster detection because analysts no longer need to pivot between consoles and manually piece together data. There’s no need to forward and periodically retrieve EDR, cloud workload or identity protection logs, and no worries about network latency or backlogs — key data is already in the platform and available for correlation, reducing the mean time to detect.
A High-Speed, Efficient Platform to Power the AI-Native SOC
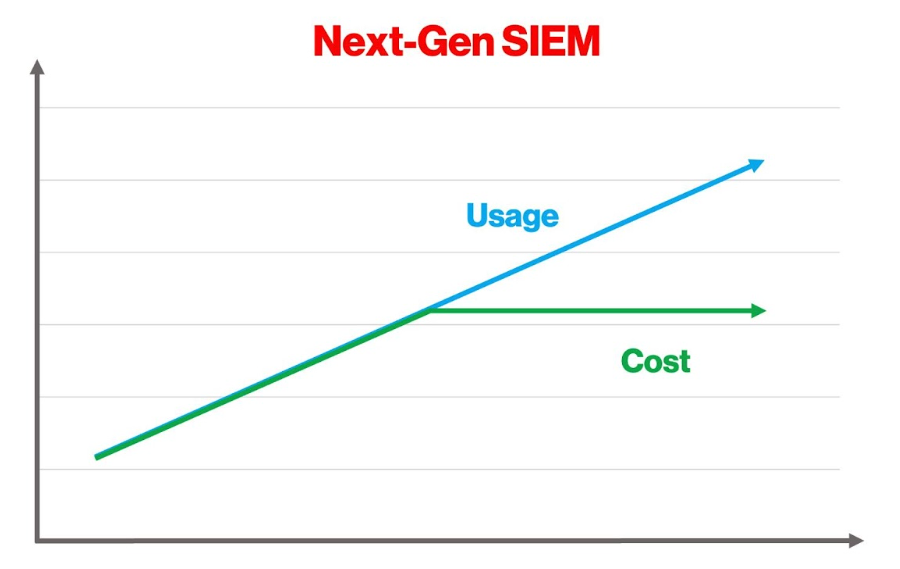
In a world of increasing log volumes and log sources, the next generation of SIEM technology must deliver exceptional performance and prevent runaway costs.
For many organizations, log volumes are growing faster than security budgets. The cost of hosting SIEM infrastructure can skyrocket as log volumes grow. As SIEM vendors pivot to the cloud, they are forced to shoulder these soaring infrastructure costs.
As a result, some SIEM vendors are blindsiding customers with high renewal fees, pricey deployment services and exorbitant charges for certain third-party data. Others are adopting consumption-based pricing models that effectively penalize customers for using their SIEM, or they’re pivoting to a multi-data platform model, shifting these costs to data lake providers.
Next-gen SIEMs’ cloud-native and index-free architecture avoids the need for traditional indexes. They use bucket storage and compression, which reduces disk size by 5x to 15x, slashing storage costs – and next-gen SIEM vendors can extend these savings to end users.
Next-Gen SIEMs are designed as part of a unified platform that brings together endpoint, identity and cloud security with third-party data. As a result, they eliminate the need to store key data on multiple tools and they avoid unnecessary data import and export costs, further reducing expenses.
Experience the Speed of the AI-native SOC
CrowdStrike Falcon® Next-Gen SIEM, built on an efficient log management foundation, scales to ingest petabytes of data per day while offering up to 80% cost savings compared to legacy SIEMs. With its simple ingest-based pricing, security analysts can execute an unlimited number of workflows, searches or API calls without being penalized.
When CrowdStrike transitioned Falcon platform customers to our proprietary log management technology in the Raptor release, we successfully reduced our infrastructure footprint by over 50% across most use cases, while enhancing search speed for the majority of queries — and we can pass these savings on to customers.
With Falcon Next-Gen SIEM, teams can afford to collect and store all of their security logs for years. This eliminates visibility blind spots as all of that data is available instantly for high-speed search and threat hunting. Security engineers don’t need to hassle with a complex web of data lakes, analytics tools or cold storage, cutting operating costs and reducing response times.
Designed from the ground up around a modern security analyst experience, it brings together adversary-driven detection, workflow automation, AI-led investigations and orchestrated response in one powerful platform, managed through one console. With Falcon Next-Gen SIEM, you can safeguard your organization with industry-leading security from the company that understands adversaries better than anyone.
Additional Resources
- Read the SOC Survival Guide to learn what’s needed to defeat modern adversaries.
- Request a virtual test drive of Falcon Next-Gen SIEM.
- Watch the AI-Native SOC Summit on demand and see the next generation of the SIEM, here today.
- Discover how leading companies such as ExtraHop, Chronosphere and Tausight rely on CrowdStrike’s high-performance log management engine to power their products.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)