Microsoft has released 84 security patches for its October 2022 Patch Tuesday rollout. Of these, 13 vulnerabilities are rated Critical, while the remaining 71 are rated Important. It should be noted that this month’s patching update does not include patches for ProxyNotShell, despite the active exploitation of two related vulnerabilities; CrowdStrike offers recommendations on mitigation until patches are provided.
Mitigations for ProxyNotShell Vulnerabilities
Two recently uncovered vulnerabilities — CVE-2022-41040 and CVE-2022-41082 — can be chained together to perform remote code execution (RCE) through PowerShell. By exploiting these vulnerabilities, an attacker could gain privileged access and remotely install the China Chopper webshell. This type of attack targets the Microsoft Exchange Mailbox server, and an attacker could use it to gain access and move laterally into Exchange or Active Directory. Microsoft’s initial mitigation recommendations were insufficient, as threat researchers showed they can be easily bypassed to allow new attacks exploiting the two bugs. The CrowdStrike Falcon® platform helps protect organizations of all sizes from sophisticated breaches that exploit vulnerabilities by using a defense-in-depth approach to deliver detections and mitigations in real-time. While no patches are yet available, CrowdStrike recommends the following mitigations for these vulnerabilities:
- For CVE-2022-41040, complete the URL Rewrite Rule mitigation. Exchange administrators need to create a rule that blocks URLs that match the following pattern: .*autodiscover\.json.*Powershell.*. This will prevent known variants of the ProxyNotShell attacks. It is also advised that Condition Input should be changed from {URL} to {UrlDecode:{REQUEST_URI}} to ensure all encoded variations are evaluated before being blocked.
