Microsoft has released patches for 97 vulnerabilities for its April 2023 Patch Tuesday rollout: 7 are classified as Critical while the remaining 90 are classified as Important. One vulnerability is identified as actively exploited; this zero-day will be discussed in greater detail later in this blog.
April 2023 Risk Analysis
This month’s leading risk type is remote code execution (46.4%, up from 40.3% in March 2023), followed by elevation of privilege (20.6%, down from 31% in March).
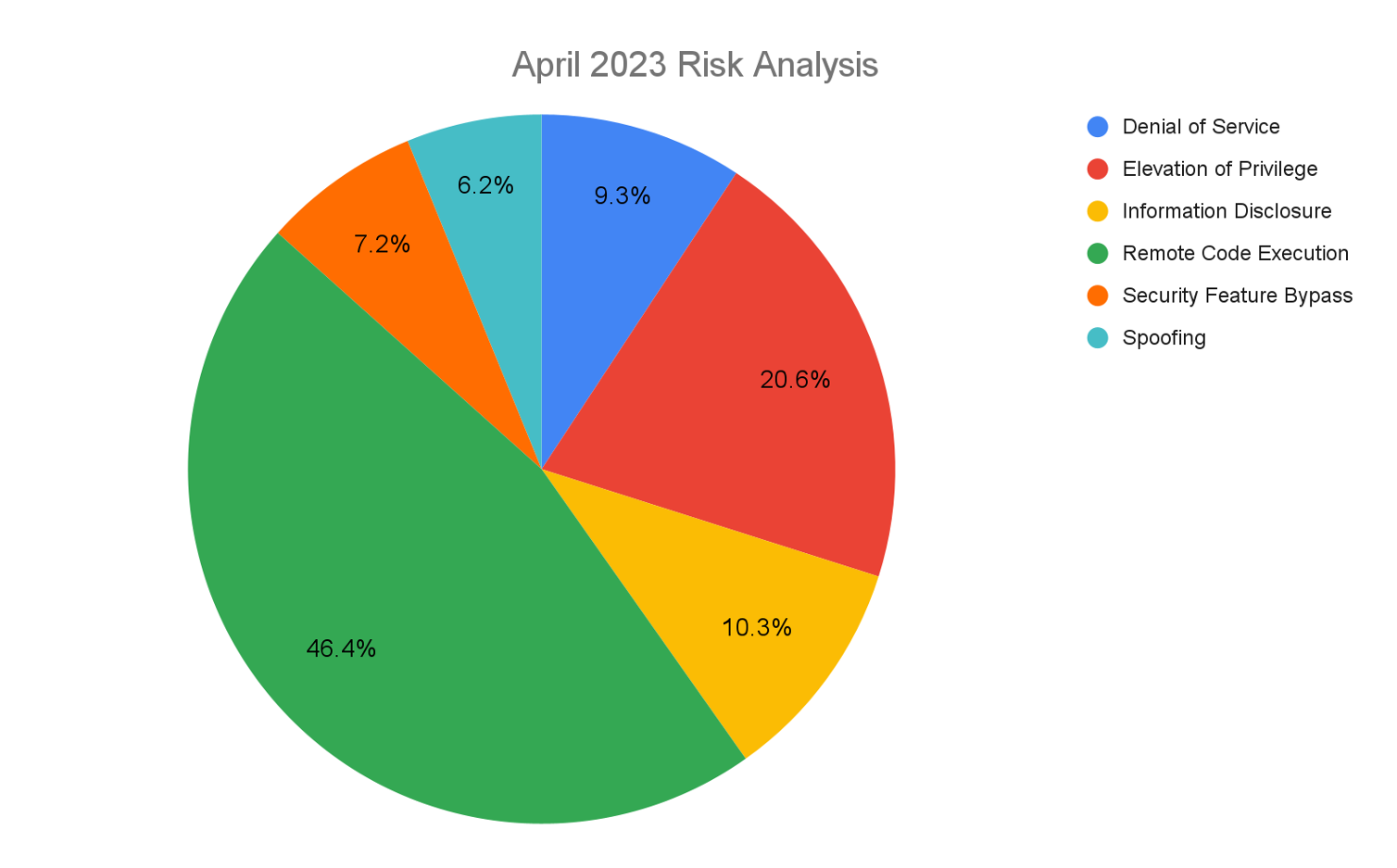 Figure 1. Breakdown of April 2023 Patch Tuesday attack types
Figure 1. Breakdown of April 2023 Patch Tuesday attack typesThe Microsoft Windows product family received the most patches this month with 77, followed by Extended Support Updates (44) and Microsoft Developer Tools (6).
 Figure 2. Breakdown of product families affected by April 2023 Patch Tuesday
Figure 2. Breakdown of product families affected by April 2023 Patch TuesdayActively Exploited Zero-Day Vulnerability in the Common Log File System Driver
Microsoft disclosed one actively exploited vulnerability (CVE-2023-28252) in this month’s release. The successful exploitation of the vulnerability will grant the attacker full SYSTEM privileges, the highest level of privilege on Windows systems. Even though this vulnerability requires an attacker to already have access to the victim computer, SYSTEM privileges are a large enough risk that this vulnerability should be patched as soon as possible. In addition, as this vulnerability is actively exploited, special care should be taken to monitor Windows endpoints for signs of intrusion. A similar vulnerability was reported in the September 2022 Patch Tuesday release.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2023-28252 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
Figure 3. Zero-day vulnerability patched in April 2023
Critical Vulnerabilities in Microsoft Windows Message Queuing System
The Microsoft Message Queuing (MSMQ) system is getting a patch for CVE-2023-21554, a Critical remote code execution (RCE) vulnerability with a CVSS score of 9.8. The MSMQ system allows applications to communicate across a network to systems that may or may not be online. This system is most often used in business-critical applications such as electronic commerce and embedded systems.
