Kicking off the first Patch Tuesday of 2022, CrowdStrike continues to provide research and analysis regarding critically rated vulnerabilities and the subsequent patches offered by Microsoft. In this month’s updates we see the lion’s share of updates directed at Microsoft’s Windows and Extended Security Update (ESU) products, while other patches target lesser-known components of Microsoft’s operating system. What is noticeably missing this month is a patch for any in-the-wild exploited vulnerabilities, as there have been several in recent months.
We also discuss three Microsoft Exchange remote code execution vulnerabilities that received updates. If you recall, Microsoft Exchange was involved in a massive exploitation campaign in early 2021. Prioritizing these patches should be strongly considered if your organization relies on this product.
New Patches for 97 Vulnerabilities
This month’s Patch Tuesday update includes fixes for 97 vulnerabilities. Combined with the 29 vulnerabilities that received out-of-band (OOB) updates at the start of January, this first month of 2022 has a total of 126 patched updates. On its own, that number isn’t too surprising, given the Log4j vulnerabilities SecOps staff have to deal with (see the CrowdStrike Log4j Resource Center for more information) but the updates from Microsoft are certainly needed, as SecOps still remain pressed for time when it comes to mitigation and remediation.
Similar to risk analysis for the past three months, the top two attack types for Microsoft products continue to be privilege elevation and remote code execution. The third primary attack type alternates between information disclosure and denial of service. However, unlike the last two months of updates — where patches were spread more evenly across product families — this month we see the large majority of updates concentrated on Windows products and Extended Security Updates (ESU) products. Consider focusing your patching based on the family of Windows products your organization uses.
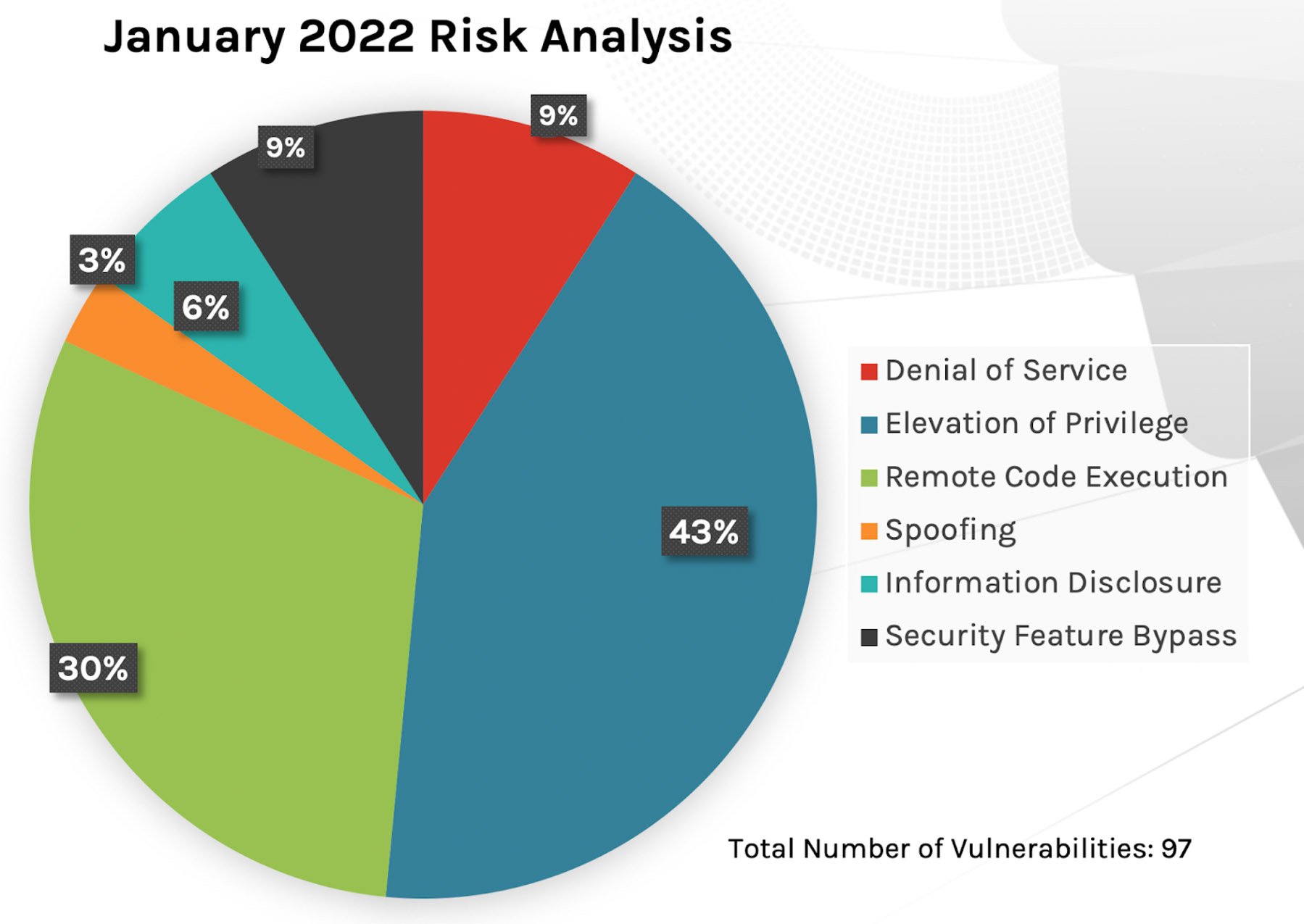 Figure 1. Breakdown of January 2022 Patch Tuesday attack types
Figure 1. Breakdown of January 2022 Patch Tuesday attack types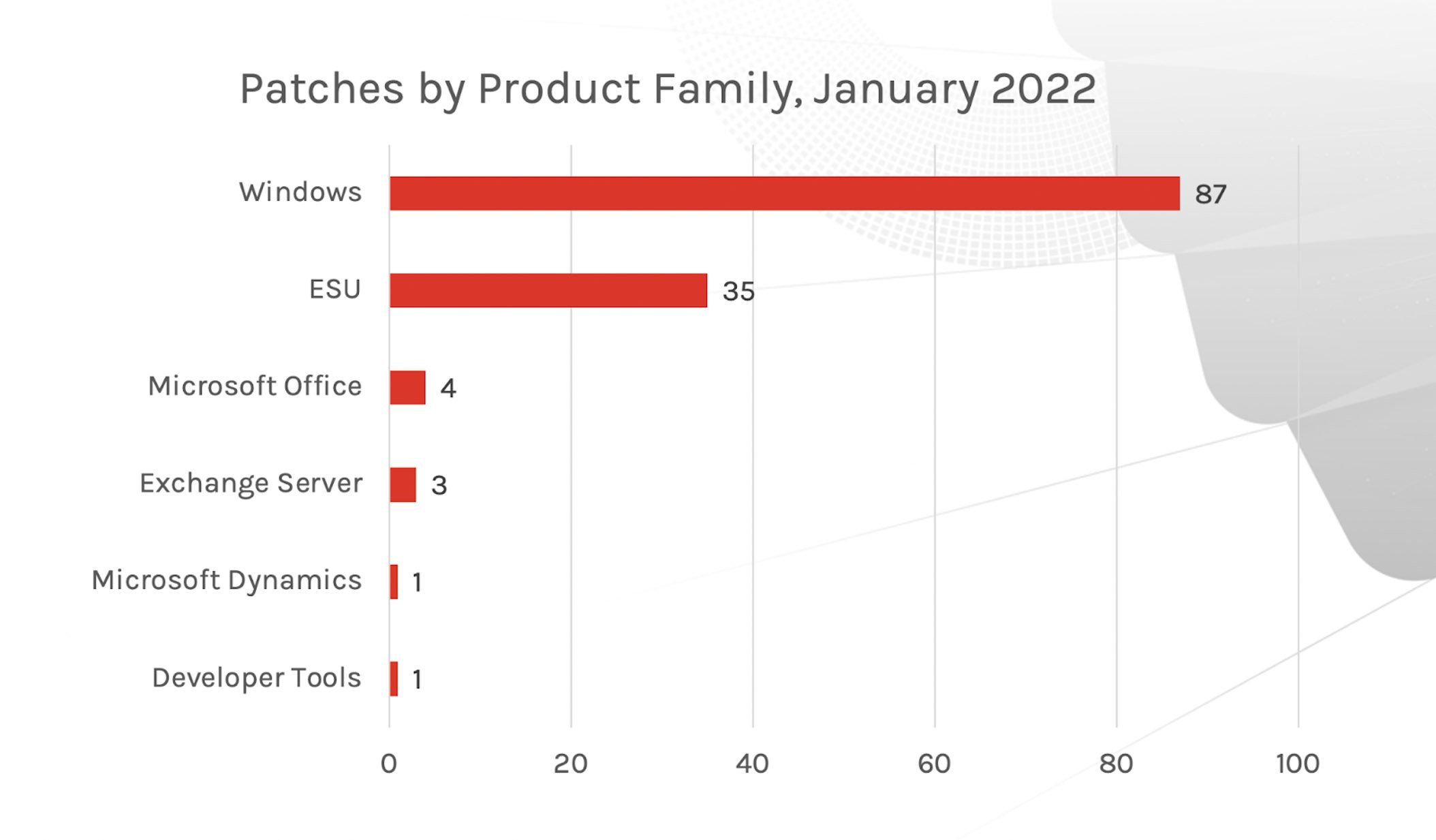 Figure 2. Breakdown of January 2022 Patch Tuesday affected product families
Figure 2. Breakdown of January 2022 Patch Tuesday affected product familiesRemote Code Execution and Elevation of Privilege Dominate as Attack Types for January’s Critical Vulnerabilities
This month, a number of vulnerabilities have a CVSS score of 8.8 or higher affecting various Microsoft products. Remember, the criticality of a CVSS score alone should not be the only determining factor in your prioritization process. A combination of various data points, attacker information and news reports could change how severe or critical that score may be for your organization. (Falcon Spotlight™ ExPRT.AI can help your staff quickly identify what’s truly critical and relevant to your organization.) However, CrowdStrike analysis shows that among this month’s critically ranked vulnerabilities, two attack types — remote code execution and privilege escalation — are particularly attractive methods, allowing attackers to gain a foothold in affected systems. CVE-2022-21849: This remote code execution vulnerability affects the Internet Key Exchange. It can be leveraged with an unauthenticated attacker that is able to run the IPSec Service. It’s been given the most Critical CVSS score of 9.8.
CVE-2022-21907: This vulnerability affecting the HTTP Protocol Stack is also ranked as Critical this month. This vulnerability impacts the Windows Operating System in Windows 10 and Windows Server 2019, but the HTTP Trailer Support feature — which is the vulnerable component — is not enabled by default. There may be additional manual validation that your SecOps staff should perform. It should be noted that this vulnerability is remotely exploitable on older versions of the operating system, which could open the door for self-propagating malware to exploit it. CVE-2022-21901: This vulnerability is exploited via privilege escalation. Attackers exploit this Windows Hyper-V vulnerability by executing a specially crafted application on a vulnerable system. If successful, an attacker could potentially interact with processes of another Hyper-V guest hosted on the same Hyper-V host. The remaining vulnerabilities listed in the table below are executed via a Remote Procedure Call (RPC) Runtime for CVE-2022-21922 and a remote code execution attack type on Microsoft Office for CVE-2022-21840. For the latter vulnerability, it’s worth noting that this vulnerability affects Microsoft Office versions for macOS, Apple’s operating system. At the time of this month’s Microsoft Patch Tuesday release, there are no currently available patches for Apple Systems running Microsoft Office products.
| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | CVE-2022-21849 | Windows IKE Extension Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2022-21907 | HTTP Protocol Stack Remote Code Execution Vulnerability |
| Critical | 9 | CVE-2022-21901 | Windows Hyper-V Elevation of Privilege Vulnerability |
| Critical | 8.8 | CVE-2022-21922 | Remote Procedure Call Runtime Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-21840 | Microsoft Office Remote Code Execution Vulnerability |
Microsoft Exchange Remote Code Execution Vulnerabilities
Microsoft Exchange Server is a known objective for attackers. When vulnerabilities affecting this product are released, SecOps staff often face the pressure of patching them as soon as possible, especially if these servers are exposed to the internet. This month’s updates include fixes for three remote code execution vulnerabilities, all with a CVSS Score of 9.0 (see the table below).
As we’re approaching the one year anniversary of the massive exploitation campaign that occurred against Microsoft Exchange Server, it’s important to keep an eye out for potential attack vectors. It’s paramount for SecOps teams to be able to identify vulnerable instances and patch them the first opportunity they have. Of note, all of the CVEs listed in the table below have been flagged as the attack vector being “adjacent.” This means that this particular attack type cannot be executed across the internet, but it could be successful if an attacker has gained a foothold on any other machine in the network.
| Rank | CVSS Score | CVE | Description |
| Critical | 9 | CVE-2022-21846 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Critical | 9 | CVE-2022-21855 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Critical | 9 | CVE-2022-21969 | Microsoft Exchange Server Remote Code Execution Vulnerability |
Remote Desktop Protocol Vulnerabilities
Three remote code execution vulnerabilities received updates this month on Microsoft’s Remote
Desktop Protocol. Two of them affect the client (CVE-2022-21850 and CVE-2022-21851), and one affects Remote Desktop Protocol (CVE-2022-21893). To exploit CVE-2022-21850 and CVE-2022-21851, an attacker would need to persuade an authenticated user to connect to a malicious remote desktop server, enabling the attacker to then exploit the vulnerabilities via remote code execution.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2022-21850 | Remote Desktop Client Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-21851
| Remote Desktop Client Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-21893 | Remote Desktop Protocol Remote Code Execution Vulnerability |
Other Critical and Important Vulnerabilities to Consider
| Rank | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2022-21920 | Windows Kerberos Elevation of Privilege Vulnerability |
| Important | 7.0 | CVE-2022-21882 | Win32k Elevation of Privilege Vulnerability |
| Important | 7.0 | CVE-2022-21887 | Win32k Elevation of Privilege Vulnerability |
| Important | 5.5 | CVE-2022-21876 | Win32k Information Disclosure Vulnerability |
| Important | 5.5 | CVE-2022-21906 | Windows Defender Application Control Security Feature Bypass Vulnerability |
| Important | 4.4 | CVE-2022-21921 | Windows Defender Application Control Security Feature Bypass Vulnerability |
Patch and Review Your Mitigation Strategy
A layered security approach — with a heavy emphasis on tools, programs and solutions that create efficiency and quicken response time — is key to a defensible security posture for your organization. Vulnerabilities are found in a wide variety of Microsoft products and platforms, with attackers diligently working on more creative ways to access valuable systems and information.
This month’s focus on Windows and ESU products underscores the value of a robust mitigation strategy for vulnerabilities that affect your organization's critical systems where patches are not available.
Learn More
Watch this video on Falcon Spotlight™ vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Learn how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- See how Falcon Complete stops Microsoft exchange server zero-day exploits.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Read our December 2021 Patch Tuesday blog post for more information on critical vulnerabilities your organization should prioritize.
- Learn about the recent Baron Samedit vulnerability and CrowdStrike’s custom dashboard.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































