It’s the last Patch Tuesday update of 2021, and as with many other updates this year, this month’s list includes important ones — among them a zero-day (CVE-2021-43890 in AppX installer), multiple critical vulnerabilities and a variety of attack types utilized in several Microsoft product families — highlighting once again that patching and prioritization are prominent programs SecOps staff must regularly implement to keep adversaries from infiltrating their organizations’ environments.
New Patches for 67 Vulnerabilities
December 2021’s Patch Tuesday covers fixes for 67 vulnerabilities. The attack-type impact resembles closely the impact we saw in September’s Patch Tuesday update, with remote code execution, privilege elevation and information disclosure dominating the attack types. While the overall quantity of updates offered by Microsoft is higher than last month, the number of updates throughout 2021 have been consistently low. Out-of-band updates have been pushed however, as adversaries continue to consistently take advantage of various weaknesses throughout Microsoft products.
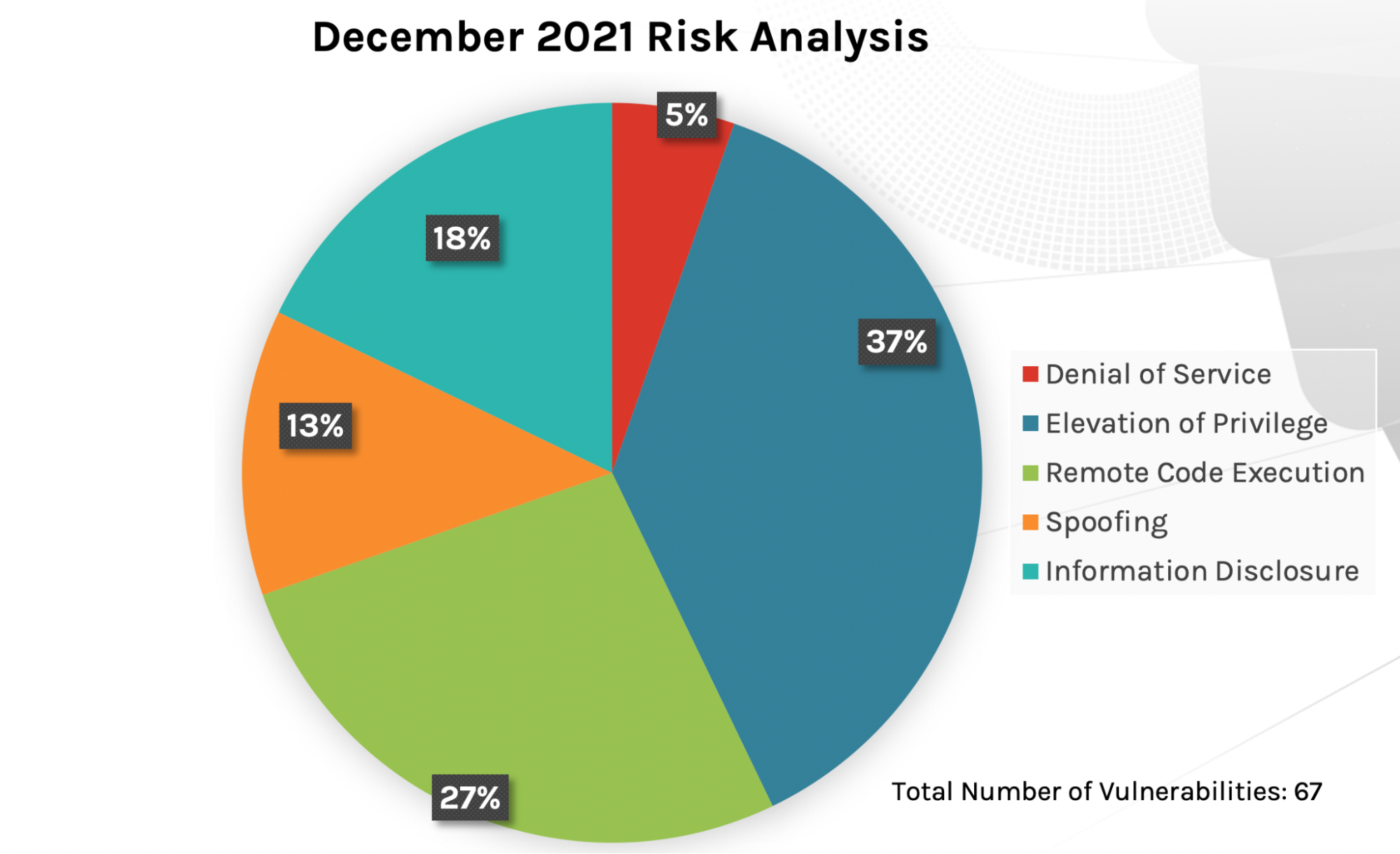 Figure 1. Breakdown of December’s Patch Tuesday attack impact
Figure 1. Breakdown of December’s Patch Tuesday attack impact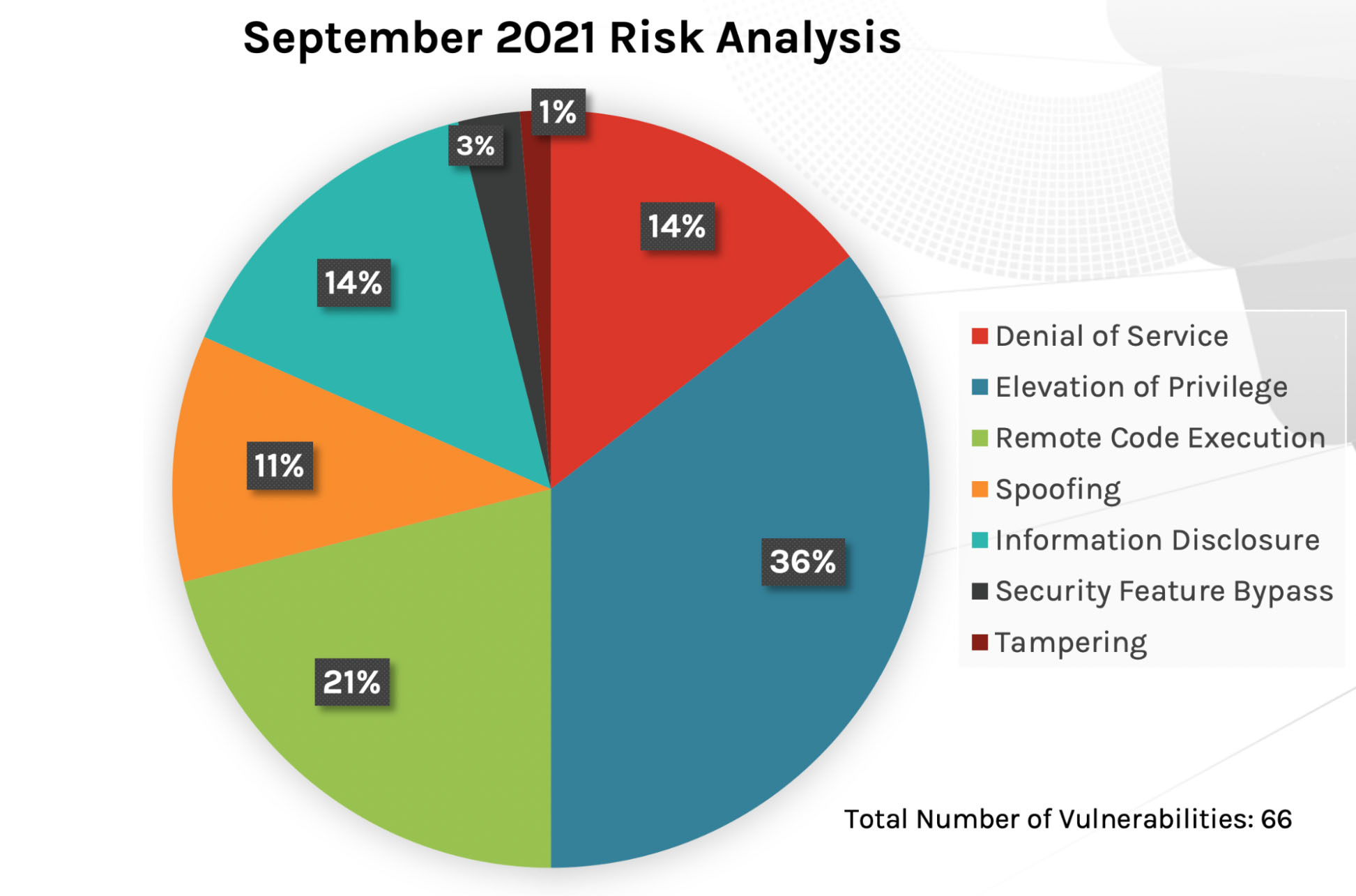 Figure 2. September’s Patch Tuesday Breakdown of Risk Analysis
Figure 2. September’s Patch Tuesday Breakdown of Risk AnalysisWhen examining patches according to product family, we see that Windows and Extended Security Updates (ESU) still have the same amount of focus, receiving most of this month’s updates. The System Center (products including Configuration Manager, Service Manager, Endpoint Protection and Orchestrator, among others) is a product area we see receiving more patches this month compared to last month: 10 updates vs. only one update released in November. Outside of the critical and zero-day vulnerabilities, if your organization uses products within these families, you should consider adjusting your organization’s prioritization schedule to include patches for these products.
