Microsoft has released 49 security patches for its December 2022 Patch Tuesday rollout. Of these, 10 vulnerabilities are rated Critical, two are rated Medium and the rest are rated Important. DirectX Graphics Kernel Elevation of Privilege Vulnerability (CVE-2022-44710) is listed as publicly known while Windows SmartScreen Security Feature Bypass Vulnerability (CVE-2022-44698) is listed as actively exploited at the time of release.
CVE-2022-44698 has a 5.4 CVSS. For this bug, a file could be created to circumvent the Mark of the Web detection and therefore bypass security features such as Protected View in Microsoft Office. Considering how many phishing attacks rely on end users working with attachments, these protections are essential to preventing malware and other attacks.
December 2022 Risk Analysis
This month’s leading risk type is remote code execution at 47%, almost double compared with the November Patch Tuesday release, followed by elevation of privilege at 33% (compared to 40% the previous month). The remaining categories make up 6% or less.
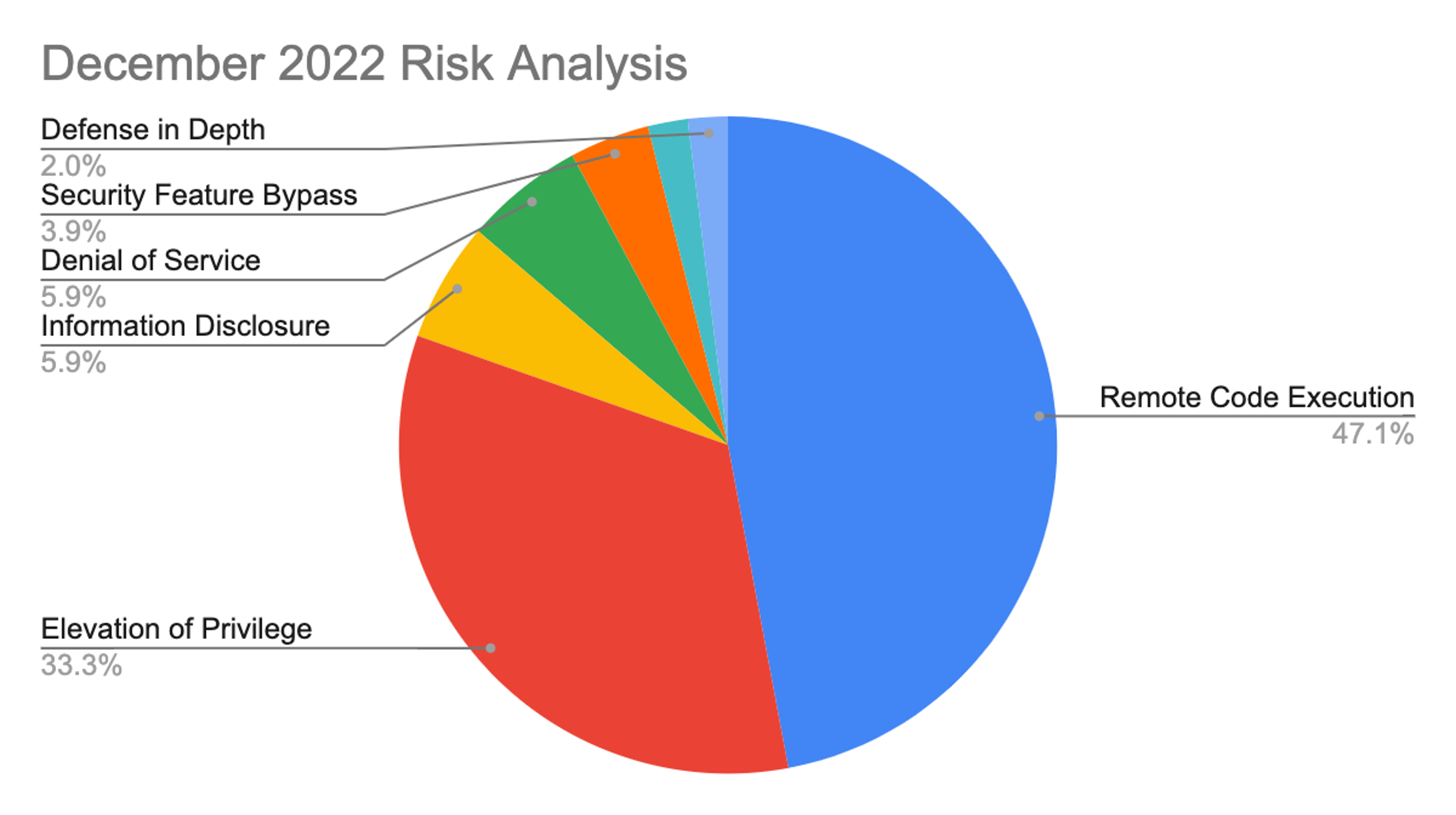 Figure 1. Breakdown of December 2022 Patch Tuesday attack types
Figure 1. Breakdown of December 2022 Patch Tuesday attack typesThe Microsoft Windows product family received the most patches this month (29), followed by Extended Support Updates (16) and Microsoft Office products (14).
