Microsoft has released 66 security patches for its November 2022 Patch Tuesday rollout. Of these, 10 vulnerabilities are rated Critical and the remaining 56 are rated Important. It should be noted that this month’s patching update does include the highly anticipated patches for ProxyNotShell, which we suggest you promptly apply; if your team decides to wait, we have listed our mitigation recommendations in our October 2022 Patch Tuesday blog.
Another zero-day vulnerability that is worth special attention and prompt patching is CVE-2022-41128, an actively exploited Critical bug in Windows Scripting Language with a CVSS of 8.8, which impacts the JScript9 scripting language. This bug could be exploited by convincing the end user to visit either a specially crafted website or server share. In doing so, they would get their code to execute on an affected system at the level of the logged-on user. Microsoft has not yet provided the details, but we can expect this will be a popular bug to include in exploit kits.
November 2022 Risk Analysis
This month’s leading risk type is elevation of privilege (40%), followed by remote code execution (24%) and information disclosure (15%).
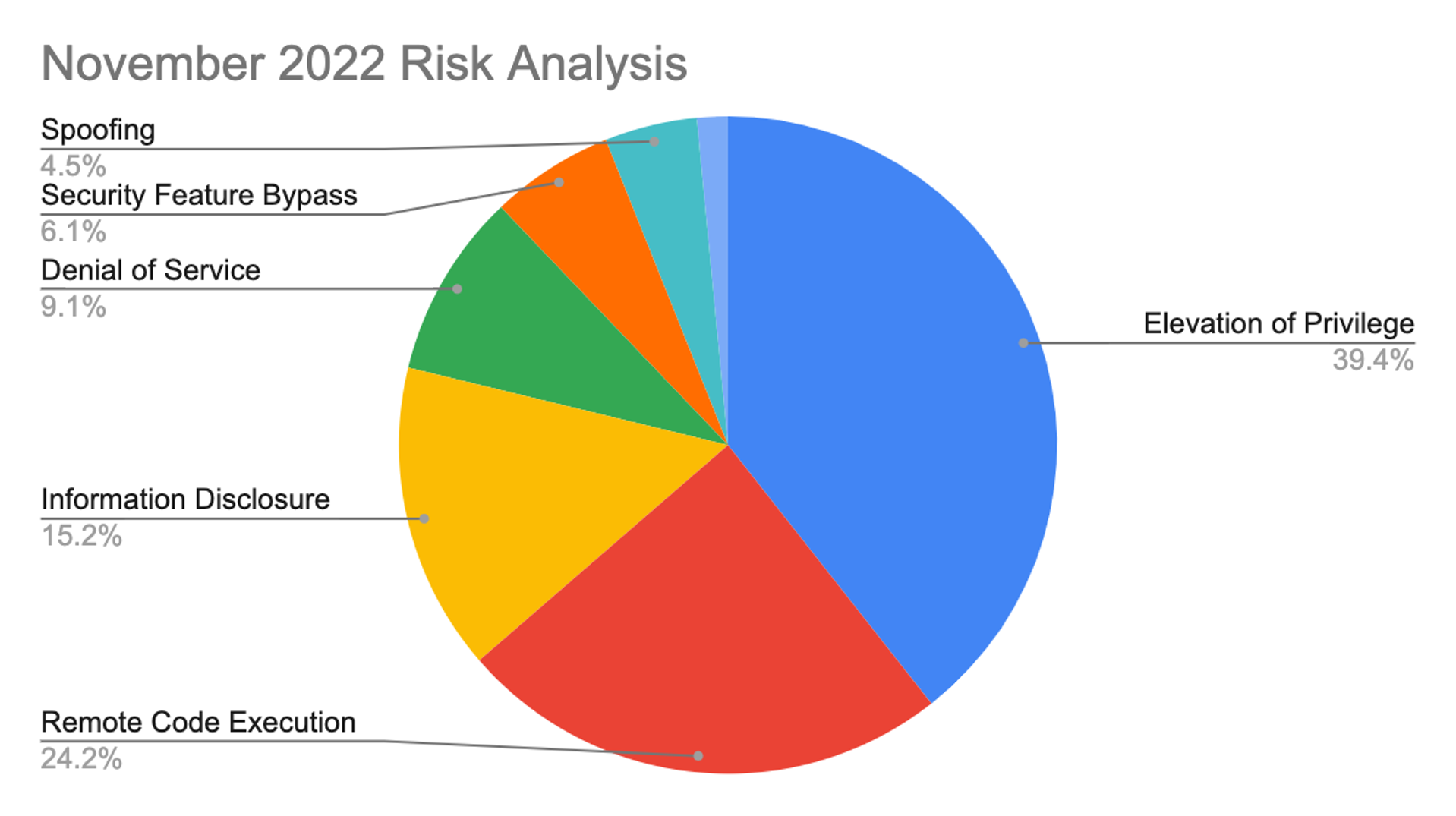 Figure 1. Breakdown of November 2022 Patch Tuesday attack types
Figure 1. Breakdown of November 2022 Patch Tuesday attack typesThe Microsoft Windows product family received the most patches this month with 40, followed by Extended Support Updates (24) and Microsoft Office products (11). Also covered in the update is CVE-2022-41073, an actively exploited Windows Print Spooler Elevation of Privilege Vulnerability with a CVSS of 7.8.
