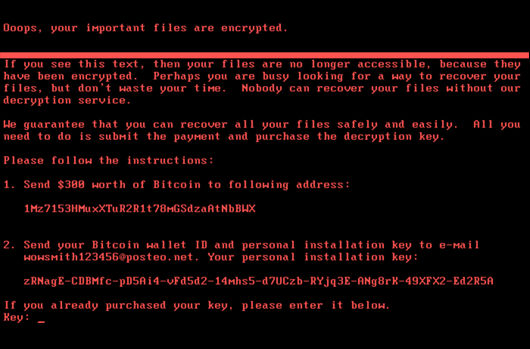
Update:
Due to naming convention consistency in the industry, CrowdStrike is now calling this variant of Petya - NotPetya.
Executive Summary
This technical analysis provides an in-depth analysis and review of NotPetya.
For more information on CrowdStrike’s proactive protection features see the earlier CrowdStrike blog on how Falcon Endpoint Protection prevents the NotPetya attack. NotPetya combines ransomware with the ability to propagate itself across a network. It spreads to Microsoft Windows machines using several propagation methods, including the EternalBlue exploit for the CVE-2017-0144 vulnerability in the SMB service. This is the same vulnerability Microsoft reported on in MS17-010, which was exploited so successfully in the recent WannaCry ransomware outbreak.
Once a machine is infected by NotPetya, a series of malicious activities ensue, including the following:
- Dropped files
- Process hashes and process privilege checks
- Credential theft
- Token impersonation
- Malware propagation
- Network node enumeration
- SMB copy and remote execution
- SMBv1 exploitation via EternalBlue
- UNC write malware to admin$ on remote target
- Remote execution of the malware
- MBR ransomware
- Physical drive manipulation
- MFT encryption
- File encryption
- System shutdown
- Anti-forensics
Ransomware instructions for file recovery occur after the infection process has completed. Do NOT pay the ransom. No files will be recovered if the ransom is paid.
Dropped Files
The following files are dropped by the malware:
- Ransomware DLL
C:\windows\perfc.dat
- The malware decompresses its resource named 0x3 of type RT_RCDATA, and writes the contents to C:\Windows\dllhost.dat. Analysis of dllhost.dat shows that it is a copy of the PsExec utility, which is a telnet replacement that allows execution of processes on other systems.
- C:\windows\dllhost.dat
- Credential theft module
- Written as a .tmp file to the temp directory
- Ransomware splash and warning files
Command Line Execution
The malware is a DLL that is launched using rundll32.exe:
“C:\Windows\perfc.dat”,#1 18 <“username1:pass1” “username2:pass2” ... >
Perfc.dat is the malware name. It is executed with the following arguments:
- #1 → This is the ordinal number of the exported function
- 18 → Minutes used to determine how long to wait for the scheduled shutdown
- “username:pass” → Credentials to be used to propagate the malware on the network.
Process Hashes and Process Privilege Checks
Upon being loaded, the malware starts a subroutine that hashes each running process on the system, and compares each hash with 3 hardcoded hashes:
- 0x6403527E → avp.exe associated with Kaspersky AV
- 0x23214B44 → ns.exe associated with Norton Security
- 0x651B3005 → ccSvcHst.exe associated with Symantec
A global flag PROC_FLAG is used to track which of the 3 processes are running on the system.
- PROC_FLAG = 0xFF → none
- PROC_FLAG = 0xFB → ns.exe or ccSvcHst.exe
- PROC_FLAG = 0xF7 → avp.exe
- PROC_FLAG = 0xF3 → avp.exe and either ns.exe and/or ccSvcHst.exe
In addition, within the same subroutine, the malware attempts to gain various levels of privilege. It uses a global flag PRIV_FLAG to track the extent of privileges the malware is able to obtain.
- PRIV_FLAG = 0 → no privileges
- PRIV_FLAG = 1 → SeShutdownPrivilege. Ability to shutdown the system.
- PRIV_FLAG = 2 → SeDebugPrivilege. Required to either debug or adjust memory for a process owned by another account
- PRIV_FLAG = 3 → SeShutdownPrivilege & SeDebugPrivilege
- PRIV_FLAG = 4 → SeTcbPrivilege. Process can assume the identity of any user
- PRIV_FLAG = 5 → SeShutdownPrivilege & SeTcbPrivilege
- PRIV_FLAG = 6 → SeDebugPrivilege & SeTcbPrivilege
- PRIV_FLAG = 7 → SeShutdownPrivilege & SeDebugPrivilege & SeTcbPrivilege
These 2 flags have a considerable impact on the execution of the malware.