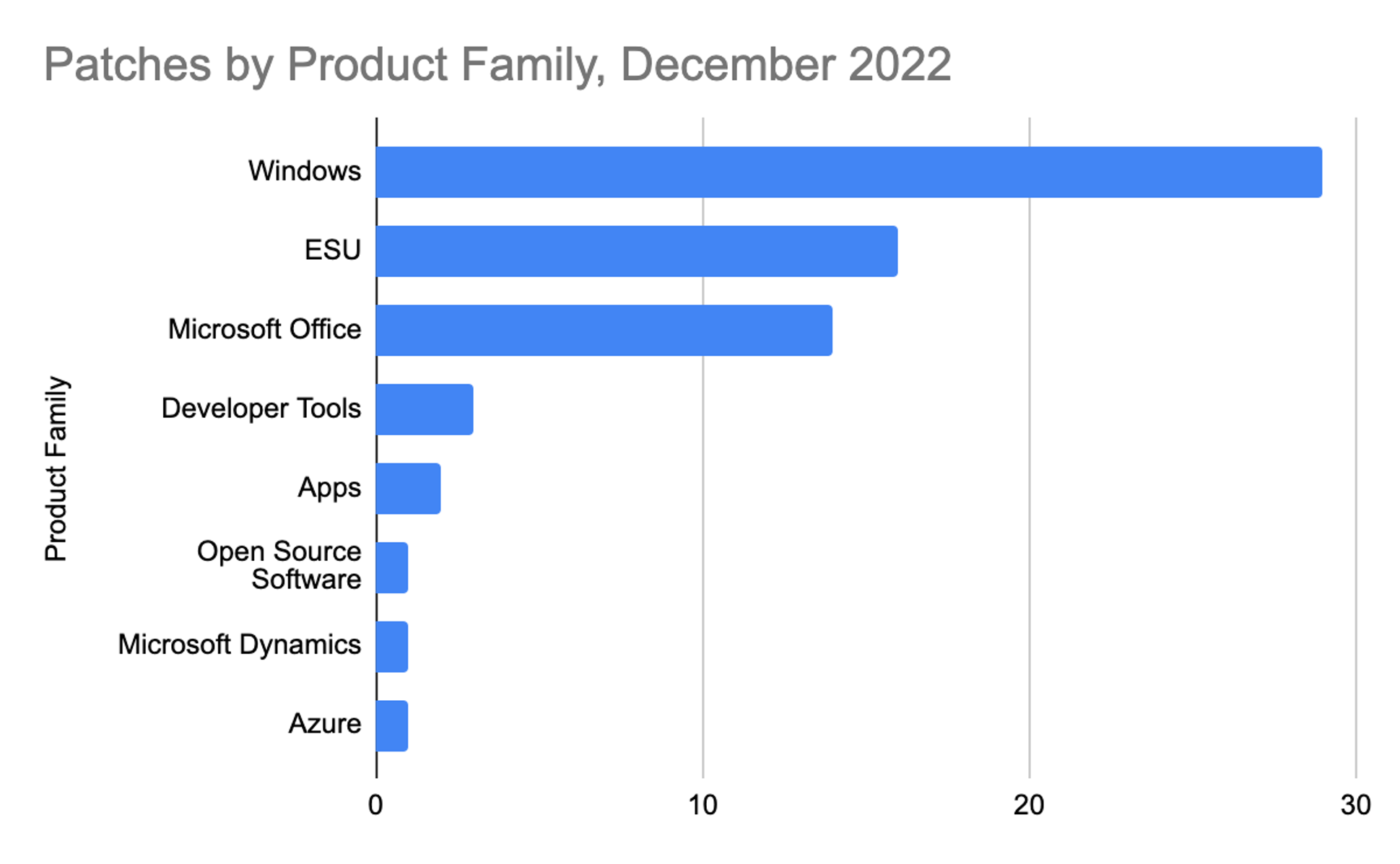 Figure 2. Breakdown of product families affected by December 2022 Patch Tuesday
Figure 2. Breakdown of product families affected by December 2022 Patch TuesdayThis month, threat actors continued to exploit the vast attack surface that is Windows Print Spooler, now affected by two new bugs. We’ve seen plenty of new patches since PrintNightmare — perhaps we will continue to see new print spooler vulnerabilities in 2023. CVE-2022-44678 and CVE-2022-44681, which have a CVSS of 7.8 and a rating of Important, are being addressed this month. In both cases, the attack vector is Local and user interaction is not required.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2022-44678 | Windows Print Spooler Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2022-44681 | Windows Print Spooler Elevation of Privilege Vulnerability |
Figure 3. Print Spooler vulnerabilities patched in December 2022
See for yourself how the industry-leading CrowdStrike Falcon platform protects against modern threats. Start your 15-day free trial today.