- CrowdStrike customers with Exchange Emergency Mitigation Service (EEMS) enabled benefit automatically from the updated URL Rewrite mitigation for Exchange Server 2016 and Exchange Server 2019. A complete guide on mitigations for reported zero-day vulnerabilities in Microsoft Exchange Server is available from Microsoft.
- For CVE-2022-41082, disable remote PowerShell for non-admins. CrowdStrike Falcon®® platform customers should disable remote PowerShell access for non-admin users in your organization (as a best practice, CrowdStrike recommends doing this anyway for non-admin users).
CrowdStrike Falcon® Intelligence™ customers can view a complete technical write-up, attribution and targeting information within the Falcon platform: CSA-221036.
October 2022 Risk Analysis
This month’s leading risk type is elevation of privilege (46%), followed by remote code execution at nearly 24% and information disclosure at 13%. The October 2022 Patch Tuesday release includes patches for 11 information-disclosure vulnerabilities, including one publicly known that affects MS Office products.
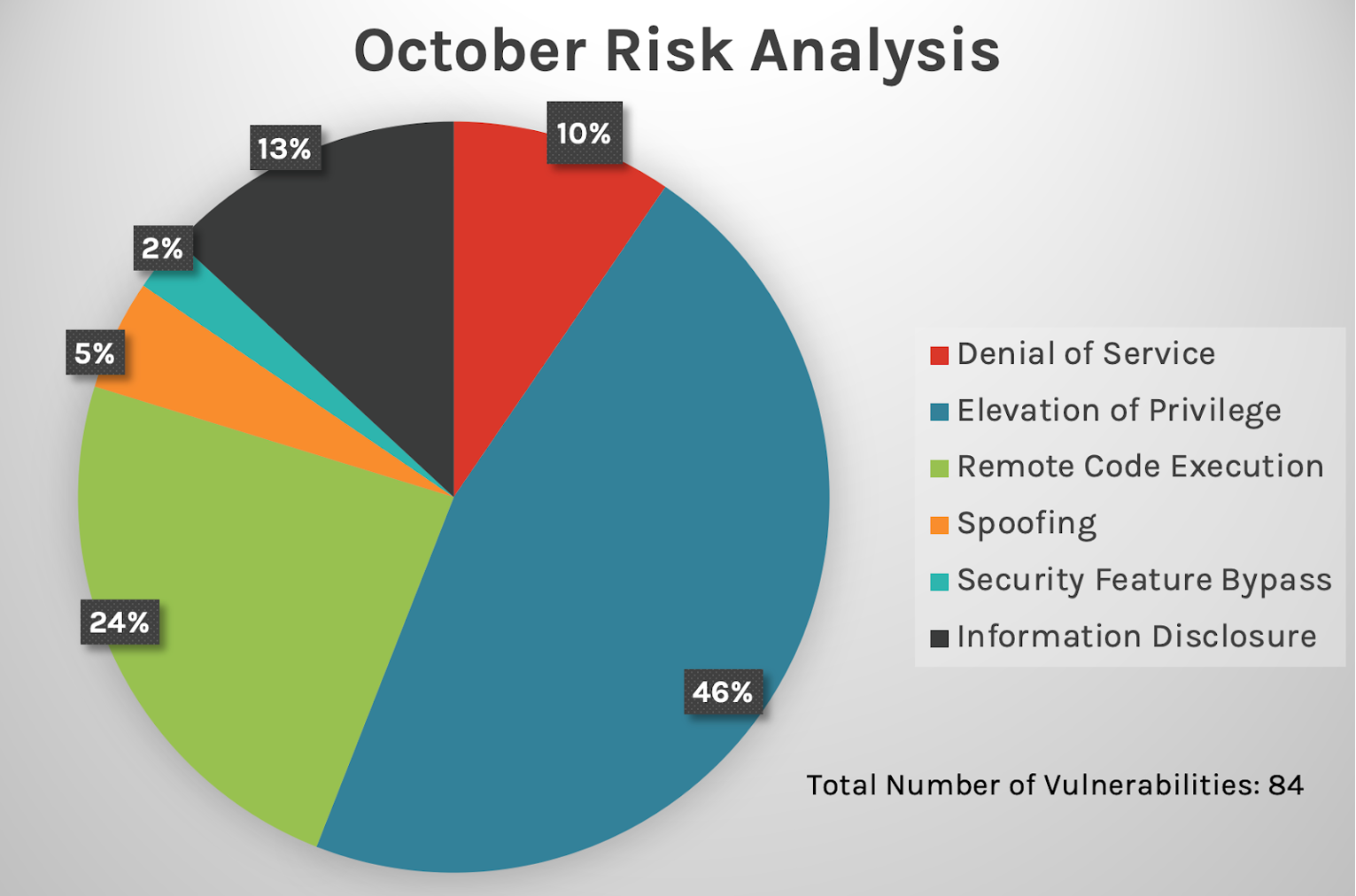 Figure 1. Breakdown of October 2022 Patch Tuesday attack types
Figure 1. Breakdown of October 2022 Patch Tuesday attack typesThe Microsoft Windows product family received the most patches this month with 67, followed by Extended Support Updates (44) and Microsoft Office products (9). Also covered in the update is CVE-2022-41033, an elevation of privilege zero-day vulnerability being used in active attacks that affects Windows COM+ Event System Service and is rated as Important with a CVSS of 7.8.