- The credential theft module is dropped if the malware has one of the following privileges: (It should be noted that the PROC_FLAG can any of the possible values)
- SeDebugPrivilege
- SeShutdownPrivilege & SeDebugPrivilege
- SeDebugPrivilege & SeTcbPrivilege
- SeShutdownPrivilege & SeDebugPrivilege & SeTcbPrivilege
- The MBR overwrite and MFT encryption subroutine is not executed if avp.exe is found running on the system
- The EternalBlue subroutine is not executed if either ns.exe or ccSvcHst.exe are found running on the system
- The system is rebooted using the API NtRaiseHardError if the process has at least the SeShutdownPrivilege level
Credential Theft
Credentials are provided to the malware in two ways:
- As an argument to the DLL (see command line execution section)
- Communication via a named pipe from the credential theft module
To create a named pipe, a random GUID is generated, and the credential theft module is launched as a child process with the named pipe as an argument. 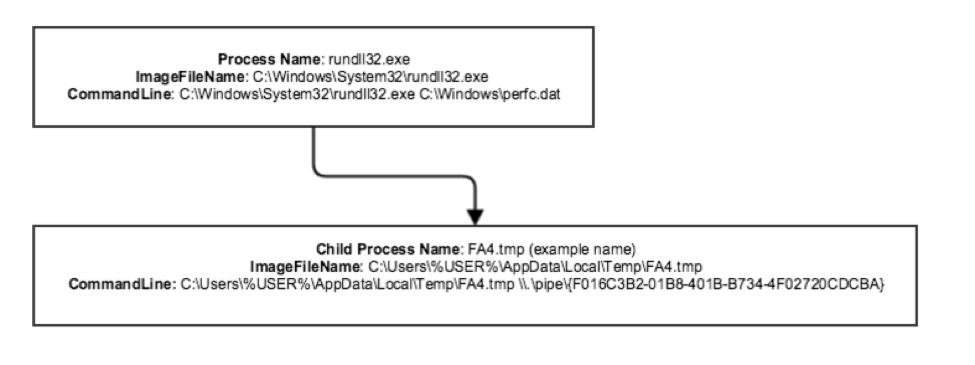 Communication is constantly monitored by a thread that invokes PeekNamedPipe to copy data from the pipe. Credential Theft Module Depending on the OS architecture, the malware will either drop a 32-bit version or a 64-bit version of the credential theft module. The malware decompresses a resource (0x1 if the OS is x86, 0x2 if the OS is x64) of type RT_RCDATA using zlib 1.2.8 compression. The resulting contents are then written to a randomly named .tmp file in the %TEMP% folder. Upon being loaded, the module initializes and sets up a CNG provider. It calls OpenProcess on lsass.exe with access flag set to VM_READ, and looks for the modules wdigest.dll and lsasrv.dll loaded in the lsass.exe process.
Communication is constantly monitored by a thread that invokes PeekNamedPipe to copy data from the pipe. Credential Theft Module Depending on the OS architecture, the malware will either drop a 32-bit version or a 64-bit version of the credential theft module. The malware decompresses a resource (0x1 if the OS is x86, 0x2 if the OS is x64) of type RT_RCDATA using zlib 1.2.8 compression. The resulting contents are then written to a randomly named .tmp file in the %TEMP% folder. Upon being loaded, the module initializes and sets up a CNG provider. It calls OpenProcess on lsass.exe with access flag set to VM_READ, and looks for the modules wdigest.dll and lsasrv.dll loaded in the lsass.exe process.
- wdigest.dll → Digest authentication security package. Used to:
- Authenticate client access with integrity protection to a directory service using LDAP
- Authenticate client access using SASL
- Authenticate client access to a web site
- lsasrv.dll → Authentication security component. The lsasrv.dll is a LSA (Local Security Authority) Server service, which both enforces security policies and acts as the security package manager for the LSA
This file extracts credentials from LSASS similar to Mimikatz. The extracted credentials are sent to the NotPetya process via the named pipe.
Token Impersonation
Impersonation occurs only if the process has the required privilege level to assume the identity of another user. OpenProcessToken and GetTokenInformation is used to grab the TokenSessionId for terminal service sessions. Each token is duplicated and the new handle is saved to a list. For each of the duplicated tokens, a new thread is created in suspended mode. The impersonated token replaces the current thread token with SetThreadToken and the thread is resumed. This thread is then used to execute the SMB copy and remote execution section as the impersonated user.
