Many of my team members know that one of my favorite parts of running CrowdStrike is meeting with customers.
It’s always fascinating to hear from customers about the challenges they face on a day-to-day basis.
Some of the customers we protect are so large they seem like mini-Internets.
Dispersed networks, heterogeneous and diverse geographies make protecting these organizations from the adversary a major challenge.
As you might imagine, their security maturity levels vary from the ultra-sophisticated, over-resourced companies with plenty of experts on staff, to the multi-billion dollar company with one security person. While each company we work with has its own unique personality and challenges, there is always one constant: At some point it had a breach.
That in itself should not be a surprise, as most people in the security industry realize this is a fact of life. But beyond the obvious, there’s one more very important similarity that many won’t be as familiar with: Each company suffered from a scenario I term as “Silent Failure.”
Each of these companies had a litany of security technologies in place that were supposed to detect and prevent a breach from advanced threats, yet a breach still occurred. As it turns out, anti-virus, firewalls, Intrusion Prevention Systems (IPS), and endpoint IOC-scanning forensics tools have all failed silently.
This scenario of silent failure is all too common and normally results in an adversary being able to roam most networks unfettered for well over 200 days on average before detection. Simply put, this is an unacceptable situation, as your most coveted intellectual property, financial information, and Personally Identifiable Information (PII) gets siphoned out of your network at the speed of light. The Security Industry’s Success is a Product of its Failure The security industry has enjoyed unbelievable growth over the past decade.
Companies like CrowdStrike have been able to flourish because we, like others, are a product of the growing and sad state of the current security industry failures.
For a customer, this scenario is incredibly frustrating as organizations continue to invest in security technologies that rely on outdated architectures and approaches.
Companies that have built these technologies of days gone by have yet to understand that the problem we face today is not an advanced malware problem.
It is an advanced adversary problem.
In your organization, you’re not fighting the latest PlugX variant from China.
You must fight to keep your organization safe from the threat actor who created this malware and who is hell-bent on getting into your company.
You have to realize that no security technology will keep a determined adversary off your network. None. This is a human problem, and just like in chess, the adversary always has a move to play and we don’t get to say when the game is over.
So why aren’t we building into our security models the fact that there will be system failure?
We must attempt to build and ensure that the systems of tomorrow do not fail silently. The Prevention Continuum One of the things that really excites me about what we’re building at CrowdStrike is that we recognize one security approach is not good enough to protect against all attackers, nor can it be designed to prevent silent failure in your defenses.
Be it virtual execution engines, sandboxing, or “math” based approaches, these one-trick ponies won’t be able to deal with every threat effectively. At CrowdStrike, we take a unique approach to prevention.
We look at prevention as a continuum from pre-compromise all the way through the post-compromise phase.
It’s all about using the right detection and prevention techniques at the right point in time to detect, prevent, and contain an adversary.
Our strong belief is that by attempting to get this right, we will ultimately prevent the adversary from achieving their objectives. Earlier this week we launched the latest release of our next-generation endpoint protection offering.
CrowdStrike Falcon®, now brings prevention to the Endpoint Detection and Response (EDR) space.
Let me walk you through the approach we take to maximize protection across the adversary attack timeline. 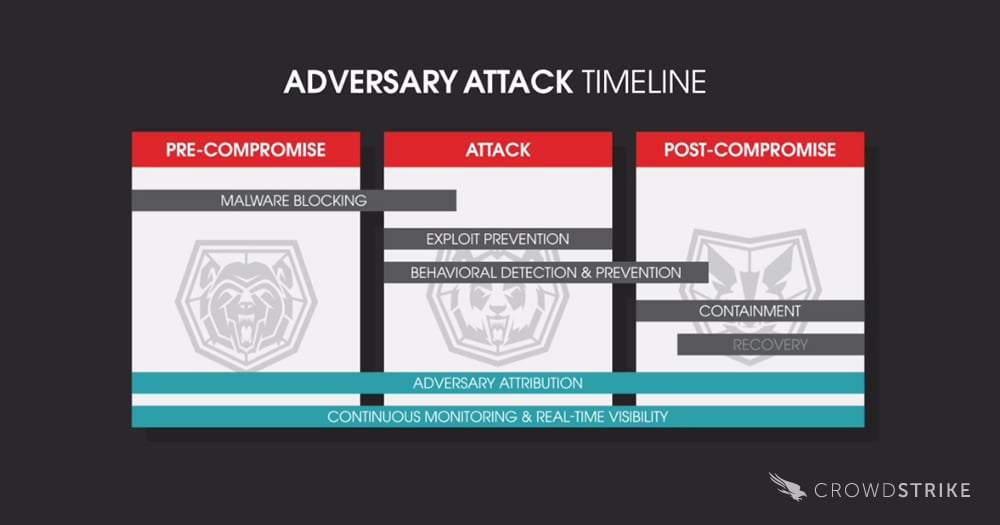 Pre-Compromise Phase During the pre-compromise phase, the adversary is focused on getting into your organization and gaining a foothold to carry out their objectives.
Pre-Compromise Phase During the pre-compromise phase, the adversary is focused on getting into your organization and gaining a foothold to carry out their objectives.
Typically, they’ll use spear phishing emails containing malicious links or attachments as first step in gaining internal system access.
They could be using off-the-shelf commodity malware or, in many cases, they’ll create one-off malware with unique hashes to avoid detection. Our first phase of protection consists of getting rid of the known malware using traditional indicators.
It’s easy and often fashionable to criticize anti-virus technologies, but the reason they’ve been around so long is that indicators are relatively cheap to look for. If you know it’s bad, simply prevent the malware from executing.