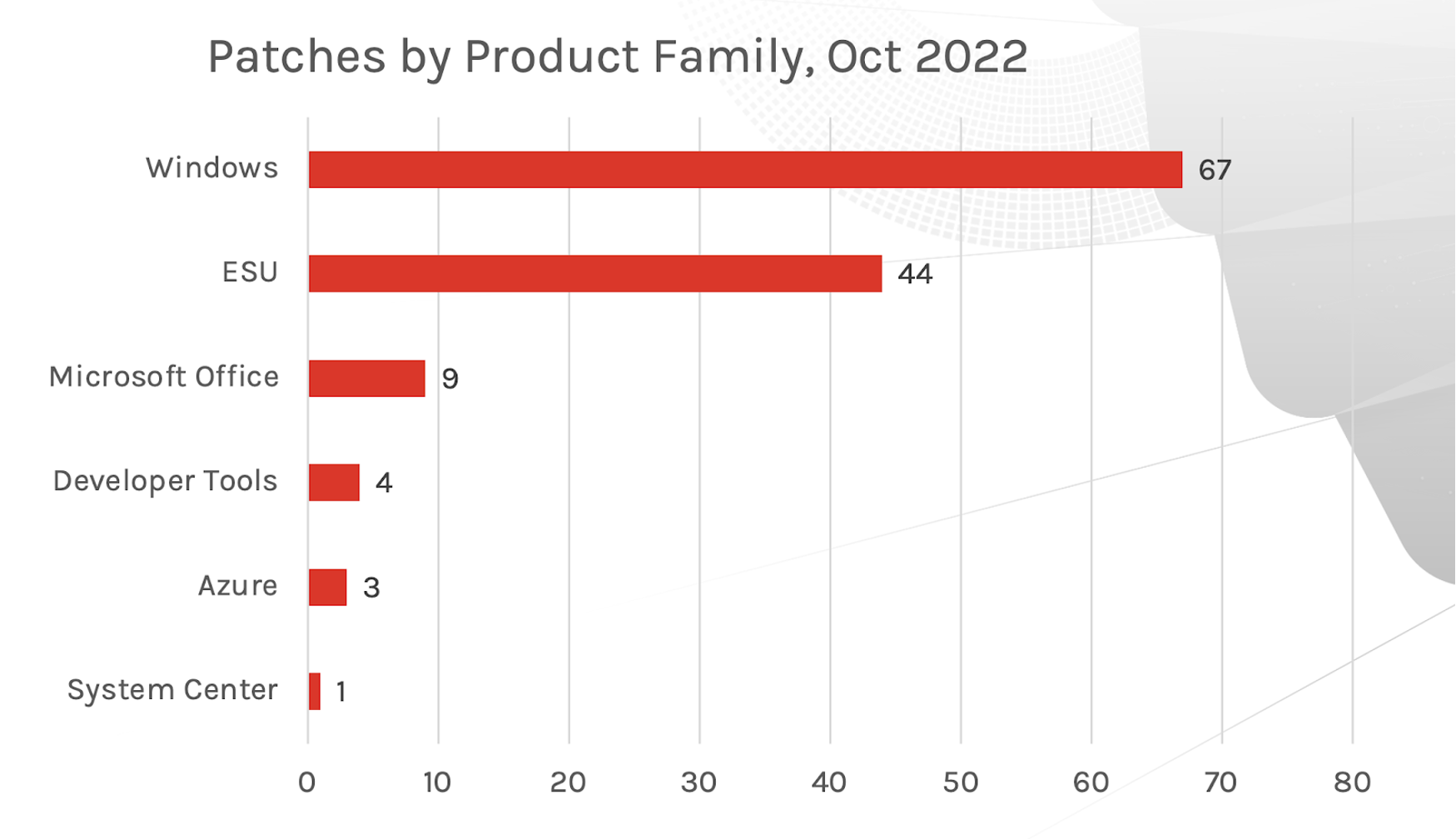 Figure 2. Breakdown of product families affected by October 2022 Patch Tuesday
Figure 2. Breakdown of product families affected by October 2022 Patch TuesdayCVE-2022-41033 is typically paired with other code execution exploits designed to take over a system. This type of attack often involves some form of social engineering, such as enticing a user to open an attachment or go to a malicious website. As shown in Figure 3, this CVE is ranked as Important. Another Important vulnerability affects Active Directory Domain Services and could allow an attacker to get domain administrator privileges, but Microsoft has not provided any details on how that would occur.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2022-41033 | Windows COM+ Event System Service Elevation of Privilege Vulnerability |
| Important | 7.1 | CVE-2022-38042 | Active Directory Domain Services Elevation of Privilege Vulnerability |
Figure 3. Zero-day vulnerability and AD vulnerability patched in October 2022
CVE-2022-37976, a Critical Active Directory Certificate Services (ADCS) vulnerability, definitely stands out as a CVE to prioritize. If successfully exploited, it provides the attacker with domain administrative privileges. However, exploiting this vulnerability is not easy. A malicious DCOM client would need to trick a DCOM server to authenticate to it through ADCS and then use the credential to launch a cross-protocol attack.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2022-37976 | Active Directory Certificate Services Elevation of Privilege Vulnerability |
Figure 4. Critical vulnerability patched in October 2022
Critical Vulnerabilities in Microsoft Office and Azure Arc
Azure Arc is getting a patch for Critical vulnerability CVE-2022-37968, with a perfect CVSS of 10. Azure Arc-enabled Kubernetes allows you to attach and configure Kubernetes clusters running anywhere. As per the Microsoft Security Response Center (MSRC), an attacker that knows the randomly generated external DNS endpoint for an Azure Arc-enabled Kubernetes cluster can exploit this vulnerability from the internet, affecting the cluster connect feature of Azure Arc-enabled Kubernetes clusters. Keep in mind that auto-upgrade is enabled by default for CrowdStrike customers using Azure Arc; however, if you manually control your updates, action is required to upgrade to the latest version.
CVE-2022-38048, a Microsoft Office RCE vulnerability, is a Critical bug with a CVSS of 7.8. Most Office vulnerabilities are rated Important since they involve user interaction — typically opening a file. An exception is when the Preview Pane is an attack vector, but Microsoft states it isn’t the case here. The rating is likely the result of the lack of warning dialogs when opening a specially crafted file. Either way, this is a use-after-free (UAF) vulnerability that could lead to passing an arbitrary pointer to a free call, making further memory corruption possible.