Malware Propagation
The following methods are used to spread across a network:
- Network node enumeration
- SMB copy and remote execution
- SMB exploitation via EternalBlue
Network Node Enumeration
The malware attempts to gather a list of known TCP endpoints and IP addresses to check whether it can connect to the IPs via SMB ports 445 and 139. The malware creates a thread for core work that invokes the following API's:
- GetExtendedTcpTable to retrieve a list of TCP endpoints
- GetIpNetTable to retrieve the IPv4 to physical address mapping table → Gets a MIB_IPNETTABLE structure
- NetServerEnum to get a list of servers on the domain with the following parameters:
- Servername = null
- level = 101 (return server names, types, and associated data)
- NetServerGetInfoto retrieve the current configuration for the local server, specifically to determine if the system is a non-domain controller server, a primary domain controller, or a backup domain controller. The API returns a SERVER_INFO_101 structure that contains an sv101_type field. The malware checks to see if the value of that field is SV_TYPE_SERVER_NT, SV_TYPE_DOMAIN_CTRL, or a SV_TYPE_DOMAIN_BAKCTRL. If the field is either of the values mentioned, the following takes place:
- DhcpEnumSubnets to get an enumerated list of subnets on the server
- DhcpGetSubnetInfo on each subnet on the list to get the DHCP_SUBNET_STATE value to see whether the DhcpSubnetEnabled flag is set
- DhcpEnumSubnetClients on each subnet with the aforementioned flag set. This function returns an enumerated list of clients associated with the IP addresses in each subnet. For each client, the following occurs:
- Obtains the IP address from the ClientIpAddress field in the DHCP_CLIENT_INFO structure
- Attempts to establish a socket connection to the client IPs over ports 445 and 139 (both associated with SMB)
SMB Copy and Remote Execution
There are two approaches to using valid credentials to copy and execute the malware to a remote host:
- Token impersonation
- Requires the process to have “SeTchPrivilege”
- Stolen credentials
Each of these methods will be used to do a UNC write to Admin$ and then execute the malware on the target machine. SMBv1 Exploitation via EternalBlue NotPetya has the capability to exploit SMBv1 via the well known EternalBlue exploit. Once the exploit is launched, the shellcode will end up writing the file and executing the malware on the target machine.
UNC Write to Admin$
WNetAddConnection2W is used to connect to a server using the default credentials for the impersonated token, and an attempt is made to write the file to:
- \\server-name\\admin$\\malware-name
- UNC write to admin$
CreateFile and WriteFile are used to write the file to the remote server. The typical filename is
perfc.dat.
Remote Execution
Remote execution relies on either PsExec or WMIC. DLLHost.dat (psexec)
The following command will execute on the remote machine:
C:\Windows\dllhost.dat \\<target host> -accepteula -s -d C:\Windows\System32\rundll32.exe “C:\Windows\perfc.dat”,#1 18 “<additional creds for arguments>””
- -accepteula → This suppresses the display of the license dialog
- -s → run as system
- -d → do not wait for process termination
- -u → username (not shown here)
- -p → password (not shown here)
WMIC
The following command will execute on the remote as the specified user:
C:\Windows\system32\wbem\wmic.exe /node:”<server name>” /user:”<username>” /password:”<password>” process call create “C:\Windows\System32\rundll32.exe \”C:\Windows\perfc.dat\” #1 19 “<additional creds for arguments>””
- /node → specify server name
- /user → username
- /password → password
- Process call create → execute remote command
Once the command line arguments are generated, either CreateProcessAsUser or CreateProcess is executed, depending on whether this is being done through impersonation or stolen credentials.
MBR Ransomware
Physical Drive Manipulation
The malware calls DeviceIOControl on //./PhysicalDrive0 with IOCTL_DISK_GET_PARTITION_INFO_EX control code to get PARTITION_INFORMATION_EX structure.
The structure represents the physical location on the disk. The malware takes the following steps to modify the MBR:
- Reads the MBR and encodes it using XOR encoding with key 0x7
- The first sector is overwritten by a custom boot loader
- The next 31 sectors are then overwritten by 16-bit code that is responsible for encrypting the MFT using Salsa20 encryption
- Sector 32 contains the following:
- CRYPT_FLAG --> Initially, this byte is set to 0, which denotes that the MFT has not been encrypted. The 16-bit code uses this flag to determine whether to infect the MFT
- A random array of bytes 0x20 in length is generated using CryptGenRangom. This is used as the Salsa20 encryption key. In addition, another random array of bytes 0x8 in length is created using the same API call; this is used as the nonce for the encryption. The malware also writes the hardcoded string 1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX in the sector. This is the Bitcoin wallet that is later displayed on the splash screen.