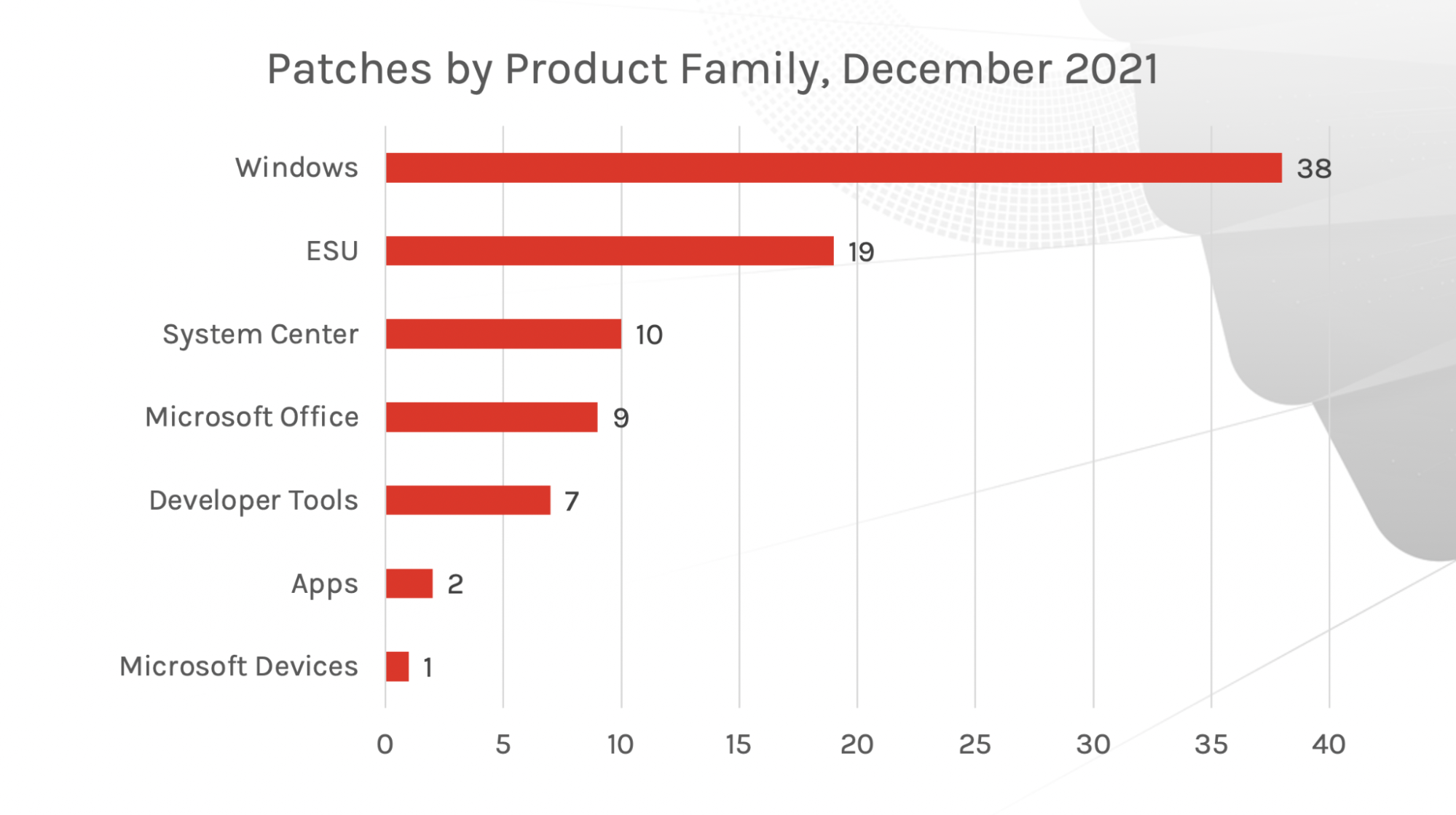 Figure 2. Patches by Product Family
Figure 2. Patches by Product FamilyZero-Day Vulnerability — CVE-2021-43890
Another actively exploited vulnerability, CVE-2021-43890, affects AppX Installer in Microsoft Windows. An attacker is able to exploit this vulnerability through “spoofing” — the crafting of a malicious attachment to be used in a phishing campaign. After convincing a user to open the attachment, the attacker could gain access to the system. Those users with admin rights would be at greater risk than those with few rights.
