This month marks the 20th anniversary of Patch Tuesday, and Microsoft has released security updates for 104 vulnerabilities, including three zero-days. One of the zero-days (CVE-2023-41763) is an elevation of privilege vulnerability in Microsoft Skype for Business. The second (CVE-2023-36563) is an information disclosure vulnerability in Microsoft WordPad, and the third (CVE-2023-44487) enables a distributed denial-of-service (DDoS) attack technique named “HTTP/2 Rapid Reset.” Twelve of the vulnerabilities addressed today are rated as Critical while the remaining 92 are rated as Important.
October 2023 Risk Analysis
This month’s leading risk type is remote code execution (43%), followed by elevation of privilege (25%) and denial of service (16%).
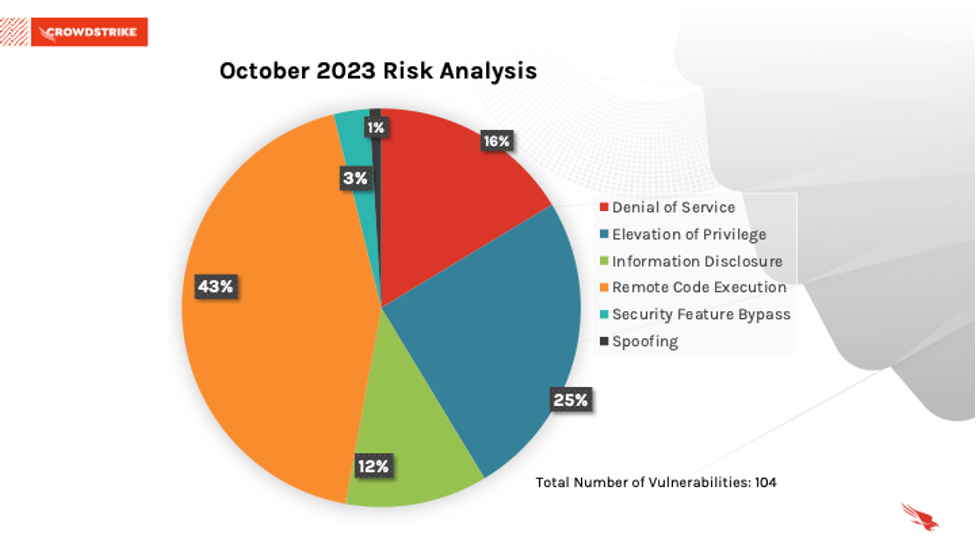 Figure 1. Breakdown of October 2023 Patch Tuesday attack types
Figure 1. Breakdown of October 2023 Patch Tuesday attack types
The Microsoft Windows product family received the most patches this month (78), followed by Microsoft Office (7), and Azure (6).
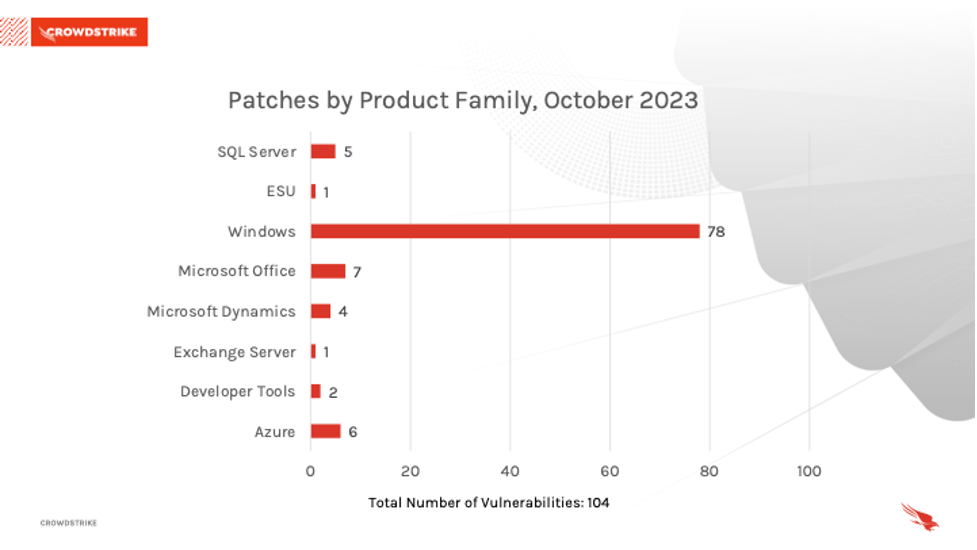 Figure 2. Breakdown of product families affected by October 2023 Patch Tuesday
Figure 2. Breakdown of product families affected by October 2023 Patch TuesdayActively Exploited Zero-Day Vulnerability Affecting Microsoft Skype for Business
Microsoft Skype for Business has received a patch for CVE-2023-41763, which is rated Important and has a CVSS score of 5.3. This local privilege escalation vulnerability allows an attacker to gain access to sensitive information on a target Skype for Business server. The vulnerability allows an attacker to send specially crafted network calls to the target server and potentially reveal IP addresses and/or ports to the attacker. The proof-of-concept has already been publicly disclosed.
| Severity | CVSS Score | CVE | Description |
| Important | 5.3 | CVE-2023-41763 | Skype for Business Elevation of Privilege Vulnerability |
Table 1. Zero-day in Microsoft Skype for Business
Actively Exploited Zero-Day Vulnerability Affecting Microsoft WordPad