- A random blob is created by CryptGenRandom 0x3C bytes in length. This is presented as the user’s personal installation key on the splash screen. It should be noted that this personal installation key is random in nature; and therefore there is no way to trace it back to the victim machine
Sector 33 contains all 0x7’s. This is used as an integrity check for the decryption process.
Sector 34 contains the original MBR that was encoded by XORing with 0x7
MFT Encryption
As mentioned previously, the malware has its own custom boot loader once the machine has been infected and rebooted. This code within the MBR is responsible for loading the code which encrypts the MFT using Salsa20, displays the ransom note, and accepts the private key. It should be noted that the code is a low-level 16-bit code that uses BIOS interrupt calls to display text to the user, accept user input, and read/write to various sectors. Since this code is run outside of the OS, its capabilities are quite limited.
However, its main purpose is to encrypt or decrypt the MFT, which it is able to accomplish using Salsa20. The following are the BIOS interrupt services used throughout the code:
- int 0x13 - read/write sectors on disk
- int 0x10 - display text
- int 0x19 - cause disk reboot
- int 0x16 - obtain keystrokes, and status of keyboard buffer
The code first checks the CRYPT_FLAG in sector 32 to see whether it has been set to 1 (encrypted). The first time a machine is infected, the CRYPT_FLAG is always set to 0 (not encrypted), which leads the malware to invoke a subroutine that displays the following decoy check disk screen to the user.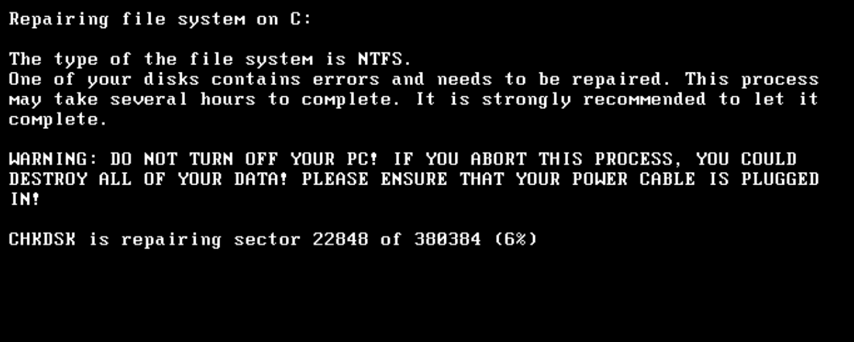
In reality, the subroutine performs the following functions:
- Sets the CRYPT_FLAG to 1. This is performed before any encryption actually takes place
- Encrypts the contents of Sector 33 using the Salsa20 cipher. Shortly after the encryption, the buffer containing the Salsa20 key is overwritten; therefore, the key is destroyed
- Encrypts the MFT and stores a counter of MFT records that are encrypted
- Causes a disk reboot
Upon a second reboot, the NotPetya ransomware note is displayed as shown below: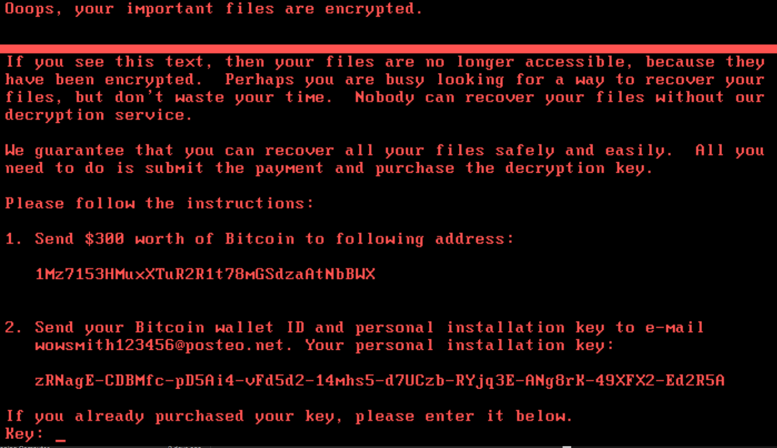
In addition, it initiates a loop that waits for the user to input the purchased key. Once the key is entered, the code attempts to decrypt the contents of Sector 33, which were previously encrypted using Salsa20 key. Once the sector is decrypted, the code reads all 512 bytes of the sector and ensures that they all equal 0x7. If this is successful, the CRYPT_FLAG is set to 2 (decrypted), and the same key is used to decrypt the MFT.