| Rank | CVSS Score | CVE | Description |
| Critical | 10 | CVE-2022-37968 | Azure Arc-enabled Kubernetes cluster Connect Elevation of Privilege Vulnerability |
| Critical | 7.8 | CVE-2022-38048 | Microsoft Office Remote Code Execution Vulnerability |
Figure 5. Critical vulnerabilities in Azure Arc and MS Office
Critical Vulnerabilities Affecting Microsoft Word and PPTP
CVE-2022-41031, a Critical vulnerability affecting Microsoft Word, is getting a patch this month. In this particular case, the Preview Pane is not an attack vector. The remaining Critical vulnerabilities affect Windows Point-to-Point Tunneling Protocol. If you’re still using it, consider migrating to a more modern (and secure) solution. To exploit these vulnerabilities, an attacker would need to send a specially crafted malicious PPTP packet to a PPTP server. This could result in remote code execution on the server side.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.1 | CVE-2022-30198 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-24504 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-33634 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-22035 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-38047 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-38000 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-41081 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2022-41031 | Microsoft Word Remote Code Execution Vulnerability |
Figure 6. Critical vulnerabilities in MS Word and PPTP
Not All Relevant Vulnerabilities Have Patches: Consider Mitigation Strategies
As we have learned with other notable vulnerabilities, such as Log4j, not every highly exploitable vulnerability can be easily patched. As is the case for the ProxyNotShell vulnerabilities, it’s critically important to develop a response plan for how to defend your environments when no patching protocol exists.
Regular review of your patching strategy should still be a part of your program, but you should also look more holistically at your organization's methods for cybersecurity and improve your overall security posture.
The CrowdStrike Falcon® platform collects and analyzes trillions of endpoint events every day from millions of sensors deployed across 176 countries. Watch this demo to see the Falcon platform in action.
Learn More
This video on Falcon Spotlight™ vulnerability management shows how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Download the CrowdStrike 2022 Falcon OverWatch Threat Hunting Report to learn more about recent adversary tradecraft and tooling and get actionable tips for staying ahead of today's stealthiest, most sophisticated cyber threats.
- See how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Learn how Falcon Identity Protection products can stop workforce identity threats faster.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