Microsoft WordPad has received a patch for CVE-2023-36563, which is rated Important and has a CVSS score of 6.5. The vulnerability allows for information disclosure, specifically NTLM (Windows New Technology LAN Manager) hashes. This allows an attacker to steal NTLM hashes by utilizing the preview pane when opening a document. NTLM hashes are important for gaining account access due to the nature of the protocol allowing for secure authentication, and an attacker would be able to exploit the vulnerability to crack the hashes or use them in an NTLM relay attack. The proof-of-concept has already been publicly disclosed.
| Severity | CVSS Score | CVE | Description |
| Important | 6.5 | CVE-2023-36563 | Microsoft WordPad Information Disclosure Vulnerability |
Table 2. Zero-day in Microsoft WordPad
Actively Exploited Zero-Day Attack Technique Affecting HTTP/2
Microsoft has released an update and workarounds to help protect against denial of service attacks exploiting CVE-2023-44487, which is rated Important. This vulnerability on HTTP/2 allows malicious actors to launch DDoS attacks targeting HTTP/2 servers by sending HTTP requests using HEADERS and RST_STREAM frames in a single connection. By doing this, an attacker can eventually bring down the server due to resource exhaustion. Microsoft and many other vendors have already applied mitigations and various protections to their own infrastructure to address Layer 7 request floods.
| Severity | CVSS Score | CVE | Description |
| Important | N/A | CVE-2023-44487 | MITRE: CVE-2023-44487 HTTP/2 Rapid Reset Attack |
Table 3. Zero-day distributed denial-of-service (DDoS) attack against HTTP/2
Critical Vulnerabilities Affecting Microsoft Windows
CVE-2023-35349 and CVE-2023-36697 are Critical remote code execution (RCE) vulnerabilities affecting Microsoft Message Queuing (MSMQ), and both have a CVSS score of 9.8. MSMQ has been highlighted in the past blogs and continues to be patched. To successfully exploit this vulnerability, an attacker would have to send a specifically crafted malicious MSMQ packet to a MSMQ server, leading to remote code execution. This Windows component needs to be enabled for a system to be vulnerable. Microsoft recommends checking if the “Message Queuing” service is running and TCP port 1801 is listening on the machine; if service is running and not being utilized, consider disabling.