Furthermore, the original encoded MBR in Sector 34 is also decoded, and placed back into Sector 0, as shown below.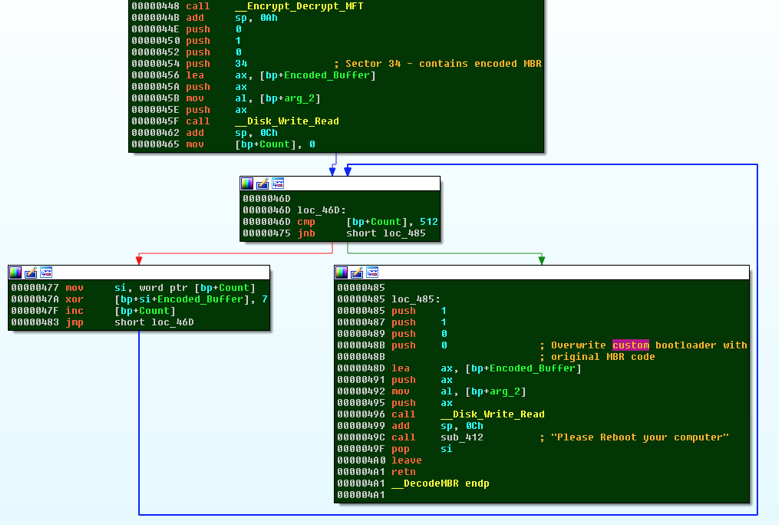
File Encryption
Along with MFT encryption, the malware also targets certain files.
The following table contains the file extensions that are targeted:
| .3ds | .7z | .accdb | .ai | .asp | .aspx | .avhd | .back | .bak | .c | ||
| .cfg | .conf | .cpp | .cs | .ctl | .dbf | .disk | .djvu | .doc | .docx. | ||
| .dwg | .eml | .fdb | .gz | .h | .hdd | .kdbx | .mdb | .msg | |||
| .nrg | .ora | .ost | .ova | .ovf | .php | .pmf | .ppt | .pptx | |||
| .pst | .pvi | .py | .pyc | .rar | .rtf | .sln | .sql | .tar | .vbox | ||
| .vbs | .vcb | .vdi | .vfd | .vmc | .vmdk | .vmsd | .vmx | .vsdx | .vsv | ||
| .work | .xls | .xlsx | .xvd | .zip |
The malware only targets fixed drives on the system. It invokes CryptGenKey to generate an AES-128 key. This key is used to encrypt all the files on the system. The malware will first start enumerating files in the directory it is being executed from. The following steps are taken to encrypt the individual files:
- Gets file handle
- Gets the file size
- Creates a file mapping of the file with PAGE_READWRITE protection
- Maps the view of the file mapping with FILE_MAP_WRITE | FILE_MAP_READ access
- Calls CryptEncrypt to encrypt the contents of the file using AES-128
Once the files in a folder are encrypted, the ransomware drops a ransomware note in a file named README.txt. The “personal installation key” is the result of the AES-128 key encrypted with an RSA-2048 key, which is included in the malware.