While cheap and easy, we know up front that this method has limitations in dealing with unknown malware typically used in highly targeted attacks.
So while this method will get rid of a lot of noise, we designed our architecture to not fail silently. Attack Phase The attack phase is really the point at which the adversary has avoided traditional indicator-based detection, and it’s focused on getting malicious code execution to occur on your endpoints (desktops or servers).
This is the area where we’ve spent a significant amount of time in building a platform solution that can inherently deal with unknown malware as well as detecting adversary activity. CrowdStrike Falcon® detects threats in real time across the adversary timeline by leveraging its groundbreaking Stateful Execution Inspection (SEI) endpoint engine to look for Indicators of Attack (IOAs) in combination with machine learning to identify the unknown threats in our Advanced Threat Intelligence cloud.
IOAs, unlike Indicators of Compromise (IOCs) used by legacy endpoint detection solutions, focus on dynamically detecting the intent and effects of what the attacker is trying to accomplish, regardless of which specific malware or exploit may be used in the attack.
Just like AV signatures, an IOC-based detection approach is incapable of detecting the increasing threats from malware-free intrusions (see Malware-Free Intrusions blog)
and zero-day exploits, necessitating next-generation security solutions to move to a stateful IOA-based detection approach pioneered by CrowdStrike. In addition to our SEI engine, we’ve also added exploit mitigation technology to our endpoint sensor.
This protection technique goes hand in hand with detecting IOAs and prevents the successful exploitation of the underlying operating system.
Essentially we’re preventing the adversary from using common exploitation techniques by obstructing the execution of their exploit code on your endpoint, all in real time.
This allows our customers to prevent successful exploitation of a zero-day attack using previously undiscovered malware.
Powered by our SEI engine, our IOA-based prevention technology combined with zero-day exploit mitigation techniques make for a very powerful and potent package for our Falcon customers. Post-Compromise Phase The post-compromise phase is all about detecting and containing an adversary.
Should an adversary gain access to your systems, it’s critical to detect their activity as soon as possible.
The good news for the defenders is that, just like in chess, there are only so many opening gambits that are possible during this phase.
Generally, you’ll see an adversary connect back out to the Internet to establish a command-and-control channel, attempt to maintain persistence (sometimes without using malware), dump credentials, and laterally move from system to system.
The bad news for defenders is that they were previously shackled with IOC-based snapshot systems that weren’t able to detect this activity in real time. To prevent silent detection failure that plagues all legacy security solutions, CrowdStrike Falcon® incorporates Endpoint Activity Monitoring (EAM) capability that acts like a DVR for your endpoint.
It records security-relevant information and provides an on-demand query capability for full real-time and historic visibility into more than 120 different types of endpoint execution activities.
These events include: process and module user-mode and kernel execution events; file system activity; network and registry activity; credential theft and lateral movement; privilege escalation; and user-logon activity. This comprehensive real-time forensic visibility is a key requirement in next-generation endpoint solutions to provide a full narrative of the attack that enables organizations to hunt for silent failures.
Like the picture in a CSI crime scene investigation, snapshot technologies only provide a small amount of information that loses all temporal fidelity.
So if adversaries clean up after themselves, the crime scene will be free of critical artifacts.
However, if you have the DVR recording of what happened, you can ensure that you have all the critical information needed to identify patient zero and drastically reduce your overall response time. Visibility and Context Across the entire continuum, CrowdStrike Falcon® provides host visibility as well as contextual intelligence about identified threats.
CrowdStrike Falcon® leverages world-class adversary threat intelligence that is seamlessly integrated into its cloud platform, to instantly attribute and categorize the adversary behind a targeted attack in order to prioritize a response and provide crucial strategic threat and business context about the attack. Security organizations today are overwhelmed with alerts from outdated and ineffective security products that don’t provide any context or prioritization of attacks, which often results in security teams missing these threats even when remnants of it may be picked up by a legacy solution.
A next-generation endpoint security solution must provide threat intelligence that provides context to prioritize your response and answer the crucial what, who, how, and why questions. Time for new approach It has been almost three years to the day that we started on our mission to change the way people view and use endpoint security.
Over that period of time, we have constantly heard from customers that they were tired of the same old approach that has been ineffective in stopping the adversary.
They were also tired of agent fatigue – loading multiple agents to detect and prevent, as well as to provide visibility and response capabilities.
They’ve been asking for a better way forward. With the introduction of prevention, CrowdStrike Falcon® takes a comprehensive approach to stopping the attacks and ensures that no one component fails silently.
With one lightweight sensor, we fully integrate all these requisite capabilities into one package that can be deployed with little friction in your environment; it literally takes less than 10 seconds to install and doesn’t even need a reboot.
Moreover, we fully integrate our threat indicators into our cloud to help customers prioritize what events are most critical based on the threat actor and their historical objectives.
Customers can also supply their own indicators to prevent execution of known malware in the pre-compromise stage across their entire organization. Finally, our unique exploit-blocking technology automatically stops execution of zero-day exploits in their tracks.
With our latest release of CrowdStrike Falcon®, we’re very excited about redefining endpoint security and making it more difficult for the adversary to operate with impunity. If you’re interested in learning more about CrowdStrike Falcon®, please visit us
to find out more information or contact sales@crowdstrike.com to arrange for a briefing from one of our associates. Stay secure and keep up the good fight! George Kurtz President & CEO, CrowdStrike Inc.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)





















