 Figure 2. Breakdown of product families affected by November 2022 Patch Tuesday
Figure 2. Breakdown of product families affected by November 2022 Patch TuesdayThreat actors continue to exploit the vast attack surface that is the Windows Print Spooler. While we’ve seen plenty of new patches since PrintNightmare, CVE-2022-41073 is listed as being actively exploited. As you may be familiar, disabling the print spooler should be an effective workaround — this, of course, breaks printing, but if you’re in a situation where patching isn’t feasible, it is an option. As shown in Figure 3, this CVE is ranked as Important, along with CVE-2022-41091, a Windows Mark of the Web Security Feature Bypass Vulnerability. This vulnerability is also listed as being under active attack, but again, Microsoft provides no information on how widespread these attacks may be.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2022-41073 | Windows Print Spooler Elevation of Privilege Vulnerability |
| Important | 5.4 | CVE-2022-41091 | Windows Mark of the Web Security Feature Bypass Vulnerability |
Figure 3. Zero-day vulnerability and print spooler vulnerability patched in November 2022
ProxyNotShell and Additional Microsoft Exchange Server Bugs
Official patches for ProxyNotShell, two vulnerabilities discovered in and exploited since September, are being released this month. Yes, they were expected last month, but they are finally here. At the time of discovery, researchers reported that these elevation of privilege and remote code execution vulnerabilities — CVE-2022-41082 and CVE-2022-41040 — had been used to infect on-premises Exchange servers with web shells, the text-based interfaces that allow people to remotely execute commands. Better known as ProxyNotShell, these vulnerabilities affect on-premises Exchange servers. Microsoft said in early October it was aware of only a single threat actor exploiting the vulnerabilities and the actor had targeted fewer than 10 organizations. CrowdStrike recommends applying patches as soon as possible if you have vulnerable on-premises or hybrid exchange servers where temporary mitigation has not been applied.
CVE-2022-41080, a Microsoft Exchange Server elevation of privilege vulnerability, was disclosed by Microsoft and is labeled as “exploitation more likely,” but there are no records of active exploitation in the wild. This new vulnerability scores a CVSS 8.8, making it a critical vulnerability to address.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2022-41040 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| Critical | 8.8 | CVE-2022-41082 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-41080 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| Important | 8 | CVE-2022-41079 | Microsoft Exchange Server Spoofing Vulnerability |
| Important | 8 | CVE-2022-41078 | Microsoft Exchange Server Spoofing Vulnerability |
| Important | 7.8 | CVE-2022-41104 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
Figure 4. Critical vulnerabilities in MS Exchange
Critical Vulnerabilities Affecting Kerberos and PPTP
For this month's release, the two privilege escalation vulnerabilities in Kerberos stand out, especially because Microsoft notes this is a phased rollout of fixes. Apparently you will need to take additional steps beyond applying the patch; specifically, you’ll need to review KB5020805 and KB5021131 to see the changes made and next steps. Also, there are three Critical patches for Point-to-Point Tunneling Protocol (PPTP). This seems to be a continuing trend of researchers looking for bugs in legacy protocols. As we said on previous occasions, if you rely on PPTP, you should really consider upgrading to something more modern.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.1 | CVE-2022-37966 | Windows Kerberos RC4-HMAC Elevation of Privilege Vulnerability |
| Critical | 8.1 | CVE-2022-41039 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-41088 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-41044 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 7.2 | CVE-2022-37967 | Windows Kerberos Elevation of Privilege Vulnerability |
Figure 5. Critical vulnerabilities in Kerberos and PPTP
Important Vulnerabilities in Group Policy, SharePoint and Microsoft Word
There are two bugs in Windows Group Policy and successful exploitation of these vulnerabilities require the attacker to have privileges to create Group Policy Templates. As is best practice, regular validation and audits of administrative groups should be conducted. Regarding the SharePoint vulnerabilities, we know for CVE-2022-41122, the attacker must be authenticated and possess the permissions for page creation in order to exploit it.
As seen in figure 6, there are three Important bugs in Microsoft Word, with CVSS of 7.8 and 5.5. We can confirm the Preview Pane is not an attack vector for these bugs; however, we wanted to emphasize the importance of patching Microsoft Office-related vulnerabilities (in this case Word) as these are heavily used products. In an email attack scenario, for example, an attacker could exploit these vulnerabilities by sending a specially crafted file to the user and convincing them to open the file.
| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2022-41062 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2022-37992 | Windows Group Policy Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2022-41078 | Microsoft Word Remote Code Execution Vulnerability |
| Important | 6.5 | CVE-2022-41122 | Microsoft SharePoint Server Spoofing Vulnerability |
| Important | 6.4 | CVE-2022-41086 | Windows Group Policy Elevation of Privilege Vulnerability |
| Important | 5.5 | CVE-2022-41103 | Microsoft Word Information Disclosure Vulnerability |
| Important | 5.5 | CVE-2022-41060 | Microsoft Word Information Disclosure Vulnerability |
Figure 6. Important Vulnerabilities in Group Policy, SharePoint and Microsoft Word
Adversaries Are Evolving, Your Mitigation Strategies Should Too
What gets patched and what is moved to the back burner should be taken into consideration in conjunction with other areas of a defensive security posture, including security hygiene and XDR. Your organization’s security strategy, and what is involved in your patching program, could have a direct impact on the strength of your organization’s security. It’s important to develop a strategy that works together with the broader organization’s security goals, not just within security operations.
The CrowdStrike Falcon platform collects and analyzes trillions of endpoint events every day from millions of sensors deployed across 176 countries. Watch this demo to see the Falcon platform in action.
Learn More
This video on Falcon Spotlight™ vulnerability management shows how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Download the CrowdStrike 2022 Falcon OverWatch Threat Hunting Report to learn more about recent adversary tradecraft and tooling and get actionable tips for staying ahead of today's stealthiest, most sophisticated cyber threats.
- See how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Learn how Falcon Identity Protection products can stop workforce identity threats faster.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