Once the README.txt is dropped on disk, CryptDestroyKey is invoked to release the handle to the key. The following message is then displayed to the user:
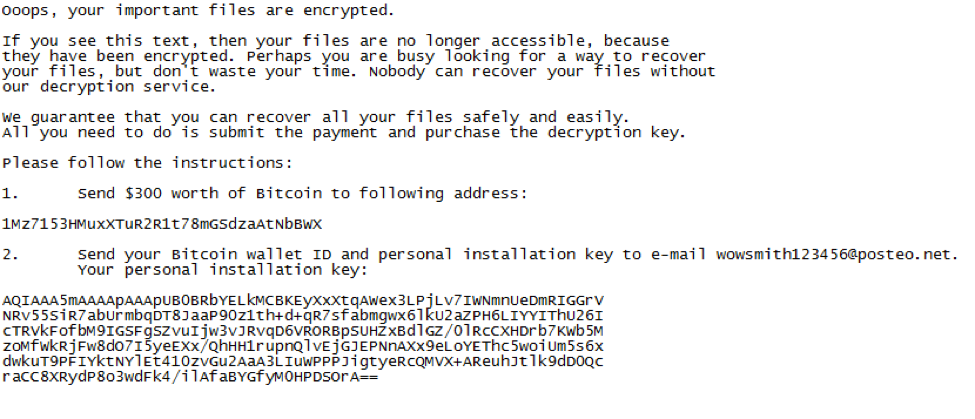 System Shutdown
System Shutdown
NotPetya employs a few methods to ensure that the system reboots so that the boot loader loads the MFT encryptor code. It spawns cmd.exe with the following command line: /c schtasks /Create/SC once /TN "" /TR "C:\Windows\system32\shutdown.exe /r /f" /ST <HH:MM> The <HH:MM> value depends on the second parameter when being invoked by rundll32.exe. If the second parameter is 30, the scheduled task will trigger 30 minutes after the malware execution. However, if no second parameter is provided, the scheduled task is set to trigger 60 minutes after the malware execution by default. Explanation of schtask parameters:
- /TN → taskname (not providing a custom name forces Windows to provide a random GUID as a name)
- /TR → taskrun. Path and filename of the task to be run
- /ST → starttime
Explanation of shutdown.exe parameters:
- /r → reboot after shutdown
- /f → forces running applications to close
In addition, it also invokes the API NTRaiseHardError. This is an undocumented Windows API that causes the system to reboot. If the API fails to execute, the malware calls InitiateSystemShutdownExW with the flag set to reboot the machine.
Anti-Forensics
The malware employs anti-forensics practices throughout its execution. For instance, immediately after execution, it loads itself in memory, and deletes itself from the disk. However, before deletion, it zeros out the file contents on disk to ensure that the malware cannot be recovered via disk forensics. The malware uses a similar approach for the credential theft module it drops as well. Once the contents of its resource section are decompressed and written to disk, it zeros out the memory buffer containing the decompressed PE files. Furthermore, once execution of those files take place, it zeroes out its file contents before deleting from the disk. The malware also spawns cmd.exe to execute the following command: /c wevtutil cl Setup & wevtutil cl System & wevtutil cl Security & wevtutil cl Application & fsutil usn deletejournal /D C:” This command is responsible for clearing out the following logs:
- Setup logs: contains events related to application setup
- System logs: contains events pertaining to system components
- Security logs: contains events such as logon attempts, file creation, access, deletion
- Application logs: contains events logged by applications
- USN journal: maintains a record of changes made to a particular volume
For information on CrowdStrike’s proactive protection features see the earlier CrowdStrike blog on how Falcon Endpoint Protection prevents this destructive ransomware.
Appendix A: Indicators of Compromise (IOCs)
Below is the relevant data for the files analyzed. File: Dropper / Payload Size: 362360 MD5: 71B6A493388E7D0B40C83CE903BC6B04 SHA256: 027CC450EF5F8C5F653329641EC1FED91F694E0D229928963B30F6B0D7D3A745 Compiled: Sun, Jun 18 2017, 7:14:36 - 32-bit DLL Signature Corrupt Subject: Microsoft Corporation Issuer: Microsoft Code Signing PCA File:Credential Theft Module 32-bit Size: 47616 MD5: 2813D34F6197EB4DF42C886EC7F234A1 SHA256: EAE9771E2EEB7EA3C6059485DA39E77B8C0C369232F01334954FBAC1C186C998 Compiled: Tue, Jun 6 2017, 13:31:37 – 32-bit EXE File: Credential Theft Module 64-bit Size: 57344 MD5: 7E37AB34ECDCC3E77E24522DDFD4852D SHA256: 02ef73bd2458627ed7b397ec26ee2de2e92c71a0e7588f78734761d8edbdcd9f Compiled: Tue, Jun 6 2017, 13:31:37 – 64-bit EXE File: dllhost.dat Size: 381816 MD5: AEEE996FD3484F28E5CD85FE26B6BDCD SHA256: F8DBABDFA03068130C277CE49C60E35C029FF29D9E3C74C362521F3FB02670D5 Compiled: Tue, Apr 27 2010, 0:23:59 - 32-bit EXE Version: 1.98 Signature Valid Subject: Microsoft Corporation Issuer: Microsoft Code Signing PCA
For information on CrowdStrike’s proactive protection features, see the earlier CrowdStrike blog on how Falcon Endpoint Protection prevents this destructive ransomware.
Experience CrowdStrike's next-gen antivirus solution first hand for 15 days by visiting the Falcon Prevent free trial page.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)