Microsoft has released 121 security patches for its August 2022 Patch Tuesday rollout. Seventeen vulnerabilities are rated Critical in severity and the rest are classified as Important, with one (CVE-2022-34713) under active exploitation. In this blog, the CrowdStrike Falcon® Spotlight™ team analyzes this month’s vulnerabilities, highlights the most severe CVEs and recommends how to prioritize patching.
August 2022 Risk Analysis
For the second month in a row, elevation of privilege continues to be the most commonly used attack type (53%), followed by remote code execution at about 25% and information disclosure at 10%. Elevation of privilege — used as an attack type in one of this month’s two zero-day vulnerabilities, both of which we analyze in detail below — is an easy attack type for even unsophisticated attackers to employ because many organizations often lack adequate security measures and controls. Rigorously enforcing the principle of least privilege, and knowing where the most sensitive company data is stored, is critical for creating a defensive security posture.
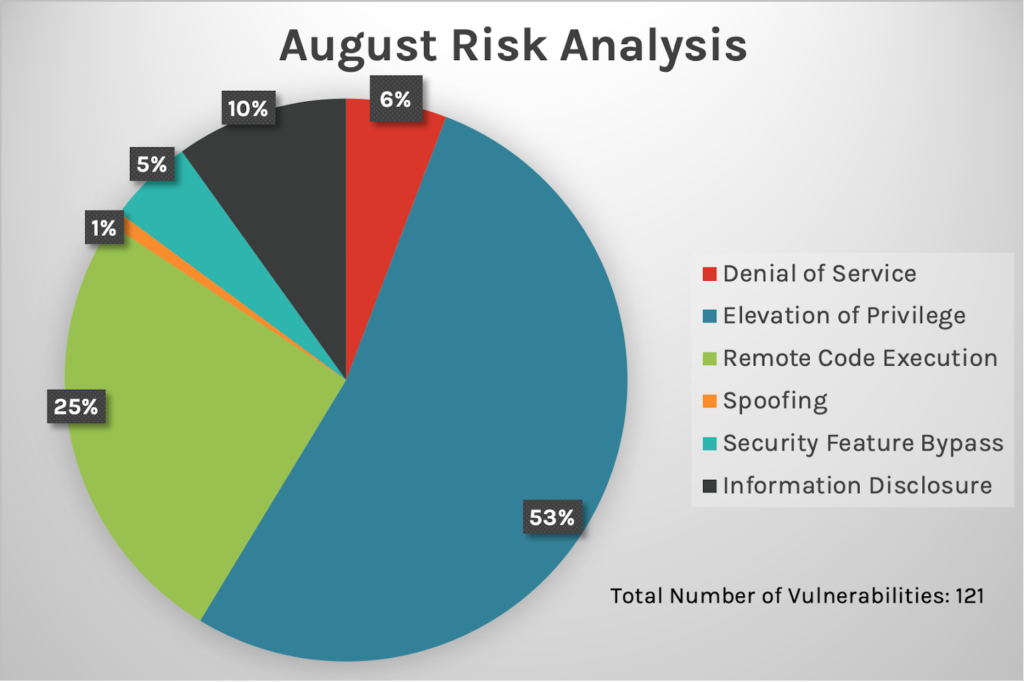 Figure 1. Breakdown of August 2022 Patch Tuesday attack types
Figure 1. Breakdown of August 2022 Patch Tuesday attack typesMicrosoft’s Windows product received the most patches this month including 45 Azure vulnerabilities — 34 of them affecting Azure Site Recovery Service, which also saw many CVEs patched in July 2022. CrowdStrike Falcon® for Azure offers comprehensive visibility into Azure workload events, and virtual machine metadata enables detection, response, proactive threat hunting and investigation to help ensure nothing goes unseen in your cloud environments. This month, there are two zero-day vulnerabilities, one affecting Microsoft Exchange Server and the other impacting Microsoft Windows Support Diagnostic Tool (MSDT).
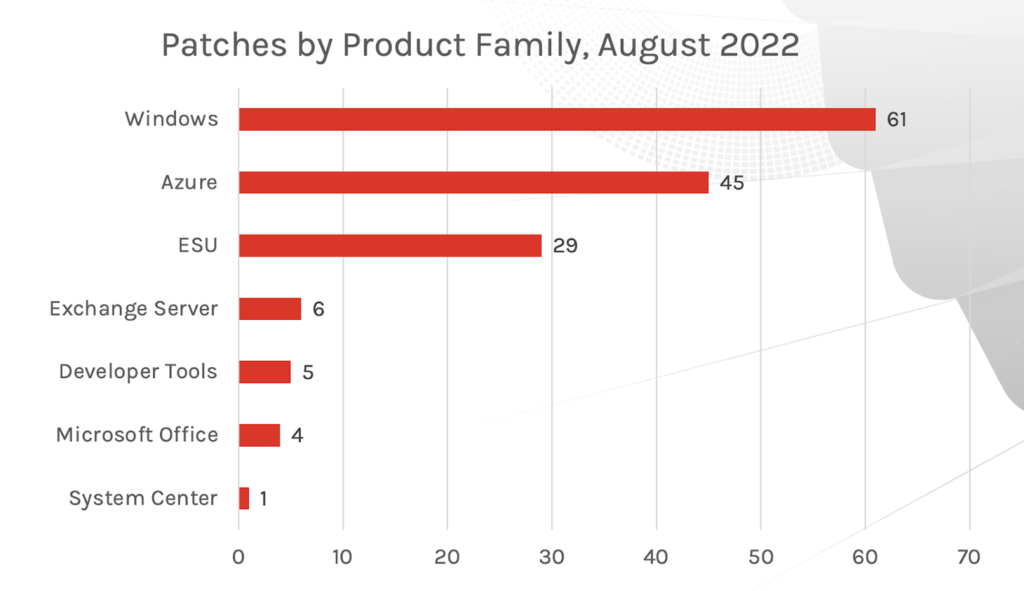 Figure 2. Breakdown of product families affected by August 2022 Patch Tuesday
Figure 2. Breakdown of product families affected by August 2022 Patch TuesdayTwo Zero-Day Vulnerabilities Affect Microsoft Exchange Server and Microsoft Windows Support Diagnostic Tool (MSDT)
An actively exploited Microsoft Windows Support Diagnostic Tool (MSDT) remote code execution vulnerability known as “DogWalk” (CVE-2022-34713) now has an update. This CVE was first discovered in January 2020, however Microsoft did not classify it as a vulnerability at the time. However, when security researchers reported the zero-day remote code execution vulnerability called “Follina” (CVE-2022-30190) on May 27, 2022, it reignited the push to classify and fix the DogWalk vulnerability. As shown in Figure 3, this CVE is ranked as Important.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2022-34713 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability |
| Important | 7.6 | CVE-2022-30134 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
Figure 3. Zero-day bugs patched this month
The second zero-day vulnerability, CVE-2022-30134, targets Microsoft Exchange Server. This CVE utilizes the information disclosure attack type, which allows an attacker to read targeted email messages. Figure 4 lists three Critical vulnerabilities affecting Microsoft Exchange Server that could allow an authenticated attacker to take over the mailboxes of all Exchange users. If utilized, an attacker could read and send emails or download attachments from any mailbox on Microsoft Exchange Server. In addition to patching, administrators will also need to enable Extended Protection to fully address these vulnerabilities.