Microsoft notes an attacker can exploit this vulnerability by crafting a malicious MSMQ packet and sending it to the MSMQ server, which runs as a network service account. This means an attacker could start up other malicious services and exploit the existing trust relationship between the server and other endpoints in the network. Additional information on the MSMQ system can be found here.
CVE-2023-28250, a Windows Pragmatic General Multicast (PGM) RCE vulnerability, is a Critical vulnerability with a CVSS of 9.8. An attacker can exploit this vulnerability by sending a specially crafted file; if the MSMQ service is enabled, the attacker can trigger malicious code on the endpoint. More information on the NetworkService account and its default permissions can be found here.
| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | CVE-2023-21554 | Microsoft Message Queuing Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2023-28250 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability |
Figure 4. Critical vulnerabilities in Microsoft Message Queuing system
Critical Vulnerabilities Affecting Microsoft Windows Networking Components
CVE-2023-28231, a Critical vulnerability affecting the Dynamic Host Configuration Protocol (DHCP) service, could result in RCE if an authenticated attacker is able to send a specially crafted remote procedure call (RPC) to a DHCP service. This vulnerability requires the attacker to have gained some sort of access to the target network. RPC calls should be actively monitored in order to identify whether or not this vulnerability is being exploited.
CVE-2023-28219 and CVE-2023-28220 are Critical RCE vulnerabilities targeting the Layer 2 or data link layer. This layer of the Open Systems Interconnection model is responsible for the transfer of network packets. This is where protocols such as Ethernet and TCP/IP work. These high-complexity vulnerabilities require the attacker to win a race condition where the attacker attempts to respond to a connection request to a remote access server before the connection request’s originator can respond. Given this race condition, the probability that an attacker is successful is not guaranteed, but provided enough time, an attacker can successfully exploit this vulnerability.
CVE-2023-28232 is a Critical vulnerability targeting the Windows Point-to-Point Tunneling Protocol. This high-complexity vulnerability requires the victim user to connect to a malicious server. Once connected, the attacker can leverage this vulnerability to run code on the victim machine. This sort of vulnerability is most often exploited through the use of phishing.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2023-28231 | DHCP Server Service Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2023-28219 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2023-28220 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 7.5 | CVE-2023-28232 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
Figure 5. Critical vulnerabilities in Windows networking components
Critical Vulnerabilities Affecting Microsoft Raw Image Extension
CVE-2023-28291 is a Critical vulnerability affecting the Raw Image file extension. A raw image file is an image that has not yet been compressed or processed into a more user-friendly format such as JPEG. This vulnerability can be exploited if the victim user opens the malicious file. The affected application is most often updated through the Microsoft Store; however, Microsoft notes the update can be downloaded outside of the store.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.4 | CVE-2023-28291 | Raw Image Extension Remote Code Execution Vulnerability |
Figure 6. Critical vulnerabilities in Raw Image file extension
Significant End-of-Life Date for Microsoft Exchange
End-of-life software is no longer getting security updates and thus should be used with utmost caution and monitoring.
Microsoft Exchange 2013 entered End-of-Life status April 4, 2023. It is recommended to update to Exchange 2019 or newer for the maximum benefit as Exchange 2016 reaches End-of-Life status in October 2025.
Not All Relevant Vulnerabilities Have Patches: Consider Mitigation Strategies
As we have learned with other notable vulnerabilities, such as Log4j, not every highly exploitable vulnerability can be easily patched. As is the case for the ProxyNotShell vulnerabilities, it’s critically important to develop a response plan for how to defend your environments when no patching protocol exists.
Regular review of your patching strategy should still be a part of your program, but you should also look more holistically at your organization's methods for cybersecurity and improve your overall security posture.
The CrowdStrike Falcon® platform regularly collects and analyzes trillions of endpoint events a day from millions of sensors deployed across 176 countries. Watch this demo to see the Falcon platform in action.
Learn More
Learn more about how CrowdStrike Falcon® Spotlight can help you quickly and easily discover and prioritize vulnerabilities here.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- For more information on which products are in Microsoft’s Extended Security Updates program, refer to the vendor guidance here.
- Download the CrowdStrike 2023 Global Threat Report to learn how the threat landscape has shifted in the past year and understand the adversary behavior driving these shifts.
- See how Falcon Spotlight can help you discover and manage vulnerabilities and prioritize patches in your environments
- Learn how CrowdStrike’s external attack surface module, Falcon Surface, can discover unknown, exposed and vulnerable internet-facing assets enabling security teams to stop adversaries in their tracks.
- Learn how Falcon identity protection products can stop workforce identity threats faster.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































