While the total number of patches Microsoft delivered in its "Patch Tuesday" update this month is lower than usual, it included some sorely needed fixes -- including one that addresses Zerologon, a vulnerability actively being exploited. In this blog, the first of a new monthly series, CrowdStrike researchers assess the new patches available, providing guidance on which ones IT staff should consider prioritizing in their patching programs. Let’s get started.New Patches for 56 Vulnerabilities
Microsoft disclosed 56 new vulnerabilities for February’s Patch Tuesday. Windows OS — kernel, TCP/IP, video codecs, PowerShell and other Windows-based applications — accounted for the largest number of vulnerabilities (28), followed by Microsoft extended support (ESU) components — Win32k, RPC, TCP/IP, spooler and so on — which accounted for 14 vulnerabilities. We also saw updates for vulnerabilities in Microsoft Office (SharePoint, Excel, etc.), development tools (Visual Studio, Sysinternals) and more. The graph indicates the type of attack impact and quantity represented in this month’s update.
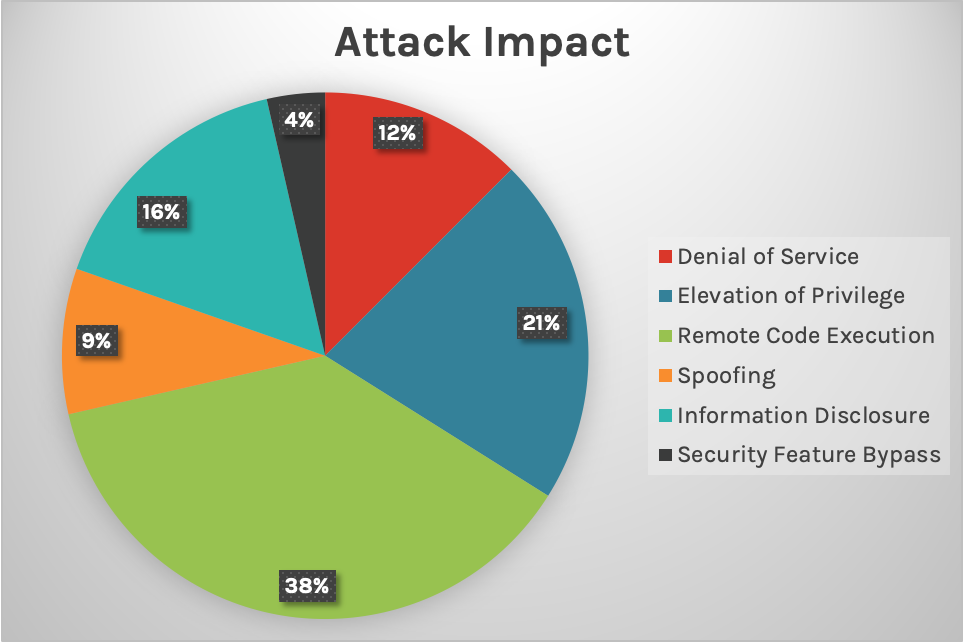 Breakdown of February’s Patch Tuesday vulnerabilities attack impact
Breakdown of February’s Patch Tuesday vulnerabilities attack impact
Other than the above two RCE vulnerabilities, there are two additional critical RCE vulnerabilities in Windows DNS server and Fax service. Please note that CVE-2021-24078 is only exploitable if the server is configured to be a DNS server. CVE-2021-24077 is only exploitable when the Fax service is running. A workaround for CVE-2021-24077 is also available.