| Rank | CVSS Score | CVE | Description |
| Critical | 8 | CVE-2022-21980 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| Critical | 8 | CVE-2022-24477 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| Critical | 8 | CVE-2022-24516 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
Figure 4. Critical vulnerabilities affecting Microsoft Exchange Server
Critical Vulnerabilities in Windows PPP, SSTP and SMB
Two Critical Windows Point-to-Point Protocol (PPP) remote code execution vulnerabilities — both with a 9.8 CVSS score — and six Critical Windows Secure Socket Tunneling Protocol (SSTP) remote code execution vulnerabilities received patches this month. As you may know, these older protocols should be blocked at the perimeter and only be used if you absolutely need them. CVE-2022-35804, an SMB Client and Server remote code execution vulnerability, would allow a remote, unauthenticated attacker to execute code with elevated privileges on affected SMB servers. It should be noted that this bug affects Windows 11 only and could potentially be wormable between affected Windows 11 systems with SMB server enabled.
| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | CVE-2022-30133 | Windows Point-to-Point Protocol (PPP) Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2022-35744 | Windows Point-to-Point Protocol (PPP) Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-35804 | SMB Client and Server Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-34702 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-34714 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-35745 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-35766 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-35767 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-35794 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability |
Figure 5. Critical vulnerabilities in Windows PPP, SSTP and SMB
Important Print Spooler and Windows Network File System Vulnerabilities
August 2022 is the fourth month in a row in which Microsoft is offering a patch for a Network File System (NFS) remote code execution vulnerability. CVE-2022-34715, a Windows NFS remote code execution vulnerability, is rated as Important and has been assigned a CVSS of 9.8. To exploit this vulnerability, a remote, unauthenticated attacker would need to make a specially crafted call to an affected NFS server, providing the threat actor with elevated privileges for code execution. While Microsoft lists this as Important in severity, CrowdStrike analysts recommend that this vulnerability be treated as Critical. Falcon Spotlight customers will receive a critical indicator so they can properly prioritize patching.
| Rank | CVSS Score | CVE | Description |
| Important | 9.8 | CVE-2022-34715 | Windows Network File System Remote Code Execution Vulnerability |
| Important | 7.3 | CVE-2022-35755 | Windows Print Spooler Elevation of Privilege Vulnerability |
| Important | 7.3 | CVE-2022-35793 | Windows Print Spooler Elevation of Privilege Vulnerability |
Figure 6. Important Print Spooler and Windows NFS vulnerabilities
CVE-2022-35755 and CVE-2022-35793 are elevation of privilege vulnerabilities located in Windows Print Spooler components, both rated as Important with a CVSS of 7.3. The first CVE can be exploited using a specially crafted input file, while exploitation of CVE-2022-35793 requires a user to click on a specially crafted URL. Both could potentially give the attacker SYSTEM privileges. These vulnerabilities can be mitigated by disabling the Print Spooler service, but CVE-2022-35793 can also be mitigated by disabling inbound remote printing via Group Policy.
Is It Time to Adjust Your Patching Strategy?
When it comes to maintaining your vulnerability management program, security hygiene and attack surface visibility can offer valuable data for informing how you prioritize and patch vulnerabilities within your environment. Adversaries are persistent and consistent, with the time and motivation to look for access in any way possible. Remember, a small amount of access is still access. Patch Tuesday is and will always be important to consider in your patching strategy. If any part of your environment uses Microsoft products, or if other vendors conduct patching cycles, it’s important to review the patches released every month and take time to apply fixes or updates to products wherever applicable.
Learn More
This video on Falcon Spotlight™ vulnerability management shows how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Find out more about today’s adversaries and how to combat them at Fal.Con 2022, the cybersecurity industry’s most anticipated annual event. Register now and meet us in Las Vegas, Sept. 19-21!
- See how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Read how CrowdStrike Asset Graph works in conjunction with Falcon Discover to offer you advanced insights on how suspicious activity is related to other assets within your environment.
- Learn how Falcon Identity Protection products can stop workforce identity threats faster.
- Download the CrowdStrike 2022 Global Threat Report to learn who and what is affecting your environment.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