CVE-2023-41765, CVE-2023-41767, CVE-2023-41768, CVE-2023-41769, CVE-2023-41770, CVE-2023-41771, CVE-2023-41773, CVE-2023-41774 and CVE-2023-38166 are Critical RCE vulnerabilities affecting Layer 2 Tunneling Protocol, and all have a CVSS score of 8.1. For an attacker to take advantage of these vulnerabilities, they would need to win a race condition by sending specially crafted protocol messages to a routing and remote access service (RRAS) server. This can lead to remote code execution (RCE)on the targeted server.
CVE-2023-36718 is a Critical RCE vulnerability affecting Microsoft Virtual Trusted Platform Module with a CVSS score of 7.8. Successfully exploitation of this vulnerability relies on complex memory shaping techniques, and the attacker must have privileges to the target environment. Operating as a guest user within the virtual machine, an attacker can potentially escape the isolated machine and access resources outside of that protected device.
| Severity | CVSS Score | CVE | Description |
| Critical | 9.8 | CVE-2023-35349 | Microsoft Message Queuing Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2023-36697 | Microsoft Message Queuing Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2023-41765 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2023-41767 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2023-41768 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2023-41769 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2023-41770 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2023-41771 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2023-41773 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2023-41774 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2023-38166 | Layer 2 Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2023-36718 | Microsoft Virtual Trusted Platform Module Remote Code Execution Vulnerability |
Table 4. Critical vulnerabilities in Windows
Out-of-Band Zero-Day’s Patched Vulnerabilities Affecting Edge, Teams, Skype and Visual Studio
CVE-2023-4863 is a Critical heap buffer overflow vulnerability in libwebp (WebP image library) in Chromium Open Source Software (OSS) that is utilized by Microsoft Edge (Chromium-based) and has a CVSS score of 8.8. This allows for a remote attacker to perform an out-of-bounds memory write via a specially crafted HyperText Markup Language (HTML) page. Microsoft released security updates to VP9 Video Extension, Skype, WebP Image Extension, Teams and Edge (Chromium-based) on October 4, 2023. The proof-of-concept has already been publicly disclosed and is actively being exploited.
CVE-2023-5346 is a High severity type confusion vulnerability in Version 8 of Microsoft Edge (Chromium-based). The vulnerability allows for a remote attacker to potentially exploit heap corruption via a crafted HyperText Markup Language (HTML) page. Microsoft released security updates to Microsoft Edge (Chromium-based) on October 4, 2023.
| Severity | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2023-4863 | Chromium: CVE-2023-4863 Heap buffer overflow in WebP |
| High | 8.8 | CVE-2023-5346 | Chromium: CVE-2023-5346 Type Confusion in V8 |
Table 5. Vulnerabilities in Chromium, Edge, Teams, Skype and Visual Studio
Not All Relevant Vulnerabilities Have Patches: Consider Mitigation Strategies
As we have learned with other notable vulnerabilities, such as Log4j, not every highly exploitable vulnerability can be easily patched — as is also the case for the ProxyNotShell vulnerabilities. It’s critically important to develop a response plan for how to defend your environments when no patching protocol exists.
Regular review of your patching strategy should still be a part of your program, but you should also look more holistically at your organization's methods for cybersecurity and improve your overall security posture.
The CrowdStrike Falcon® platform regularly collects and analyzes trillions of endpoint events every day from millions of sensors deployed across 176 countries. Watch this demo to see the Falcon platform in action.
Learn More
Learn more about how CrowdStrike Falcon® Spotlight can help you quickly and easily discover and prioritize vulnerabilities here.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- For more information on which products are in Microsoft’s Extended Security Updates program, refer to the vendor guidance here.
- Download the CrowdStrike 2023 Global Threat Report and CrowdStrike 2023 Threat Hunting Report to learn how the threat landscape has shifted in the past year and understand the adversary behavior driving these shifts.
- See how Falcon Spotlight can help you discover and manage vulnerabilities and prioritize patches in your environments.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of CrowdStrike Falcon® Prevent next-generation antivirus.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