Microsoft Sharepoint Receives Updates for Multiple Vulnerabilities
This month, four different CVEs affecting Microsoft Sharepoint 2019 have received patches. IT staff seeking to properly update Sharepoint instances will need to apply more than one patch to cover all related vulnerabilities reported this month.
| Rank | CVSS Score | CVE | Description |
| Important | 7.2 | CVE-2021-42294 | Remote Code Execution |
| Important | 8.8 | CVE-2021-42309 | Remote Code Execution |
| Important | 7.6 | CVE-2021-43242 | Spoofing |
| Important | 8 | CVE-2021-42320 | Spoofing |
A Variety of Attack Types Utilized for December’s Critical Vulnerabilities
CVE-2021-41333: A privilege escalation vulnerability which occurs in Windows Print Spooler. This vulnerability adds to an already existing set of vulnerabilities reported starting in July 2021. The PrintNightmare vulnerabilities were among those related to the Print Spooler Service, affecting many organizations, forcing them to disable the service altogether until a fully formed patch was released.
CVE-2021-43215: An Internet Storage Name Service (iSNS) vulnerability found in the iSNS protocol. This protocol manages an iSNS server, providing a registration function to allow all entities in a storage network to register and query the iSNS database. To take advantage of this vulnerability an attacker can send a specially crafted request to iSNS that could result in remote code execution. Microsoft has applied a CVSS score of 9.8 to this vulnerability and labeled it as Critical, having deemed “exploitation most likely” for this vulnerability. CVE-2021-43899: A vulnerability within Microsoft’s 4K Wireless Display Adapter could allow remote code execution. This flaw could allow an unauthenticated attacker to execute their code on an affected device, if the attacker is able to send specially crafted packets on the same network to the device. When patching, IT staff need to install the Microsoft Wireless Display Adapter application from the Microsoft Store onto a system connected to the Microsoft 4K Wireless Display Adapter. From there, staff can access the “Update & Security” section of the app to download the latest firmware for mitigation. CVE-2021-43907: This vulnerability affects the Visual Studio Code in the Windows Subsystem for Linux (WSL). A WSL extension in Visual Code lets a user run a Linux environment, command-line tools and applications directly on Windows, without the overhead of a traditional virtual machine or dual boot setup. An attacker is able to exploit this vulnerability with no privileges required and could carry out remote code execution on the WSL extension.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2021-41333 | Windows Print Spooler Elevation of Privilege Vulnerability |
| Important | 7.1 | CVE-2021-43890 | Windows AppX Installer Spoofing Vulnerability |
| Critical | 9.8 | CVE-2021-43215 | iSNS Server Memory Corruption Vulnerability Can Lead to Remote Code Execution |
| Critical | 9.8 | CVE-2021-43899 | Microsoft 4K Wireless Display Adapter Remote Code Execution Vulnerability. |
| Critical | 9.8 | CVE-2021-43907 | Visual Studio Code WSL Extension Remote Code Execution Vulnerability |
| Critical | 9.6 | CVE-2021-43905 | Microsoft Office app Remote Code Execution Vulnerability |
Another Critical Vulnerability to Consider
CVE-2021-43233: This is a lower-scored vulnerability — with a CVSS score of 7.5 — but one to consider including in your organization’s patching schedule this month. This vulnerability enables attackers to access Windows Remote Desktop Client (RDP) via remote code execution. RDP Protocol is a common vector for adversaries. Microsoft has flagged this vulnerability as Critical. CrowdStike encourages IT staff to mitigate this vulnerability before attackers start to leverage this flaw.
Additionally, Microsoft has provided 10 patches for Microsoft Defender for IOT this month. Of these 10 patches, one is labeled as Critical, with the other nine classified as Important. Adversaries utilize remote code execution and privilege escalation to gain access to these vulnerabilities. Consider these vulnerabilities and determine where they fall within your organization’s prioritization schedule.
Patching and Speedy Mitigation is Still Vital
Identifying, patching and mitigating critical vulnerabilities, along with performing regular maintenance on these programs, is critically important for organizations to keep a secure posture. Gaining robust visibility into all the vulnerabilities that can affect an organization’s environments can be daunting — unless you have the right tools. With Falcon Spotlight, IT staff gain not only required visibility, but also tools to more efficiently see flaws within their systems. With features like an ever-adapting machine learning model to identify the constant changes to vulnerability information, staff can more accurately prioritize those vulnerabilities that will specifically affect their systems.
Learn More
Watch this video on Falcon Spotlight vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- For the latest information on all CVEs related to the Log4Shell vulnerabilities (CVE-2021-44228, CVE-2021-45046 and CVE-2021-4104), please see our Support Portal.
- Learn more on how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- See how Falcon Complete stops Microsoft exchange server zero-day exploits.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Read last month’s Patch Tuesday for more information on critical vulnerabilities your organization should prioritize.
- Learn about the recent PrintNightmare and CrowdStrike’s custom dashboard.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