Critical Bugs Affect SSTP, PowerShell and SharePoint Server
For this month's release, the Critical vulnerability affecting PowerShell stands out. A PowerShell remote code execution vulnerability (CVE-2022-41076) could allow an authenticated user to escape the PowerShell remoting session configuration and run unapproved commands on the targeted system. This could allow threat actors using tools already on a system to maintain access and move laterally throughout the network.
Next we have two SharePoint server Critical vulnerabilities (CVE-2022-44690 and CVE-2022-44693) both with a CVSS of 8.8 — the highest for this month. In a network-based attack, an authenticated attacker with Manage Lists permissions could execute code remotely on the SharePoint server, gaining the capability to create and delete lists, add or remove columns in a list, and add or remove public views of a list. The attacker must be authenticated to the target site, with the permission to use Manage Lists within SharePoint.
listed in Figure 4, there are also two Critical vulnerabilities affecting Secure Socket Tunneling Protocol (SSTP). CVE-2022-44670 and CVE-2022-44676 could allow a remote, unauthenticated attacker to execute code on an affected system by sending a specially crafted connection request to a server with the RAS Server role enabled. If you aren’t using this service, consider disabling it, and if you are using it, we suggest applying the patches promptly.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2022-44690 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-44693 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| Critical | 8.5 | CVE-2022-41076 | PowerShell Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-44670 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-44676 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability |
Figure 4. Critical vulnerabilities in SSTP, PowerShell and SharePoint Server, December 2022
Other Important Vulnerabilities to Consider
Email client vulnerabilities are not commonly highlighted or considered Critical but CVE-2022-44713, a Microsoft Outlook for Mac spoofing vulnerability, warrants special attention. This bug could enable an attacker to appear as a trusted user when they should not be. This could cause a user to mistakenly trust a signed email message as if it came from a legitimate user. Next on our list is CVE-2022-44704, a Microsoft Windows Sysmon elevation of privilege vulnerability, which could allow a locally authenticated attacker to manipulate information on the Sysinternals services to achieve elevation from local user to SYSTEM admin.
Two Windows kernel bugs are also getting addressed this month. The first, CVE-2022-44683 with a CVSS of 7.8, could be used to elevate privileges to SYSTEM assigned integrity level. Denial of service vulnerability CVE-2022-44707, with CVSS of 6.5, could cause a system to crash, making it inaccessible to its intended users.
| Rank | CVSS Score | CVE | Description |
| Important | 7.5 | CVE-2022-44713 | Microsoft Outlook for Mac Spoofing Vulnerability |
| Important | 7.8 | CVE-2022-44704 | Microsoft Windows Sysmon Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2022-44683 | Windows Kernel Elevation of Privilege Vulnerability |
| Important | 6.5 | CVE-2022-44707 | Windows Kernel Denial of Service Vulnerability |
Figure 5. Important vulnerabilities to consider, December 2022
Review Your Mitigation Strategy Before 2022 Ends
With only a couple of weeks left in 2022, it’s important to review your strategy and make sure it integrates with the broader organization’s security goals, not just within security operations. Security and operations teams need layered security and tools that help prevent, detect and identify vulnerabilities and guide them through their patching and assessment process. A fresh and up-to-date mitigation strategy will help to reduce the areas of opportunity for attackers, helping your organization remain as secure as possible and prevent any potential breach.
Learn More
This video on CrowdStrike Falcon Spotlight™ vulnerability management shows how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Download the CrowdStrike 2022 Falcon OverWatch Threat Hunting Report to learn more about recent adversary tradecraft and tooling and get actionable tips for staying ahead of today's stealthiest, most sophisticated cyber threats.
- See how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Learn how Falcon Identity Protection products can stop workforce identity threats faster.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