Review Patching Policies and Back Up Your Data
While the count of updates Microsoft disclosed for this particular Patch Tuesday isn’t exceptionally high, CVE-2021-1732 has been actively exploited in the wild. This, combined with the mandatory enablement of enforcement mode to protect against the also actively exploited Zerologon vulnerability, makes this Patch Tuesday an important one to prioritize. All of these updates, including the updates to components that can’t be disabled practically (such as TCP/IP stack), are important for applying workaround or patches as soon as possible. Continuously scanning for vulnerabilities, working together with your IT and security teams, and rigorously applying your patching protocol is the best defense to strengthen your environment from adversaries. More exploits are occurring in the wild — don’t forget to regularly update systems and keep data backed up.Additional Resources
New Patches for 56 Vulnerabilities
Microsoft disclosed 56 new vulnerabilities for February’s Patch Tuesday. Windows OS — kernel, TCP/IP, video codecs, PowerShell and other Windows-based applications — accounted for the largest number of vulnerabilities (28), followed by Microsoft extended support (ESU) components — Win32k, RPC, TCP/IP, spooler and so on — which accounted for 14 vulnerabilities. We also saw updates for vulnerabilities in Microsoft Office (SharePoint, Excel, etc.), development tools (Visual Studio, Sysinternals) and more. The graph indicates the type of attack impact and quantity represented in this month’s update.
 Breakdown of February’s Patch Tuesday vulnerabilities attack impact
Breakdown of February’s Patch Tuesday vulnerabilities attack impactCritical Vulnerabilities to Consider
The most notable CVE in this release is CVE-2021-1732 — Elevation of Privilege in Win32k, for which Microsoft has already seen active exploitation in the wild. It has been rated as CVSS 7.8 and is applicable on even the latest Windows 10 20H2. We advise you to prioritize patching this vulnerability first.| Rank | CVSS Score | CVE | Description |
| Critical | 7.8 | 2021-1732 | Windows Win32k Elevation of Privilege |
Important Tip
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate the severity and characteristics of software vulnerabilities. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Final Updates for Zerologon
This month’s update from Microsoft mandates the enablement of enforcement mode in relation to the Zerologon vulnerability, which saw active exploitation in September 2020. Zerologon is a vulnerability located in Microsoft Windows Netlogon Remote Protocol (MS-NRPC), an area responsible for the authentication of Active Directory. If an attacker were to exploit this vulnerability, it would allow them to compromise the Windows Server domain controllers. Once an attacker achieved access to the controllers, they could compromise the environment that relies on Active Directory authentication. Since adversaries are actively exploiting this vulnerability, IT teams should look to prioritize this final update.Additional Patches for Critical RCE Vulnerabilities
TCP/IP accounted for the most critical vulnerabilities, according to the CVSS base score (9.8) assigned to them. Both CVE-2021-24074 and CVE-2021-24094 are Remote Code Execution (RCE) vulnerabilities, meaning that attackers could use Windows Server 2008-2019 to install software remotely. This CVSS score is considered very critical, and IT teams should also consider prioritizing these vulnerabilities. However, if immediate patching isn’t an option, there are some workarounds for these vulnerabilities until such time when patching is possible.| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | 2021-24074 | Windows TCP/IP Remote Code Execution |
| Critical | 9.8 | 2021-24094 | Windows TCP/IP Remote Code Execution |
| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | 2021-24078 | Windows DNS Server Remote Code Execution |
| Critical | 9.8 | 2021-24077 | Windows Fax Service Remote Code Execution |
Learn More
Watch this video on Falcon Spotlight™ vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
Review Patching Policies and Back Up Your Data
While the count of updates Microsoft disclosed for this particular Patch Tuesday isn’t exceptionally high, CVE-2021-1732 has been actively exploited in the wild. This, combined with the mandatory enablement of enforcement mode to protect against the also actively exploited Zerologon vulnerability, makes this Patch Tuesday an important one to prioritize. All of these updates, including the updates to components that can’t be disabled practically (such as TCP/IP stack), are important for applying workaround or patches as soon as possible. Continuously scanning for vulnerabilities, working together with your IT and security teams, and rigorously applying your patching protocol is the best defense to strengthen your environment from adversaries. More exploits are occurring in the wild — don’t forget to regularly update systems and keep data backed up.
Additional Resources
- Learn more about how Falcon Spotlight can help you identify and prioritize vulnerabilities.
- Read about the custom CrowdStrike dashboard for CVE-2020-1472 ZeroLogon Vulnerability.
- Learn about the recent Baron Samedit vulnerability and CrowdStrike’s custom dashboard.
- Watch how to use Falcon Spotlight and Real Time Response (RTR) for emergency patching.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)











































